In this überbrief video tutorial, you'll find instructions for adding a CNAME record to tinydns. The steps, demonstrated in the video, are as follows: Open up the data file, type a capital C, the domain you'd like to use, or subdomain, the IP address of the machine or destination you'd like that hostname to route to and the TTL or time to live. Save the changes, type make, and test it out!

This video demonstrates how to use SSH to connect remotely to your server using its IP address. If you do not have the IP addres of your server, you'll need to obtain it before SSHing into your computer from a remote location. Watch this tutorial for a step-by-step walkthrough of the process.
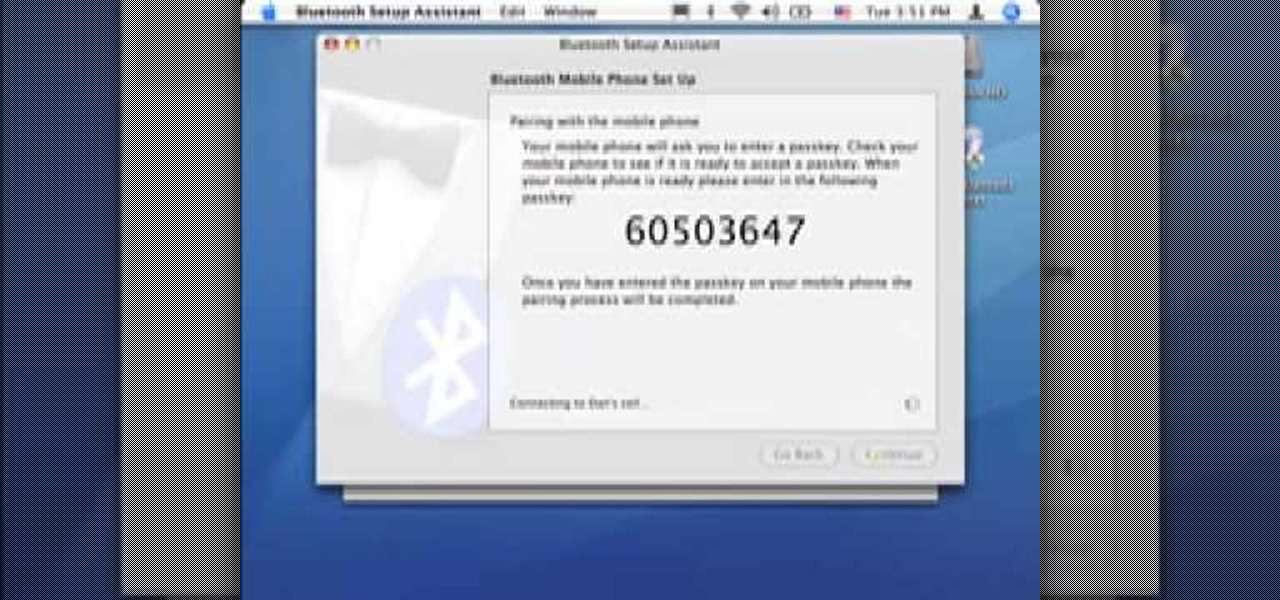
