Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

Leaked databases get passed around the internet and no one seems to notice. We've become desensitized to the data breaches that occur on a daily basis because it happens so frequently. Join me as I illustrate why reusing passwords across multiple websites is a truly awful practice — and compromise hundreds of social media accounts in the process.
Continuing to take the steps necessary to reign supreme among the top game engines of the world, with a steady stream of major updates, enhancements, and new features, the team at Unity are keeping the user base in a regular state of surprise. At this rate, it's almost like Christmas every few days.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.

before I move on to more exciting areas in this series, I want to also point out some things to protect your information & how to not get DoXed.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Welcome back, my aspiring hackers! As I mentioned in earlier posts, the best hackers (or at least those not behind bars) have a keen understanding of digital forensics. If I am tasked to intrude upon an enemy's file server to retrieve war plans, such as in this tutorial, it is essential to my country's (and my own) well-being that it not be traced back to me. Understanding digital forensics helps us to leave without a trace and never have a trail back to us or our employer.

Welcome back, my novice hackers! This next subject might seem a bit obscure, but I promise you, this lesson will benefit you significantly either as a hacker or system admin. This tutorial will cover what is usually referred to as a regular expression, or regex for short.

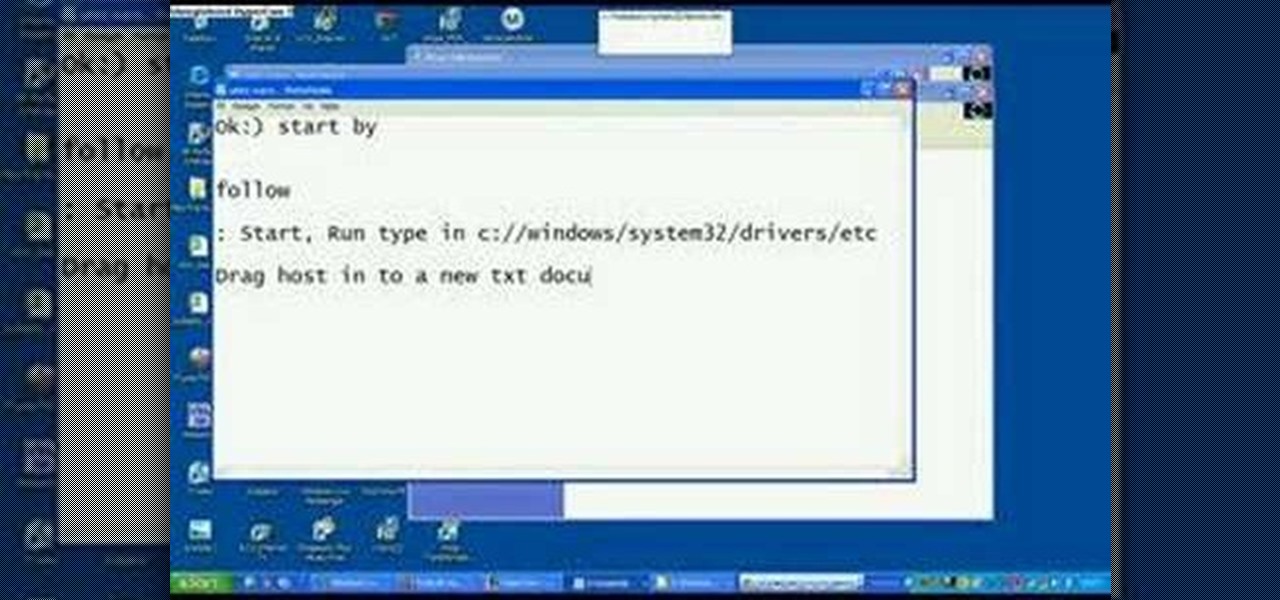
In this tutorial, we learn how to block a website. First, you will start by going to the start menu then go to "run". After this, type in "c://windows/system32.drivers/etc". After this, a new window will pop up on your screen. With this, you will drag the host into a text document. Then, type in the website that you want to block inside of this document. Once you are finished, type in the IP address of your computer next to that and save it. This will finish up the blocking of the website and...

