PAT MONAGHAN is a professor at DePaul University in Chicago. She holds a Ph.D. in both literature and science. She is the author of "Dancing with Chaos," a book that expresses the complex ideas of chaos theory in poetry. The THEOSOPHICAL SOCIETY in America is a branch of a world fellowship and membership organization dedicated to promoting the unity of humanity and encouraging the study of religion, philosophy and science so that we may better understand ourselves and our relationships within...
There has been an update with the NES emulator, so you have to put the ROMs in the /var/mobile/Media/ROMs/NES folder, and not the /var/root/Media/ROMs/NES folder.

This video series demonstrates how to fold the origami model "Scorpion" that Robert J. Lang designed. Robert kindly gave me permission to make this video accessible to you. It is a complex design, so only experienced folders should attempt it.

There are several types of chords including major, minor, suspended and dominant. Watch this experienced musician as he explains the basic essentials of music theory such as understanding notes and beats in this free online video series.
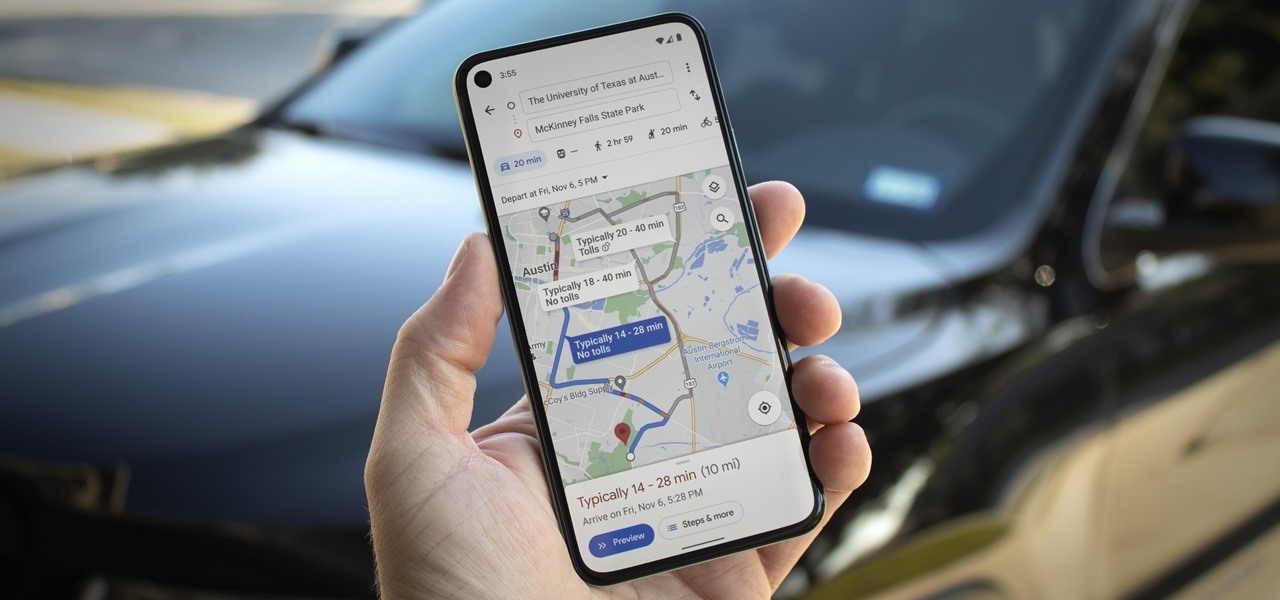
If you're in the market for a new house, how do you know what your commute would be like if current traffic is unseasonably low? Or if you're considering a new job across town and want to weigh the pay raise against the extra time stuck in a gridlock, how do you measure the discrepancy? Google Maps can help.

Creativity is one of our most unique features. We can dream up gods and demons and give them form through drawing. We can even take a two-dimensional surface and bring our ideas to life in three dimensions. It only takes a little training for our giant imaginations to blossom on the page.

From booting into Fastboot mode with a single command to installing mods without root access, there's no shortage of reasons to use ADB. The catch, though, you had to be tied to a computer with a USB connection. However, a new feature in Android 11 finally allows you to run ADB commands over Wi-Fi instead of being tethered.

The legal drama surrounding Chinese startup Nreal and Magic Leap continues, and now we finally have an update.

