Welcome back, my fledgling hackers! In the first part of my series on Wi-Fi hacking, we discussed the basic terms and technologies associated with Wi-Fi. Now that you have a firm grip on what Wi-Fi is exactly and how it works, we can start diving into more advance topics on how to hack Wi-Fi.

Welcome back, my tenderfoot hackers! This is the third installment of my series on basic Linux skills that every hacker should know. Although some hacking tools are available for Windows and Mac, every real hacker uses Linux—for good reason.
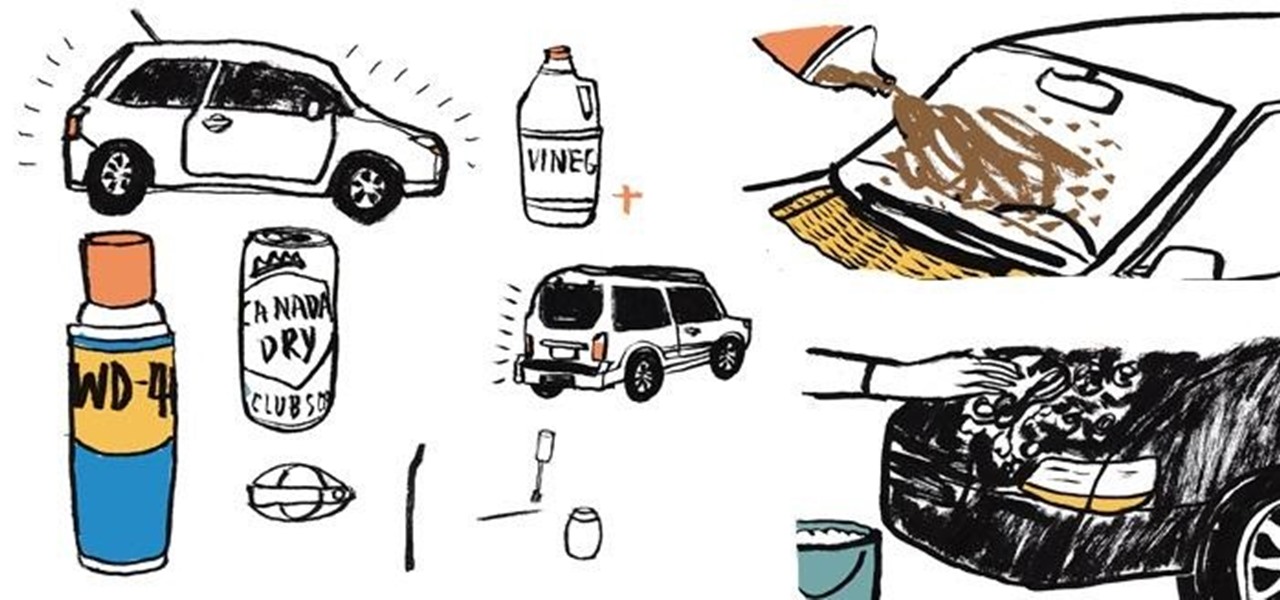
Ever see those cars so covered in dirt, dust, and grime that someone writes "Wash me" on it using their finger? Well, for those cars' sakes, as well as cases less extreme, a word of advice: procrastination is not a solution — it can only compound the problem. Self-cleaning cars are the stuff of the future, not the present, and your car needs attention now.

If you're a Breaking Bad junkie who can't wait for the next episode, satisfy your craving with a little at-home chemistry and make some blue DIY smash-glow crystals! No, this is not Walter White's so-called "Big Sky" or even the subpar cringe-worthy product of his competitors. It's not even the same kind of crystals, otherwise you wouldn't be reading this. This is totally legal, even kid-friendly if you play it safe, though it actually requires more safety precautions than the potassium nitra...

