In this video from rscp1050 we learn how to SSH into a jailbroken ipod touch or iphone. First go into Cydia and search for SSH. You need to download OpenSSH. Then also install Toggle SSH. After installed, restart the iphone. Now on your computer, download WinSCP. Once installed, open it. Type in your IP address which can be found by going to your settings on your iphone. Click wifi, and click the blue arrow next to your network. There is your IP address. Then, User name is root. Password is a...
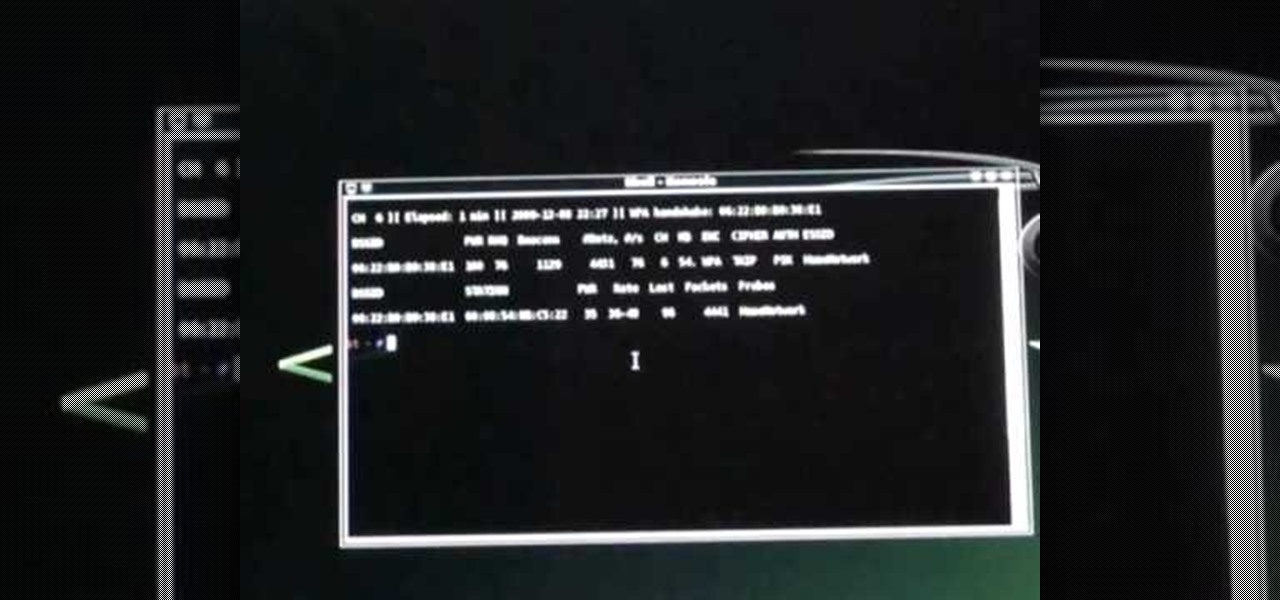
In this video we learn how to crack WPA using Back Track. The first step is the boot into Back Track using a VMware Virtual Machine Image. Next you need to open a shell console. In the console you will type "airmon-ng" and press enter. This does a check to find the wireless guard interface name. Next, type "airodump-ng wlan0" and press enter. This will tell it what wireless card to use and scan for wireless networks. You are looking for the one that comes up WPA. Copy the MAC address then typ...
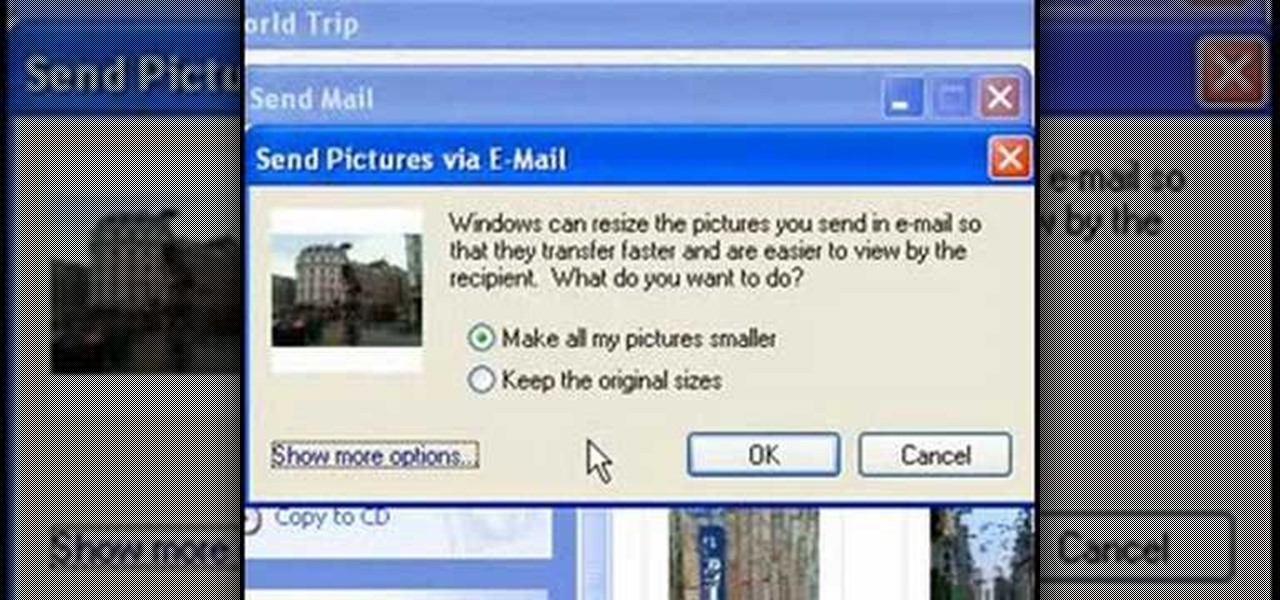
This video tutorial from easycomputercoach shows how to easily attach pictures to email addresses. In Windows XP you can send pictures resizing them in the process, in case you have large file sizes.

