Next time you don't want to make your bed, dry the dishes or clean the house there's no need to feel guilty. You may be doing yourself a favor. There are legitimate scientific reasons why some chores aren't always the best health choice.

A series of videos that help show just how tough it can be to install a remote car starter. Unless your an electrician or a technician, this complex job can result in a variety of electronic failures in your car including prevention of actually getting into your car as well as prevent you from driving home.
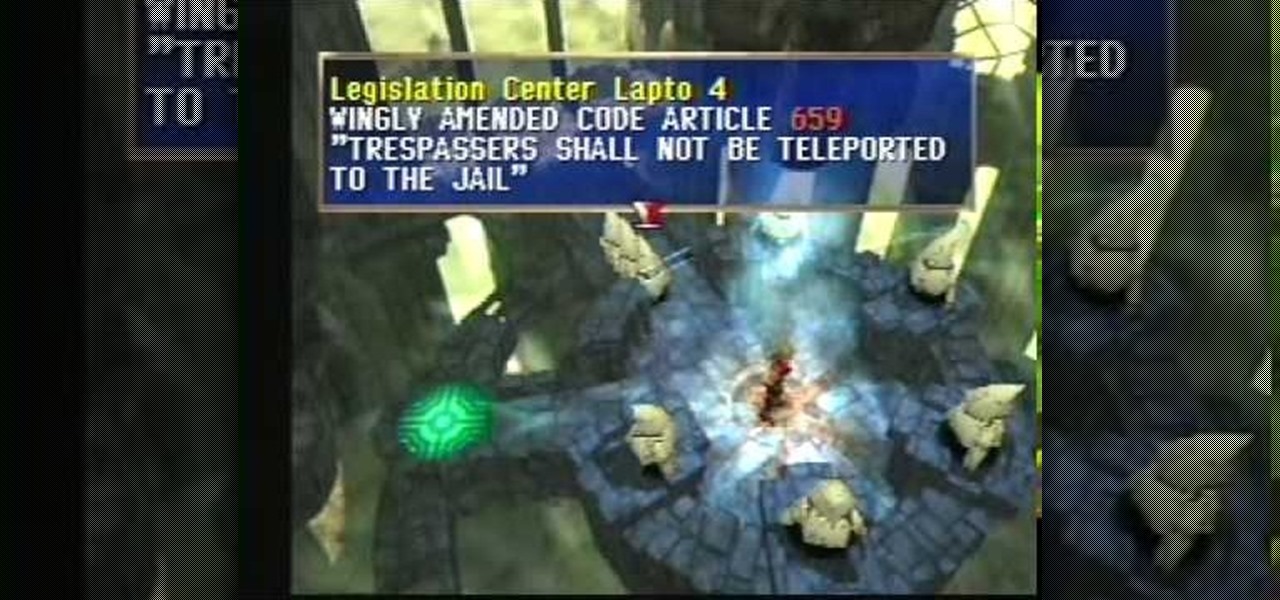
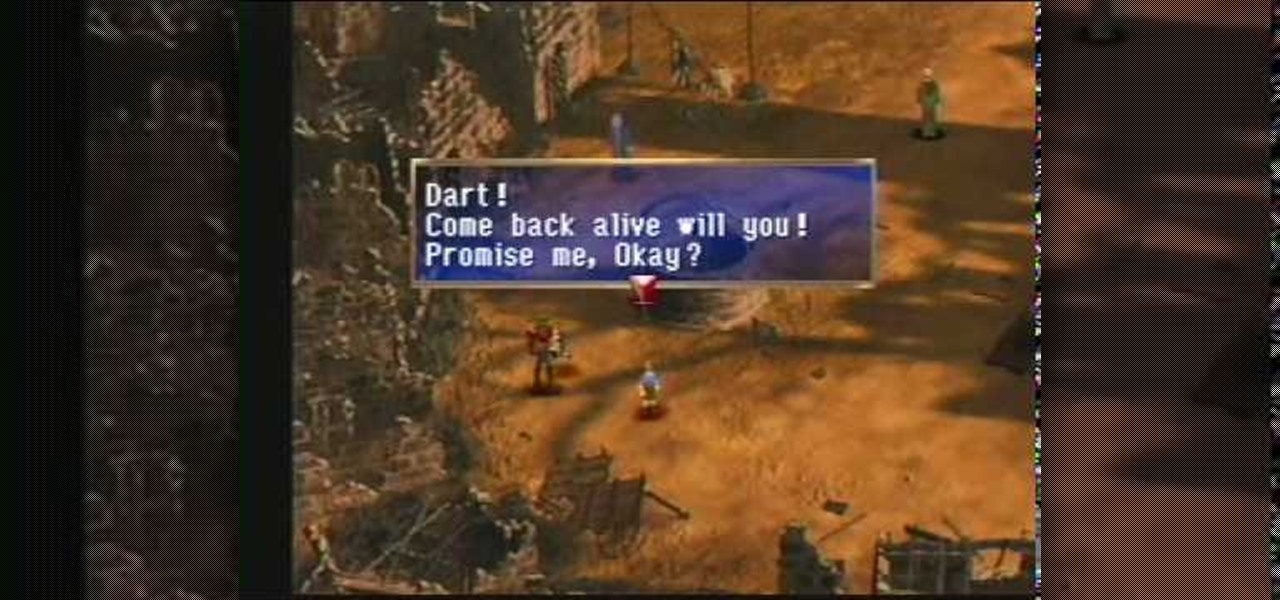
Dart and his friends are almost done. They just need to defeat Faust and return to the Law City Zenebatos in this part of The Legend of Dragoon for PlayStation. This video walkthrough takes you from where Dart and company fight and defeat Magician Faust in Flanvel Tower, they leave Flanvel and Kashua Glacier and back to the Law City Zenebatos to where they are exploring the city and rewriting laws so they can move about easier.