In case you thought the long and unfortunate story of ODG was over, hold on, there's one last chapter to tell.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

We are in the midst of a mini-boom for communications tools designed for augmented reality headsets, with the introduction of Avatar Chat and Mimesys for Magic Leap One and Spatial for the HoloLens within the last few months.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

Looking to inject a little more processing juice into your HoloLens? Unity can fix you up with the Standalone Universal Windows Platform Holographic Emulation.

Backdooring a powered-off MacBook is easy when a few minutes of physical access is allowed. That attack works well if the hacker also shares a Wi-Fi network with the victim, but this time, I'll show how to remotely establish a connection to the backdoored MacBook as it moves between different Wi-Fi networks.

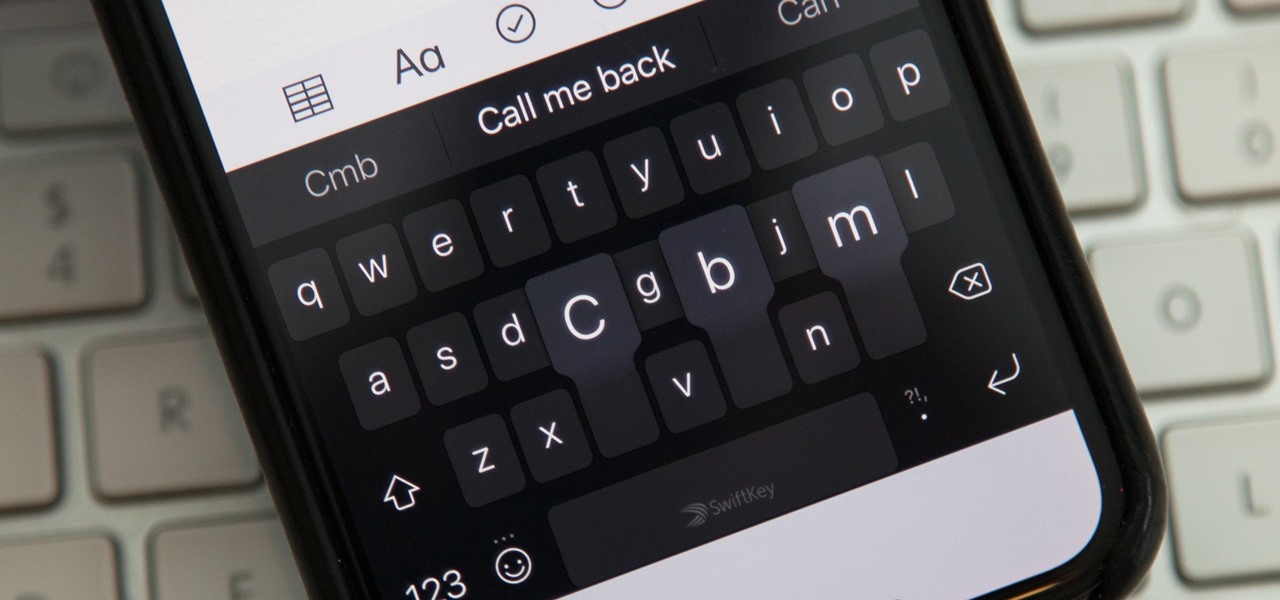
While you're probably already used to the keyboard on your iPhone, you'll likely never be able to type on it as fast as you can on a computer keyboard. But that doesn't mean you can't get any faster at typing on your iPhone. By using keyboard shortcuts to auto-populate commonly used phrases, email addresses, and other big-character items, you can drastically speed up your virtual keyboard skills.

If you've ever made graphs and charts, you know it can be a struggle to represent a large amount of data. It's something that just doesn't work very well on a flat surface. In virtual and mixed reality, however, the data can exist all around you.

Would you like to know what your next house is going to look like? With the HoloLens, you can just plop a hologram down in an open outdoor area and find out.

The human body is amazingly complex, and seeing inside one poses a variety of challenges whether you're dealing with an actual human or some kind of facsimile. Mixed reality offers the ability to get the best of both worlds by creating a holographic teaching tool for human anatomy.

In this series you will learn how to use PHP to perform attacks, gather information, and setup backdoors. Along with performing attacks you will learn how to protect yourself from them. In this part you will learn about PHP as well as install Apache and PHP. What you'll need for this series

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the victim portion of the shell. Today, we'll be building the attacker portion. This script will initialize interaction with the victim portion of the shell, send commands, and receive the output.

