In this überbrief video tutorial, you'll find instructions for adding a CNAME record to tinydns. The steps, demonstrated in the video, are as follows: Open up the data file, type a capital C, the domain you'd like to use, or subdomain, the IP address of the machine or destination you'd like that hostname to route to and the TTL or time to live. Save the changes, type make, and test it out!

This video demonstrates how to use SSH to connect remotely to your server using its IP address. If you do not have the IP addres of your server, you'll need to obtain it before SSHing into your computer from a remote location. Watch this tutorial for a step-by-step walkthrough of the process.

This how-to video will walk you, step by step, through the process of upgrading the hard drive on your MacBook. More specifically, this tutorial addresses saving your old data by creating a copy, or cloning, your MacBook hard drive with SuperDuper, removing it, and installing the new drive. For precise instructions, press play!
If your cell phone doesn't have internet capabilities, or you're just unwilling to pay the insane price of the web connectivity rates, you can still access Google as long as you can text message. Google responds to text messages with the best match, so it's more ideal for looking up phone numbers, addresses, weather reports, or a word definition. Watch this video cell phone tutorial and learn how to search Google on phone through SMS text messages.
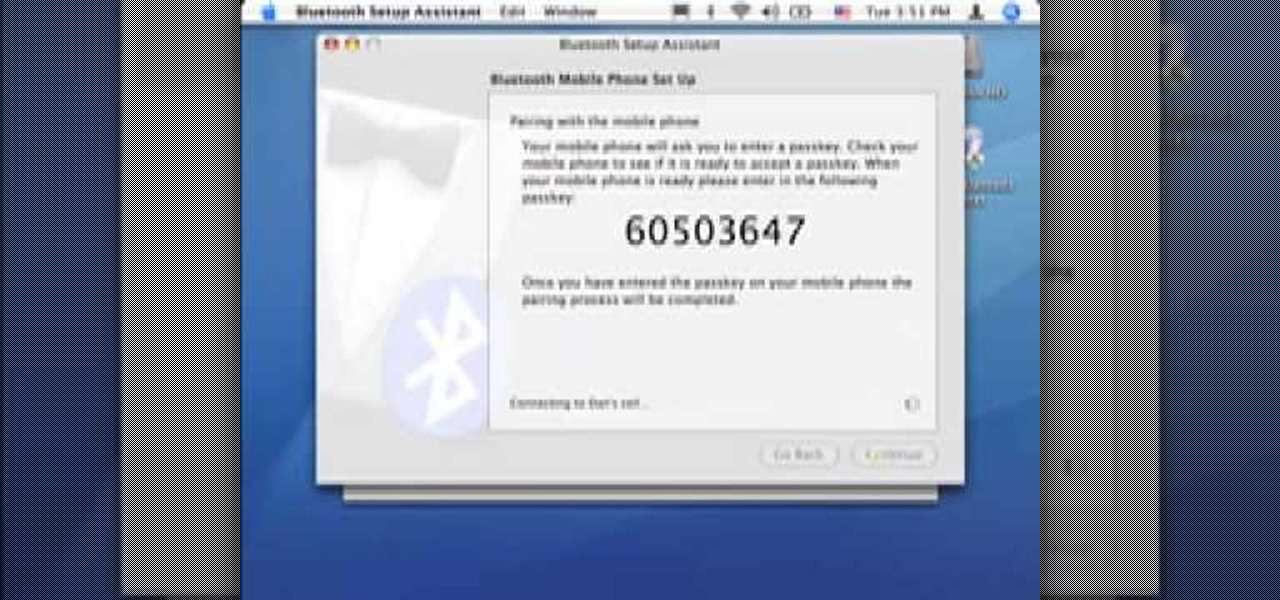
Did you know you can sync up your cell phone (any cell phone with Bluetooth) with your MAC computer? Doing so will enable you to do several things, including importing and syncing your address book, iCal (calender application), and even tethering your phone with your computer so you can get internet.

Stuff veal to add moisture and substance to your meal. Veal should be cooked more like poultry than beef. Make your favorite stuffing and allow it to cool before addressing the veal. Be careful not to overstuff the veal breast. Finally, tie it shut with cooking twine, season and cook.