Start your battle with the Magician Faust in this section of The Legend of Dragoon for PlayStation. This video walkthrough takes you from where Dart and company fight and defeat Belzac and Kanzas, they head to Deningrad to buy/sell some stuff, through the Kashua Glacier to the Flanvel Tower, and they explore the Tower to where they are fighting Magician Faust.
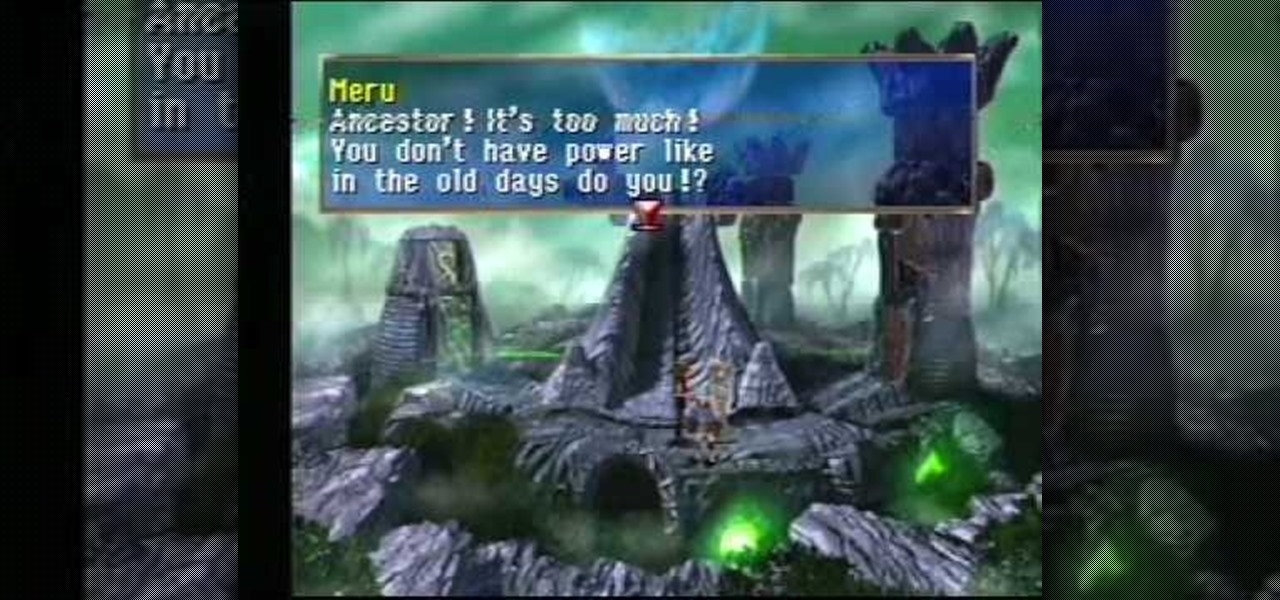
You'll find yourself in Kadessa and Deningrad in this installment of The Legend of Dragoon for PlayStation. This video walkthrough takes you from where Dart and company are exploring Kadessa, they fight and defeat the Grand Jewel for possession over the Dragon Block Staff, the party leaves Kadessa just as the Divine Dragon is launching an attack upon Deningrad, the Winglies try to teleport the party to Deningrad but they are too late to stop the attack, the party rush to the castle and make s...
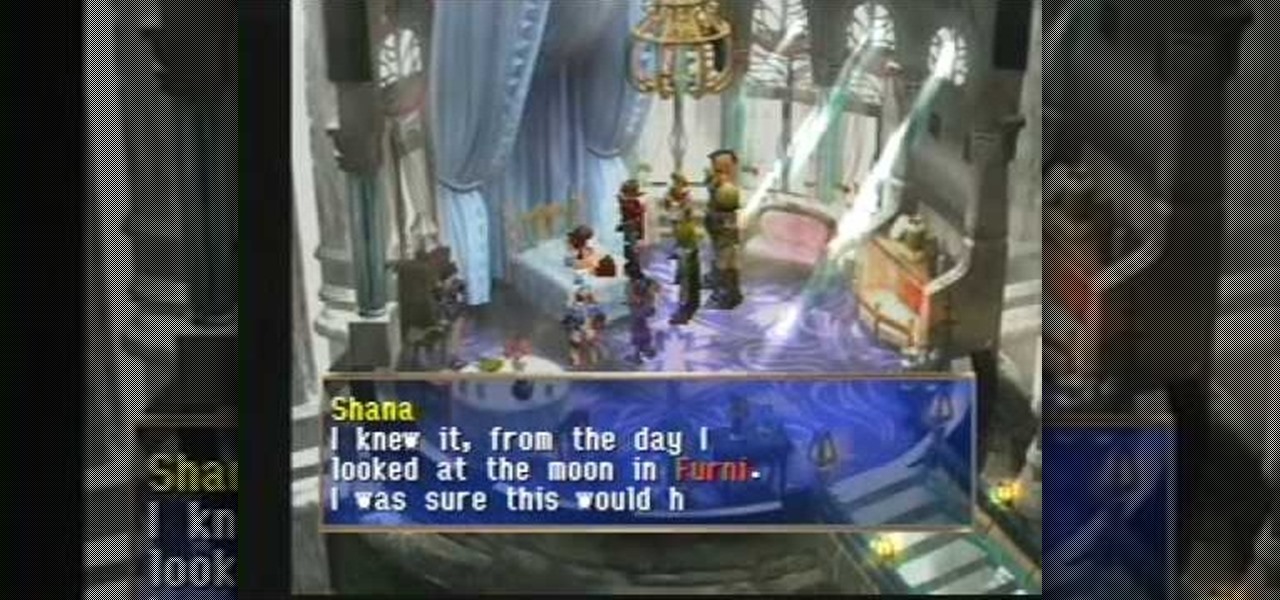
There's a lot going on here. In this level of The Legend of Dragoon for PlayStation, you'll see Queen Theresa, Sister Miranda, Shana, Winglies, and Neet. This video walkthrough takes you from where Dart and company make a visit to the Crystal Palace, Queen Theresa gets the party to agree to stop the Divine Dragon, Shana's Dragoon Spirit leaves her for First Sacred Sister Miranda, Shana collapses and is forced to stay behind, the party leaves and goes through the Evergreen Forest, they make a ...