Did you know you can sync up your cell phone (any cell phone with Bluetooth) with your MAC computer? Doing so will enable you to do several things, including importing and syncing your address book, iCal (calender application), and even tethering your phone with your computer so you can get internet.
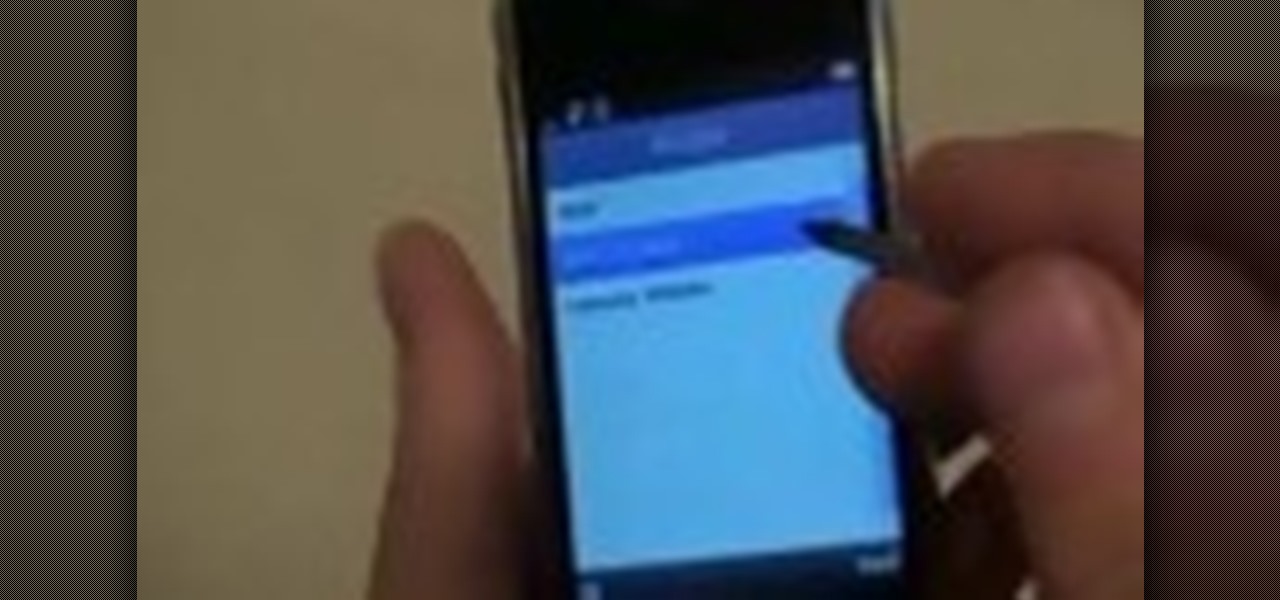
Do you have a Sciphone? With its internet capabilities, you can check your email or surf the web. Take a look at this instructional video and learn how to set up your internet on the Sciphone 168. In order to set it up you need to contact your service provider for information such as an IP address, etc.
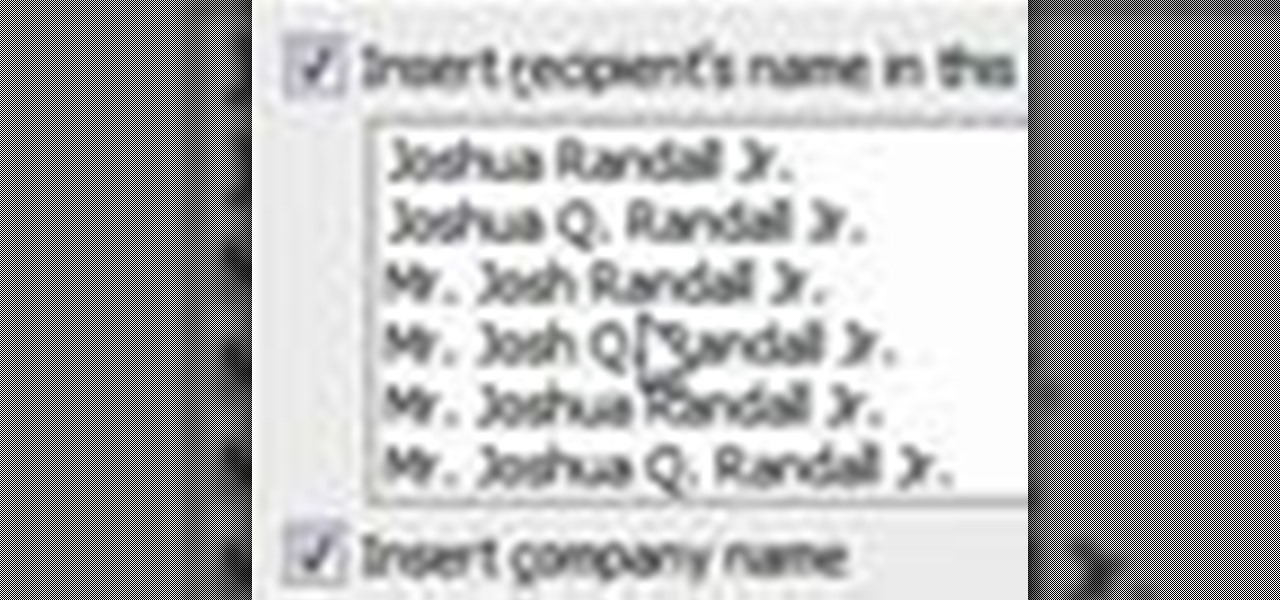
This video shows how to set up a mail merge in outlook which allows you to create a document then send it to your address book. A great tool in Outlook