If you are are creating a new computer network connection and aren't sure which IP range to use, watch this video. It will explain the differences between the three IP address ranges and which one would work best for a network of your size.
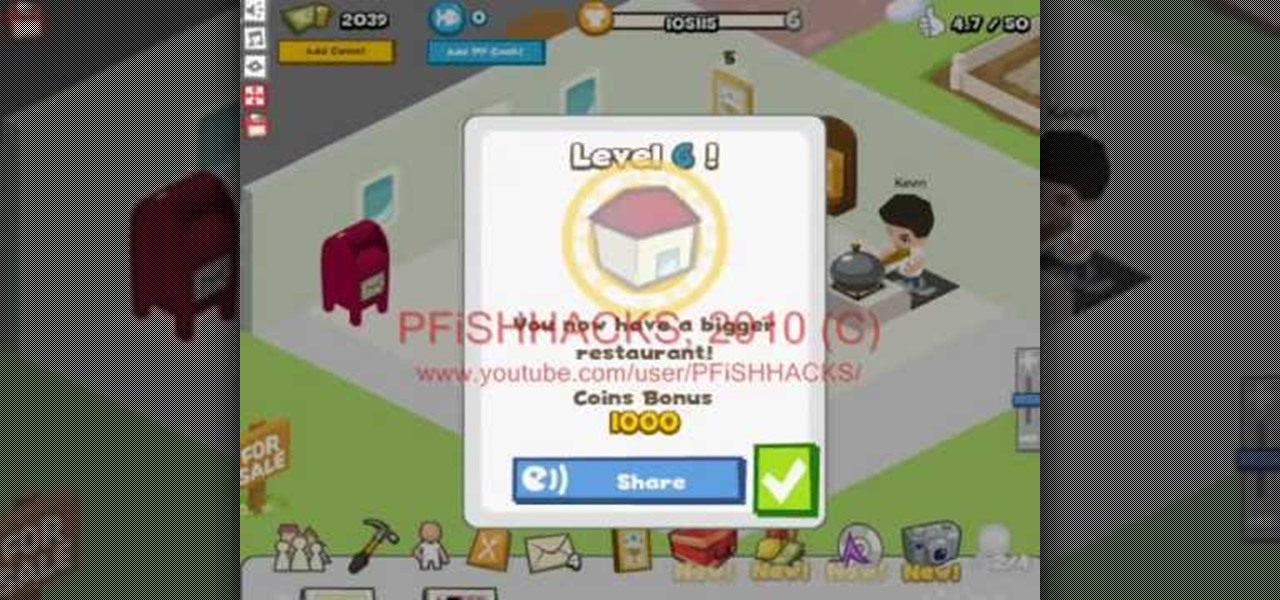
Want to earn coins and easy experience for your Pet Society pet without, you know, actually having to play the game? It's easy. This video guide show you everything you'll need to know to generate unlimited experience and digital cash money.

Want to be the John (or Jane) D. Rockefeller of Restaurant City? Watch this video tutorial to learn how to hack Restaurant City with Cheat Engine 5.5 (02/04/10).

In this language tutorial, you will learn how to use the vocative case in biblical Greek (Koine). The vocative case is the case used for a noun identifying the oblect being addressed. This is a perfect lesson for those who wish to study this ancient language. Listen and repeat the words in this language tutorial and you will be speaking biblical Greek in no time.

Dr. Mercola addresses factors that could degrade the quality of this beneficial form of nutrition. Watch and learn how to make the most out of fish oil supplements.

A short tutorial on how to use the ip deny manager to deny the access to website from particular IP address using cPanel. This Video is provided to you by scandicsoft,(wwww.scandicsoft.fi)

Massage therapy is the application of pressure to the muscles and soft tissues of the body for relaxation and health.

Have you ever thought of building your own social networking site? Before you get to making websites like Facebook, you need to start off smaller, and this 29-part video series is where to begin with developing a social networking community website . Before you start with these lessons though, make sure you have all the following:

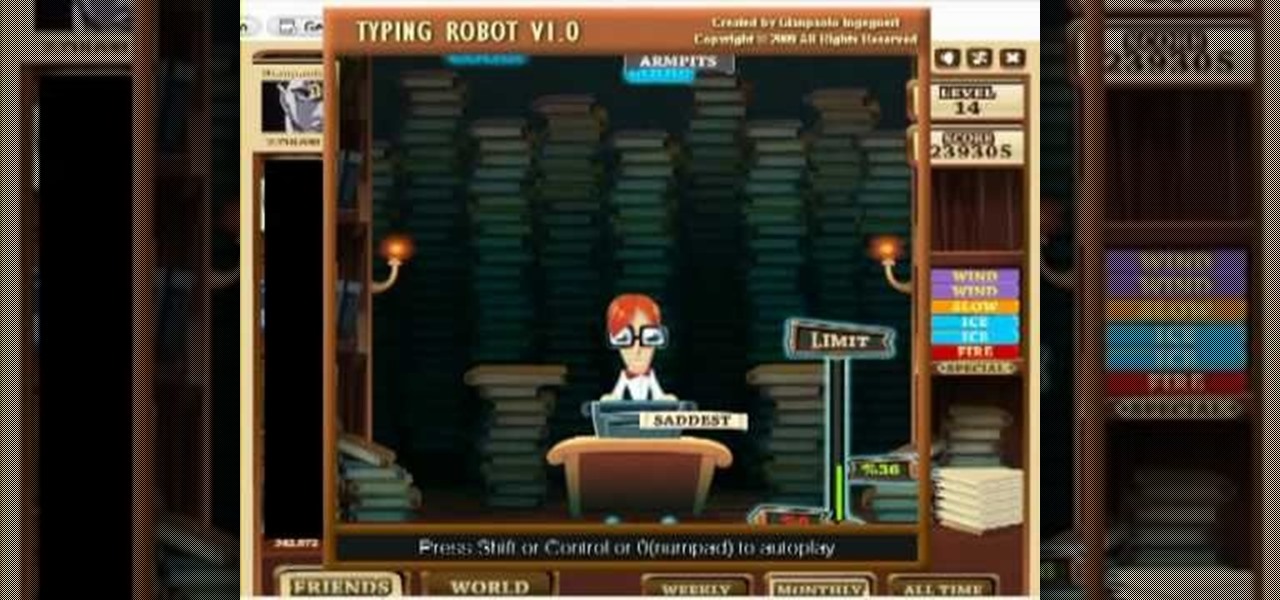
http://www.texturemind.com/post463/ TypingRobot is an artificial intelligence studied to increase your points record with the Typing Maniac game on Facebook. It can recognize several labels because it uses a powerfull OCR system (tesseract) and some principle of word correction. With this program you can make millions of points without problems (my personal record is about 2.700.000 points).

Learn how to follow proper netiquette rules. You may be a model of decorum in person, but a bonehead online. Check out how much you know about Internet manners.

Motors. The word screams of complexity. They're everywhere and in everything, from car engines to airplanes to toys and electric wristwatches. But sometimes the most complex things can be really simple, as in the case of the homopolar motor, where the main point is a magnetic field. The only items you'll need to make a DIY homopolar motor are a AA battery, copper wire and a rare earth neodymium magnet. This tutorial will show you how to build this simple motor.

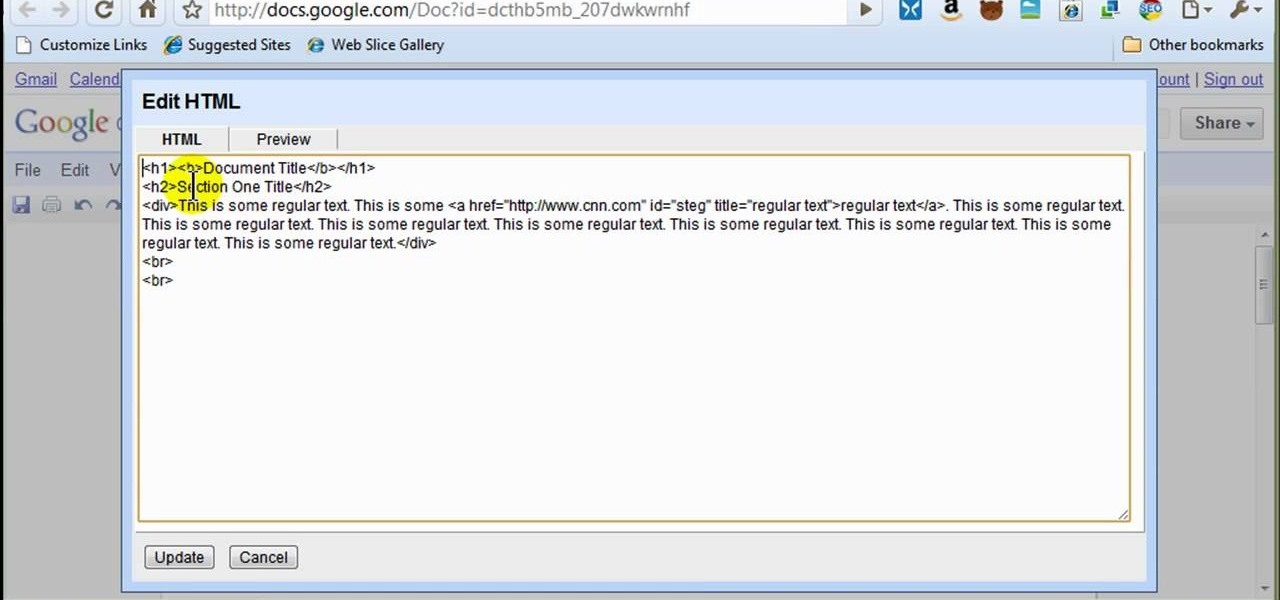
In this how to video, you will learn how to style documents with the Google Docs CSS editor. First, create a new document in Google Docs. First, click on the drop down menu for style. Type in a title in the document. Select heading 2 in the menu and type in the section title. Next, take off the style and type in the body for the content. Select some of the body text and click the hyperlink button. Type in the address and click okay. Now you can click this text to go to a website. Go to file a...