This video tutorial from iTouchMaster2 shows how to SSH to iPod or iPod Touch using FileZilla application.

Steps to Configure Your Modem/Router are: 1. Open Network connection and click properties
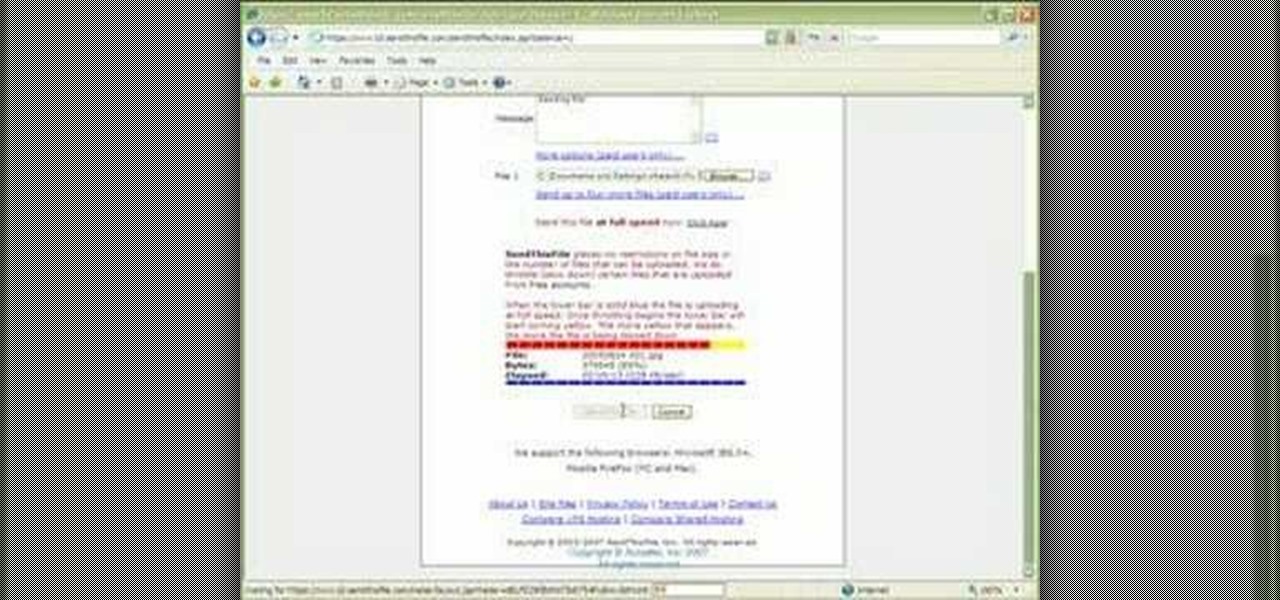
1. Type in WWW.sendthisfile.com in the web toolbar and press enter 2. Click on Register found on the top right side

