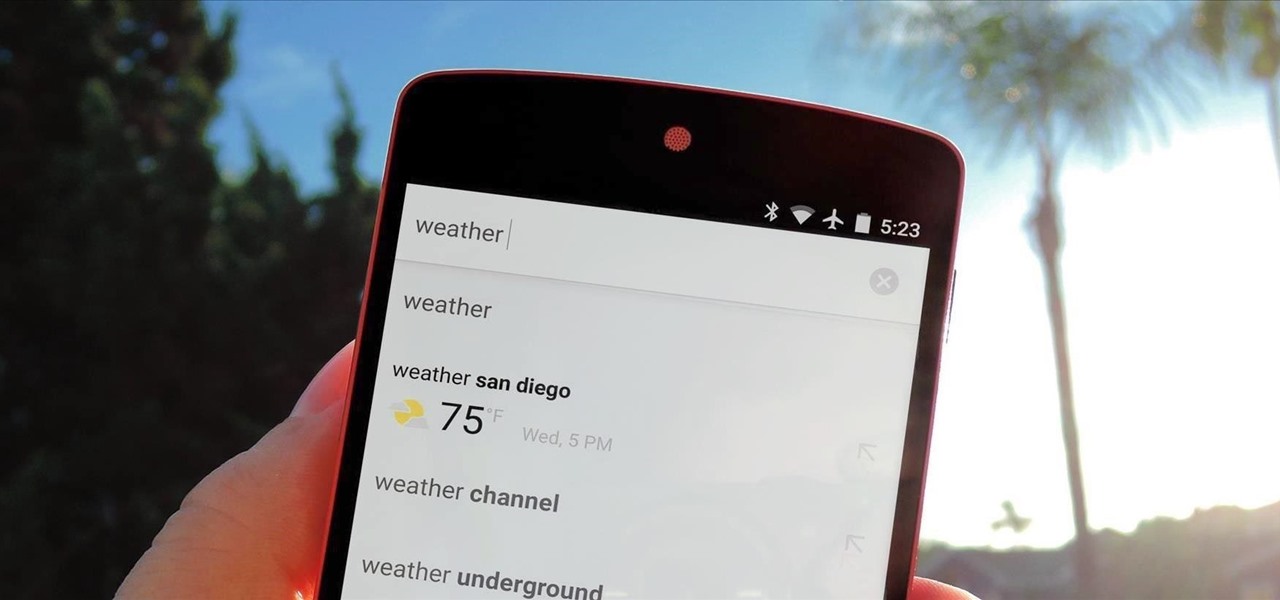
Besides its extensive collections of add-ons for Android, Firefox's mobile browser apps have many built-in features that you won't see in other mobile browsers. One feature in particular, available for both Android and iOS versions, makes it easy to switch back and forth between search engines for any query.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.

RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices.

A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer inside these routers has become so popular and easy that automated tools have been created to make the process a breeze.