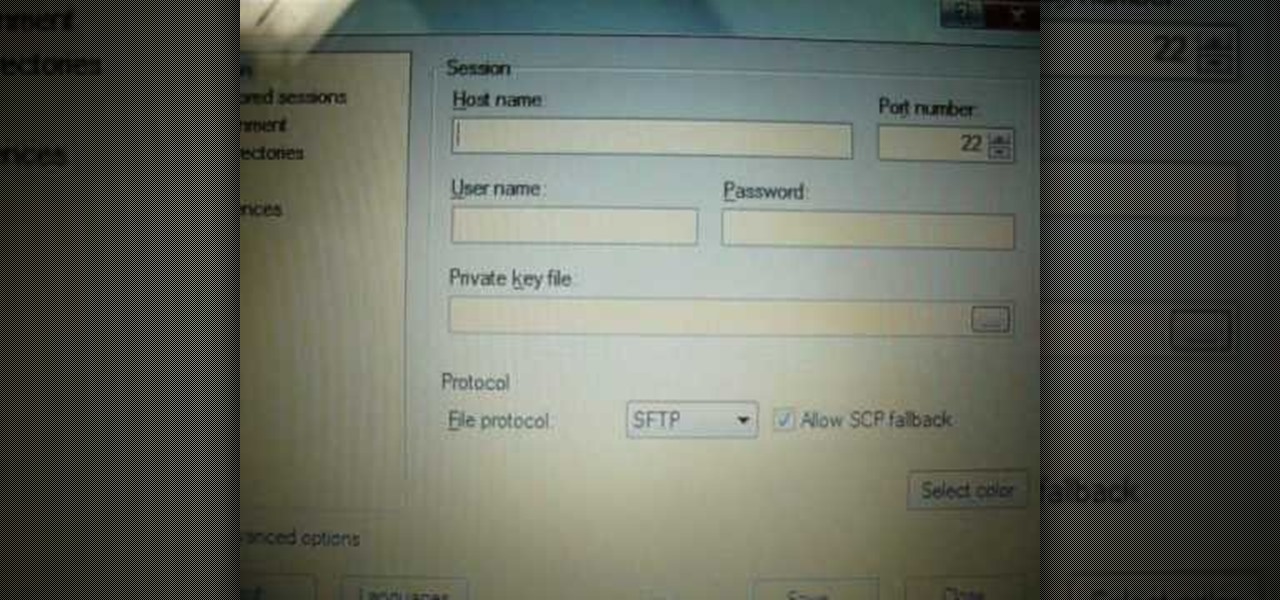
iPodTouchedMaster shows how one can easily SSH into their iPod Touch with all firmware! To SSH is the ability to hack into your iPod Touch's file system. First, your iPod Touch must be jailbroken. Next, you'll have to open Cydia. Click "Featured Packages" or search for the terms "Open SSH" (it will be listed under Console Utilities & Daemons). When you have OpenSSH click on it and click 'Install' and 'Confirm'. After this is finished, click return to 'Cydia'. This may take a lot of battery po...

Learn how to spot a dishonest contractor for home repair. It’s no accident contractors have such a bad reputation – they get more fraud complaints than any other workers! Here’s how to find a reputable one – and skip the scammers.

Thinking of selling your car on the internet? Make sure you don’t get taken for a ride. You Will Need

There are just a few situations in golf that can be addressed with an intentional "chicken wing" swing, but this cool shot is a great way for advanced golfers to get out of severe downhill lies. Mel demonstrates the technique for you in this Mel in Motion video golf tip. Learn how to add the "chicken wing" swing to your arsenal by watching this video golf tutorial.

In this video tutorial we look at how to quickly and easily convert a file using the great free service at www.Media-Convert.com

This is a video which addresses the basics of electric meat grinding, demonstrates deboning Boston butts and shows just a little of the actual grinding.