Make copy-and-paste chores a snap with this quick Firefox tweak from Tekzilla. Just type about:config into the address bar, find "middlemouse.paste," the double-click on the value to change it from false to true. That's it. Anything you cut in Firefox you can paste back into Firefox by clicking on the scroll wheel in-between the buttons on your mouse.

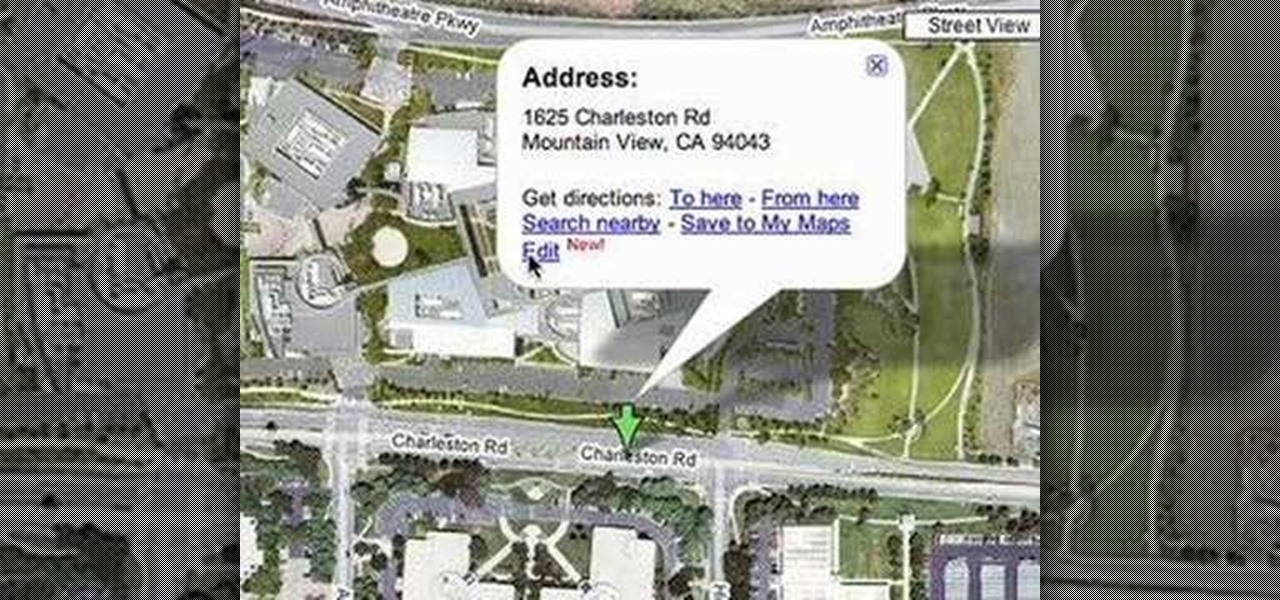
Now you can edit the physical location of any address in the US in Google Maps. You can correct your home, your business, or even your favorite park. Try it at maps.google.com

Tired of Windows and Mac OS? You might want to try Ubuntu or some other variation of the Linux operating system. The Lab Rats, Andy Walker and Sean Carruthers, teach you how to install and run Ubuntu on your system. They also address several concerns you may want to be aware of.

There's such a variety of massage styles to choose from today. Take Shiatsu and Thai massage. They're based on traditional Asian medicine, and are designed to address aches and pains, but are also aimed at balancing the energy of the body to improve health and well-being.

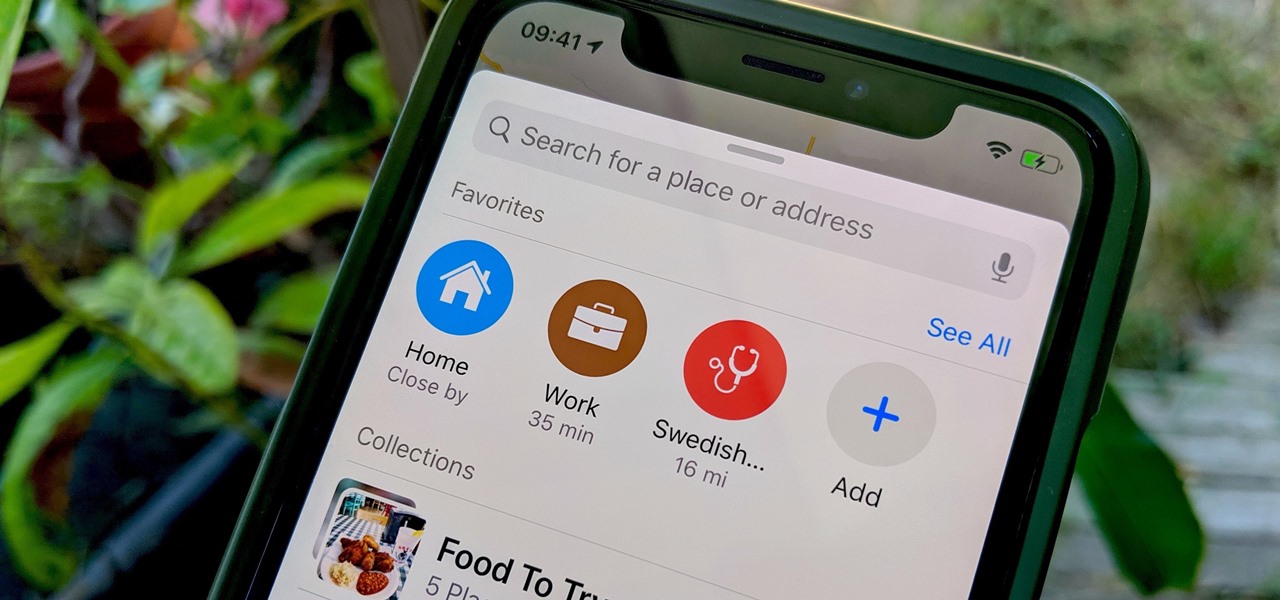
In iOS 13, Apple Maps makes it easier for you to organize essential places on your iPhone, allowing you to save locations as favorites that you can access at a glance.

With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.

Featured on MTV's Catfish TV series, in season 7, episode 8, Grabify is a tracking link generator that makes it easy to catch an online catfish in a lie. With the ability to identify the IP address, location, make, and model of any device that opens on a cleverly disguised tracking link, Grabify can even identify information leaked from behind a VPN.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith's computer.

