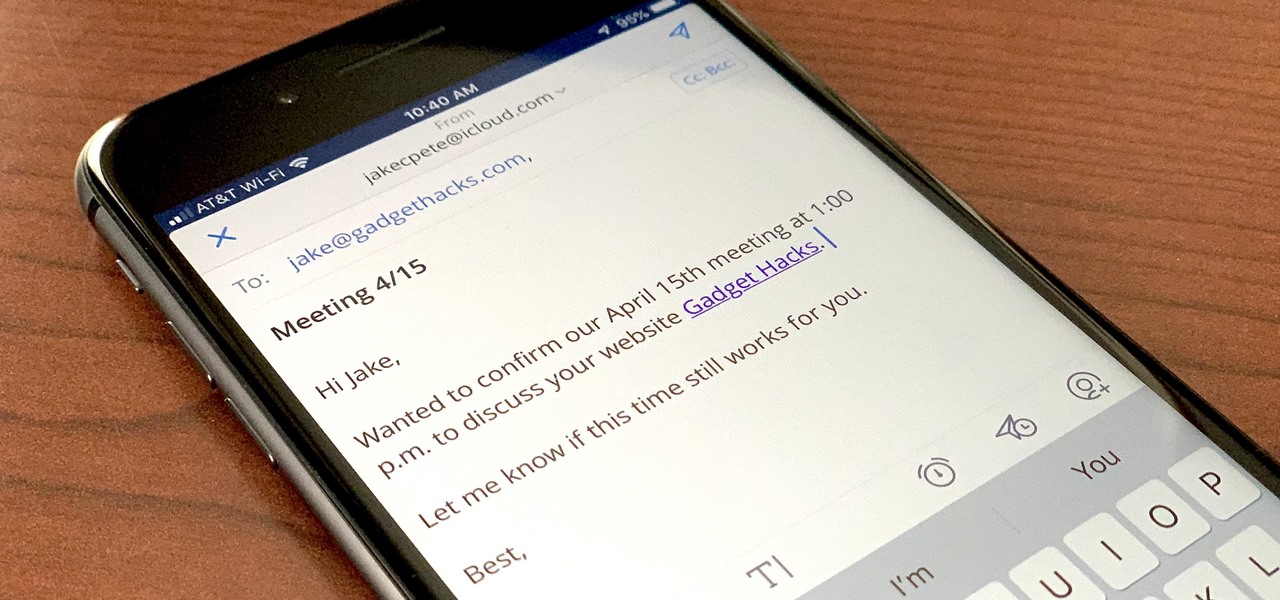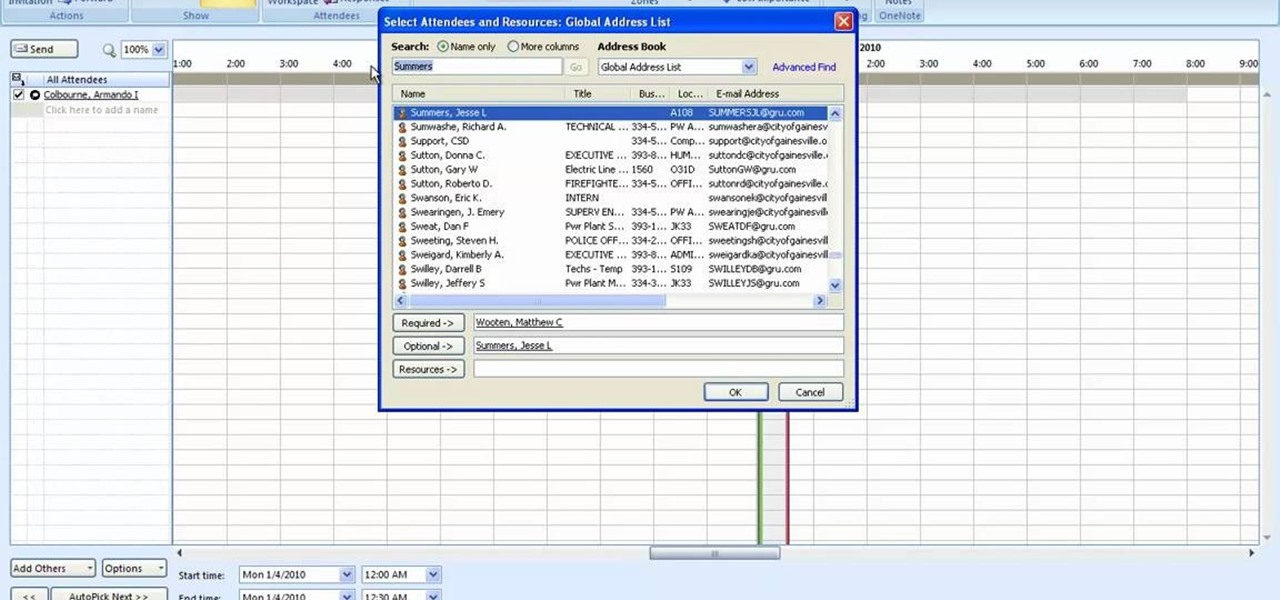
This how to video shows you how to setup a meeting using Microsoft Outlook. First, open the program. From here, click on calendar. Next, go to the upper left corner and select new. On the subject line, type in the subject of the meeting. In the body, type in what the meeting is about. Go to scheduling and go to the left and select invite attendees. From here, select the address book and search for people by their last names. Select who is optional and who is required. Click okay. You will see...