In this video, we learn how to delete your Facebook account. First, go to your Facebook account and then go to your account options. From here, find the link on the page that will allow you to delete your account. Next, you will need to confirm you want to delete your account and enter in your password along with a Captcha phrase. Now, you will need to go to the e-mail address associated with the account and click on the link from here. With this, you will have completely confirmed that you w...

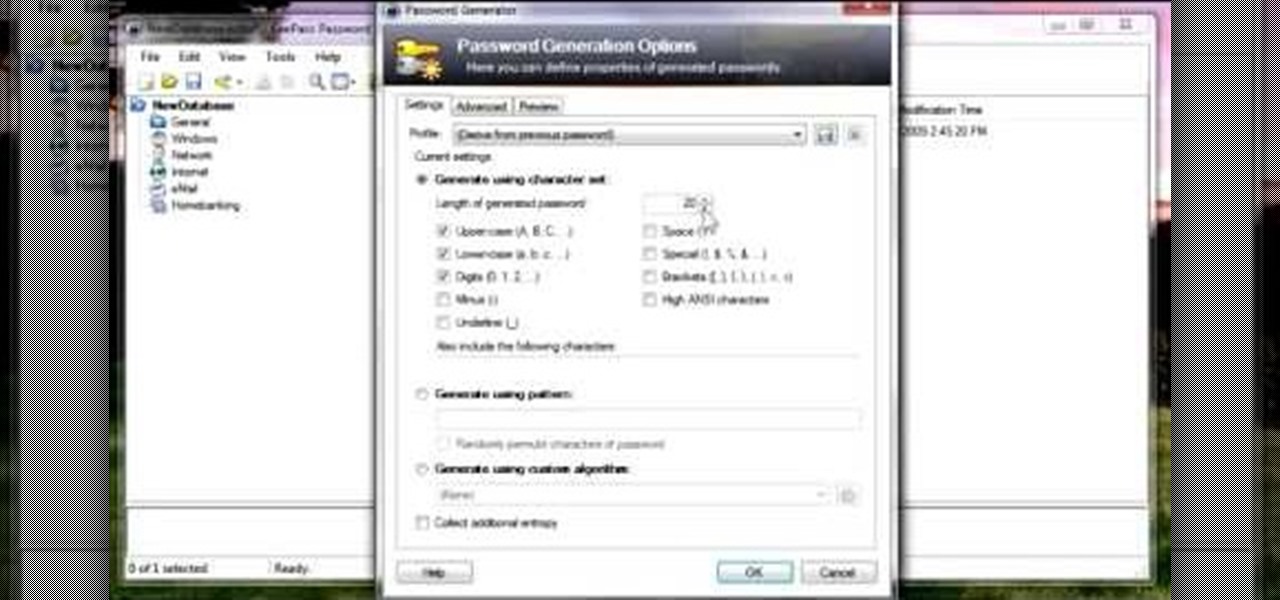
In this video, we learn how to use KeePass password generator. First, open the entry to edit the existing password and type in your username and e-mail address. Type in notes if you need it, then click on the bottom key icon. This will generate a password for you when you click on it and cover it up. If you click it once more, it will uncover what the password is. You can decide what kind of password you want and make one specific for the account you're using. When finished, you will have a n...

