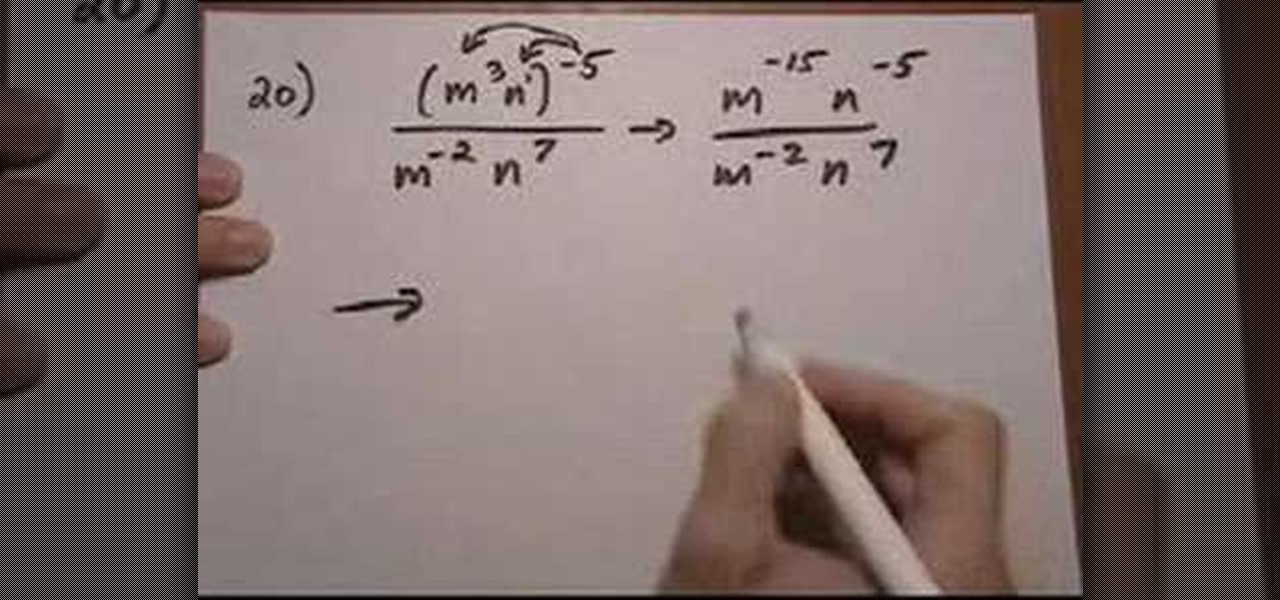Autodesk Maya, affectionately known as just Maya to its users, is a 3D computer graphics software that makes it easy to create impressive, realistic models of real-life - or imagined - objects. Super useful for graphic designers, film makers and web designers, the program is one that you should study if you're looking to go into one of the fields above.

Salad isn't everyone's first choice for a main dish, but when you try out this shrimp salad, you're sure to start making it your entrée instead of your side.

One you understand how a subnetwork works on an Internet Protocol (IP) network, creating one becomes very easy. In this five-part video, you'll learn about IP address and subnets, along with creating an IPv4 (IP version 4) address using Class C, which leaves each network with 256 local addresses. If you're new to subnetting, this is where you start!