This video tutorial from Mark Dusting shows how to create and edit wiki page in Wikispaces. To start, open internet browser and go to www.wikispaces.com.
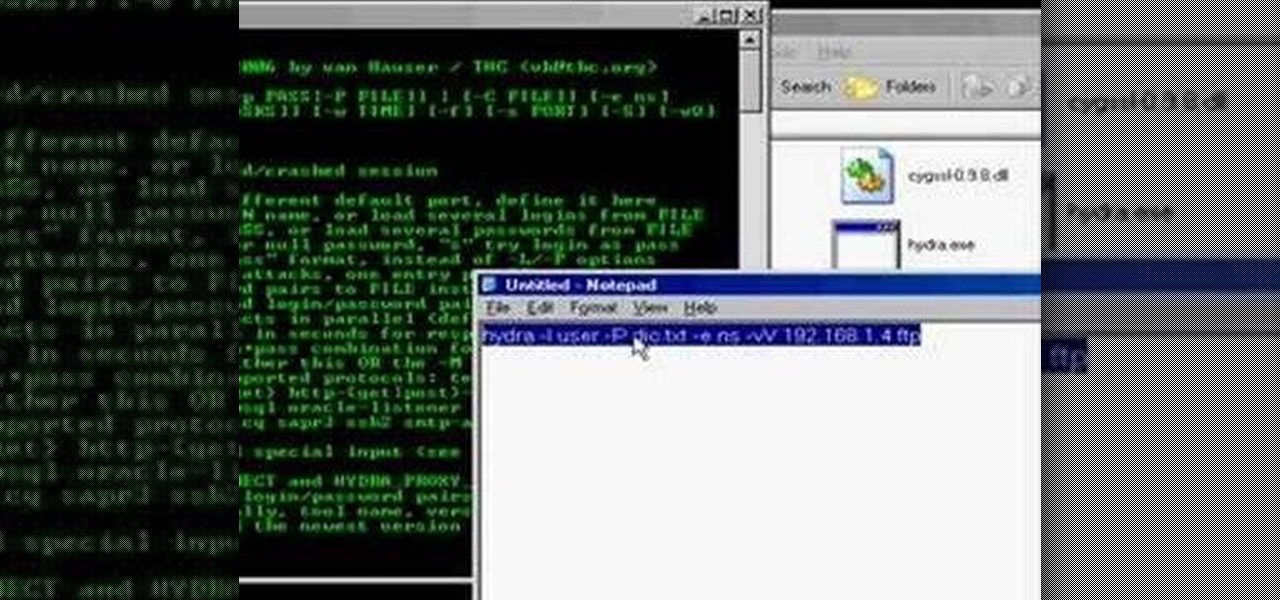
This is a how-to –video on using hydra 5.4 to crack FTP passwords. This video is intended for educational purpose only. It reveals the basics of hacking a FTP server using dictionary search technique. Here are the steps involved.

In this how to video, you will learn how to speed up your Azureus Vuze program. First, open up Azureus Vuze. Next, go to advanced, option, and click preferences. Select preferences and change the port to a number between 49152 to 65535. Once it is changed, go to transfer and make sure that these are set to zero. Once that is done, open your web browser and type in your default gateway. To find this out, go to system preferences, network, and router. Next, enter your user name and password to ...
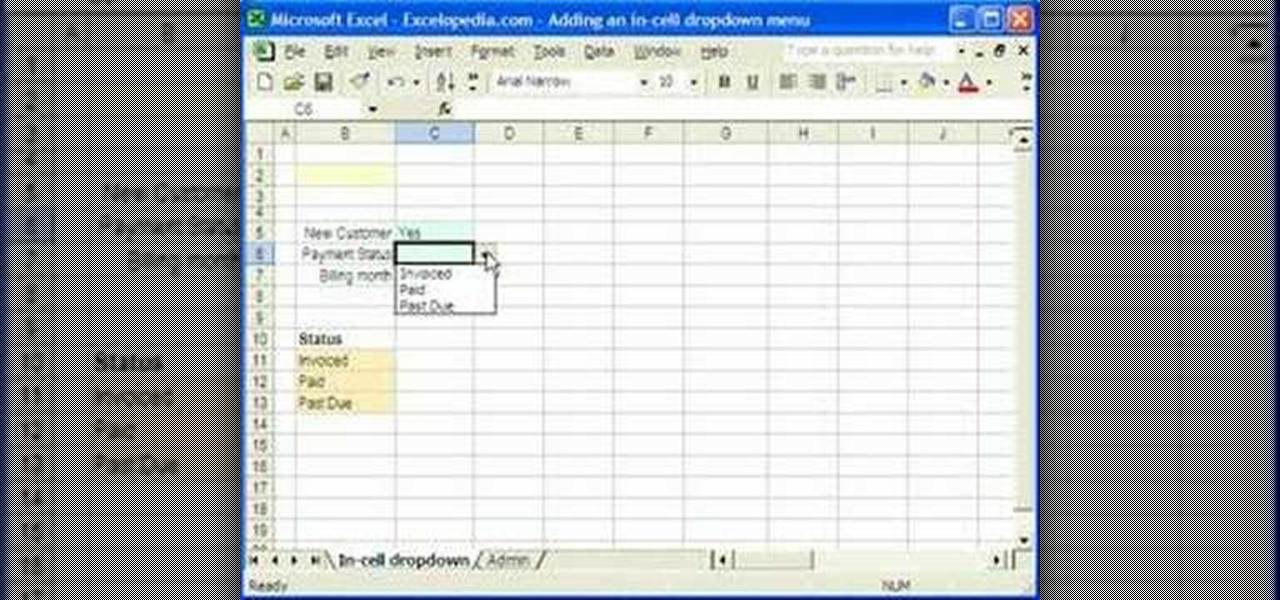
1. Select the cell for which the dropdown menu is to be applied. 2. once the cell is selected goto DATA menu select VALIDATION.Data validation dialog box will be displayed.