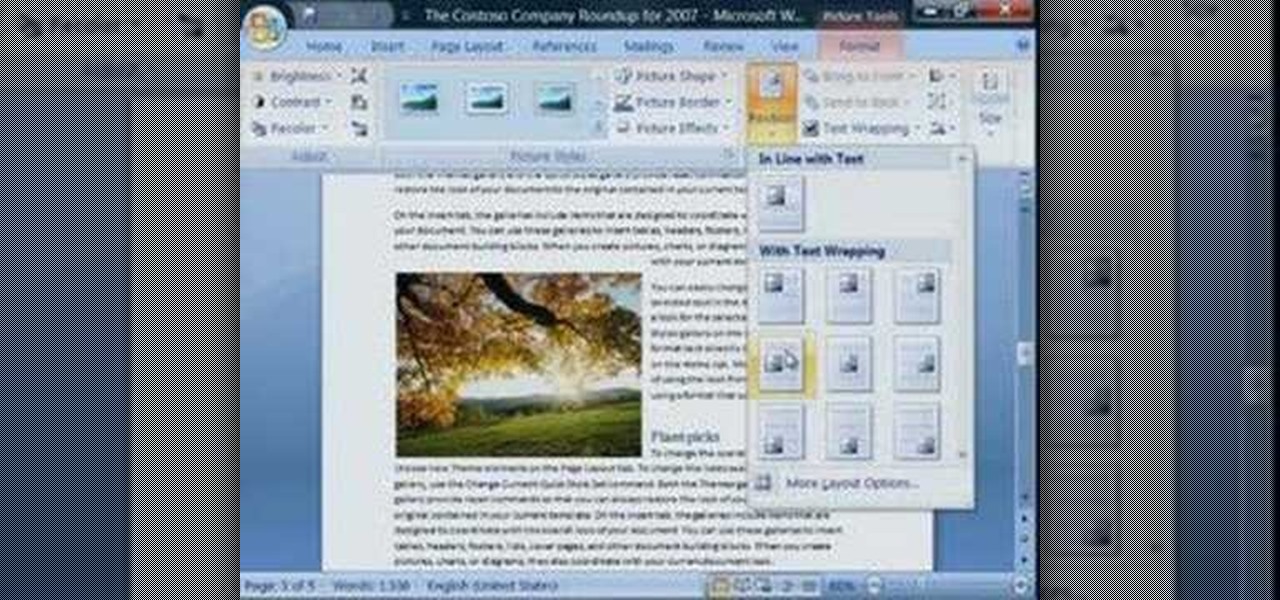
If you're baffled about how to get your own photographs into your Microsoft Office Word 2007 documents, watch this instructional video. A Microsoft employee who uses Word himself shows you how to insert your picture or digital photo into a document and format it the way you want. He addresses questions about terms like "inline" and "floating," and explains how easy it is to set up a watermark.

Do you have a Sciphone? With its internet capabilities, you can check your email or surf the web. Take a look at this instructional video and learn how to set up your internet on the Sciphone 168. In order to set it up you need to contact your service provider for information such as an IP address, etc.

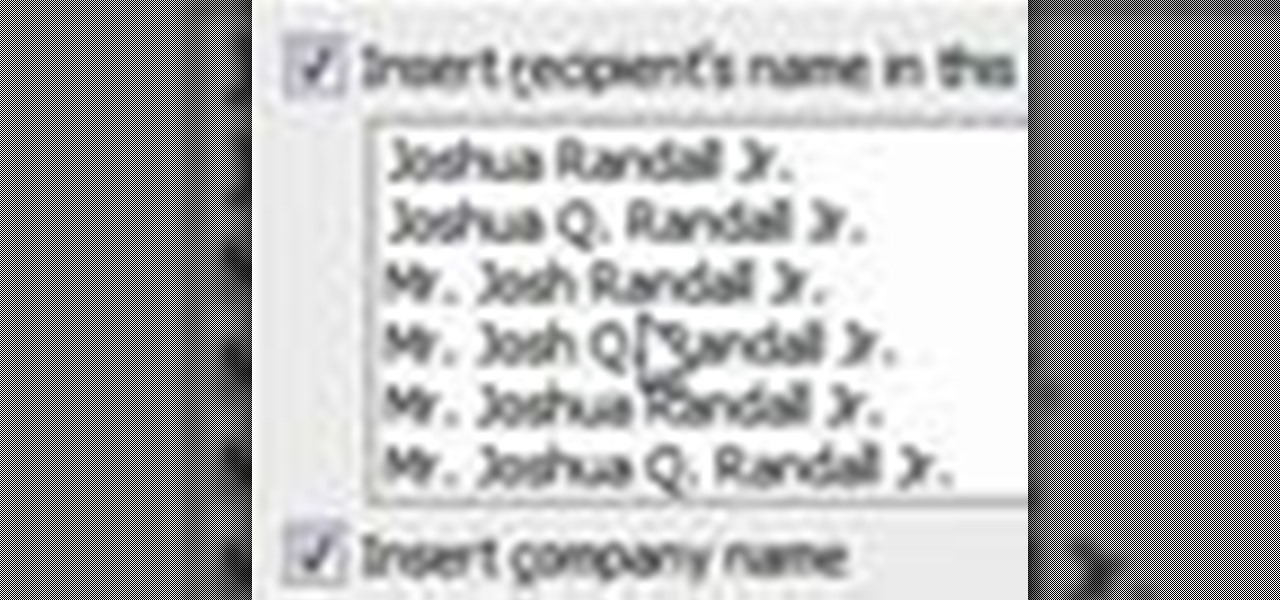
This video shows how to set up a mail merge in outlook which allows you to create a document then send it to your address book. A great tool in Outlook