The most convenient way for US users to buy Ripple (XRP) or Stellar (XRM) is through Binance. However, you can't deposit money directly into this app, but you can deposit cryptocurrency like ether or bitcoins to buy other alt-coins. The easiest way to do that is by using Coinbase, the most popular cryptocurrency app.

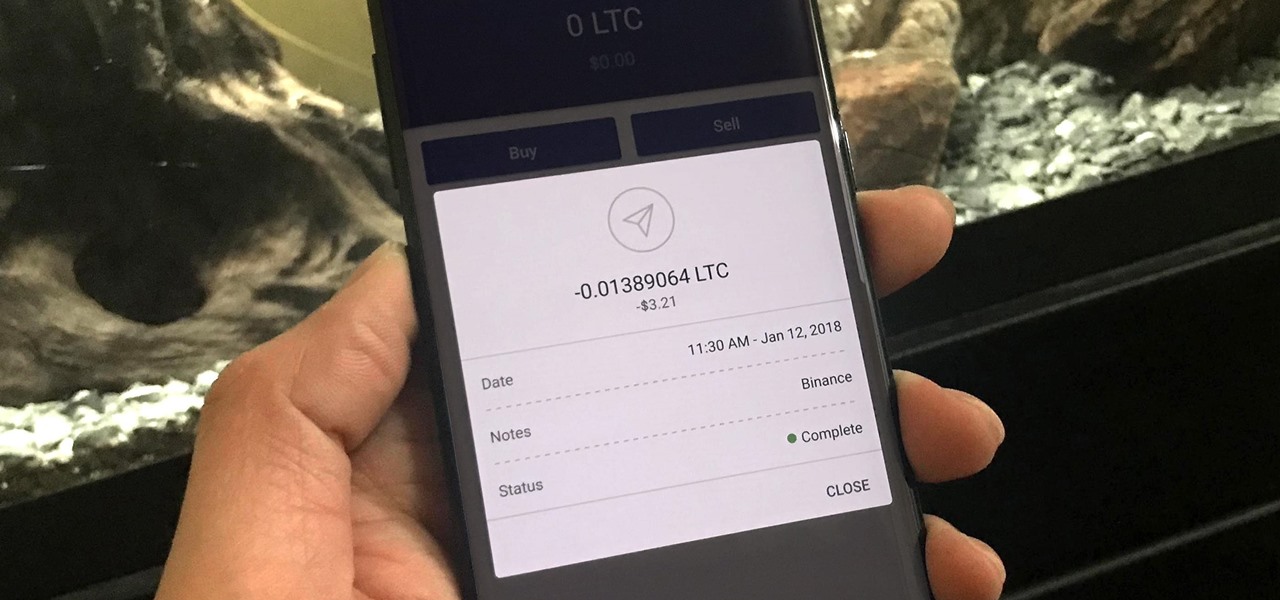
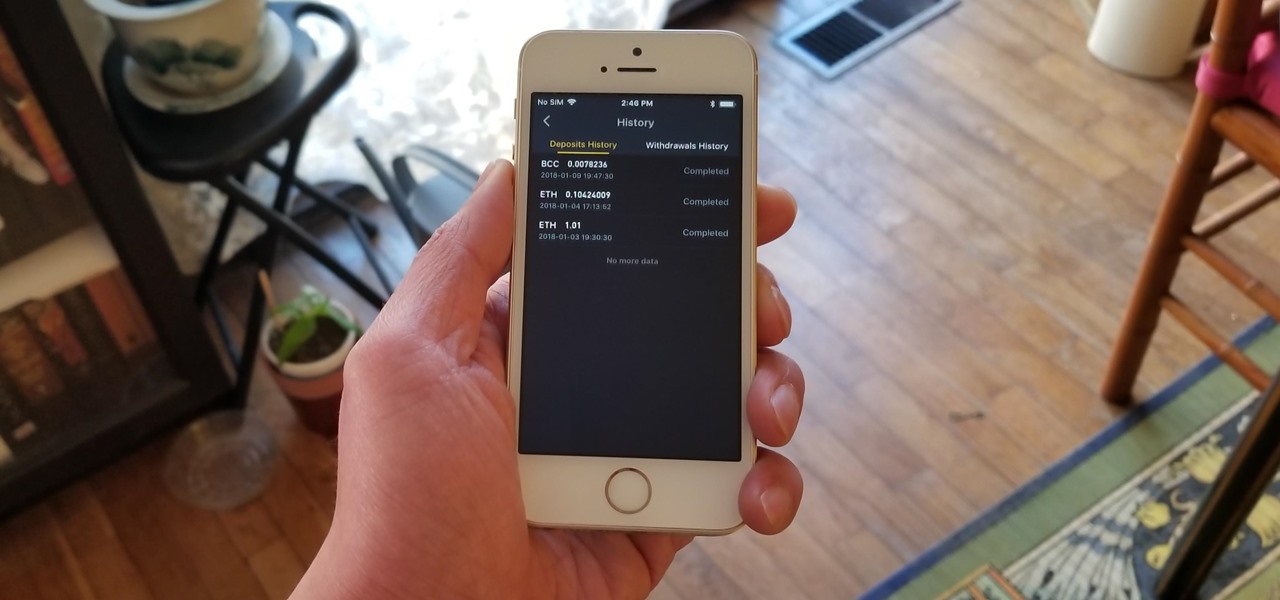
As cryptocurrencies gain mainstream acceptance, it's not far-fetched to think that we'll one day be able to buy alt coins like Ripple (XRP) and Stellar (XLM) using debit cards and bank accounts. Until then, we'll have to rely on using bitcoins and ethereum to buy digital coins. Thankfully, depositing and withdrawing cryptocurrencies with Binance is relatively hassle-free.