WeaponCollector teaches viewers how to make a mini survival kit using an Altoid's tin. You can get an S.A.S. guide for exact instructions and further information on what you will need in an survival kit. First, you should make sure you have rubber bands around your tin to hold it shut. It is easier to get into it and it keeps it closed. You can also wrap the tin with a power cord. Elastic bands work better if you plan on using this everyday. Simply wrap 3 bands around the width and one around...

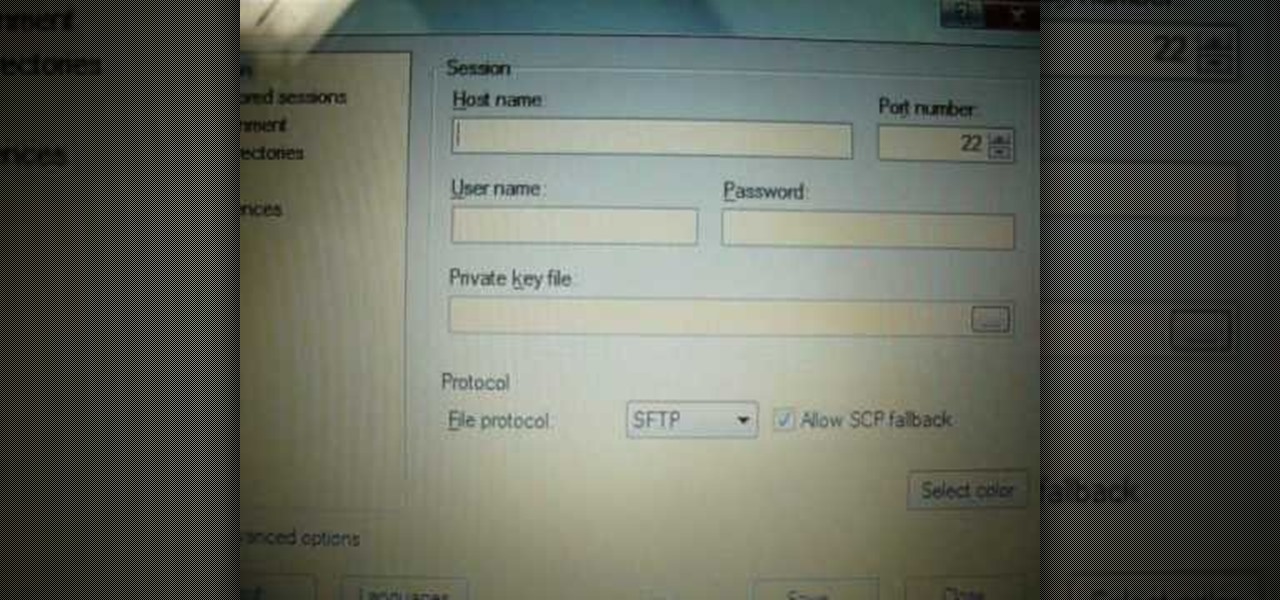
HighQuality Tutorials demonstrates how to change your iPod Touch alpine default password. Changing the default password is useful when using your iPod Touch in a public setting to make it less vulnerable to hacking. To change the default password, first open up your internet connection and search for Putty. Download the Putty program. Open and run the Putty program. Your host name will be your IP address for your iPod Touch. Select port 22 and SSH and open up the program. Log in as root and c...