School internet filters serve a valid purpose—they keep students from wandering off into the deep corners of the web while still allowing at least some internet access. But a lot of these restrictions are completely ridiculous, to the point where some school districts block access to the educational material in National Geographic or forbid searching terms like "China," "Iran," or "Russia"—because, you know, breasts and commies.
Greetings null-bytians. Say you have been able to penetrate your neighbour's AP, and of course you had spoofed your MAC address. Now you go on and test to see with excitement if the password really works and the MAC is still spoofed. You login successfully and you browse the web forgetting to check what your current MAC is. Well, if you may do an ifconfig command, you will see that your permanent MAC is being used. Oh!! and guess what, ... your real MAC has been logged. Even though there is t...

Hello Elite Hackers! Welcome to my 3rd Post, which explains how to hack any account like G-mail, Facebook, etc.

Welcome back, my nascent hackers! In previous tutorials for my Wi-Fi Hacking series, I have shown you how to crack WEP and WPA2 passwords, break a WPS PIN, and create Evil Twin and Rogue access points. In this continuation of the series, let's look at slightly different approach to attacking wireless.

Seldom in recent history has a cyber security event caused so much media stir (maybe because it happened to a media company?) and international relations upheaval. Cyber security breaches seem to take place daily of major corporations, but the Sony hack seems to have captured the American imagination and, for that matter, the whole world's attention.

Video: . Extraterrestrial life is life that does not originate from Earth. It is also called alien life, or, if it is a sentient and/or relatively complex individual, an "extraterrestrial" or "alien" (or, to avoid confusion with the legal sense of "alien," a "space alien"). These as yet hypothetical forms of life range from simple bacteria-like organisms to beings far more complex than humans. The possibility that viruses might exist extraterrestrially has also been proposed.

Only a few months from its official September release, the iPhone 6 has been spotted in the wild again, giving us a better look at upcoming flagship device from Apple.

Welcome back, my hackers novitiates! As you read my various hacking tutorials, you're probably asking yourself, "What are the chances that this hack will be detected and that I'll land behind bars, disappointing my dear mother who already thinks I'm a loser?"

By Zech Browning Shihan of Gyodokan Martial Arts. Step 1: "Storm Within the Calm - Putting It All Together - Part 1"

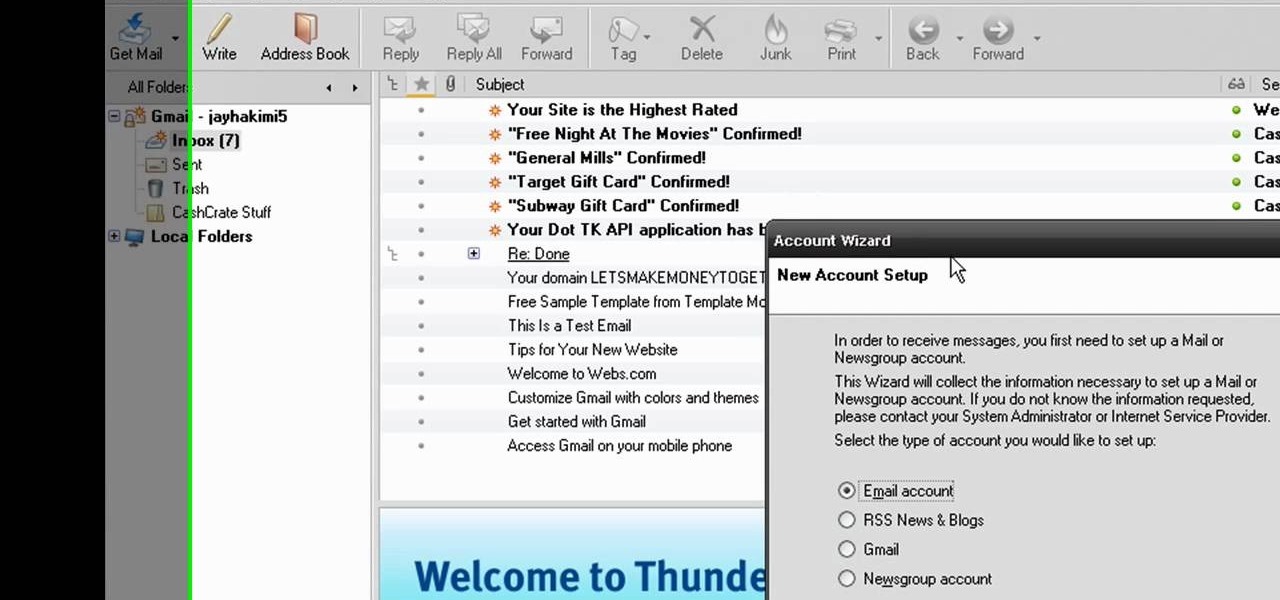
In this video from MegaByteTV we learn how to set up a Gmail account in Mozilla Thunderbird. First go to your browser and download Thunderbird from the Internet. Once downloaded, go to the Thunderbird application. Go to New and Account. Click on Gmail and enter your name and email address. Click Next and check off download messages now and click Finish. Your messages should now appear there. The first time you do this, all of your messages will look new but you can change that. If you'd like ...