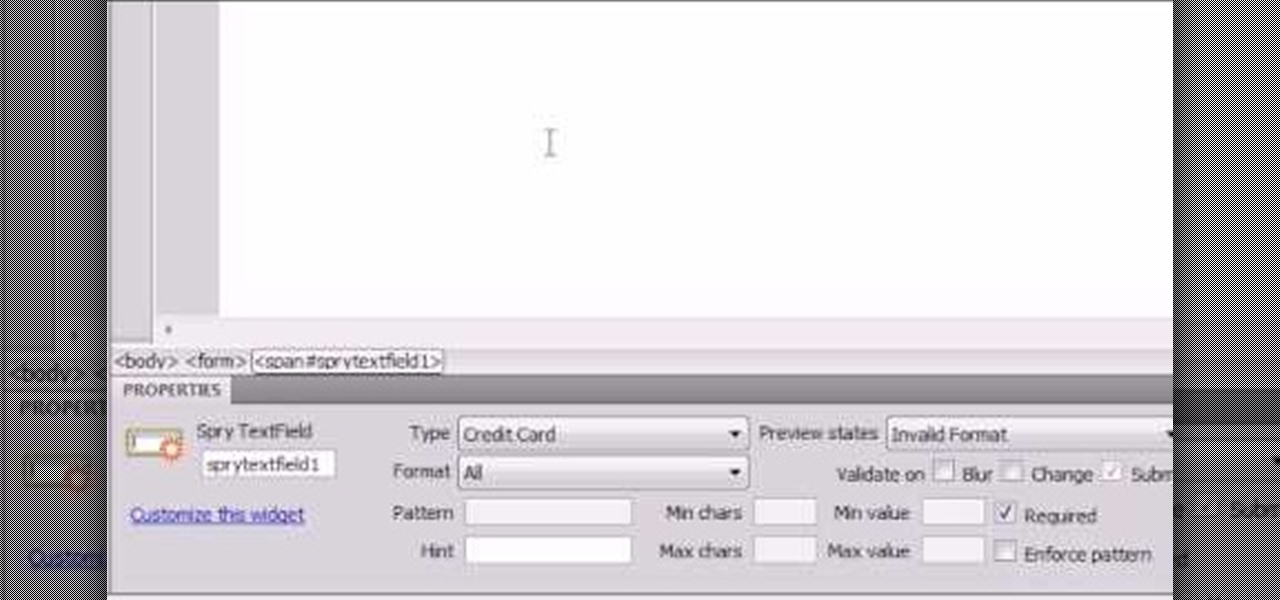
Here the New Boston shows you some tips about using the Spry Validation Text Field. To begin you will go to the Spry Validation Text Field, on Dreamweaver CS4. Looking at the bottom of the page notice the various options that are available for Properties. You find drop-down boxes for Type, Pattern, Minimum or Maximum values, Required, Enforce pattern, Format, Validate on, Blur or Change and Preview States. You can see the types of text available for validating by left mouse clicking the Type ...

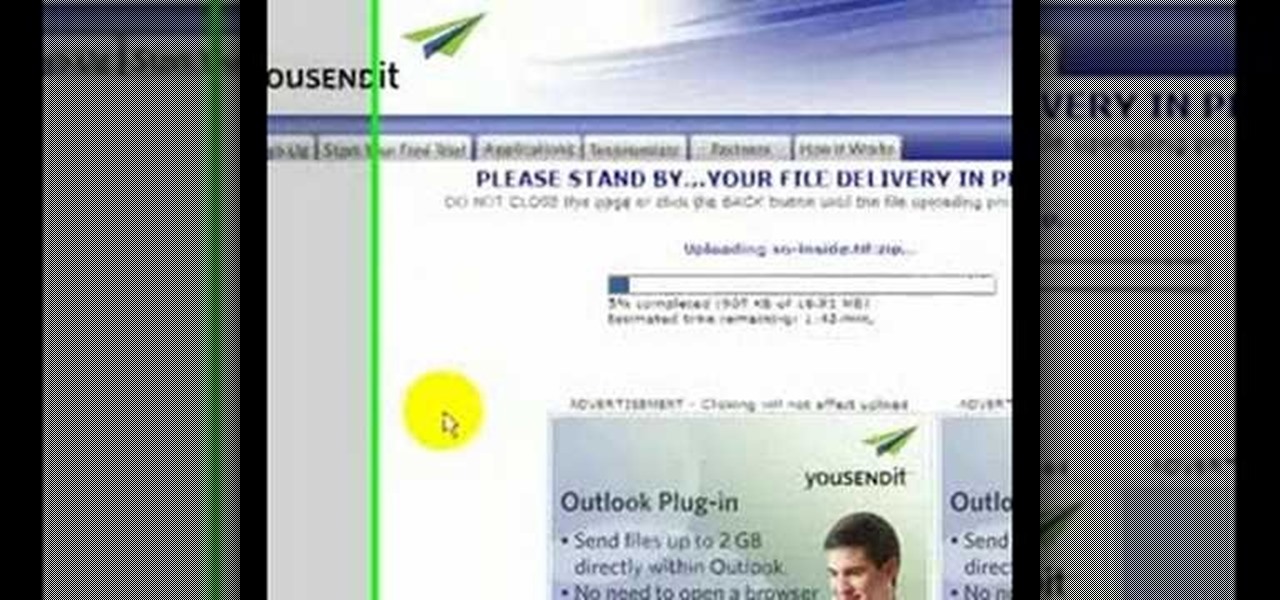
This video shows you how to use the online file delivery service YouSenditIt.com to send a file to someone. There are two ways to do this. One is to register for an account and send a file, and the other is to do it directly from the interface that you'll find on the website. You don't have to register, but generally if your file is going to be larger than 20 MB the person on the receiving end will need to register. But in this video we're shown how to send a file from the interface you're pr...

