The ability to browse the web in coffee shops, libraries, airports, and practically anywhere else you can imagine is more than convenient, but convenience has risks. Using public Wi-Fi allows others to spy on you easily. Even your own internet service provider can see every website you've ever visited. Don't fall into the trap of protecting your identity, data, and devices after it's too late.

With so many competing outlets to reach people, accessing inboxes remains one of the most effective forms of communication. Yet newsletter creators run into a constant problem: bounced emails.

It's nearly impossible not to be at least somewhat familiar with Microsoft Excel. While it's needed for many office jobs and data analysis fields, hackers could also benefit from improving their spreadsheet skills. Many white hats already know some of the essential Excel hacks, such as cracking password-protected spreadsheets, but there's so much more to know from an attack standpoint.

Few things are more important than being well-versed in data analytics and interpretation when it comes to succeeding in today's increasingly data-driven world. As a data scientist, these skills are the key to a high-paying career. For hackers, there's no better way to defeat the enemy than to become the enemy.

Augmented reality's status as a new storytelling medium has already led to the reinvention of filmmaking and journalism.

So far, iOS 13's major point updates have all been pretty exciting for iPhone. We've seen iOS 13.1, 13.2, and 13.3 come and go, offering more than 60 new features and changes combined to that very first version of iOS 13. While iOS 13.3.1 was a minor update, its successor, iOS 13.4, is a return to form.

It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploit contains a variety of modules that can be used to enumerate MySQL databases, making it easy to gather valuable information.

The updated Reminders app in iOS 13 makes productivity a little bit more seamless on the iPhone. The overhauled user interface makes it easier to find your reminders, the new Messages integration makes it simpler to remember to-dos regarding your contacts, and the new toolbar provides shortcuts to tasks that were once clunky and confusing.

For Snapchat users wondering if that selfie is ready to send to their crush, independent Lens Studio creator Andrew Mendez created a handy tool called the Smile Rater.

Imagine being able to play a video instantly on hundreds of thousands of devices across the globe. It's totally possible, as long as all of those devices have a Chromecast plugged in. When Chromecasts are left exposed to the internet, hackers can use add them to a botnet that can play YouTube videos at will. The "attack" is made even easier thanks to a simple Python program called CrashCast.

As the tech world patiently waits for the advent of mainstream consumer smartglasses, Google is content to stick to the business world (for now).

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

A relay is an electrical component that works like a light switch, where it's turned on or off with an electrical signal. By connecting a relay to a Wi-Fi connected microcontroller like an ESP8266, you can build a connected switch that can be controlled from the web browser of any device connected to the same Wi-Fi network — all for just a couple of dollars.

The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python tool for brute-forcing websites called Hatch, this process has been simplified to the point that even a beginner can try it.

Intel's RealSense family of depth tracking cameras has a new addition with a different set of sensory capabilities.

Designing and manufacturing waveguides for smartglasses is a complex process, but DigiLens wants us to know that they have a software solution that partially solves that problem.

Occipital's initial augmented reality module, the Structure Sensor, gave iPhones and iPads the depth-sensing abilities of the HoloLens. Now, the company's latest product promises to do the same for Android devices, as well as augmented reality and virtual reality headsets and other devices.

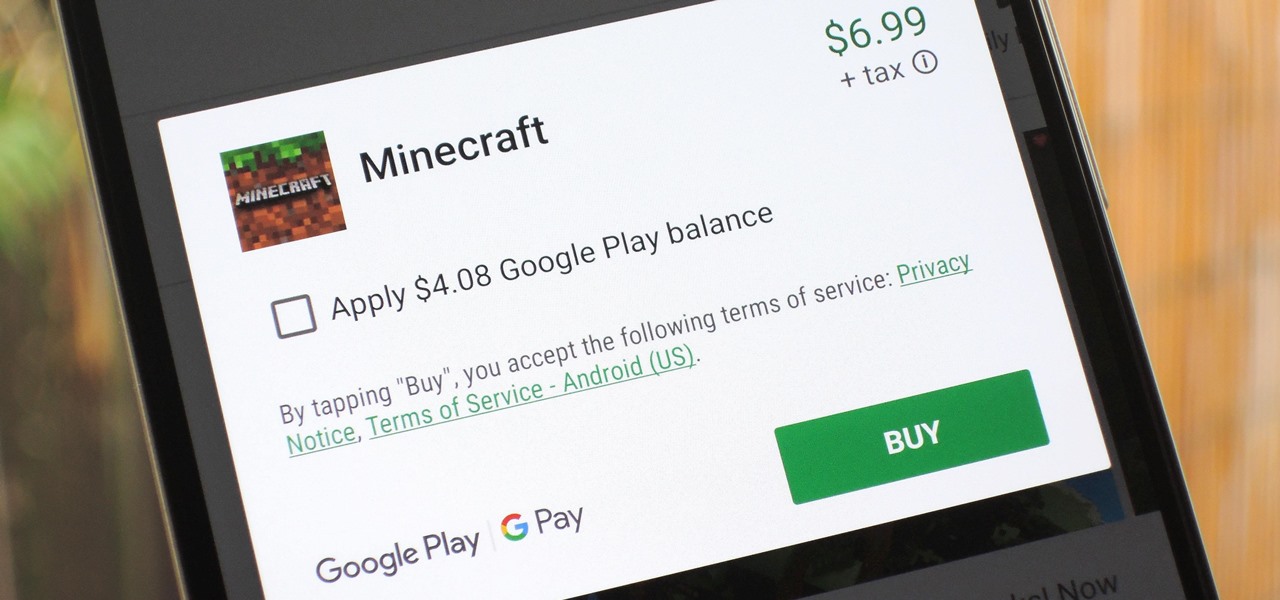
The iTunes App Store makes it easy to buy an app or game on someone else's behalf, and it's a great way to send an iPhone user a thoughtful gift. The Google Play Store doesn't have such functionality, but there are still a few workarounds to accomplish the same goal: gifting an app to an Android user.