You should encrypt everything. These are what you need: BackTrack 4,0, modify IP tables, Python and ARPspoofing. Program the PC to flip to forwarding mode. Adjust the programming in the IP tables. You are convincing the host and the client that the man (PC) in the middle is the host and capture passwords, user names and other information from unsuspecting clients. This program strips the "S" from "https" which make your computer vulnerable to hackers. You need to observe the address bar and m...

Google is the biggest and best search engine on Earth, and if you are a webmaster and want your website to be a big success it would really behoove you to know as much about how it works as possible. The Google Webmasters series of videos and website were created to teach webmasters, SEO professionals, and others how Google works by answering their questions and giving them insights into how they can best integrate and utilize Google's functionality to improve their business. This video will ...

Jordon Schranz brings you this tutorial on drawing. Search WonderHowTo for Sessions Online School of Fine Arts for more drawing tutorials. The technique & craft of drawing isn't necessarily about inherent talent, it is something that comes with lots of practice. It is all about being able to accurately record what you see.

Fixing your Aviso Carbon Fiber surfboard is just as easy as fixing your old poly surfboard. You can remove the drain plug. Dry it out completely. There is no foam to rot or wood to break. If fixed properly Aviso surfboards will keep all of there integrity. This addresses a puncture and a cracked and severely damaged rail.

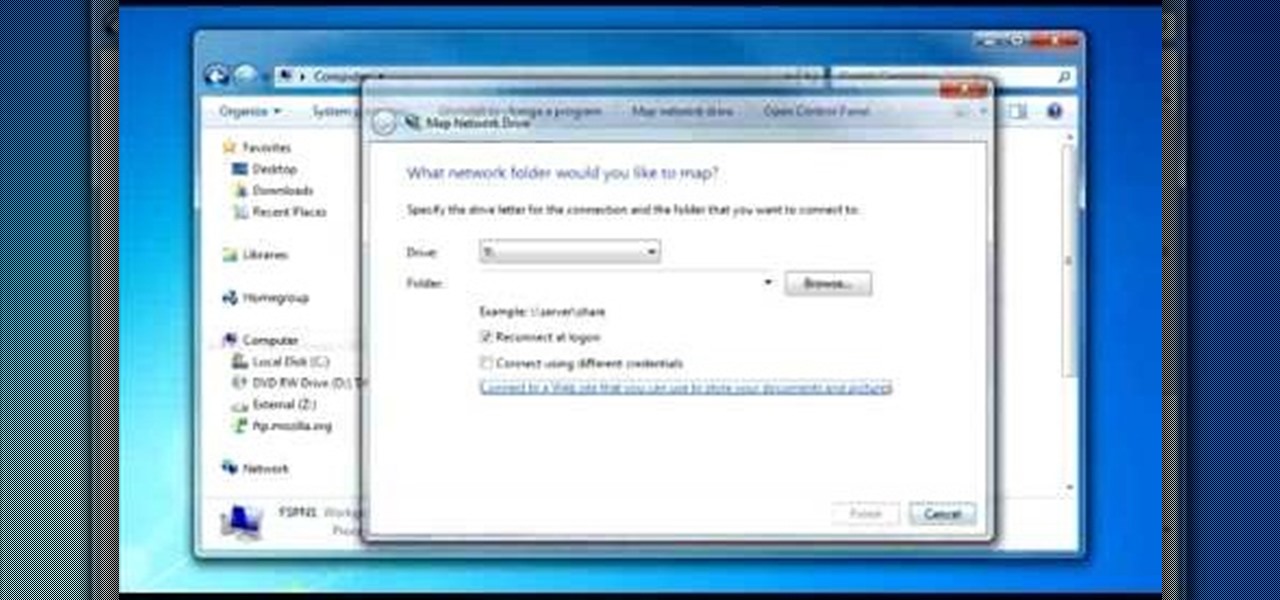
To do that click on tools in windows explorer and choose map network drive. Now click on "connect to a web site that you can use to store your documents and pictures" and then click on next and next. Now you have to type your internet or network address for example you type ftp://ftp.mozilla.org. This is a public server and it does not require a user name or password. Now click on next and there make sure you selected "log on anonymously" but if your server require a password then you have to...