In order to create a custom caption box in WordPress you'll need to go to your dashboard. Here click on appearances, then on editor. Now over on the right select the sidebar option. Here you'll see some code, what you need to do is find the word that you want to replace on the main page, you can use ctrl+F to find the word. When you've found it within the code just replace it with whatever you want and then press the 'apply' button. You'll see that the main page will now be displaying the wor...

This video shows the method to SSH into iPod Touch 1G or 2G. You need an iPod touch 1G/2G with Firmware 2.2.1 or previous (Windows), a Windows based computer and a jailbroken iPod Touch which has Wi-Fi connectivity. Open Cydia, go to search and type OpenSSH and install it. Go to settings, Wi-Fi and click on the blue arrow next to the network. Copy down your IP address from the resultant window. Open WinSCP.net and go to Downloads, installation package. Install the package and open WinSCP from...

This is a javascript trick that will work on any website. Just go to the webpage you would like to view go bananas, erase the url from the address bar, insert this code into the empty address bar, hit enter, and enjoy:

It seems like its hard to get as much sleep as we need, doesn't it? Sleep is important and effects how you function throughout the entire day. Follow these tips and you will be on your way to a good night's rest.

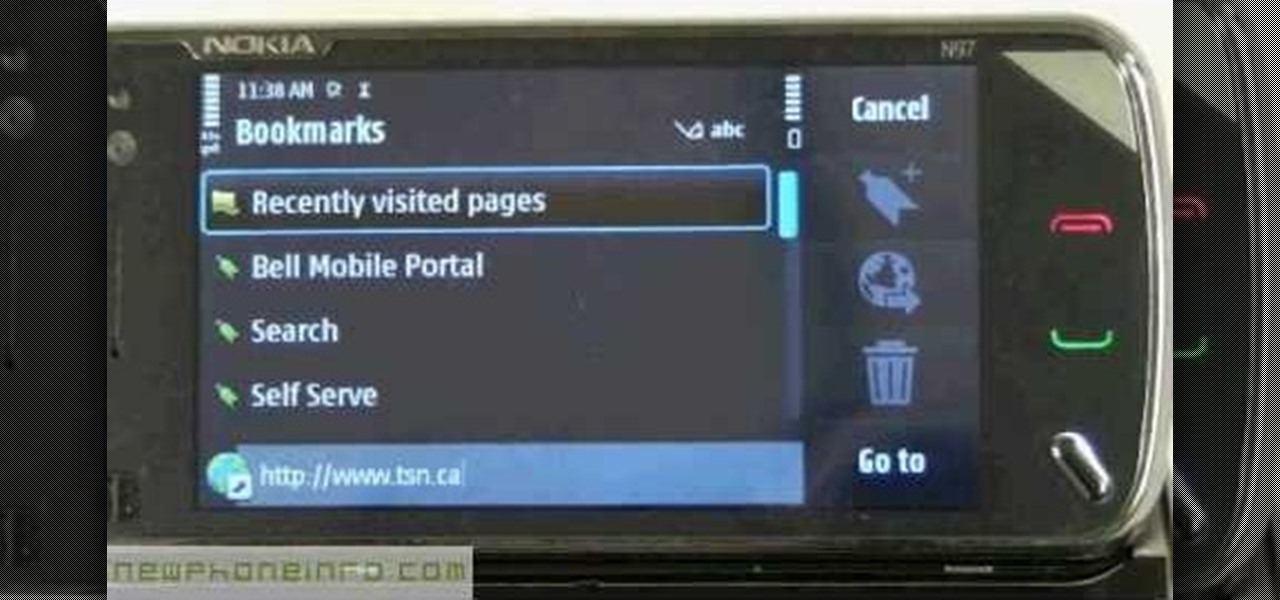
If you want to know how to use the web browser on your Nokia N97, you should watch this video. On the home screen, tap the Web icon. Bookmarks screen appears. On the right side of the screen there are icons present namely: Exit, Add Bookmark, Go to Web Address, Delete, and Options. Type in your desired URL and tap Go To after tapping the Go to Web Address icon and a URL textbox appears at the bottom. Wait for the webpage to load. If you want to display some options, tap the Expand Sidebar ico...