Election Day is like the Super Bowl for network and cable TV news, so ABC News is breaking out the big guns with a new augmented reality experience to win over eyeballs of viewers.

In the waning days of October, at the Innovation Tokyo 2018 conference, attendees got their hands on some of the new augmented reality experiences that Niantic is working on through its Real World Platform.

Augmented reality productivity software maker Upskill has expanded the reach of its Skylight platform with support for Microsoft HoloLens.

While many of the latest content partnerships announced by Magic Leap appear to lean towards entertainment and gaming, a new partnership with medical technology provider Brainlab has Magic Leap getting down to more serious business.

One developer has taken the formal name of the Magic Leap One: Creator Edition quite literally with an app that enables users to create a custom universe in their own living room.

Four months after unveiling the latest productivity apps for the HoloLens, Microsoft now has a series of compelling real-world use case videos showing how the augmented reality device and its apps are helping oil giant Chevron.

Not content to let NFL's official pizza sponsor corner the market for feeding football fans, 7-Eleven has taken a page out of Pizza Hut's playbook with a promotional augmented reality game.

For the second time in a row, Apple pushed out a new iOS 12 developer beta on a Monday, and for the first time this round, they've done it only one week after the last one. While the August 6 release of iOS 12 developer beta 6 doesn't contain a wealth of updates, there are still a few things you'll want to know about.

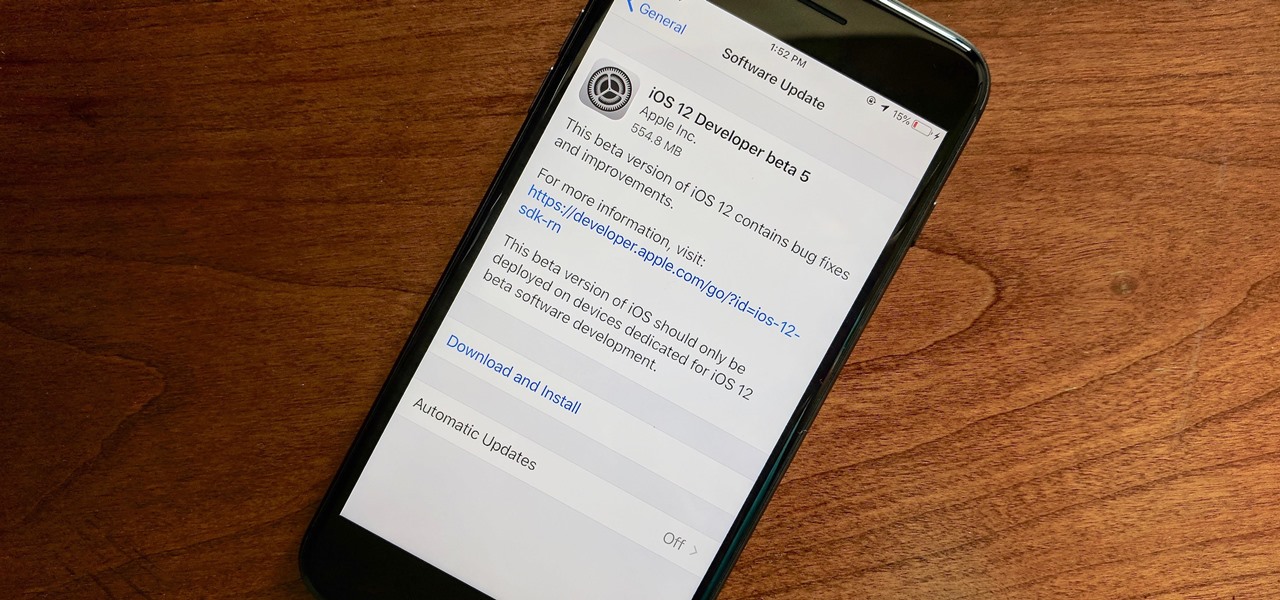
Apple released the fifth developer beta for iOS 12 on Monday, July 30, only 13 days after the release of dev beta 4 and 12 days after public beta 3. Until this release, Apple kept a consistent two-week schedule for developer beta updates, so we were a little surprised to see this one drop one day early.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it's easy to install, set up, and utilize.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

Recently, many manufacturers have started offering phones with a clean, stock Android UI. Motorola, Essential, Nokia, and OnePlus are probably the biggest names that have listened to user feedback and shifted more towards AOSP. But if your phone still has a bloated OEM skin, there are a few things you can do about it.