Learn how to do narrow grip seated rows. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do seated dumbbell shoulder presses. Presented by Real Jock Gay Fitness Health & Life. Benefits
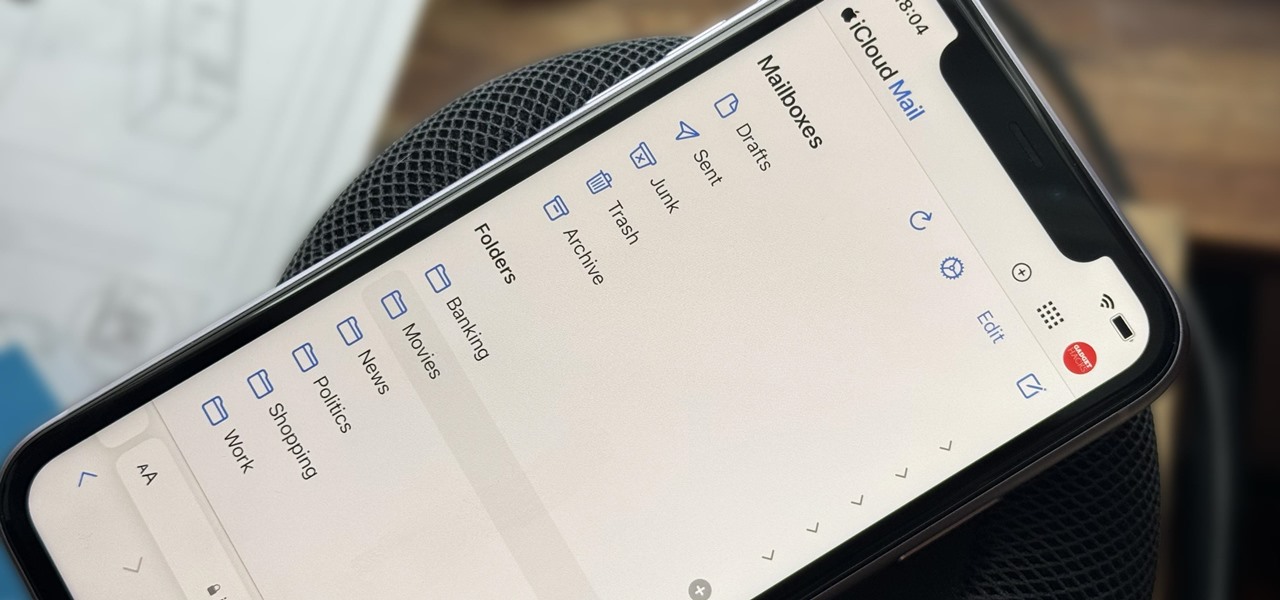
Apple includes a lot of helpful features for iCloud email addresses, but one of its best-kept secrets will give you total control over organizing your inbox like a pro.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

It's finally out. After months of testing, iOS 13 is available to install on your iPhone, which means over 200+ new features you can use right now. The update, released on Sept. 19, can be installed over the air or from a restore image using iTunes in macOS Mojave and older or Finder in macOS Catalina. Ditto for the 13.1 update issued on Sept. 24.

Dark themes are all the rage these days, and both Android and iOS have system-wide versions. Many big-name apps and device manufacturers have already jumped on board the night train, and Google Chrome is no different. But the Chrome mobile browser offers various ways to enable its dark theme.

There's a lot of misinformation about VPN services, and it stems from the fact that not all of them are created equal. Some focus on privacy, others on security, and a few VPNs are seemingly even purpose-built for the polar opposite: data collection. We made this guide to help clear the air on some of these issues while objectively ranking the best of the best.

Shopping wasn't always this easy. Now, in a matter of minutes, you can order your groceries for the week, send your cracked phone in for repairs, get your holiday shopping done, and have everything delivered to your front door in just a few days — without ever having to leave your home. Online shopping is convenient, comfortable, and a blessing ... right? Well, it can also be a headache.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

After about 40 days of beta testing, Apple pushed out iOS 11.4.1 to everyone as a stable build on Monday, July 9, exactly one week after the final beta appeared.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

Ever since Google CEO Sundar Pichai took the helms of the world's most valuable brand, he has made it his mission to bring smartphones to lower-income communities. Born in India, Mr. Pichai has created several programs to address the needs of the Indian market, particularly the lower income families.

Besides its extensive collections of add-ons for Android, Firefox's mobile browser apps have many built-in features that you won't see in other mobile browsers. One feature in particular, available for both Android and iOS versions, makes it easy to switch back and forth between search engines for any query.

Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the lowest level. This is referred to as binary exploitation, and today we're going to check out a tool known as Protostar.

Tesla hopes high-level personnel changes will help it gain an edge in neural network knowhow for its models' self-drive features, following the replacement of its Autopilot chief and the appointment of a recent Stanford grad to head its AI and Autopilot vision research.