In order to set up a secure wireless router, you will need to use the security that is available with your wireless routing. You will need to change the default ID names and password on your computer. Try to make sure that your passwords are difficult. Also, turn on the encryption: e.g. WEP.

Before you attempt this firmware install, if you have already installed custom firmware on your PSP this measure might brick it. Don't double install if you have already hacked your PSP.

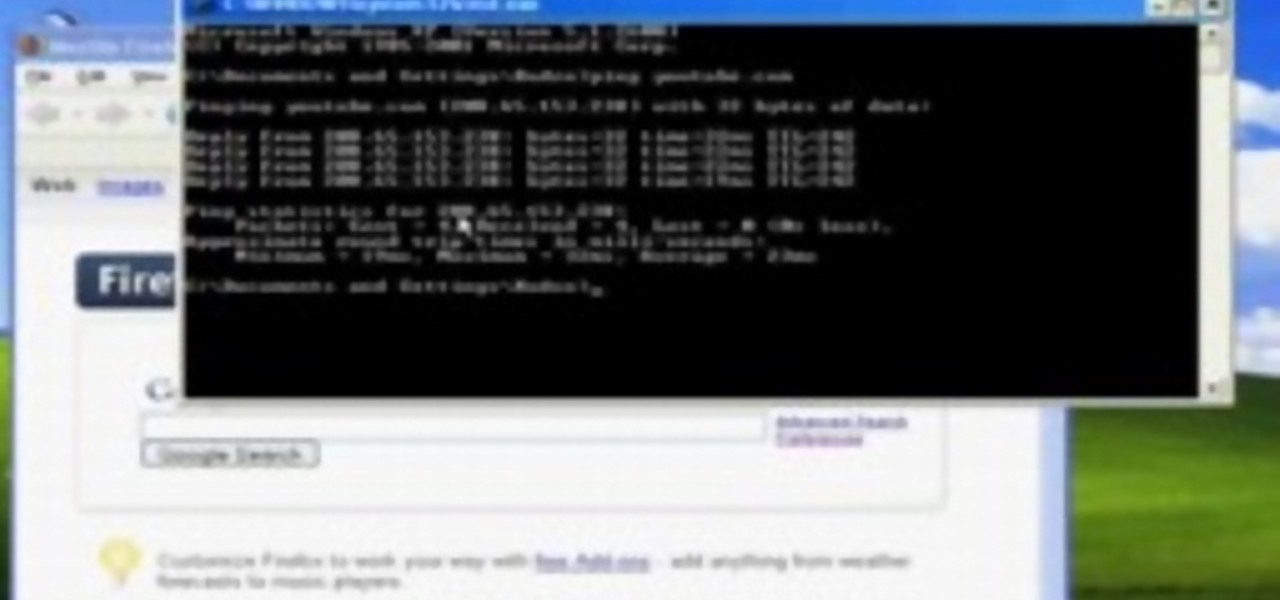
Get past your school's web filter without having to use a proxy server. Through the Start Menu, run the 'cmd' program. Then type in 'ping' plus the name of the site you want to visit. This will give you the IP address, which you can then use to get directly to the site you want to visit.

In order to block websites on your computer, you will need the address for the website that you want to block. Gather that information first. Then, click on Start. Then, go to Run. Next, type in the following: c://windows/system32/drivers/etc. Click OK.

This video tutorial from izbyfl shows how install Google Chrome and enable its plugins in Ubuntu. First download application from here: http://www.google.com/chrome/intl/en/eula_dev.html?dl=unstable_i386_deb.