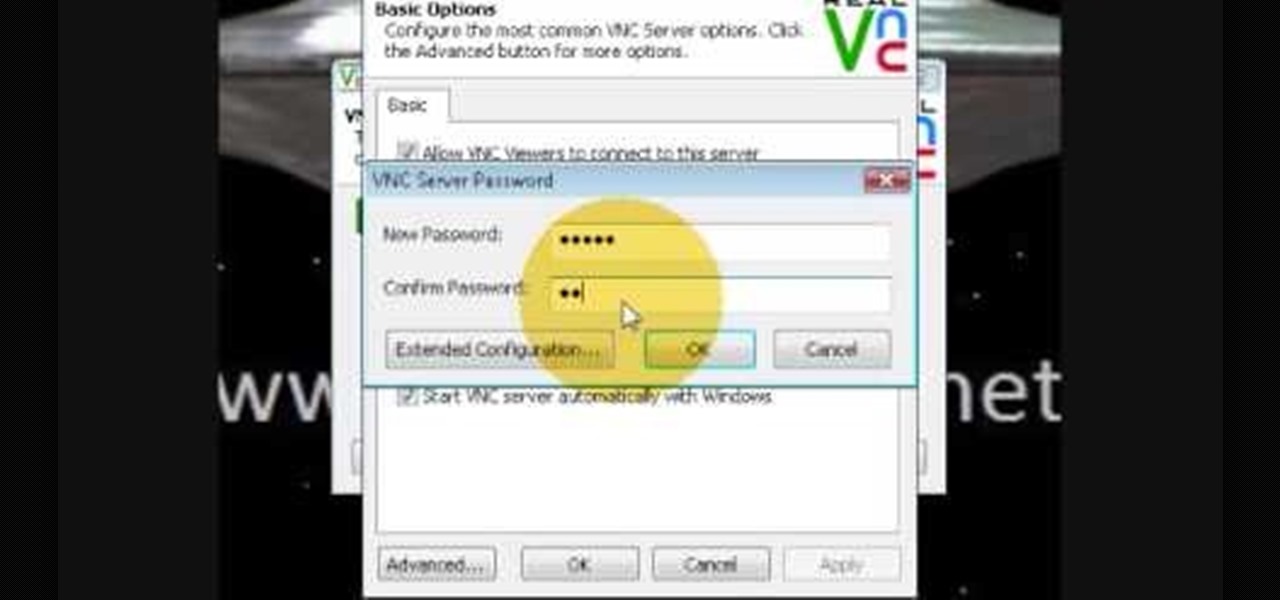
If you want to know how to monitor another computer screen with Real VNC, you must watch this video. Install Real VNC in your computer and computer that you're going to monitor. Remember the folder where you installed it and check the "Create a VNC Viewer desktop icon" checkbox. Write on a paper the IP address of the computer that you're going to monitor. On the VNC Server Status window, click Configure button. On the Authentication field, select VNC password and on the Encryption field, sele...