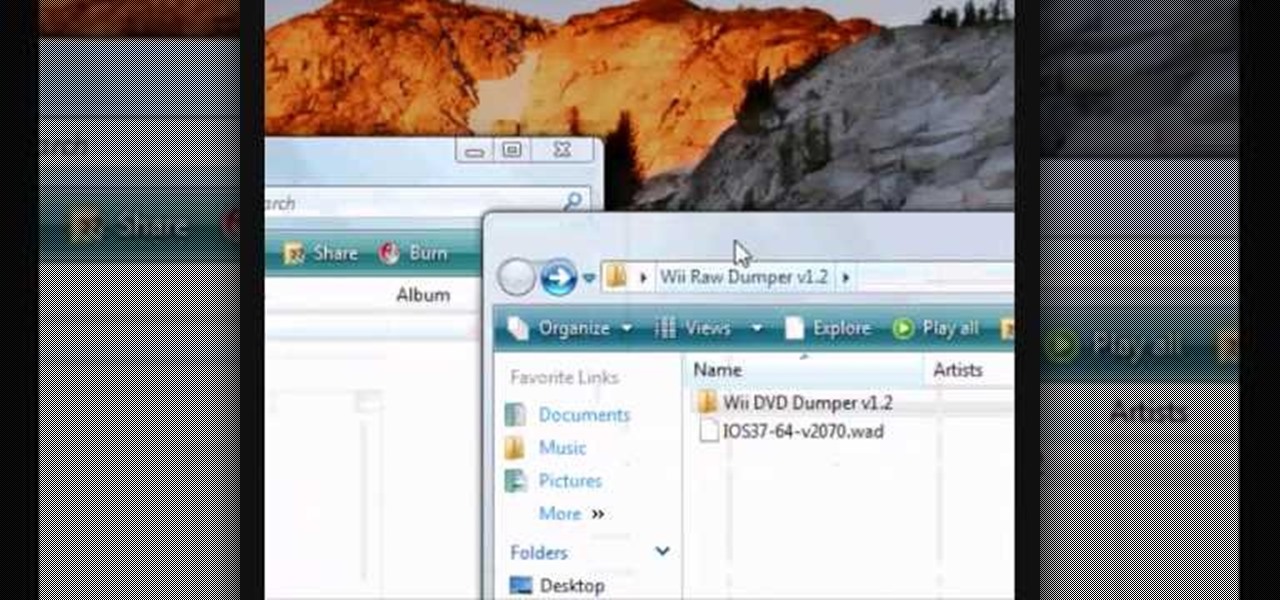
This video tutorial from noxad presents how to backup and burn games for Nintendo Wii game console.To setup game transfer from computer to your console you'll need any type of SD memory card. In this tutorial it's Lexor 1 GB SD card.Insert SD card into your computer card reader. Autoplay window will open, asking what action you want to perform. Select Open folder to view files.You can open SD card manually from My Computer window. (Start button-Computer).Make sure your SD card has folder name...

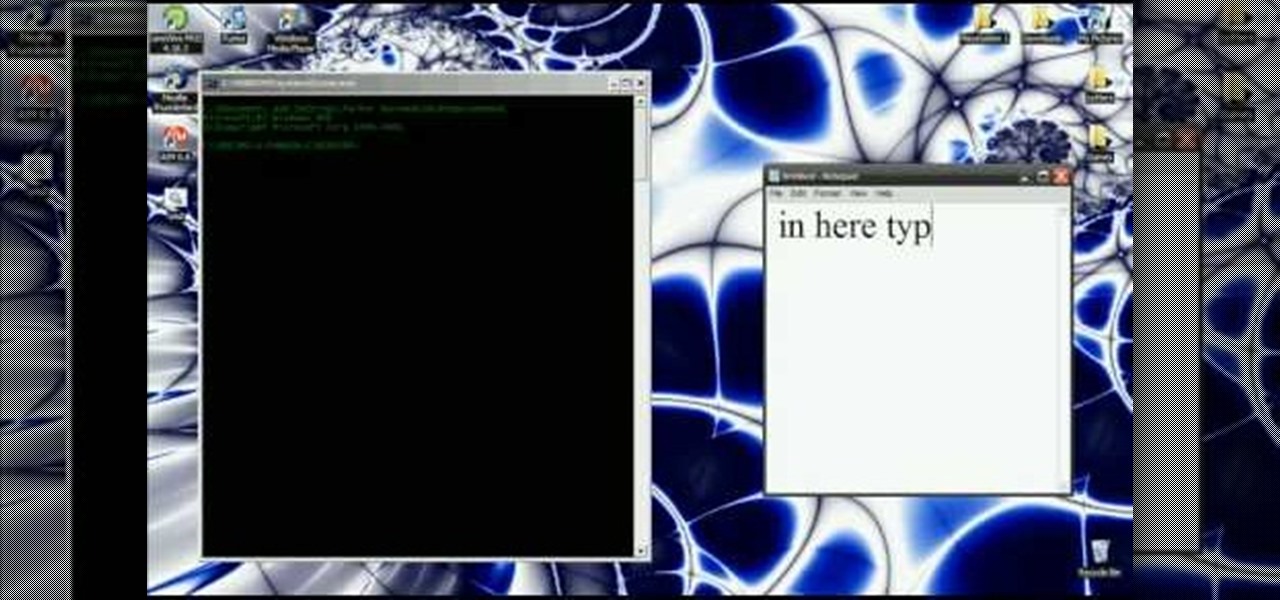
In this video you will learn how to get past website blocks on your school network. Some school computers have command prompts blocked. If this is the case then you will want to open a notepad. In the notepad type command, then save as something school related, making sure the file name ends with .bat. Do not save it on the desktop, but rather in a folder deeper on the unit. Once you've saved it, make sure no one is looking, then open the file. It will bring up a blank black window. In the bl...

This video demonstrates how to use Skype to make calls. The best thing about it is that it is free. You only need a computer, a microphone and a web camera. To use Skype, you first have to download the Skype software. This can be done through the website of Skype. Then install the Skype on your computer. Next you need to have an account created. For this you have to provide a screen name and also your email address. You need to type a password for your account too. Once your account is create...

This video is a tour of circlepad rather than a tutorial, for people who would like to make web pages without having to learn html using circlepad.

If you don't have a Wi-Fi network, you can still easily SSH into your iPhone. Just follow the steps outlined in this video tutorial. First, you will need a Mac or iPhone along with Fuju. Just download the program. Once you have all of this, click on the Wi-Fi bar and click on Create New Network. As a name, click on iPhone SSH and click Manual. This creates your new network, which you will see on the desktop. Double click on it and then look at your iPhone. Go to iPhone. Connect to the network...