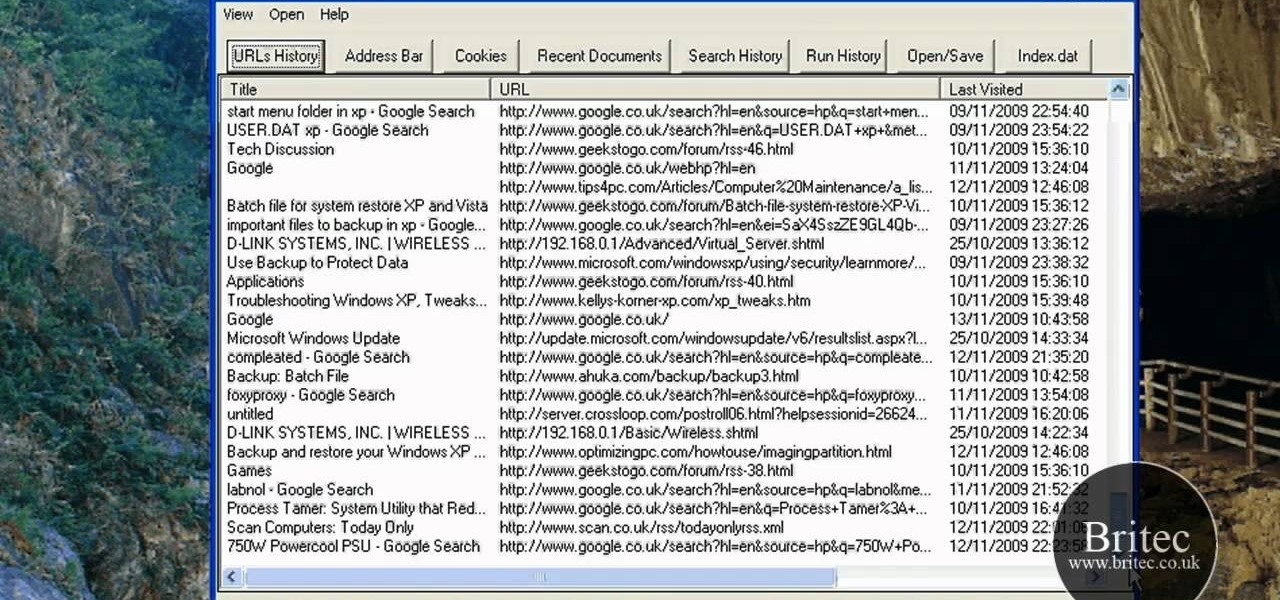
Interested in reading the list of web addresses in an index.dat file on a Microsoft Windows computer? This clip will teach you everything you'll need to know. With WinSpy, it's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over two minutes. For more information, including detailed, step-by-step instructions, take a look.

In this video, we learn how to submit a children's book manuscript to publishers. First, you will want to type your manuscript oh white paper and make sure it's double spaced and indented at the beginning of each paragraph. Use one inch margins on each side as well. Make sure the pages are number consecutively and your name, address, phone number, and e-mail are listed on the cover page. Don't break the text up and don't include pictures unless you're a professional illustrator. When you are ...

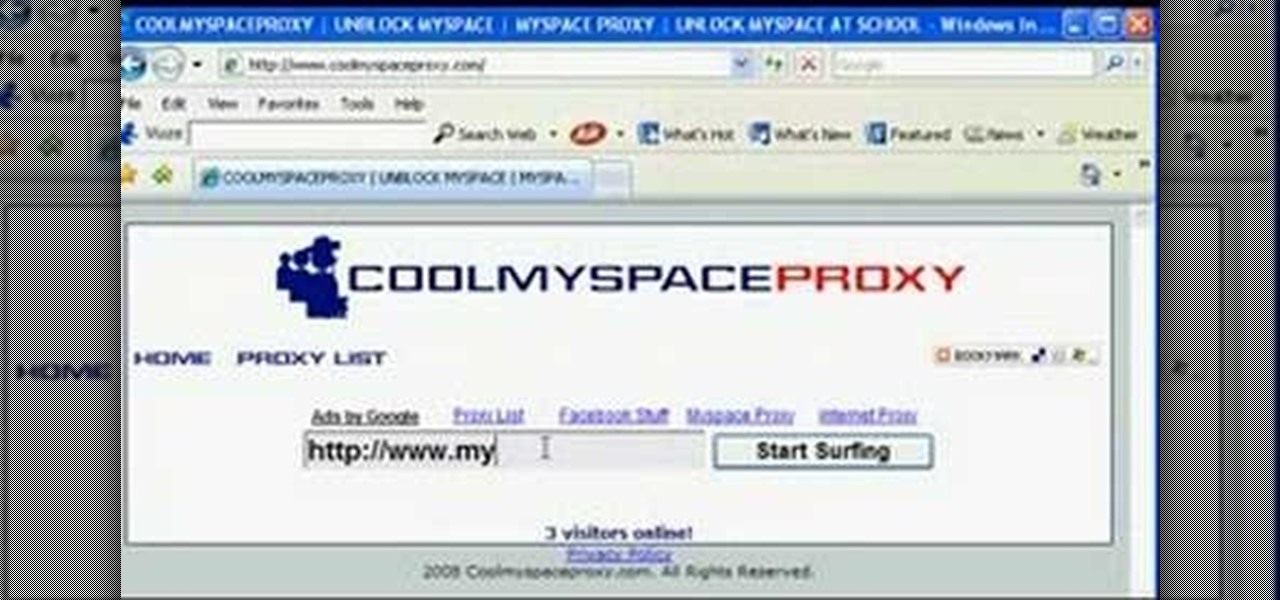
In this Computers & Programming video tutorial you will learn how to unblock MySpace (or any other site) at school or work or anywhere else. This is really very easy and simple to do and takes practically no time. It is like going directly to the original site. For this, you first go to the site Cool MySpace. Once on this site, simply type in the address of the website you want to go to in the surf box. For example, http://www.myspace.com and then click on 'start surfing'. That's it! You are ...