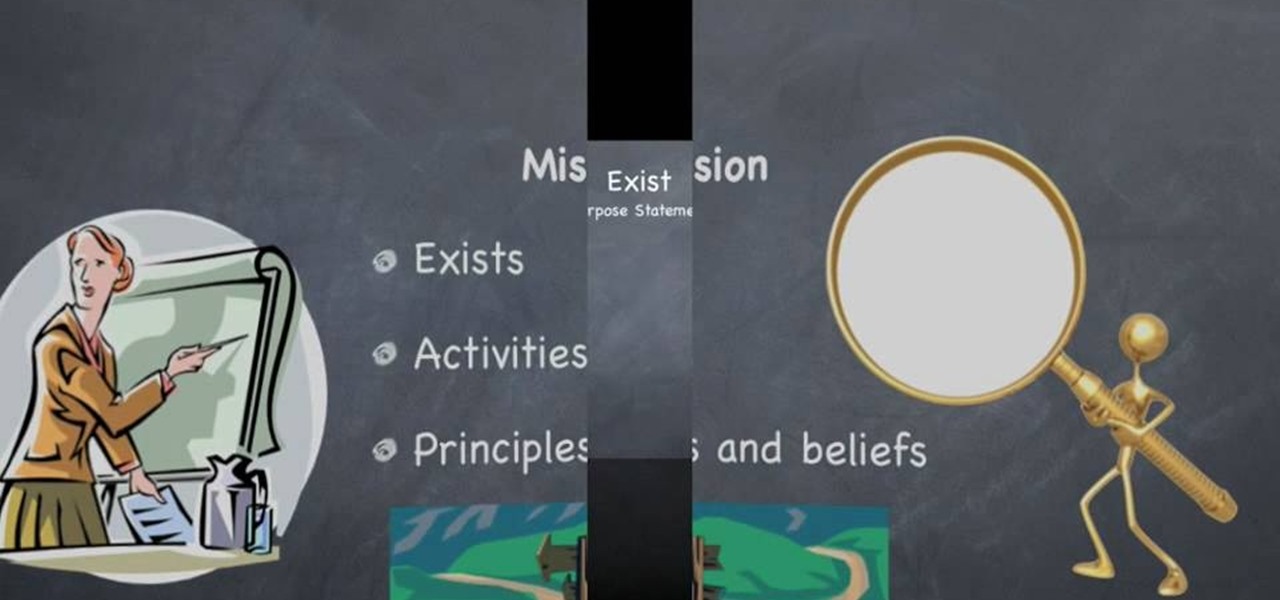
Award winning author Susan L. Reid teaches us how to write a great mission statement for your business. 1. First, write your "purpose statement". This answers what your business wants to accomplish and what problem or need your business is trying to address. Simply state the answer to this question. 2. Write your "business statement'. This describes the activities or programs your business must do to support it's purpose. Ask yourself what you are doing to address the need identified in your ...

This how-to video explains how to copy and paste text in the browser in a Motorola Droid phone.

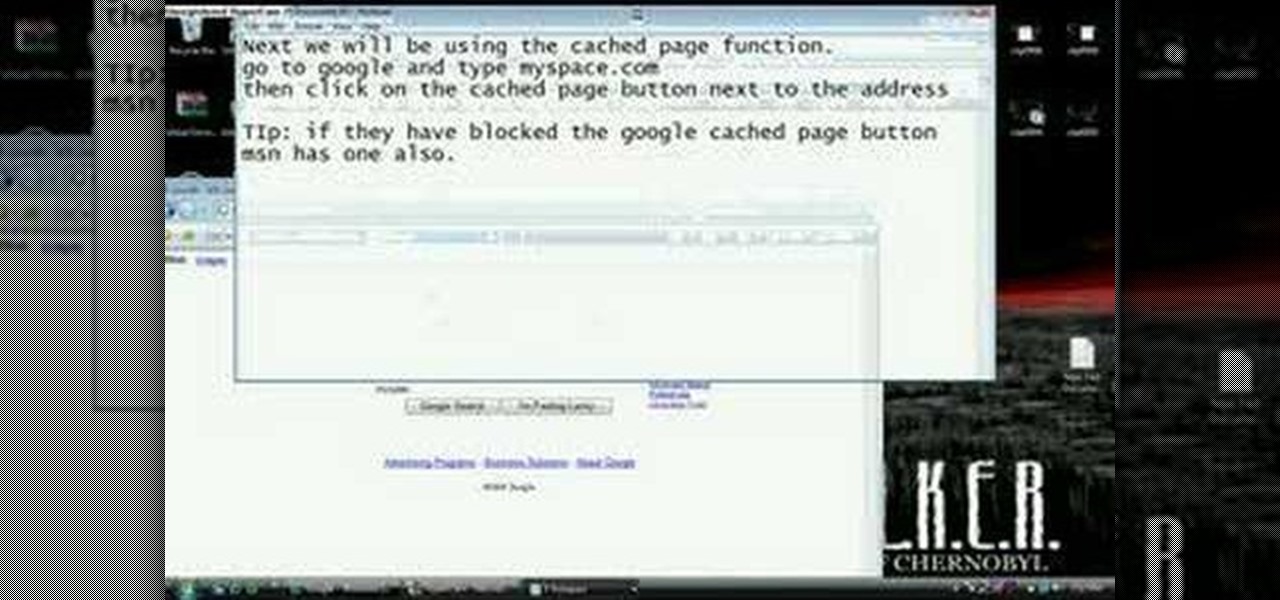
Nowadays many schools and colleges have blocked the social community sites from accessing them through school computers. The video shows how one can access to these sites using a command prompt.

Having trouble coping with the fact your son picked a less than stellar choice to marry? Not too fond of your son’s taste in women? That’s his problem; don’t make it yours.

Attention aspiring screenwriters! In this tutorial, learn how to sell that script. You may have written the next Hollywood blockbuster – but unless you can finance the film yourself, you’ll need to sell the screenplay to a producer who can make it come to life.