This video demonstrates how to check your computer for hackers. The video explains a little bit about hacking and shows how to see the IP addresses of the computers connected to yours.

The biggest update to arrive since iOS 18 and iPadOS 18 just came out, and it's packed with new features and changes for your iPhone or iPad. From new Apple Intelligence capabilities to Game Center improvements and new calling tools, there's a lot going on in iOS 18.1 and iPadOS 18.1.

The first step to getting your life together? Getting your online security together. After all, security when you're shopping, video calling, and more means more than ever in a digital age when anyone can copy your info or try to pose as you on the web. This Premium Privacy Bundle featuring Zenmate and StartMail will give you a secure VPN and encrypt your emails, all at a bundled price. The security duo is on sale for 60% off for a limited time, which means it's just $44.99 (regularly $113).

There are many considerations to make when choosing a web hosting plan. Storage space, performance, security, and reliability all matter. The cheapest option isn't always the best idea.

For a hacker, there are a lot of advantages to creating a fake network. One advantage forces nearby devices to use their real MAC address if you happen upon a network that's stored in their preferred network list.

If you've ever wanted to track down the source of a Wi-Fi transmission, doing so can be relatively easy with the right equipment.

It's exciting to get that reverse shell or execute a payload, but sometimes these things don't work as expected when there are certain defenses in play. One way to get around that issue is by obfuscating the payload, and encoding it using different techniques will usually bring varying degrees of success. Graffiti can make that happen.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet.

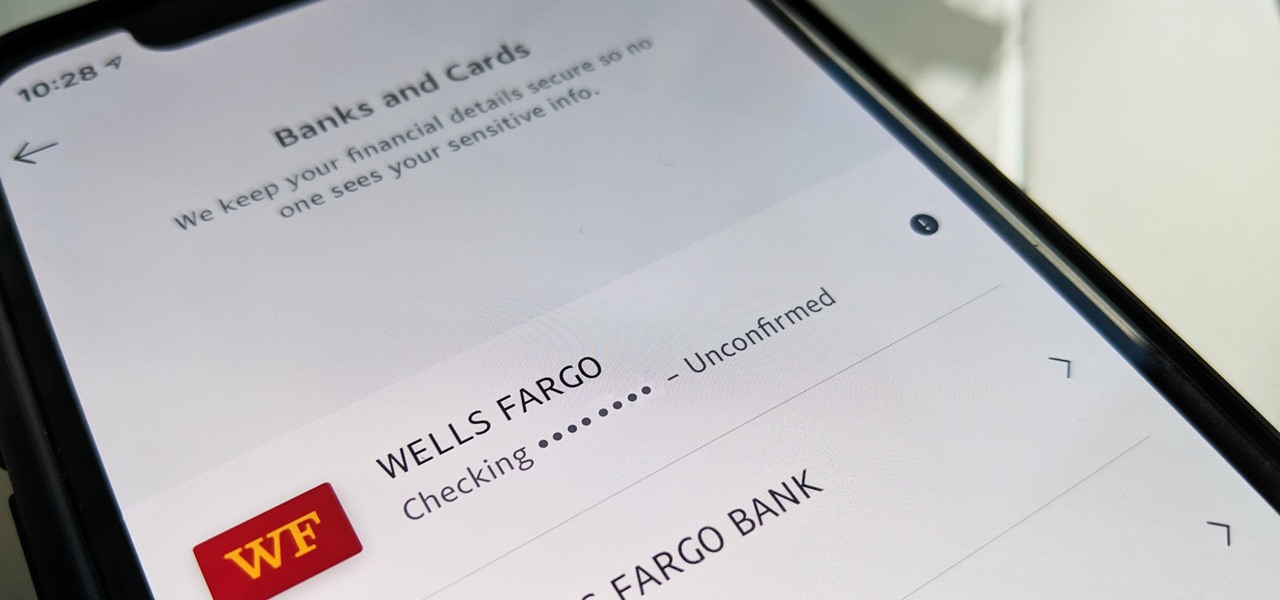
PayPal is one of the most popular payment systems across the globe. It makes payments fast, easy, and secure, and with 250+ million users, it's not going anywhere. If you're new to the online service, one of the first things you should learn is how to add your bank account, credit card, or debit card to PayPal, and make your life easier when it comes to online payments and withdrawals.