Facebook is an internet phenomenon which is quickly gaining popularity. For those who do not yet have a Facebook, this video will show you the basics of how to meet people and to connect with people online as well as how to set up your profile on the site. After creating an account using your email address and setting up your password, log on to the website. Set up your profile by clicking on the tab labeled "info" and entering information which you would like to share about yourself. You can...

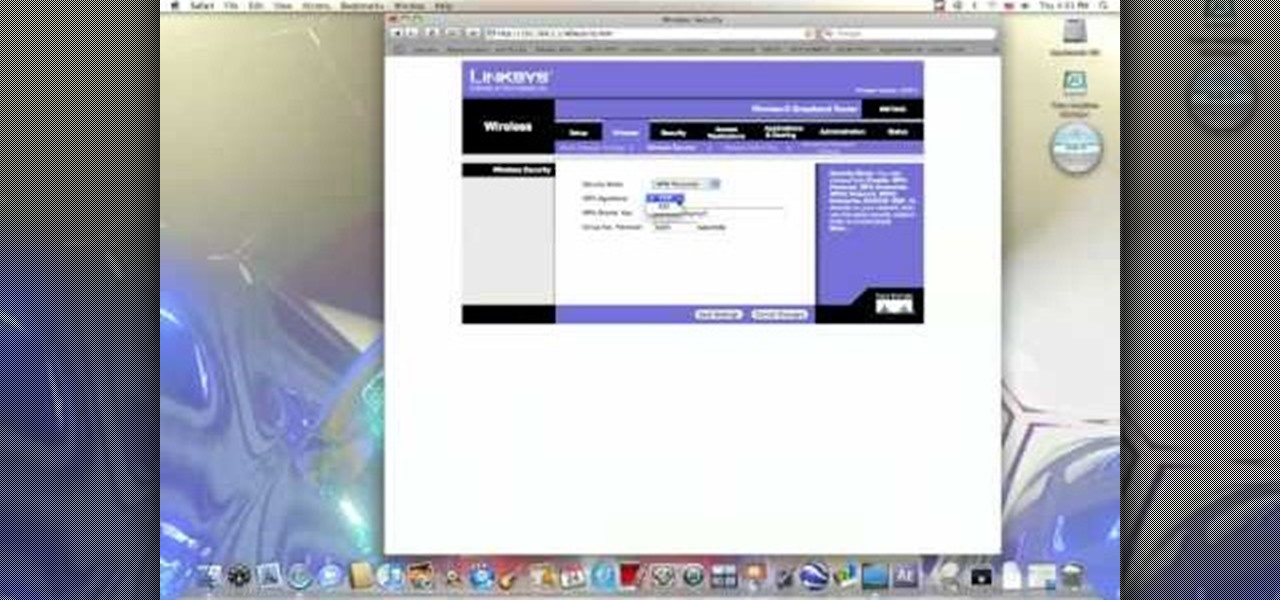
In this video from benjamoon we learn how to secure a linksys wifi network from a Mac. First type in your IP address in your browser bar which is 192.168.1.1 then press enter. If it asks for a password it is admin. Click on Wireless and here you can edit your name and who can access your wifi network. Under wireless security, go to WPA personal from the drop down menu. When you make your password, make it very challenging. He recommends just banging your hand against the keyboard, as long as ...