Make copy-and-paste chores a snap with this quick Firefox tweak from Tekzilla. Just type about:config into the address bar, find "middlemouse.paste," the double-click on the value to change it from false to true. That's it. Anything you cut in Firefox you can paste back into Firefox by clicking on the scroll wheel in-between the buttons on your mouse.

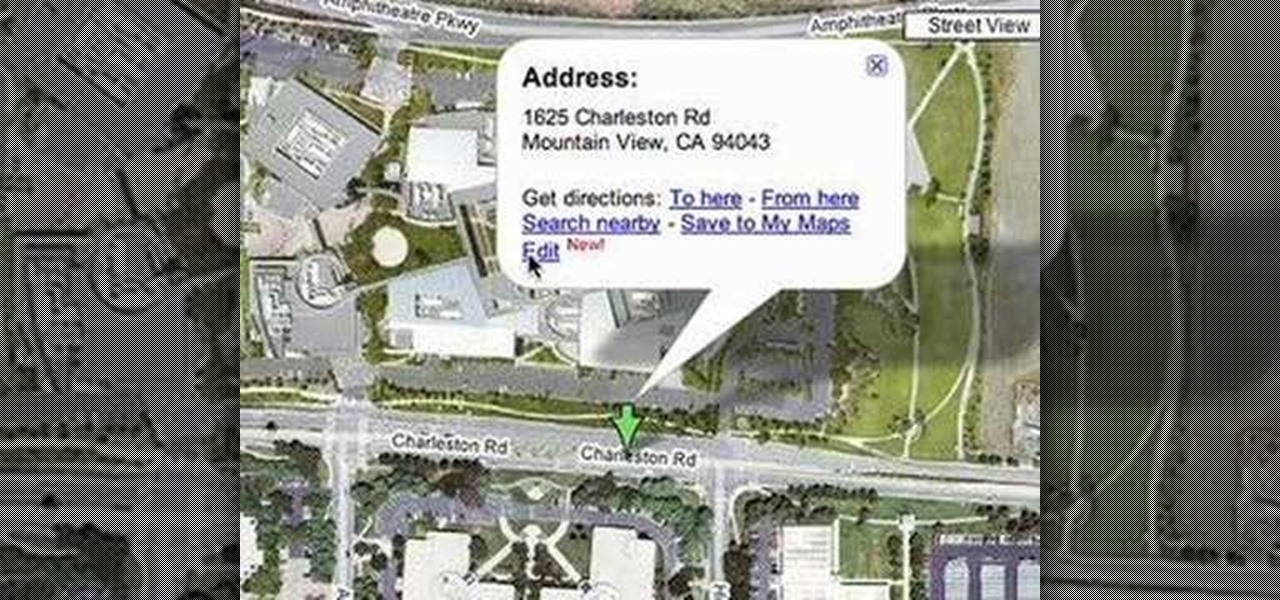
Now you can edit the physical location of any address in the US in Google Maps. You can correct your home, your business, or even your favorite park. Try it at maps.google.com

Segment on how to season a metal untreated wok from the Master Chef Apprentice Training Package. Brought to you by WokFusion, this tutorial addresses the skill and preparation that must go into preparing Chinese food.