In Hellena Prison, save the King from his execution… save the day in this level of The Legend of Dragoon for PlayStation. This video walkthrough takes you from where Dart and company are racing to the top of Hellena Prison to save King Albert from execution, they fight and defeat Fruegel, Lloyd steals the Moon Gem from Albert, Lavitz turns Dragoon in an attempt to help King Albert and gets slain, King Albert joins the party, they all go talk in Seles to where they travel to and explore the Bl...

Looking to make a nutritious change in your life? By choosing the right foods in the right amounts, you can reap rewards that will benefit you in all aspects of your life. In this tutorial, learn how to eat healthy and make positive changes in what you consume.

When used together with the "sit!" command, "stay!" can form the foundation for more complex tricks.

Pinochle is a card game with complex rules, strategies, and tactics. Here’s a game overview for new players.

Does the morning routine in your household include temper tantrums and a mad rush to get out of the house? Follow this plan to keep everyone on track.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to hide secret data inside a photo.

Ever hear of a Rubik's Cube, well, did you know that some people can even solve it blindfolded? Yes, that right... blindfolded.

A collage is a complex array of images and pictures all mashed up and overlapping; learn how to make an artistic collage in this free video art lesson.

Learn how to do lean barbell single side rows. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do power stability ball lower back extension with pelvic thrusts. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do face down dumbbell rotate and press on an incline bench. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do dumbbell lateral to front raises. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do dumbbell 45-degree angle raises. Presented by Real Jock Gay Fitness Health & Life. Benefits

This is a Google Tech Talk from March, 26 2008. Timothee Cour - Research Scientist lectures. Movies and TV are a rich source of highly diverse and complex video of people, objects, actions and locales "in the wild". Harvesting automatically labeled sequences of actions from video would enable creation of large-scale and highly-varied datasets. To enable such collection, we focus on the task of recovering scene structure in movies and TV series for object/person tracking and action retrieval. ...