In this video tutorial, viewers learn how to convert .docx file format to a .doc file. Begin by downloading and saving the file to your desktop. Then open your internet browser and go to this link: Zamzar/]. In Step 1, click on Browse and locate the file that you want to convert. In Step 2, select .doc as the format that you want to convert the file to. In Step 3, type in your email address. In Step 4, click on Convert and wait for it to upload. Now open your email to find the sent converted ...

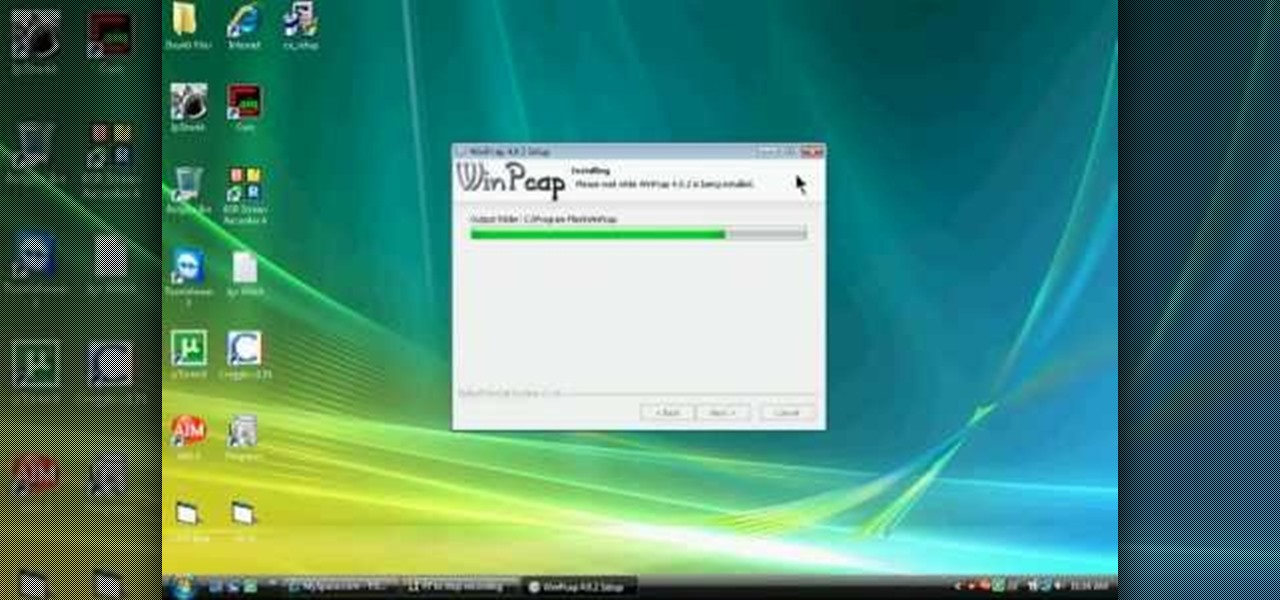
First you have to install program, called 'Cain and Abel'. Then, you will be automatically asked to install 'Win Pcap' and you should do that. After installation you have to click on 'Cain and Abel' program icon with right mouse button and start it as administrator. Then push blue plus sign to scan Mac addresses. After scanning go to the bottom of program window and press APR tab. Then push blue plus icon again. When table appears push first option in first square and first option in second a...

Jim McLean shows us how to do an eight step swing in this video. You start the swing in the "address" or universal position. The first step is to move the club three feet back from the ball in a uniform motion. Position two is moving the club half way back where the club is pointing down the target line. Position three is a three quarter golf swing is when your elbows are level and the shaft of the club is pointing into the plane line. Position four is preparing to swing forward. Position fiv...

This is an instructional video on how to hit a golf ball out of thick rough. The major issue that most people have with hitting the ball out of the rough is that they end up smothering the ball when they swing. This is caused by the grass catching on the shaft and closing the club face. They way to fix this is, at address you need to open the club face a slight amount. When you swing the club will catch and your club face will be positioned perfectly and the ball will shoot out of the rough l...