Sometimes you need a password to gain access to an older running Windows system. Maybe it's a machine in your basement you forgot about or a locked machine that belonged to a disgruntled employee. Maybe you just want to try out your pentesting skills.

Hello, this is my first post on Null-Byte. This is made for those who have an interest in writing into another processes memory. Why would you want to do this? Who knows, personally I just wanted to mess around with games on my computer(have unlimited health).

Hello ladies and gentlemen, welcome back to the Part 2 of our UDP & Wireshark adventure as I promised. Last time we discussed about what DNS is and how it uses UDP as its transport protocol but we left some unexplained parts behind and I'm about to investigate those with you. I would advice you to go back to Part 1 so you can have a clear understanding in case you don't feel comfortable with the topic. So our computer made its request to the DNS server and asked "Hey, I want to find out what ...

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the victim portion of the shell. Today, we'll be building the attacker portion. This script will initialize interaction with the victim portion of the shell, send commands, and receive the output.

Greetings my fellow hackers.

If you're a U.S. expat living, traveling, or studying abroad, or just someone who typically uses virtual private networks (VPNs) in order to access the North American video libraries of services like Hulu or Netflix, you were probably surprised to see that these video streaming services don't work on your Chromecast or Chromecast 2.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Welcome back, my greenhorn hackers! Although we have focused primarily on technical hacks here, social engineering can sometimes be especially effective. This one requires a bit of technical skill, but not too much. In addition, it's limited by how specific a target you can choose—but it will work.

Welcome back, my hackers novitiates! As you read my various hacking tutorials, you're probably asking yourself, "What are the chances that this hack will be detected and that I'll land behind bars, disappointing my dear mother who already thinks I'm a loser?"

Welcome back, my greenhorn hackers! Recently, I asked the Null Byte community what subject they would most like me to cover in future tutorials. Many of you cited scripting, and I decided it's best to cover this subject soon, so here goes.

Welcome back, my hacker apprentices! My recent posts here in Null Byte have been very technical in nature, so I thought that I'd have a little fun with this one.

One of the most frustrating things on the Internet are sites that make you register just to view content. I'm not talking about paywalls—I mean the sites that make you give them personal information to look at free articles or forum threads. Most people are uncomfortable with this because a lot of these sites either spam you themselves, or sell your information to someone else who will.

Security researcher and iPhone hacker pod2g has brought attention to a flaw in Apple's iOS that allows the user to change the reply address of an SMS message. This bug has been a part of the iPhone's SMS since the first iPhone in 2007, but Apple has yet to address it. Basically, there's a section in the text payload called User Data Heading (UDH) that controls some advanced features, one of which is the reply address. By changing the reply address of a text message, you can make someone send ...

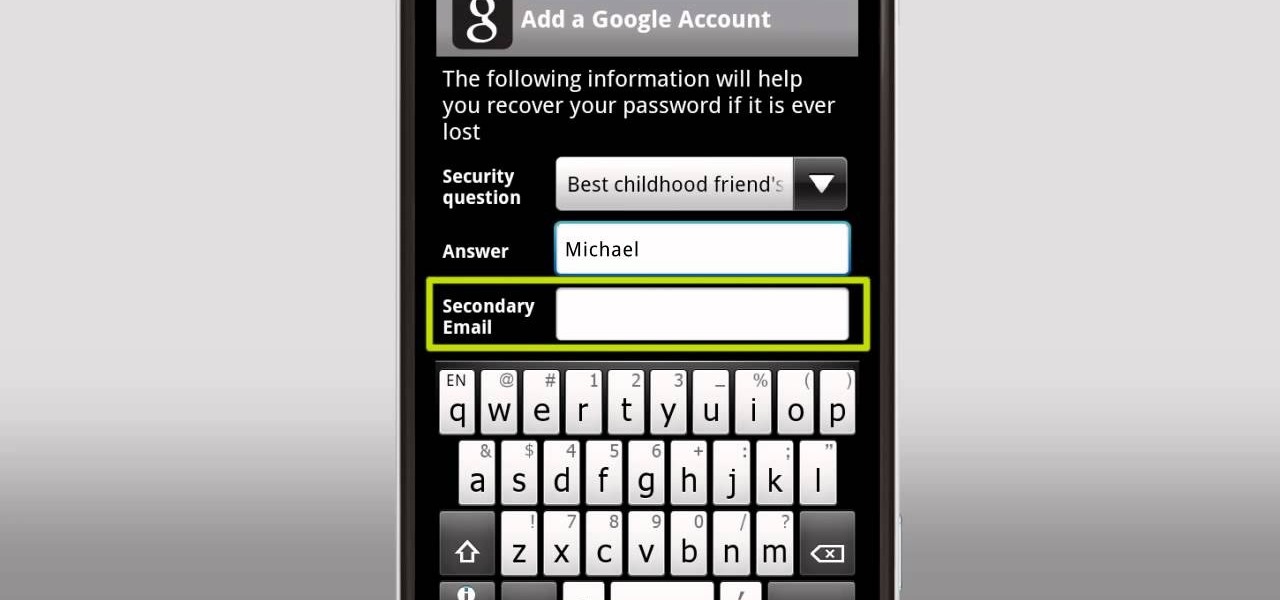
Use your Gmail as your primary email account on your myTouch 4G! This clip will teach you everything you'll need to know to set up and use a Gmail address. Whether you're the proud owner of a T-Mobile myTouch 4G Google Android smartphone or are merely toying with the idea of picking one up sometime in the near future, you're sure to be well served by this brief, official video tutorial from the folks at T-Mobile. For complete instructions, watch the video!