Video demonstrates tutorial of how to hide the logical drive icons in Windows. In the demonstration there is two partitions C and D and also there is a DVD drive, DVD Rom and DVD Writer. Here drives C, D and F from My computer is going to be hidden with help of utility called “No Drives Manager”. If you don’t want your young ones to access some of your important data you can hide it. It will just be hidden. This means if go to the address bar and types the name of the drive you can go to that...

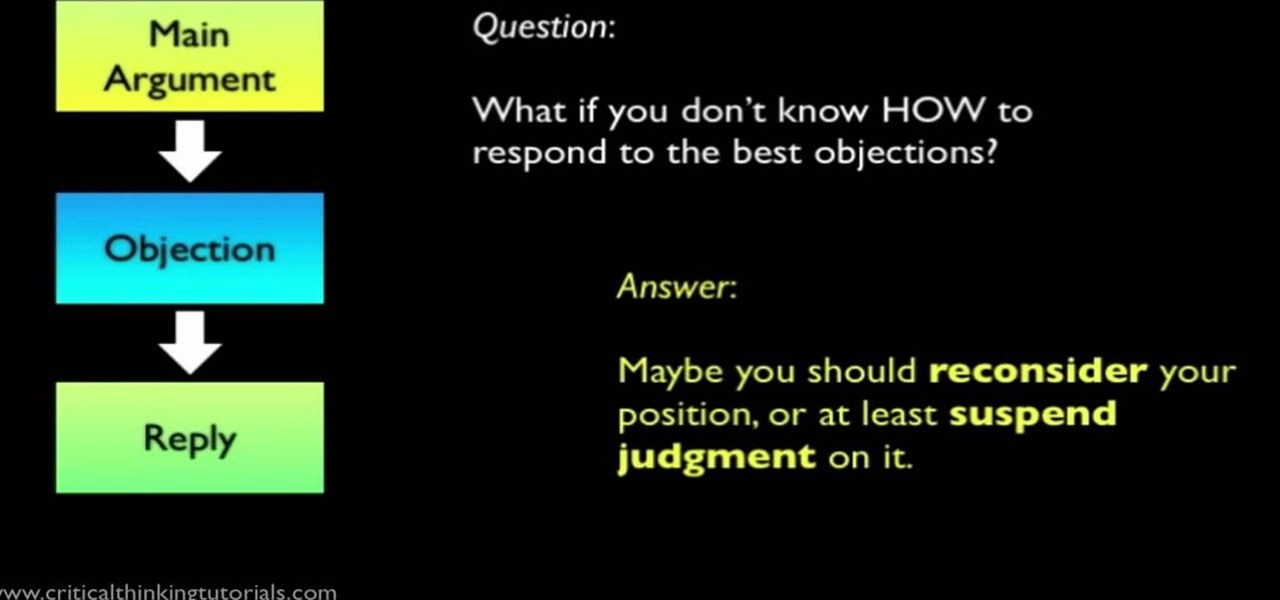
In this tutorial video, you will learn the basic structure for a good argumentative essay. The narrator in this tutorial, makes a very important distinction in the video; a good argument versus an average or mediocre argument. The narrator teaches you that a good argument will have, at minimum, a 5-part structure. The elements in the structure include an introduction, a body, and a conclusion. Within the body, a good argumentative essay would contain a main argument, an objection, and a reply...

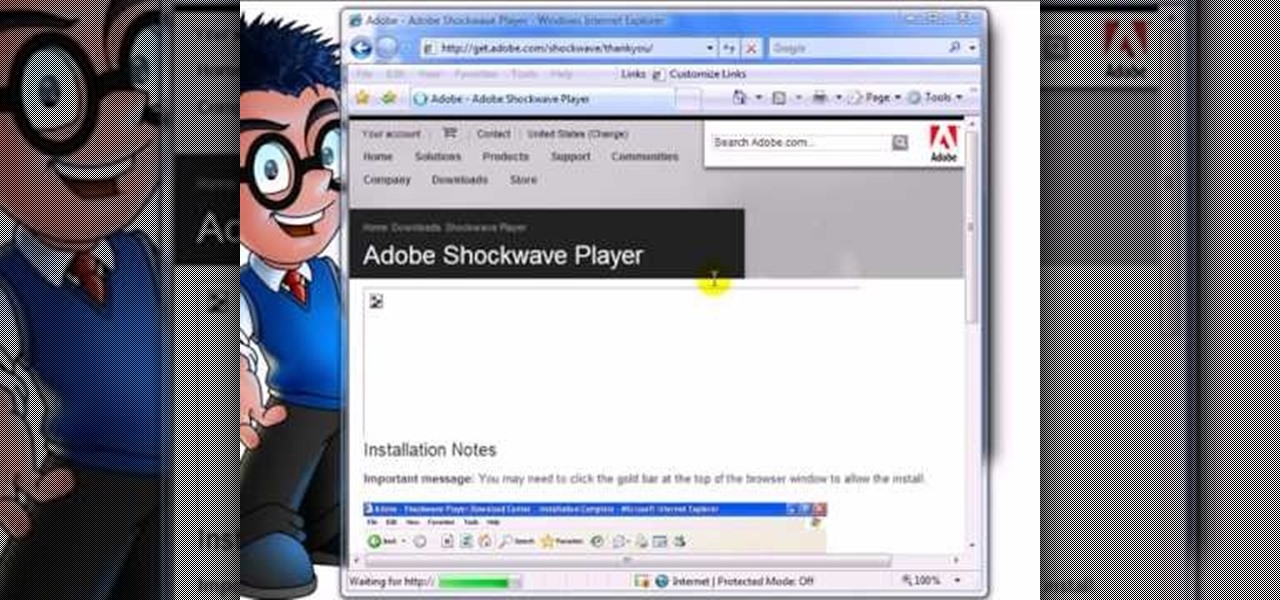
This video tutorial is about how to install Adobe Shockwave Player in Internet Explorer browser. This video tutorial is provided by ClearTechInfo.com. One can clarify any computer technology-related doubts using this site.