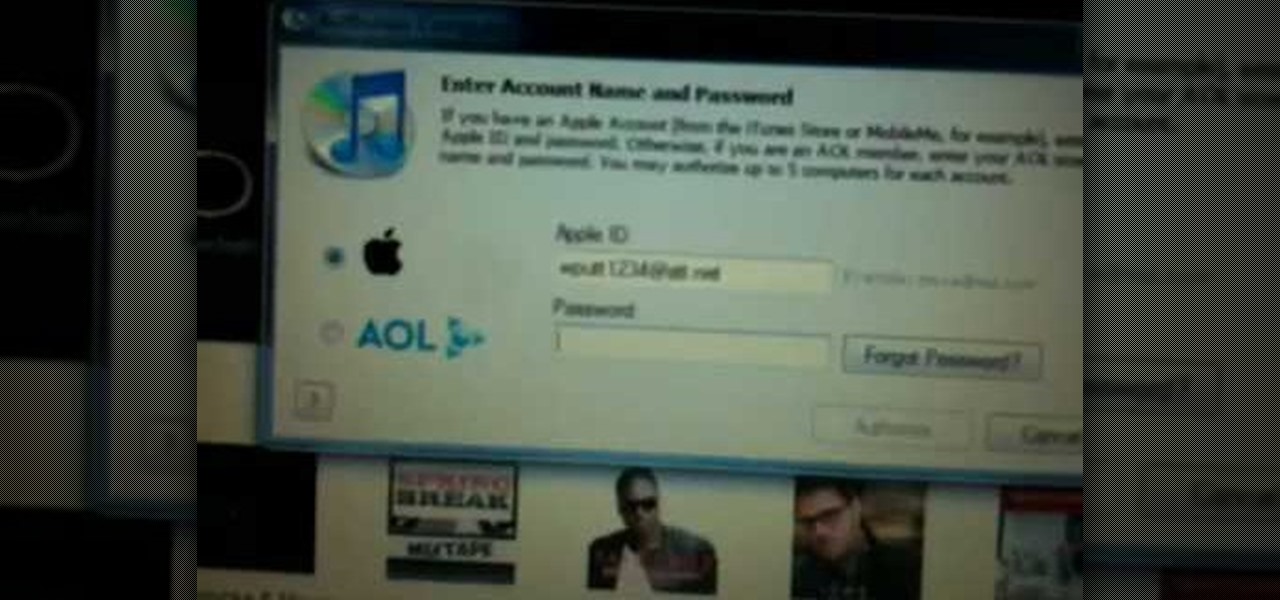
In this video from wadeputtii we learn how to authorize or de-authorize a computer on iTunes. Go to iTunes, sign into your account. Now click on Share and you will see Authorize Computer or Deauthorize Computer. If you want to authorize, click on that and enter your apple user email address and password. Then click authorize. If you have a new computer or you want to prevent someone else from using your account on your computer and you want to deauthorize your old computer, go to Share and De...

This tutorial will show you how to view your iPod or iPhone screen on your desktop. First of all, you need to have a jailbroken iPod for the applications necessary and secondly you will need Wi-Fi. You will need to download the application RealVNC for your desktop and Cydia for the jailbroken iPod or iPhone. Within Cydia you will search for the program Veency and go to the homepage. From there you will go into settings Veency. Now you have down everything on your iPod or iPhone. Now on your c...

In this video you will learn how to make Google your homepage. This is a very simple tutorial and it will show you what the instructions are. The first thing that you need to do is to open your browser. Now go to 'Tools' and select 'Options'. The next step that you need to do is to click on the 'Main tab'. From there go to the Homepage writing section and just enter the Google address. Another way to make Google your homepage is to go to the Google homepage and click on the "Select Google as ...

FROMAN1115 teaches you how to change your NAT type to Open on your PlayStation 3. On the PlayStation 3, go to Settings-Network Settings-Settings and Connection Status List and write down your IP. Go to your PC and start your internet browser. Type in 192.168.1.1. This will bring up the router settings page. Go to Applications and games and then DMZ. Check the first box that says Enabled. Enter your IP address below and click ok. Your settings have been saved and you can enter a new internet m...