Before many games make it to the US-based iOS App Store, they get "soft launched" in a smaller country to get real-world testing for bugs. It's a pilot program, so to speak, as countries like Vietnam or the Philippines have far fewer iPhone users than the US, thus offer a more controlled environment for developers to get feedback and zero-in on issues that may occur in a game's early development phases.

Using extreme time-lapse microscopy, scientists watched a virus take over a bacteria to create a cell that looked and functioned more like a plant or animal cell. True story.

When I tried to set up an eviltwin for a MitM-constelation in kali 2.0, I couldn't provide internet to the victim. The origin was the brctl bridging. I have read many tutorials but all of them where explained in backtrack and older versions of kali. So i was searching for a solution without using brctl and this solution will be explained now. This will just work on unencrypted wireless-environments.

Why did I write this when they're tons of scanning tools available.

Airports are terrible germ-infested purgatories where people sit around for hours without Wi-Fi while they anxiously await to get wherever they really want to go. Unfortunately, there isn't much we can do about waiting, but this little Wi-Fi hack could help make the waiting a little less boring.

I still remember when I had to get up from my comfy spot on the couch to change the channel on my old television. So for me, the remote control may be one of the most underrated inventions of the last century. These days, remotes take on all sorts of shapes, not just the typical brick, but also in the form of watches and cell phones.

Apps that have no business accessing the internet can share your location, device ID, and other personal information with potentially malicious data snatchers. If you're connected to the internet on your Nexus 7 tablet, you're a potential target for cyber threats.

Welcome back, my greenhorn hackers! In a previous tutorial on hacking databases, I showed you how to find online databases and then how to enumerate the databases, tables, and columns. In this guide, we'll now exfiltrate, extract, remove—whatever term you prefer—the data from an online database.

Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensics. In other words, what can a network forensic investigator learn about the attacker during an investigation and how.

Ever since the FBI took down the Silk Road and Dread Pirate Roberts last month, many questions have been raised about whether Tor still provides anonymity or not, and if it's now broken. I'll try to address that question here today succinctly from multiple angles, keeping it as simple and plain-language as possible. The Closing of Silk Road

Welcome back, my rookie hackers! When Wi-Fi was first developed and popularized in the late '90s, security was not a major concern. Unlike wired connections, anyone could simply connect to a Wi-Fi access point (AP) and steal bandwidth, or worse—sniff the traffic.

The NSA's massive internet spying efforts will continue. In President Obama's latest press conference, he went public to (in so many words) say that the NSA's spying efforts will continue uninterrupted. This, coming just weeks after the Amash Amendment which would have defunded the program, was narrowly defeated in the House (you can check if your congressmen voted against it here).

Welcome back, my fellow hackerians! Today we'll be hacking Facebook profiles on your local network. You may think, "How is this useful, nobody but me is using my network." Well, you can use this on other Wi-Fi networks that are available for free (like at Starbucks) and crack their precious Facebook profile!

Tracing any IP hostname or web address free online is demonstrated in this video. To trace any IP, website and hostname free online firstly go to the websiteGeoLocationWhen the webpage appears you will get a find option. Enter your IP address, website or hostname here. Then click the find option. Your IP hostname or web address is traced. So easy. Quick and simple to use. Your IP address, city, country, continent and time zone will be displayed in a rectangular box in your location in the wor...

As an adult you will come a cross a point in time when you need to make the right impression by writing a formal letter. Follow the format and you will be able to be most effective at conveying the information in your letter.