Tired of Windows and Mac OS? You might want to try Ubuntu or some other variation of the Linux operating system. The Lab Rats, Andy Walker and Sean Carruthers, teach you how to install and run Ubuntu on your system. They also address several concerns you may want to be aware of.

There's such a variety of massage styles to choose from today. Take Shiatsu and Thai massage. They're based on traditional Asian medicine, and are designed to address aches and pains, but are also aimed at balancing the energy of the body to improve health and well-being.

In this economy being competitive for a job means your application must stand out above the rest. Here's how to write a cover letter to successfully introduce your resume. Make sure your cover letter follows business letter format. Your name and address must be written at the top left corner. The employer's name and address are written just below. The letter should be addressed to a specific person within the company. Paragraphs in a business letter are not indented, but instead are left just...

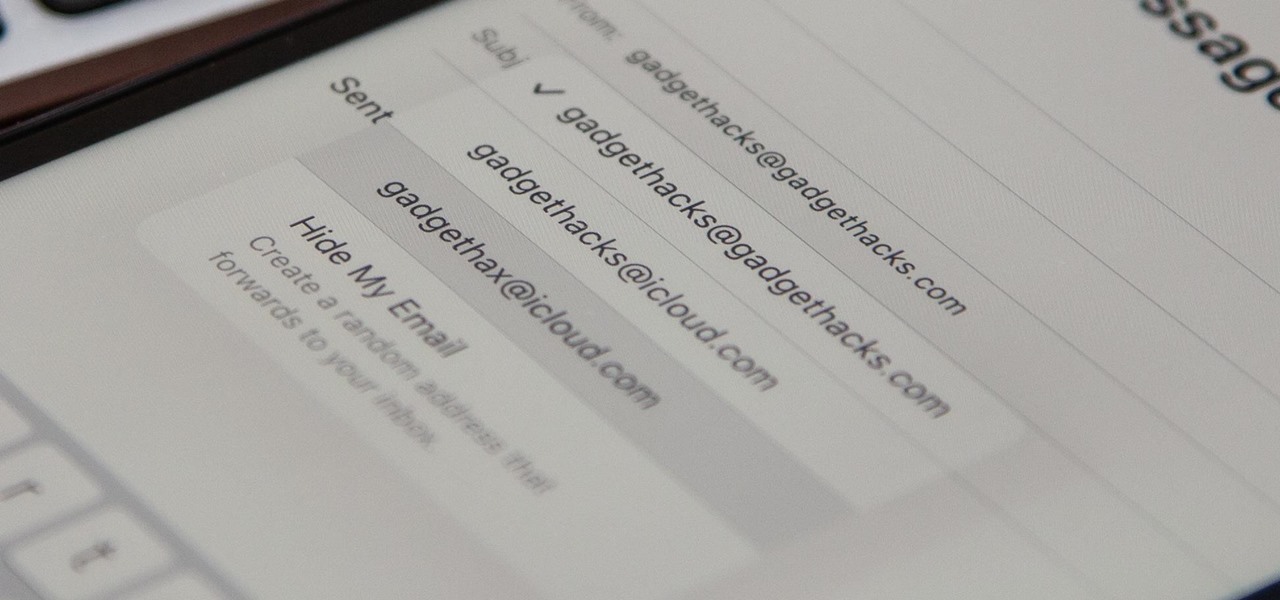
On your iCloud Mail account, you can easily use subaddressing to create hundreds of new iCloud email addresses to give to companies and other parties, all of which go straight to your primary iCloud email address's inbox. The problem with these types of alternative email addresses is that you can't ever respond to emails with the plus tag intact. But Apple has another alternative for you to start using.

For the most part, Google Wifi and Nest Wifi systems take care of themselves. But there are still a few manual features that might come in handy, like being able to check on network activity to see which devices are using the most bandwidth when your connection gets bogged down.

When it comes to sniffing Wi-Fi, Wireshark is cross-platform and capable of capturing vast amounts of data. Making sense of that data is another task entirely. That's where Jupyter Notebook comes in. It can help analyze Wi-Fi packets and determine which networks a particular phone has connected to before, giving us insight into the identity of the owner.

Most of us have had a cloud-connected address book for years now. The result of this is an ever-growing contact list that will continue to get harder to navigate and manage. With the increased size of our contact lists, it becomes more important to sort contacts in a way that works best for us.

With the imminent arrival of the HoloLens 2 expected any day now, Microsoft is preparing new users to take advantage of its software from day one.