Open your internet browser, type in the address bar 192.168.1.1 and enter your user name and password to access. Look in the right and search for Port Forwarding / Port Triggering. Click on Add Custom Service. Type a name to the service, like XBox Live, now access HushedCasket and scroll down to see the ports you need to open. Go back to the setting and select UDP in Service Type. Put 88 in Starting Port and Ending Port. Go to your XBox and enter in System Settings, go down to Network Setting...

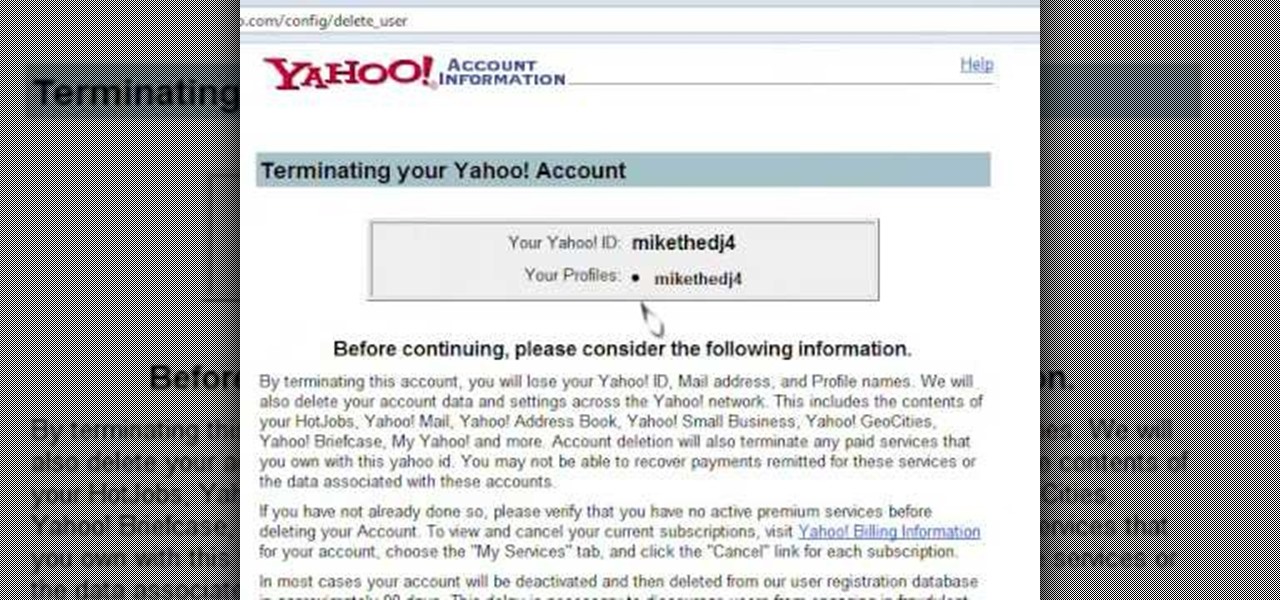
Learn how to delete your old Yahoo or Yahoo mail account in simple steps. First open your web browser and enter the web address for Yahoo to open it. Now log into your account using your Yahoo username and password. Go the account termination page, confirm your account termination and enter code give. Finally press 'Yes' and enter your password . Now your Yahoo or Yahoo mail account will be deleted.

Learn how to delete your old Yahoo account from this video in simple steps. First open your web browser on your computer and go to the Yahoo home page. Now sign into your account using your username and password. Now copy and paste this link "http://edit.yahoo.com/config/ delete_user" in your address bar. Enter your password to confirm the deletion of your account. Finally enter the code to confirm and delete your account.

This video tutorial gives you a way to access websites that you can not normally access because of a web block or filter. What you need to do is click on the ‘Start’ button and then click on ‘Run’. In the small window, type in ‘cmd.exe’; this then opens a black window. Then type in ‘ping’ and the website; this gives you an address that you type in directly to your web browser, granting you access to a normally blocked website. This comes in very handy when you are in such locations like schoo...

Take a look at this video if you've ever been curious on how people send video messages via the iPhone.

At midnight on February 17, 2009, all full-power television stations in the United States will stop broadcasting in analog and switch to 100% digital broadcasting. Digital broadcasting promises to provide a clearer picture and more programming options and will free up airwaves for use by emergency responders.

