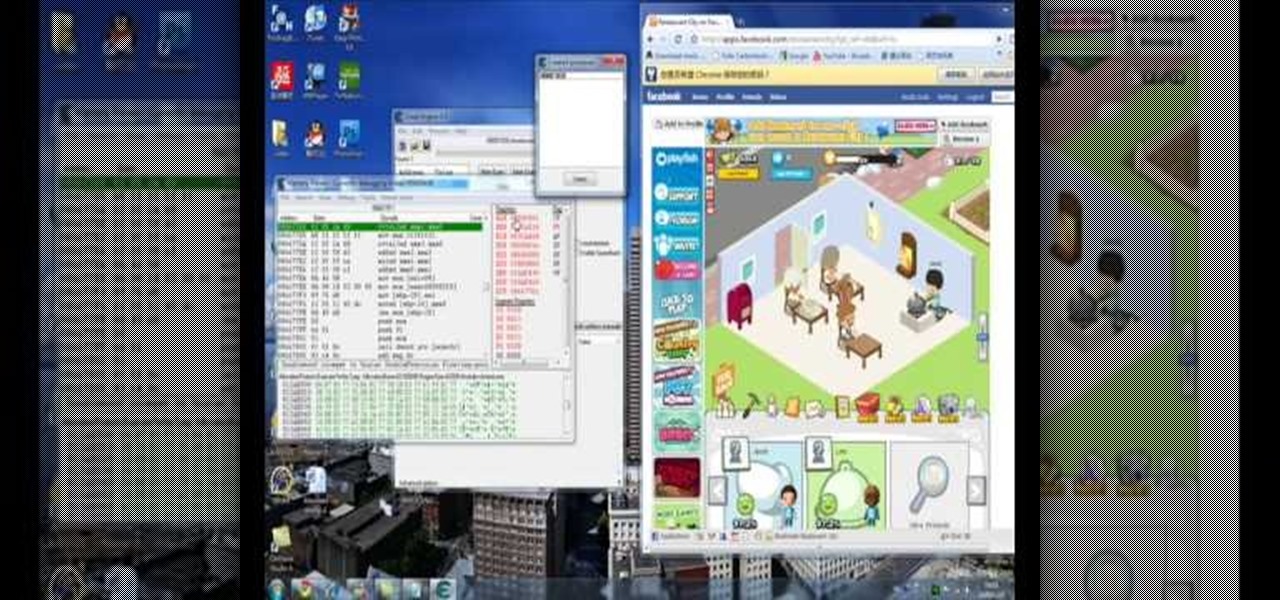
How To: Hack levels in Restaurant City (12/05/09)
Open up Cheat Engine and be prepared to hack Restaurant City! This is a new level hack that will help you gain levels fast.


Open up Cheat Engine and be prepared to hack Restaurant City! This is a new level hack that will help you gain levels fast.

This video address the "My RC does not work... fix it" questions that I get. The main issue is that people do not understand how to break the rc into segments and troubleshoot or diagnose off of that. This video will show you how to troubleshoot on a basic level the nitro engine, glow plugs, mccoy, clutch bell, carb, shoes, spur gear, slipper clutch, transmissions trans tranny, brake, drive line dog bones dogbones, cvds, diffs differential pinions wheels, and other common parts that will not ...
Many educators and institutions are already integrating podcasting successfully into their curricula — with great results. Podcasting enables educators to use music and recorded audio to enhance learning. The addition of photos and video to podcasting allows educators to add a wide range of visual content to their teaching and address even more learning styles.
This is a short tutorial on how to use your iPhone as a remote control for your eeePC. First download touchpad from installer.app, as well as install VNSea if you don't have it.
This video series takes you through every step of building a building in SketchUp and is taken from chapter 4 of "Google SketchUp for Dummies" in case you want to follow along. PART 1 explains how to switch to a 2D view to get you ready to build the floor plan. It's a good idea to have accurate measurements of everything you want to build before starting this project. PART 2 familiarizes you with the tools available in SketchUp to help you create your floorplan. PART 3 shows you how to draw t...