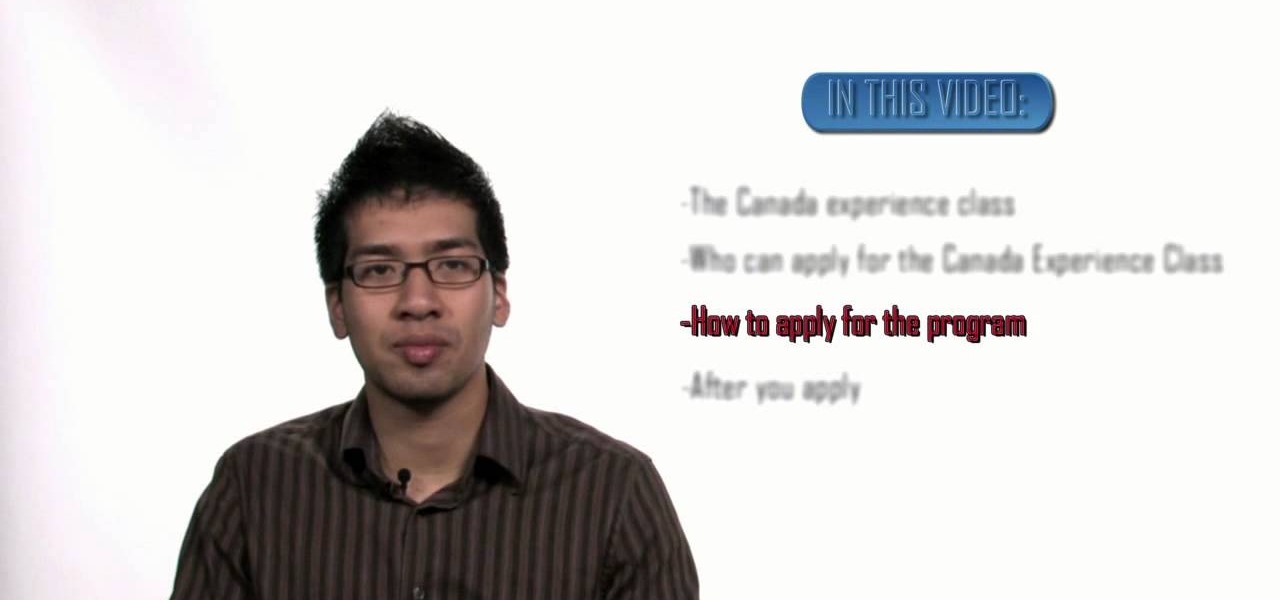
The CEC, Canada Experience Class, is a new program to help a person who has held residency in Canada gain permanent residency status. The program realizes that, by going to school or living in Canada while working, many people have the skills necessary to make the transition to live in Canada permanently. To qualify for CEC, you must be a temporary worker living in Canada for at least two years with two years of skilled working experience. A second way you can qualify is by being a foreign gr...

Speed up and stay rested by simply getting more stamina in this hack for Country Story. Using Cheat Engine, you can easily up your stamina!

With social networking systems, YouTube comments chains, chat rooms, bulletins boards, Twitter updates... It seems as if almost everyone has at one time publicly stated an opinion on the Internet. Nearly half of all prospective employers research job applicants online. Make sure that what you’re posting today doesn’t cost you a dream job tomorrow!

How to hack Pet Society! Pet Society cheats, tricks, hacks. Watch this video tutorial to learn how to hack gold in Pet Society (09/29/09).

Got a digital camera, but no idea how to share pictures with friends and family? Try the photo-sharing site Flickr.

If you're feeling unappreciated, underwhelmed, or just plain trapped, taking some time off may help.