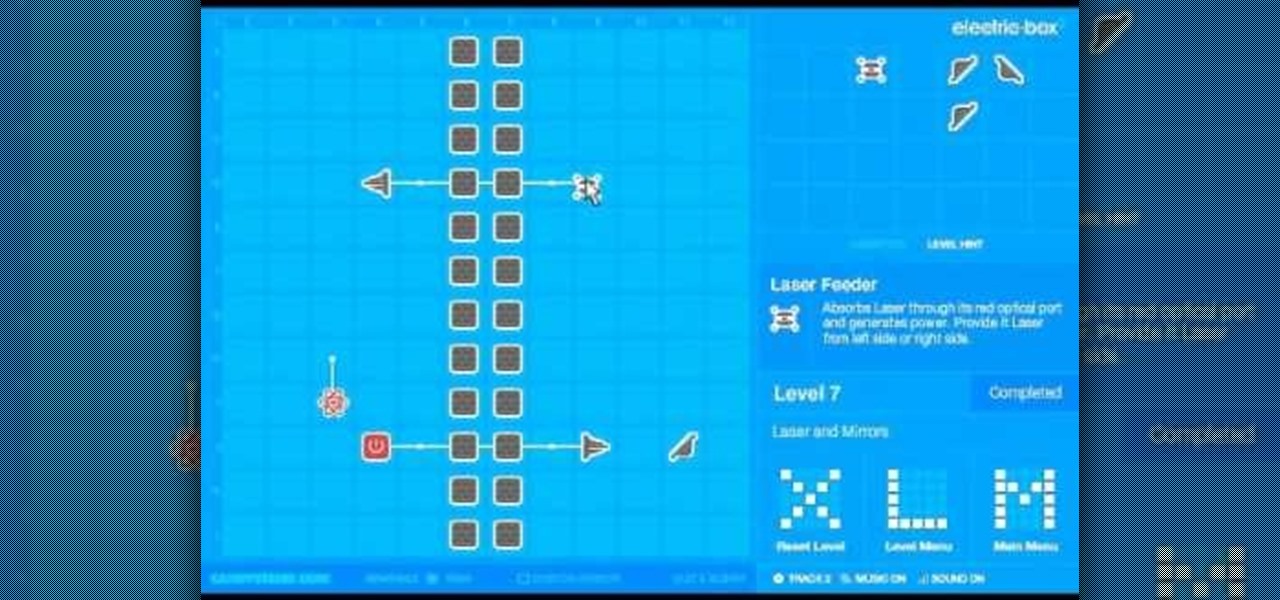
Box 2 is a fun and educational Flash game on Candystand that teaches people about the joys of renewable energy generation in increasingly complex puzzles. This series of videos will show you how to beat all 40 levels, including the alternate level 38 in it's own section.

You've manage to get your hands on some ruthenium, and now you want to destroy the hard silvery-white metal of the transition series. Well, you're going to try all kinds of ways to dissolve this odd metal, but the only successful way to dissolve ruthenium is with a common household cleaner… bleach.

If you want to draw and paint a robot Mecha style you should first make a square and color this in a dark gray. Draw a silhouette in a darker gray color. You should draw basic body parts such as the head, arms and limbs and shoulder. You should draw this with simple dark layers. In the face, you can draw a different or cool complex design. You can also make the background darker and make shadows. To distinguish the figure from the background color the figure a dark dull blue. Now you need to ...

John Campbell shows you how to make an all natural bowl with spout using hot coals to burn the desired shape into a block of wood. First you'll need to make a straw from a cattail stock by burning through the center with a hot coat hanger. John next demonstrates how to use this straw and some hot coals placed on the wood to burn the shape of a bowl and spout into the block. Finally, John uses a stone to sand the bowl down and remove the charcoal leaving a clean wooden container. The final res...

Some times malicious programs can infect your registry and fill it with lots of unwanted information. You may need to clean it to prevent the virus from causing any further damage to your computer or to even disable the virus. It is a very lengthy and complex process to do this manually. So you will need to use one of the powerful free tools available online. Hijack This is one of the most powerful program that can be used for this purpose. So go the website and download this free tool. Insta...

The video shows how to solved mixed property problems using the exponent rules. See if there are any rules you can apply to the problem until you get to a point where you can't simplify anymore. The instructor shows in the example problem that the two bases are the same, but there is extras happening the numerator. The power to power multiply rule is applied removing the extra issues from the numerator. Next the quotient rules is applied as there is the exact same base to the power so we keep...

This video shows how to change the advanced settings to make Firefox faster on Mac and PC.