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

If you have just purchased a new Ford Taurus, you may have noticed the new SYNC feature. SYNC is a GPS built right into your dashboard. If this is your first time using a global positioning system, you may need a few pointers. Check out this video and learn how to access step by step directions and get where you need to go.

This how-to video is about how to use command prompt to view the blocked websites at school. This step by step instruction will help one to open the blocked websites at school.

There're plenty of great ways to get traffic, especially this off-site optimization technique using classified ads to point website traffic back into your site itself.

We've already highlighted the importance of learning Microsoft Excel from a hacker's standpoint, but it's also just a good skill to have as you'll likely come across the number-crunching powerhouse at school and work, as well as in other areas of your life, such as budgeting.

Communication is an essential skill for successfully launching products. Whether you're developing the latest and greatest app or trying to get ahead of a large data science project, effective communicators are always in high demand.
The powers of the Nreal Light continue to increase incrementally with each passing week. Now, the latest feature added to the device is possibly the most requested feature for anyone who has tried the Nreal Light: hand tracking.
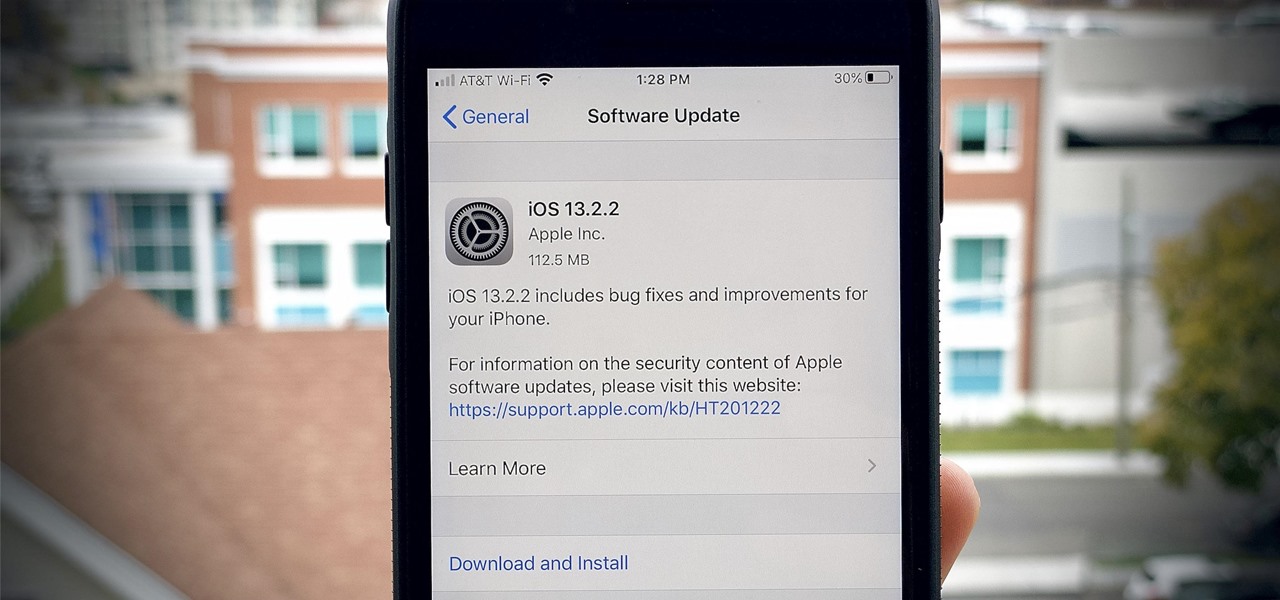
If you're a beta tester, you know Apple released iOS 13.3 this week, bringing with it stability for multitasking as well as minor changes throughout the OS. It seems Apple doesn't want the rest of us to go without this critical patch, as the company releases iOS 13.2.2 today, Thursday, Nov. 7.