Apple's Mail app has always been a stylish yet simple way to check and send emails. Third-party apps up the ante with powerful tools and features to help keep junk and spam mail out of your eyesight. But with iOS 13, you don't need them since Apple gave the Mail app some much-needed superpowers. One of those being the ability to block senders from emailing you.

If your iPhone XS or XS Max has been suffering from Wi-Fi connectivity and charging issues, Apple just released iOS 12.0.1 on Monday, Oct. 8, as an over-the-air update for all compatible iPhones. The main focus of the update is to give fixes for users going through "Chargegate" and experiencing Wi-Fi issues.

With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative.

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.

Instagram can be pretty exact when it comes to where you are located. That's why, sometimes, it's best never to geotag your precise location, but a broader area where you are less likely to get, well, um ... stalked?

Google's personal messaging service Allo could reveal your search history and other private information to friends if the Google Assistant bot is called upon in chats, according to a story from Re/code.

A new iPhone exploit has recently been discovered by YouTube user videosdebarraquito, who has found many other exploits and bugs in iOS over the years. This new exploit allows someone to bypass the lock screen and gain access to contacts and photos via Siri, Apple's digital voice assistant—but it only affects the iPhone 6s and the iPhone 6s Plus because it requires 3D Touch functionality.

In this how-to we will be sending an email with an image we get from a php script after running some fishy code. What you'll need

Before I get ostracized by all of you whisky lovers who live and die by whisky served neat, let me say my piece.

Unless you've been living under a rock or ignoring recent news headlines, Ashley Madison, the dating site for married people (or individuals in a committed relationship) has recently been hacked. Millions of their users are shitting their pants, and for good reason, as all of those accounts have just been leaked.

Welcome back, my novice hackers! Episode 6 of Mr. Robot has come and gone and, as usual, it did not disappoint. Once again, our hero, Elliot, has used his extraordinary intellect and hacking skills to awe and inspire us.

Smartphone users often wish for a privacy, where no one is able to poke his/her nose in their personal stuff. Unfortunately, none of the smartphones have been able to guard their privacy in this fashion. Smartphones usually come up with none or almost negligible built-in security to serve your purpose.

In the wake of the NSA scandal and celebrity-photo hacks, lots of people scrambled to find more-secure ways to send text messages, share emails, and surf the internet. Known for their incredibly secure data networks, Germany's email services saw a remarkable increase in new users from across the world. Last year, we covered Sicher, a German app that lets you send and receive encrypted self-destructing messages on your smartphone.

Getting caught using your iPhone at school or work (when you're using it for personal reasons) can be a little bit embarrassing. Even worse, it can be detrimental to how you're perceived by your teacher or boss. But sometimes you just have to beat that next level of Candy Crush, view a risqué photo on Snapchat, or send an important WhatsApp message.

I can be pretty forgetful. If there's something important to remember, I need to jot it down right away or risk losing it forever.

Spam emails are emails that are sent to you without your permission. They can quickly fill up your email account if you don't do anything about it. Each email server deals with spam in a different way. Gmail is good at separating the spam for you so that you can get rid of it more quickly. It is easy to delete the spam and if you want to take it a little farther, you can get some of the spam to stop coming all together.

When it comes to text documents and spreadsheets, Microsoft Office is the be-all and end-all office suite—but it's not cheap. Paying anywhere from $140 to $400 puts a big dent in your bank account, especially if you're a broke college student eating ramen for breakfast, lunch, and dinner. Something that I wish I would've known about during college is Microsoft's HUP (Home Use Program). With HUP, any employee or student of an organization that has a Microsoft volume license is eligible to purc...

Android has released a new application called ezNetScan, which is a free app that scans the wireless network you're connected to and gives you a full log of all of the devices connected to that network. This isn't new for smartphone users, let alone Android users. Fing has been around for a while and does practically the same thing that exNetScan does. It gathers information such as the IP and MAC addresses, device vendors, and ISP location. But while Fing is a great program, it does lack a f...

What's your Twitter handle worth? If it's considered "desirable" (aka short and simple), it'll get you around 100 bucks, or, if you prefer, the affections of a teenage girl.

Quilling is one crafting skill you probably picked up in fourth grade and then never touched again. But it's time to bring out those long paper strips once again. Quilling is one of the easiest ways to add complex and beautiful decorations to greeting cards and other paper projects.