For anyone interested in using cheap, Wi-Fi-connected microcontrollers like the ESP8266, the Arduino programming language can be a barrier to entry. Based on C++, Arduino requires knowledge of more computer science than languages like Python. Fortunately for beginners, setting up MicroPython on an ESP8266 allows anyone to write Python on affordable microcontrollers in a matter of minutes.

If you want to carry a variety of network adapters without looking suspicious, a perfect solution is accessing them through Airserv-ng. Tucked away in the Aircrack-ng suite, this tool allows a hacker to plug any number of network adapters into a Raspberry Pi and access them over a Wi-Fi or Ethernet connection.

To be honest, the Mail app for iPhone had always been somewhat forgettable. It lacked many of the features that made third-party clients like Spark and Edison better, but with iOS 13, the gap between Mail and its competitors is much smaller. Apple updated the layout and added many new features to its native emailing app, and that may be just enough to get you to switch back.

Game streaming has never been better. Not only can you watch your favorite Twitch streamer play, but with the new tools being added to YouTube, you can even play along with them. And now, with a solid internet connection, you can stream your Xbox One games to your phone to enjoy console games on the go.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

Apple released iOS 12.2 beta 4 to developers on Monday, March 4, then shortly thereafter also pushed it out to everyone on the iOS 12.2 public beta program. All previous public beta updates for iOS 12.2 were released the following day, but this one changes course. In the iOS 12.2 public beta 4, there are new icons, an updated "About" page, and better Now Playing tile.

Smart home speakers, such as Google Home and Apple HomePod, are must-have accessories if you're trying to turn your home into a smart home. While HomePod is made to be used with the Apple ecosystem, the less-expensive Google Home can also be used with your iPhone — in more ways than you'd think.

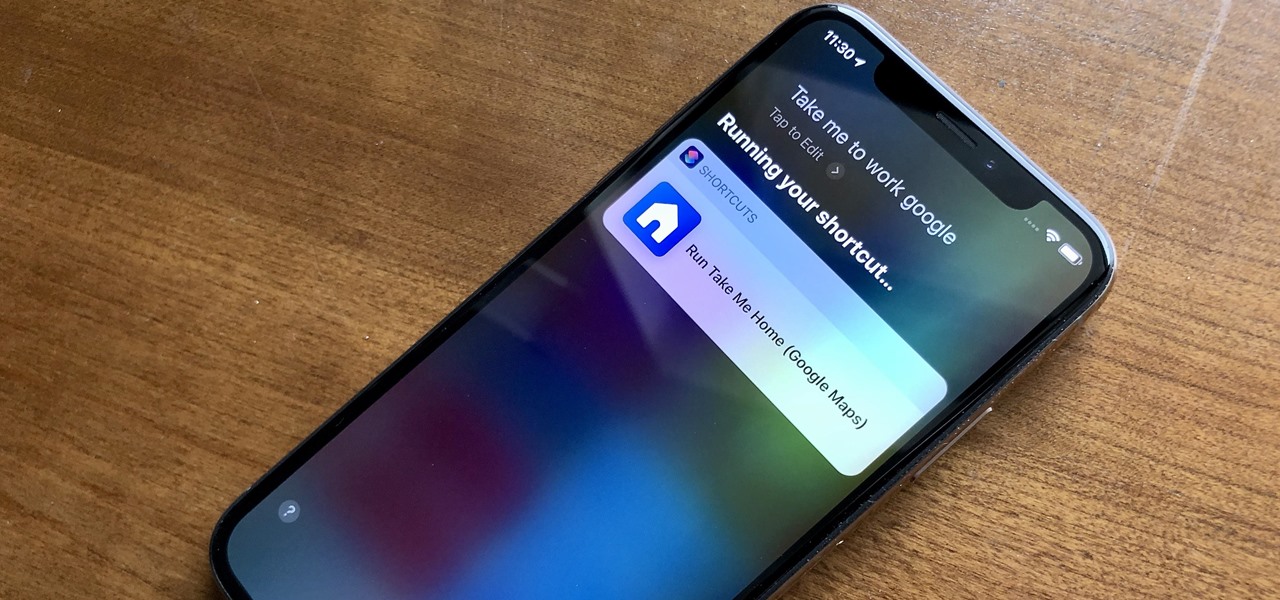
When driving, you can get directions hands-free by asking Siri. You can also make general map searches, show a location's details, call a query's phone number, and view traffic details. However, Siri defaults to Apple Maps for all those. If you prefer Google Maps, Waze, or another third-party navigation app, the map-based Siri commands won't work. But that doesn't mean you can't still use Siri.