In this tutorial, we learn how to find your computer's IP address. An IP address is used to know the exact location of someone using a computer with internet access is located at. First, turn your computer on and go to your main desktop. Then, click on "start", (which is located on the lower left hand side of the tool bar at the bottom), then click "run" and once that opens up, type "cmd" into the white empty space. Hit "ok" and when this comes up, type in "IPConfig" and hit "enter". Your com...

Candy bars are tasty but all they do is spike your blood-sugar momentarily leaving you with and energy crash. For high, sustained energy you will need a balanced diet full of complex carbohydrate and protein.

This video will show you how to easily find out what your IP address is. In your windows computer, you should go to the start icon and find a button which says "Run". After clicking on this button, type in "cmd" and a black box will appear. In this black box, you should then type in "ipconfig". In the data that appears after you type this in, you will see a section which says "IPv4". The numbers that follow this section is your IP address. Viewers might need to know their IP address for vario...

ER showed the world what goes on inside the emergency room, and in every episode, we experienced a common but very important procedure— intubation. But ER never made it seems easy; it showed just how hard it is for medical students to successfully intubate a patient due to fear and naivety. And for real-life doctors and medical practitioners, learning the art of airway management is just as difficult.

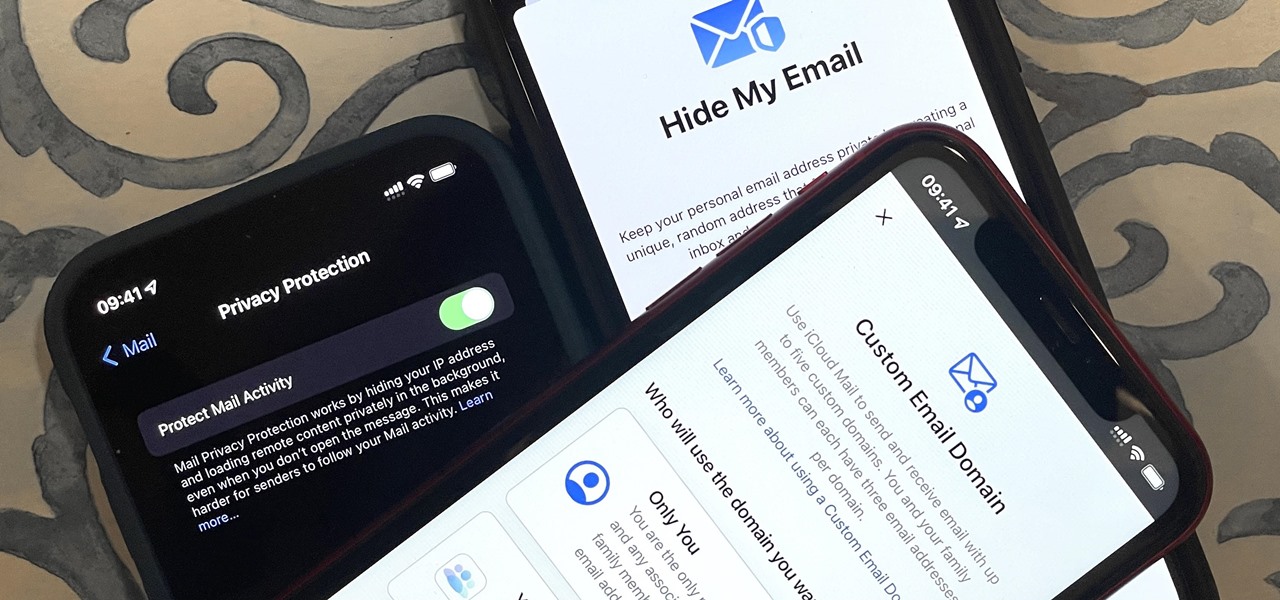
Privacy is a growing concern in the tech industry, but Apple has fallen behind many of its peers when it comes to email security. Fortunately, iOS 15 changes that. Your email address is the key to a vast amount of personal information, not to mention a stepping stone into your other online accounts, so it's great to see new features for iPhones that protect email accounts and their contents.

Google has always experimented with Chrome's UI, but when they make more drastic changes, they start by hiding them in the feature flags menu. One of the latest designs makes Chrome more accessible in a world of big and tall phones.