In this video you will learn how to add various links from Google Maps to an email. The first step you will need to accomplish is to find a section of map you wish to attach to an email. After you have the section of map in view you will see a copy link option at the top right of the image. After you select the copy link you can now open your email program. Once you've accessed your email select attach link and copy/paste the address into the link field. The map image will now be properly att...

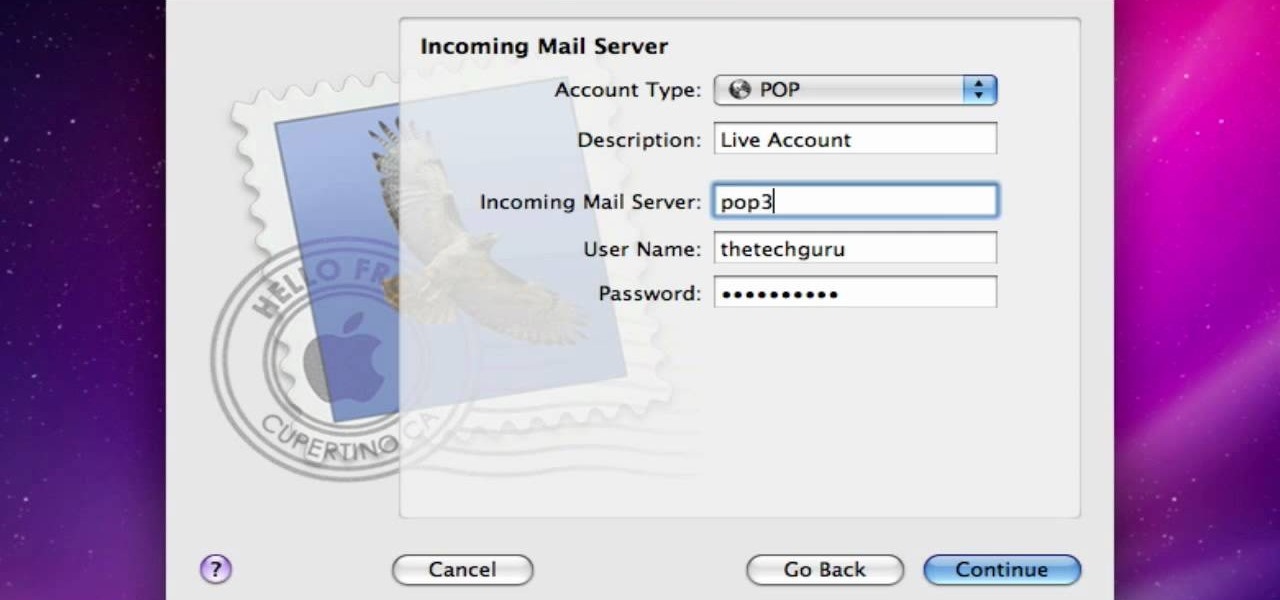
In this video from AppleGenius0921 we learn how to enable a Live/Hotmail account on the Mail application on a Mac. Open Mail. In full name put your full name. Type in your email address and password and continue. Leave the account type on POP and name the description what you'd like. The incoming mail server is pop3.live.com. Type in your live.come username with @live.com in it! Click Continue. The outgoing mail server should be smtp.live.com. Check use only this server and check use authenti...

In this tutorial, we learn how to unblock Facebook or MySpace at school or work. First, go to your start menu and run "services". After this window pops up, look for DNS client and then right click on it. Then, click "stop". After this, restart the browser that you are on with your computer. From here, type in the address of the website that you want to go to. It should not be working and you will be able to go onto the website without any problems! This is a great way to get past blocks your...

In this tutorial, we learn how to block a website using a Linksys Router. First, go to your web browser and type in "192.168.1.1" into the address bar. After this, you will need to enter in your username and password to the pop up window. From here, go to the tab that says "access restrictions" and look for where it says "policy name". Type in 'blocked website' to the bar and then click 'enable'. From here, go down to the bottom of the page and enter in the URL of the website you want to bloc...