You may have seen news reports over the last two days detailing a major security flaw in virtually all smartphones. The devices that are at risk are not limited to either iPhone or Android — all of us are affected. If you want to make sure your smartphone and its data stay secure, there are a few steps you can take.

French manufacturer Renault Trucks is looking to the HoloLens to improve quality control processes with its engine assembly operations.

This week, Samsung officially kicked off the Oreo Beta Program for the Galaxy S8 and S8+ in North America and several other markets. The full list of changes is quite substantial, so we'll be running through them in a series of posts detailing what's new. First up, the Galaxy phones inherit notification channels from Android 8.0.

The default tool for payload generation is MSFvenom, a Metasploit standalone payload generator as well as encoder. This tool is an incredibly powerful tool for payload generation, but it can be difficult and requires a bit of reading for newer users.

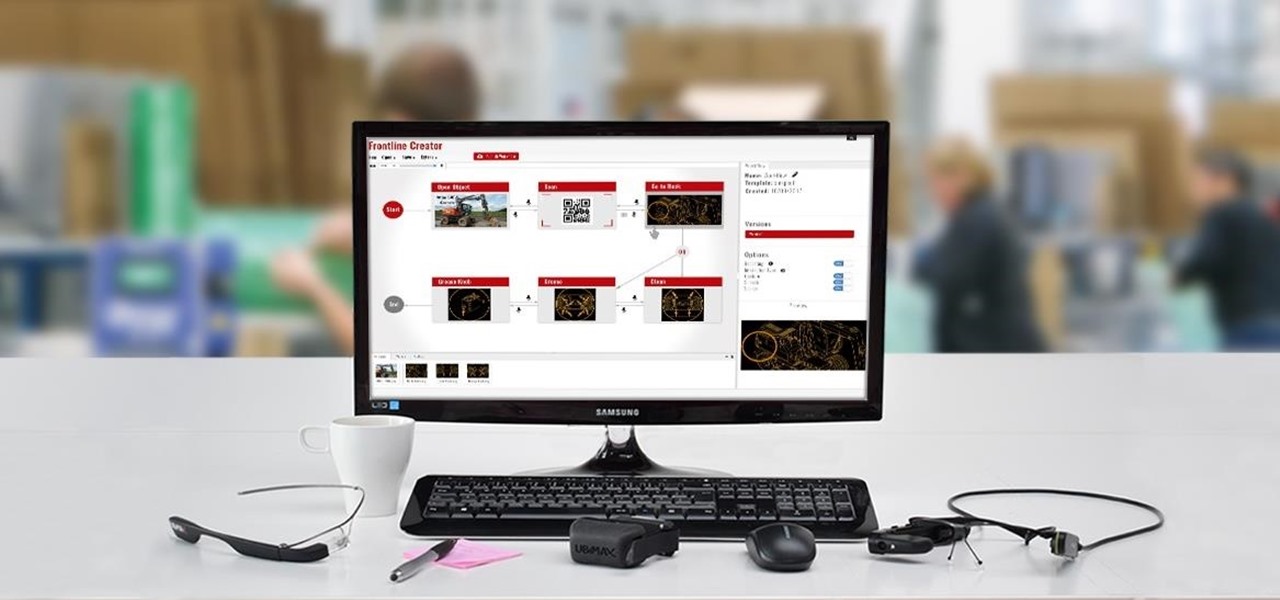
Augmented reality software provider Ubimax unveiled their graphical authoring and publishing tool for their Frontline enterprise platform to attendees at Augmented World Expo Europe today.

When it comes to streaming your favorite movies and TV shows, there aren't many media players that are better than Kodi. With its fast performance and easy-to-use interface, it is definitely one of the best options. But what really sets it apart is its ability to add functionality.

3D modeling can be a long drawn out process. If you are a developer or programmer without 3D modeling experience, this process can be daunting, to say the least. This often leaves developers hunting sites like TurboSquid or the Unity Asset Store for free temporary models at the very least, or often times buying final models that don't quite fit their needs.

Recently released accident reports by the state of California's Department of Motor Vehicles show humans did a lot of dumb things to cause accidents with General Motors' (GM) Cruise Automation driverless vehicles in San Francisco this year.