Apple released iOS 13.0 on Sept. 19 and announced on the same day the release of iOS 13.1 on Sept. 30. But that deadline was pushed up to Sept. 24, and that's why we have 13.1 just five days after 13.0. But that's good news since we don't have to wait any longer for some of the features promised in iOS 13 that didn't make the first cut.

With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

The next libSSH or OpenSSH exploit may be just around the corner. Keep your SSH service out of Shodan's database before hackers find new ways to bypass the password protecting the server.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

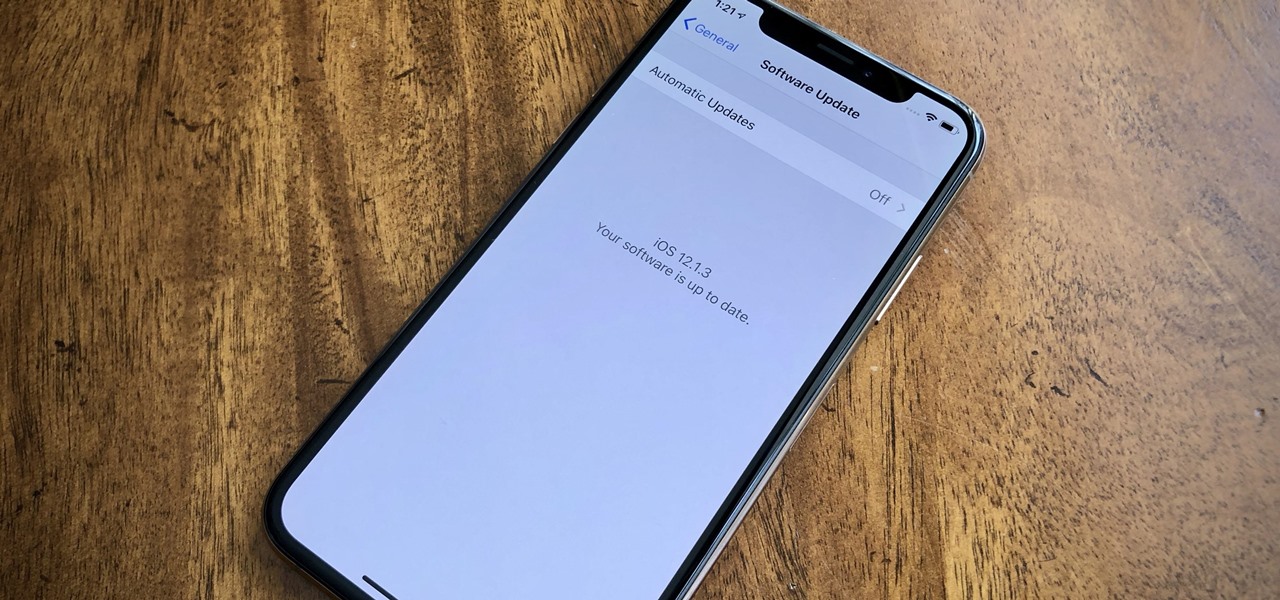
Just after a month of testing, iOS 12.1.3 has been released for iPhones. Like the previous iOS 12.1.2 update, there's not much to get excited about. There are no new features discovered yet, but there are a few fixes for issues with photos in Messages, imperfect pics when using the share sheet, and disconnecting CarPlay.

With CES in full swing, it seemed like Magic Leap would have little to announce at the major tech event, but it turns out that one of its partners has weighed in with a rather substantial update regarding the company.

If waveguide display maker DigiLens has its way, enterprise businesses and consumers will soon be able to purchase smartglasses for less than $500 — as long as they can supply their own computing and battery power.

While Leap Motion has given makers a DIY solution for building their own augmented reality headset with Project North Star, a self-described "AR wonk" has taken the blueprints one step further by creating an untethered version.

Over the last few years, the virtual reality space has earned a welcome reputation for fostering better representational balance with regard to gender compared to the general tech industry, with women like Nonny de la Peña and many others leading the charge.

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.

One of the first steps in reconnaissance is determining the open ports on a system. Nmap is widely considered the undisputed king of port scanning, but certain situations call for different tools. Metasploit makes it easy to conduct port scanning from directly inside the framework, and we'll show you three types of port scans: TCP, SYN, and XMAS.

Luxury automaker Mercedes-Benz has joined the growing list of automakers adopting augmented reality to provide an assist to its manufacturing operations, in this case, via the Microsoft HoloLens.

As Android bug bounty hunters and penetration testers, we need a properly configured environment to work in when testing exploits and looking for vulnerabilities. This could mean a virtual Android operating system or a dedicated network for capturing requests and performing man-in-the-middle attacks.