In this tutorial, we learn how to configure Outlook 2007 to work with Gmail. First, go to the start menu and then open up Outlook. From here, go to tools and then options. After this, go to the mail setup tab and then click e-mail accounts. Then, click on "new" and then next. Enter in your information in the blank boxes on the screen. Then, enter in your e-mail address and make sure the server is not checked on this screen. From here, you will continue to go through the wizard until it's comp...

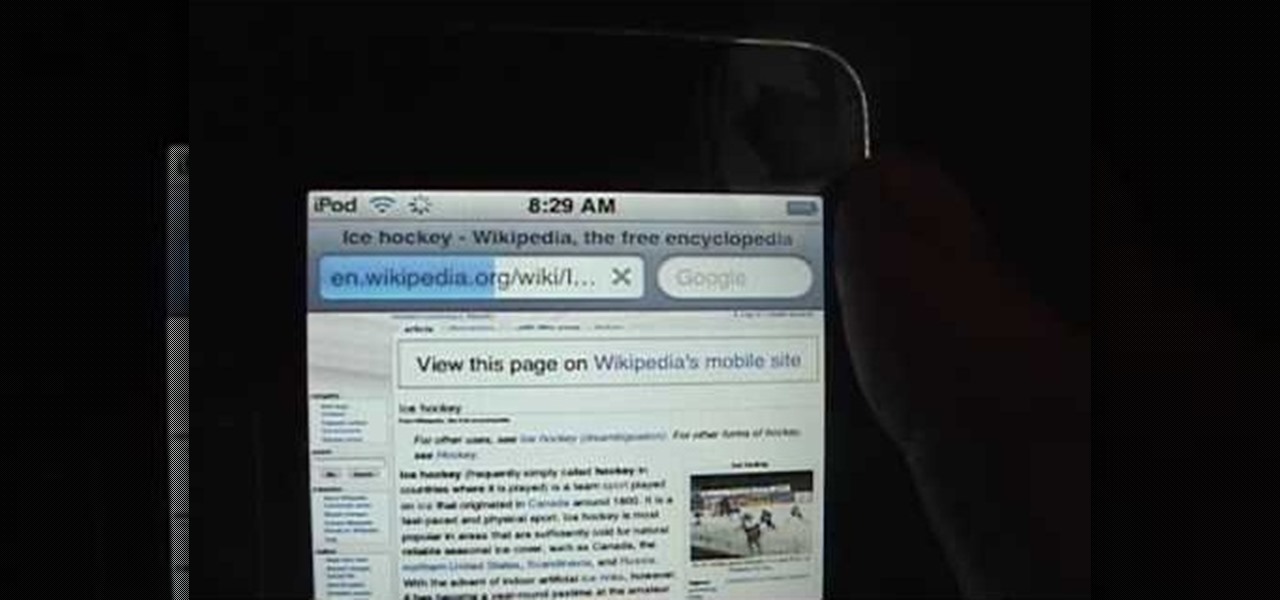
In this video, we learn how to view the internet on your iPod Touch or iPhone. First, you will need to look for the Safari sign on the bottom of your phone. From here, you will be led to the Google home page. You can click on the box to get the on-screen keyboard and type in what you want to search for. After this, the results page will show up. To go to a website, you just simply need to type the exact site into the address bar and then it will load for you! This is simple and easy, just tak...

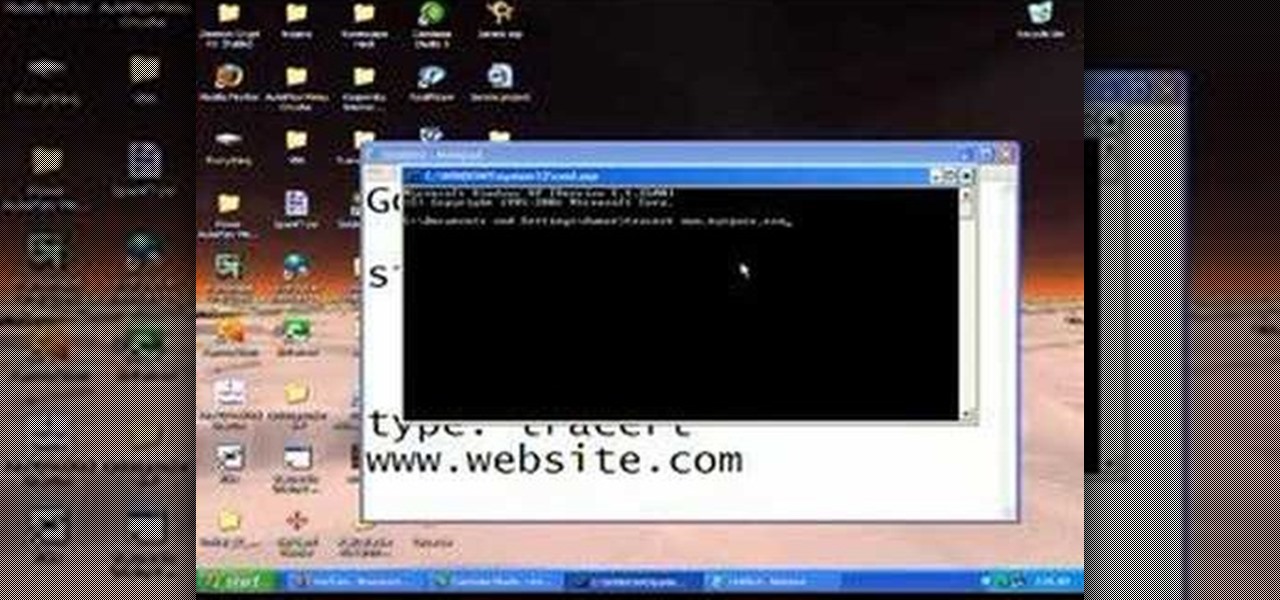
In this video, we learn how to hack school filters to get on Facebook with Tracert. First, go to the start menu and then type in "cmd" into where it says run. After this, type in "tracert" and then the website name. Wait for all of the information to fill in in the black screen. Then, copy and paste the IP address that appears inside. Now you can take this and use it to go to Facebook while you are at school. Or, you can go to any website that you'd like to that you normally can't go to at sc...