If you have friends who aren't privacy-conscious, you've surely heard the old "What do I have to hide?" excuse. Despite the fact that billions of people are using the internet each day, many of them don't know the dangers that can find them. And many don't know the tools to combat them.

Apple might be a secretive company, but it's showing its hand these past few weeks. The release of iOS 13 was met with much excitement for its hundreds of new features but also frustration over the numerous bugs. Apple soon released iOS 13.1, then iOS 13.1.1, as a patch for some of those bugs, but clearly they weren't enough. How do we know? The company just released iOS 13.1.2 today, Monday, Sept. 30.

Businesses that have adopted enterprise-grade wearables for their workforces now have a new option among the multitude of AR productivity apps that can help their team members communicate in AR.
Featured on MTV's Catfish TV series, in season 7, episode 8, Grabify is a tracking link generator that makes it easy to catch an online catfish in a lie. With the ability to identify the IP address, location, make, and model of any device that opens on a cleverly disguised tracking link, Grabify can even identify information leaked from behind a VPN.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.

The latest business move by Magic Leap could result in a significant boost to its spatial computing platform's performance and headset design.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

A new app for iPhones and iPads gives developers a sandbox for testing their AR experiences and sharing them with the world.

Another entrant into the do-it-yourself AR content creation market has emerged, as Zappar has updated its ZapWorks Studio software to include features for development newbies.

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

Open-source data scraping is an essential reconnaissance tool for government agencies and hackers alike, with big data turning our digital fingerprints into giant neon signs. The problem is no longer whether the right data exists, it's filtering it down to the exact answer you want. TheHarvester is a Python email scraper which does just that by searching open-source data for target email addresses.

Today at Microsoft Build 2017 in Seattle, Washington, ScopeAR announced that their mixed reality smart instruction development platform, Worklink, will now work with the Microsoft HoloLens in addition to the mobile devices that are currently supported.

Sophisticated hackers have been exploiting vulnerabilities in Chrome and Firefox to trick even the most careful internet users into logging into fake domains for sites like Apple, Google, and Amazon.

While there are many uses for augmented reality in the automotive industry, adoption has been slow. With the plethora of makes and models on the road today and rolling off assembly lines tomorrow, developing and deploying knowledge bases that utilize augmented reality to dealerships and garages can be costly and difficult to scale.

If you've ever built a piece of IKEA furniture, you're familiar with the confusion that some 2D instruction booklets can create. But neuroscience suggests that they're cognitively overloading, as our brains have to translate their basic flatness into physical reality and that's pretty hard to do. Fortunately, augmented reality has come to the rescue.
While Leap Motion and Microsoft are looking to capture natural human motion with cameras, Enflux figured out how to do it with a shirt and pants that feel completely natural.

Google Maps, once considered superior to Apple Maps, has contributed to a terrible mistake for one woman. A group of demolition workers in Texas were using the service to find a worksite, and to the dismay of homeowner Lindsay Diaz, Google was entirely inaccurate.

Anyone who paid attention to the Lavabit shutdown had a feeling it was connected to Edward Snowden, the high-profile NSA whistleblower. Ever since the government's case against Lavabit went public in late-2013, people have put two and two together.