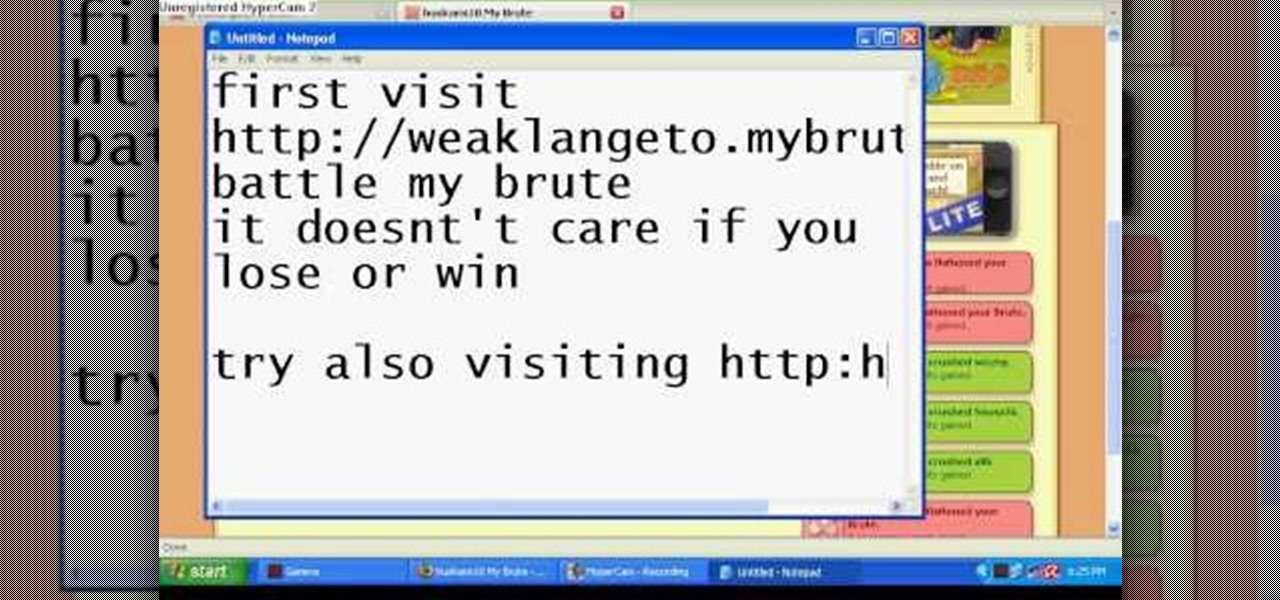
Hack mybrute with this mybrute cheat. MyBrute hacks, cheats, tricks. Watch this video tutorial to learn how to hack a wolf or bear in MyBrute (07/26/09). Without Cheat Engine!

Learn how to write a grant proposal. If your organization has come up with a great idea that needs money to get off the ground, you'll need a great proposal. Here's how to write one.

Thanks to the Freedom of Information and Privacy acts, we’re all entitled to see what the FBI has on us. Learn how to get your hands on your FBI file.

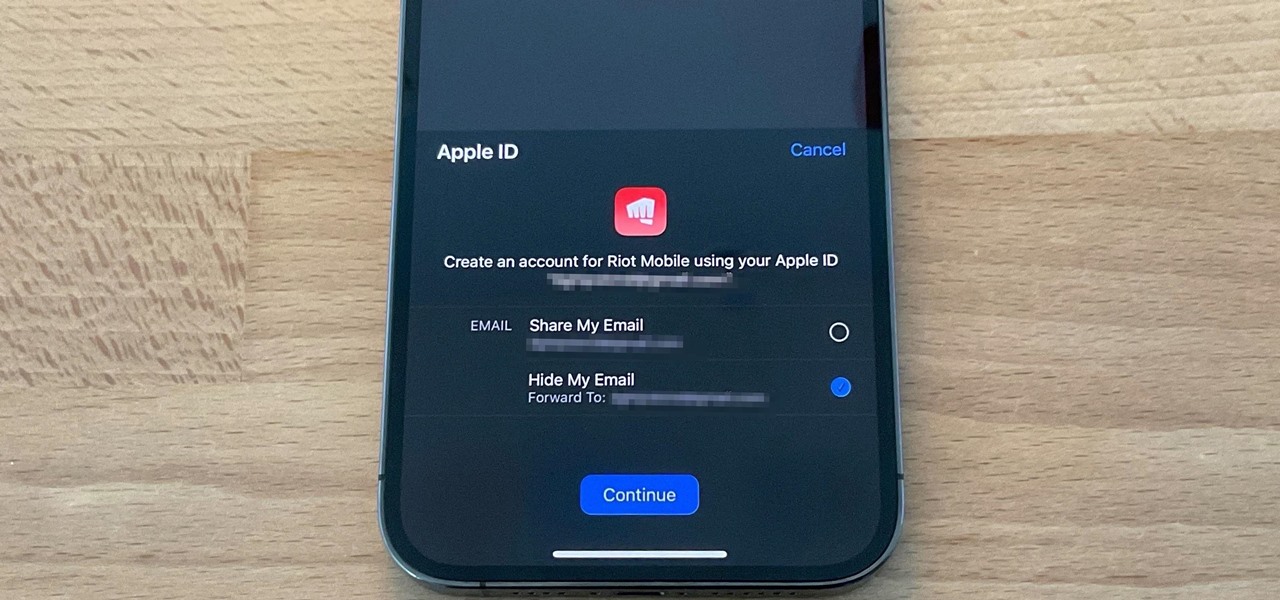
The "Sign in with Apple" service lets you create accounts with third-party apps and websites more easily using your Apple ID. More importantly, it can hide your personal email address using auto-generated disposable email addresses. However, it's easy to lose track of the accounts you use with Sign in with Apple, as well as any throwaway email addresses you used to hide your actual address.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

Virtual private networks, or VPNs, are popular for helping you stay anonymous online by changing your IP address, encrypting traffic, and hiding your location. However, common IoT devices, media players, and smart TVs are hard to connect to a VPN, but we have a solution: Turn a Raspberry Pi into a router running through PIA VPN, which will ensure every connected device gets the VPN treatment.

Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google.