Anxiety can take a toll on your body and there are many ways to help ease anxiety in your body. Essential oils can relieve anxiety and relax the body. Get advice on reducing and managing stress in this stress management how-to video.

In this how-to, you'll find instructions for programming with the Python programming language. More specifically, this tutorial addresses everything from locating and installing Python to running it and writing your first programs. If you're interested in learning more about the Python programming language, watch this helpful video tutorial.

If you're new to DreamCoder for Oracle, one of the things you may want to know how to do is to is write complex SQL queries. Happily, this tutorial will walk you, step by step, through the process. To learn how to use the DreamCoder for Oracle Query Builder, press play!

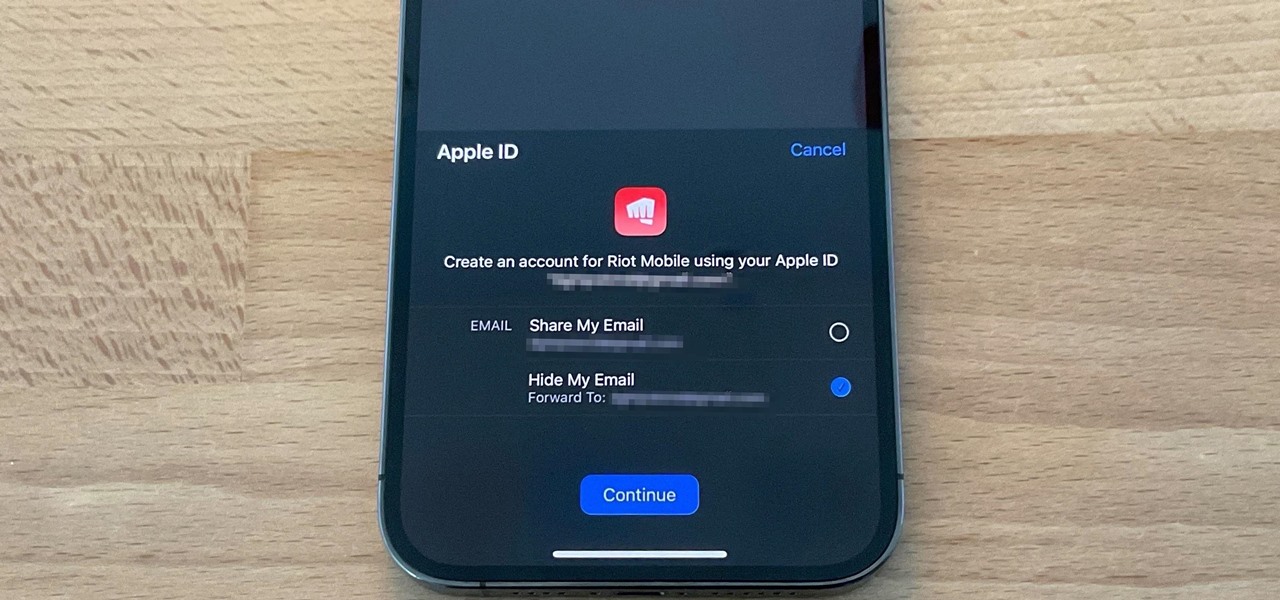
The "Sign in with Apple" service lets you create accounts with third-party apps and websites more easily using your Apple ID. More importantly, it can hide your personal email address using auto-generated disposable email addresses. However, it's easy to lose track of the accounts you use with Sign in with Apple, as well as any throwaway email addresses you used to hide your actual address.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

Apple released iOS 13.4 to public beta testers on March 18. The update comes the same day we learned that iOS 13.4 would be made available March 24. The sixth beta is iOS 13.4's GM (golden master), even though Apple refers to it as "beta 6."

Apple released iOS 13.4 to registered developers on March 18. The update comes just hours after news broke that iOS 13.4 would hit all compatible devices on March 24. The update is the GM (golden master), which makes it the same build as the official release we expect to see on March 24, although Apple does refer to it as "beta 6" on the dev site.

After three rounds of beta testing, Apple finally released iOS 13.3.1 today, Jan. 28. It's the latest update to iOS 13, coming exactly seven weeks after the release of iOS 13.3. So, what's new?