Thanks to the Freedom of Information and Privacy acts, we’re all entitled to see what the FBI has on us. Learn how to get your hands on your FBI file.

Job applications should be taken seriously, and filling them out with correct information, as well as specific details that make this application stand out, is an art form. Fill out job applications with tips from a career adviser in this free video on job guidance by following the instructions of the application, making it legible and addressing the value the applicant will bring to the company.

In this video tutorial dedicated to the Google's Gmail, you'll learn how to set up Gmail to retrieve mail from a second email account. This tutorial also looks at how to set up labels and filters, and explains the Gmail Archive function and Gmail Conversations. Become an advanced Gmail user with this video tutorial!

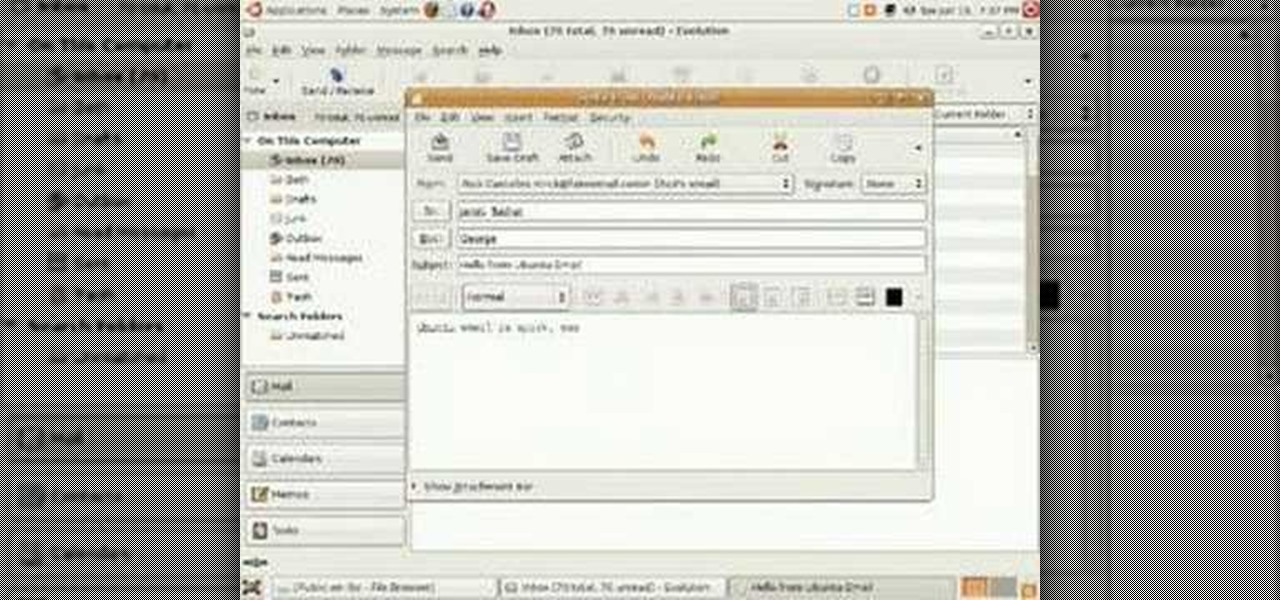
Sending email with the Evolution client in Ubuntu Linux is much the same as with any other email program. In addition to offering step-by-step instructions for the setup and use of Evolution, this Ubuntu tutorial also will teach you how to access your address book when writing an email. For a detailed look at the Evolution email client, take a look!

You can have as many iPhone e-mail accounts as you have addresses. Watch this iPhone tutorial video to learn how to add multiple email accounts to your iPhone. This how-to video is intended for new iPhone owners.

Watch this helpful electronics tutorial video to learn how to quickly access the Safari address bar on an iPhone. This how-to video, geared primarily toward new iPhone users, will make using quick URLs to browse the internet on an iPhone very easy.

A tutorial showing how to set up a free dynamic DNS address with DynDNS.org and configuring the home router/firewall to forward traffic to your webserver.

The first of a two part series on setting up your linux server and network for external access through your cable modem or DSL. Covers modifying the Linux servers network setting to a static IP address.