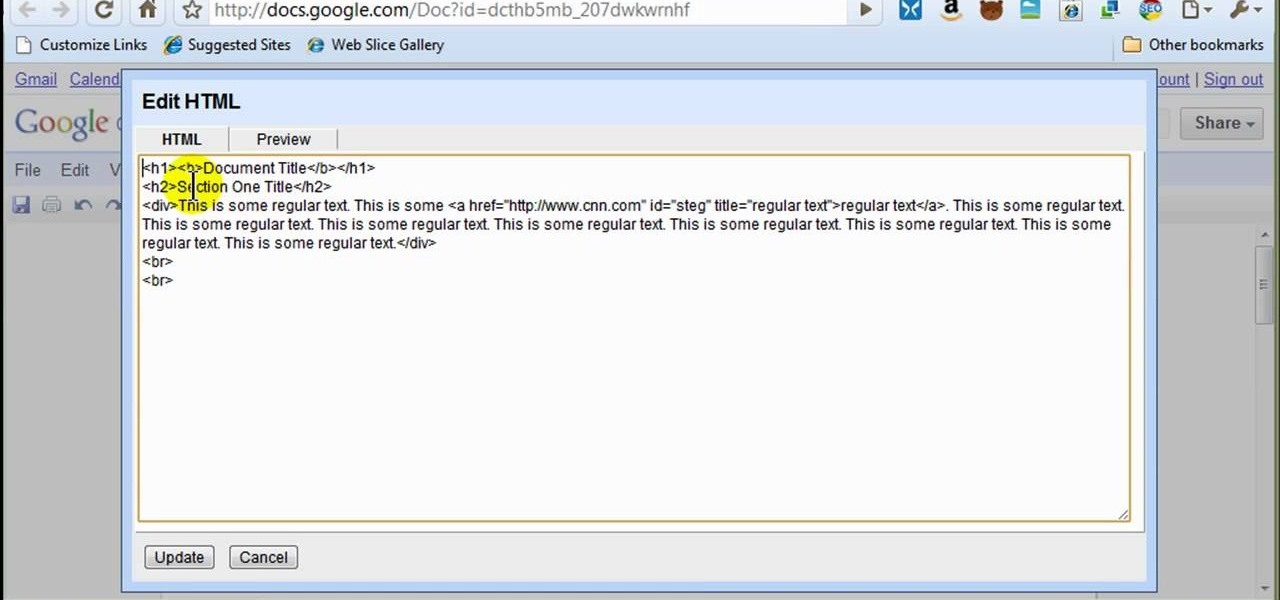
In this how to video, you will learn how to style documents with the Google Docs CSS editor. First, create a new document in Google Docs. First, click on the drop down menu for style. Type in a title in the document. Select heading 2 in the menu and type in the section title. Next, take off the style and type in the body for the content. Select some of the body text and click the hyperlink button. Type in the address and click okay. Now you can click this text to go to a website. Go to file a...

iPodTouchedMaster shows how one can easily SSH into their iPod Touch with all firmware! To SSH is the ability to hack into your iPod Touch's file system. First, your iPod Touch must be jailbroken. Next, you'll have to open Cydia. Click "Featured Packages" or search for the terms "Open SSH" (it will be listed under Console Utilities & Daemons). When you have OpenSSH click on it and click 'Install' and 'Confirm'. After this is finished, click return to 'Cydia'. This may take a lot of battery po...

Learn how to spot a dishonest contractor for home repair. It’s no accident contractors have such a bad reputation – they get more fraud complaints than any other workers! Here’s how to find a reputable one – and skip the scammers.

Hello everyone! How's subnetting going? Did you practice a lot? I hope you did, but even if you didn't we will go through some more examples so you can be feeling confident after reading this article. It's all about that bad boy binary!

Welcome back, my novice hackers! The worst thing that can happen to any hacker is being detected by a security admin, the security technologies (IDS, firewall, etc.), or a forensic investigator.

From booting into Fastboot mode with a single command to installing mods without root access, there's no shortage of reasons to use ADB. The catch, though, you had to be tied to a computer with a USB connection. However, a new feature in Android 11 finally allows you to run ADB commands over Wi-Fi instead of being tethered.

If you're a long-time Spark user, you'll know that one of the only drawbacks to the app used to be its lack of rich text-editing tools such as hyperlinking. If you needed to link out to a site in an email, your best bet was to grab a computer to get the job done. Well, close those laptops and shut down those PCs — Spark corrected this issue, implementing support for hyperlinking right into the app.

Backdooring a powered-off MacBook is easy when a few minutes of physical access is allowed. That attack works well if the hacker also shares a Wi-Fi network with the victim, but this time, I'll show how to remotely establish a connection to the backdoored MacBook as it moves between different Wi-Fi networks.

Most packages sent to you via delivery services include a tracking number that allows you to track it from the creation of the shipping label all the way to your doorstep. The U.S. Postal Service includes tracking information with many of its mailing services, but not for first-class mail or periodicals. Luckily, there's a workaround to that limitation that you can set up pretty quickly.

Hello, everyone. Stealth is a large part of any successful hack; if we don't get noticed, we're much less likely to be caught. In these next few articles, we'll be building a shell based on keeping us hidden from a firewall. There are many ways to stay hidden from a firewall, but we'll only be incorporating a couple into our shell. This article will outline and explain these evasion concepts and techniques.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

After a few unnecessary U-turns, I quickly realized that Apple Maps wasn't for me, which is why I hate that it opens as the default app any time I select a shared location or an address from Yelp. Copying and pasting the address to Google Maps isn't a huge deal, but it's certainly not as fluid of a process as I'd like.