Welcome back, my rookie hackers! The Golden Fleece of hackers is to develop a zero-day exploit, an exploit that has not been seen by antivirus (AV) software or and intrusion detection system (IDS). A zero-day exploit is capable of skating right past these defenses as they do not contain a signature or another way of detecting them.
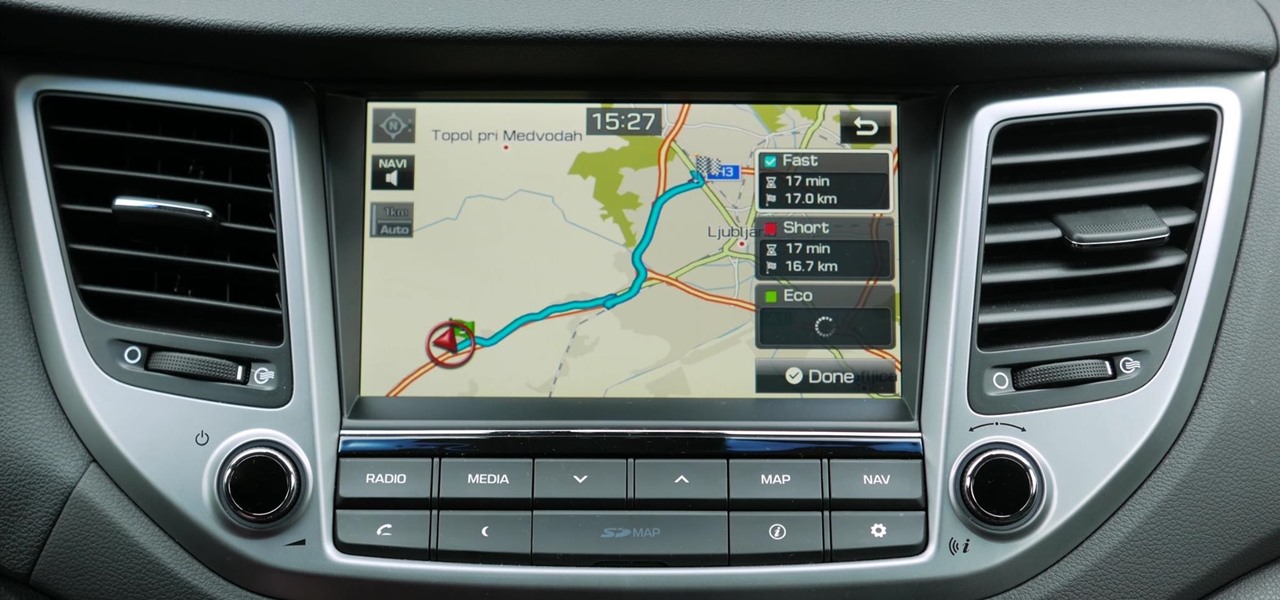
How to enter an address in the navigation (infotainment) system in a Hyundai Tucson (2015–2016 model, formerly known as ix35) as well as other Hyundai models with similar systems.
Google's design chief Matias Duarte has gained fame and acclaim for his recent visual revamp of the Android operating system, and now, Google's starting to incorporate this Material Design styling into more of its products.

This Is for the Script Kiddies: This tutorial is about a script written for the How to Conduct a Simple Man-in-the-Middle Attack written by the one and only OTW.

Welcome back to another tutorial on functions. Last time, we looked inside memory to see what functions looked like in the flesh and all that Assembly was pretty nasty. At least you have some exposure to it. This time, we will be examining how functions work with the stack.

Many websites are crowded with ads, pictures, and other irrelevant content that make it harder than necessary to read a simple article on your iPhone. In many cases, you have to zoom in just to get a better view of the text you're attempting to read—unless the webpage blocks zooming.

This tutorial is for those who've purchased an account with Private Internet Access to hide your VPN and would like to set it up in Kali. Please note, you can chose to run your PIA service from your Windows computer without configuring it in linux as long as you'll be using a NAT connection. Using a NAT connection will allow your Windows machine and Kali Virtual Machine to use the same IP address, hence if your IP is hidden on one, it will be hidden on the other.

Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement to solve cases. I am trying to demonstrate, in this series, ways that hacking is being used in these professions. For those of you who are training for those careers, I dedicate this series.

I'm sure you've been here before: sitting on an airplane, bored out of your mind, and you forgot to install a few games or download a movie before your flight departed. No worries, though. If you have the latest Chrome Beta installed on your Android, there's a fun little mini-game baked right into the "You are offline" screen.