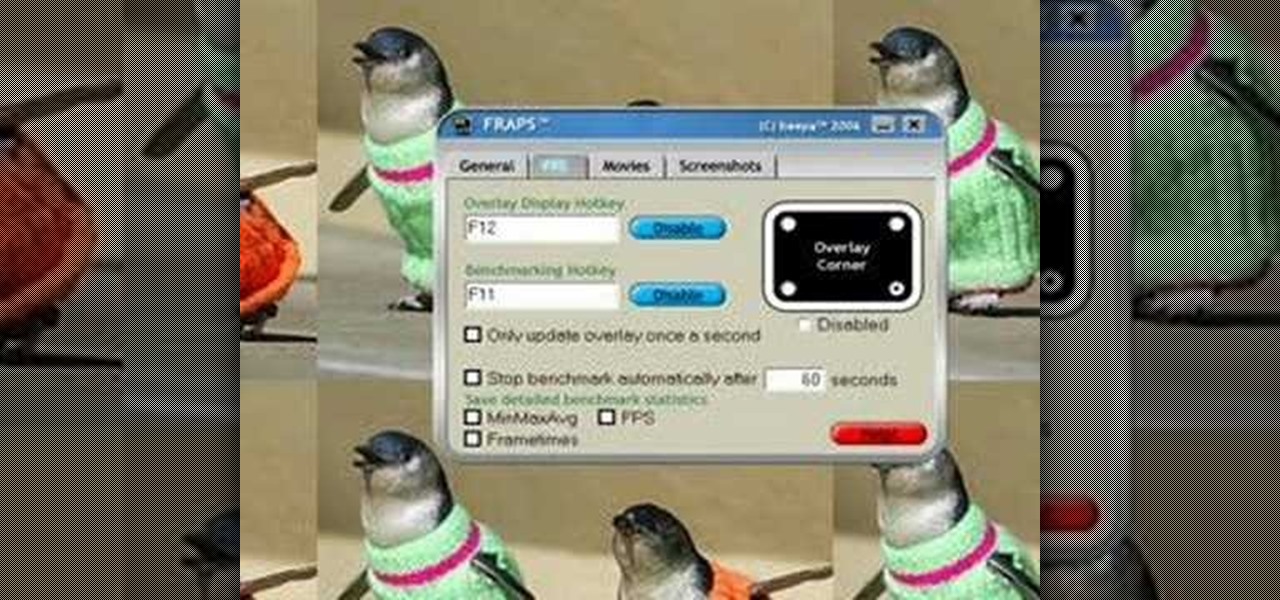
This tutorial details how you can use a program known as FRAPS to record your video games. The second video in the sequence details questions not addressed in the first video.

This is an awesome liquid dancing tutorial for novices, focusing on tips and addressing common mistakes. Stick to the rhythm

This video addresses the consonants of Hindi from velars to retroflexes, including the writing system (devanagari script). It is concluded by part 4 (b). Please watch the videos on Hindi phonetics before this part.

Dave shows you how to address problems with grubs which can destroy your lawn.

In this video, Jonathan Cohen demonstrates how to surf the web using a BlackBerry 8800. The explains how to start up the Internet on the cell phone, how to input an address, and give some hints on using the browser.

As long as you're on the internet, you can be hacked. With an estimated 2.65 billion social media users, these apps are prime targets for hackers.

Are you here yet? When will you arrive? How long until you get here? How far are you? Hurry up! When you're meeting up with someone or a group of people, you may get flooded with messages like that. Instead of trying to answer them mid-trip, you can send them your status from Apple Maps, so they know precisely when you'll arrive, and they'll even get updates if traffic is holding you back.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

During our last adventure into the realm of format string exploitation, we learned how we can manipulate format specifiers to rewrite a program's memory with an arbitrary value. While that's all well and good, arbitrary values are boring. We want to gain full control over the values we write, and today we are going to learn how to do just that.

The dark web is an intimidating place for a newbie hacker, but it's a powerful tool once you've learned to navigate it safely. To help you out with that, this guide will cover some need-to-know information for traversing the dark corners of the internet while keeping your identity and data safe. (Hint: Using Tor is not enough.)

General Motors acquired Cruise Automation in March 2016 for a reported $1 billion (well, at least $581 million). GM President Dan Ammann made a point of being in the press release photograph with Cruise founders Kyle Vogt and Daniel Kan (see photo below). On January 19, 2017, Vogt posted on Twitter: "Took GM Pres. Dan Ammann for a ride in a Cruise AV."

When performing something such as a mass mailer attack on a company, sending executables usually isn't the best option. That's why, in this tutorial, I'll be teaching you how to code a VBA script macro into a Word document in order to compromise a system. Combined with a little social engineering, this can be a very effective technique.

In recent weeks, major bank websites around the world have experienced outages after being have been hit with Distributed Denial of Service (DDoS) attacks. Although few, if any, of these banks have been totally knocked offline, these DoS attacks have dramatically slowed the response time of their websites to legitimate customers. The most recent victim was the Royal Bank of Scotland. Due to this attack, RBS customers were unable to access their accounts for about an hour last week.