In this video, we learn how to send documents for review by email in Acrobat 9 Pro. First, go to the comment button and choose "attach for e-mail review". A wizard will now open with an e-mail based review. Anyone who has Adobe will be able to open this up. Use a PDF file that you want to use, then click "next" and invite your reviewers by typing in their e-mail addresses or finding them in your address book. Then, add in the subject and send the e-mail. From here, the document will send and ...

This is a video tutorial in the Software category where you are going to learn how to revert to the Fixedsys font using mIRC. Click on the channel icon and select font. Here you can select the font and the size and then click OK. If you have Windows XP or older version of Windows, you can type in fixedsys in the font window, select the size, click OK and the fixedsys font will be selected. But if you have Vista or Windows 7, this will not happen. So you bring up the Windows explorer and in th...

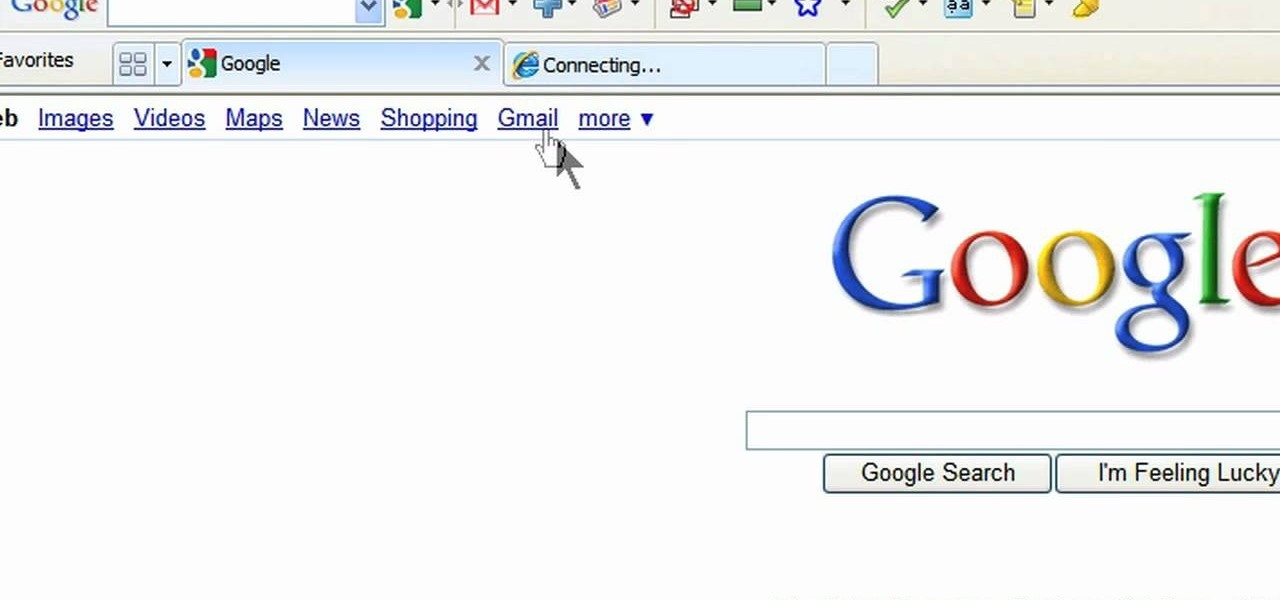
In this video, we learn how to add the Gmail button to the toolbar. First, log onto Google and go to your Gmail account. After this, drag the icon for the Gmail to the toolbar on the screen. After you do this, test out if it is working correctly. Exit out of your browser, then go back into it. Now, click on the icon that has the envelope with red outlining. Once you click this, a new tab should open up with your Gmail opened up! This is great if you want to check your e-mail quickly, without ...