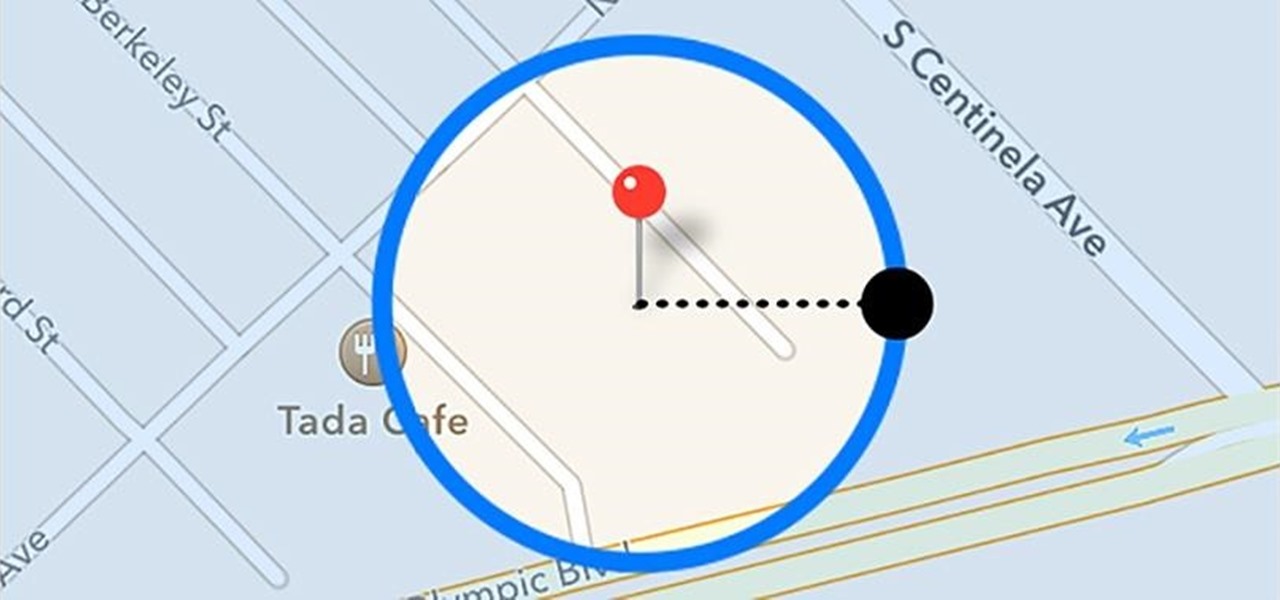
Instagram can be pretty exact when it comes to where you are located. That's why, sometimes, it's best never to geotag your precise location, but a broader area where you are less likely to get, well, um ... stalked?
Before many games make it to the US-based iOS App Store, they get "soft launched" in a smaller country to get real-world testing for bugs. It's a pilot program, so to speak, as countries like Vietnam or the Philippines have far fewer iPhone users than the US, thus offer a more controlled environment for developers to get feedback and zero-in on issues that may occur in a game's early development phases.

Welcome back, my rookie hackers! The Golden Fleece of hackers is to develop a zero-day exploit, an exploit that has not been seen by antivirus (AV) software or and intrusion detection system (IDS). A zero-day exploit is capable of skating right past these defenses as they do not contain a signature or another way of detecting them.

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the attacker portion of the shell. In this article, we'll just be testing it to see if everything works correctly.

In this how-to we will be sending an email with an image we get from a php script after running some fishy code. What you'll need

Hello fellow Nullbytiens, today we will be talking about IRC again (if you haven't read OTW's post about head over there now)and more specifically about using 1 nickname with multiple devices or IRC clients.

When I tried to set up an eviltwin for a MitM-constelation in kali 2.0, I couldn't provide internet to the victim. The origin was the brctl bridging. I have read many tutorials but all of them where explained in backtrack and older versions of kali. So i was searching for a solution without using brctl and this solution will be explained now. This will just work on unencrypted wireless-environments.

Unless you've been living under a rock or ignoring recent news headlines, Ashley Madison, the dating site for married people (or individuals in a committed relationship) has recently been hacked. Millions of their users are shitting their pants, and for good reason, as all of those accounts have just been leaked.

In recent weeks, major bank websites around the world have experienced outages after being have been hit with Distributed Denial of Service (DDoS) attacks. Although few, if any, of these banks have been totally knocked offline, these DoS attacks have dramatically slowed the response time of their websites to legitimate customers. The most recent victim was the Royal Bank of Scotland. Due to this attack, RBS customers were unable to access their accounts for about an hour last week.

Why did I write this when they're tons of scanning tools available.

An app with overabundant features can make it more customizable, but too many options can also be overwhelming, even on a mobile web browser. If you're tired of Safari or Chrome on your iPhone, try out Frameless from developer Jay Stakelon, a simpler web experience using just the essentials.

Google continues to be the most commonly-used search engine for a reason. While continuing to stay ahead of the pack with advanced semantic search functions, Google even introduced Knowledge Graph results that offer key information without ever having to click a search result.

Airports are terrible germ-infested purgatories where people sit around for hours without Wi-Fi while they anxiously await to get wherever they really want to go. Unfortunately, there isn't much we can do about waiting, but this little Wi-Fi hack could help make the waiting a little less boring.

I'll be the first to admit how horrible my memory is, whether it's remembering to take out the garbage or paying a bill on time. That's why I regularly utilize the stock Reminders app on my iPhone; it's definitely compensated for my memory deficiencies.

I still remember when I had to get up from my comfy spot on the couch to change the channel on my old television. So for me, the remote control may be one of the most underrated inventions of the last century. These days, remotes take on all sorts of shapes, not just the typical brick, but also in the form of watches and cell phones.

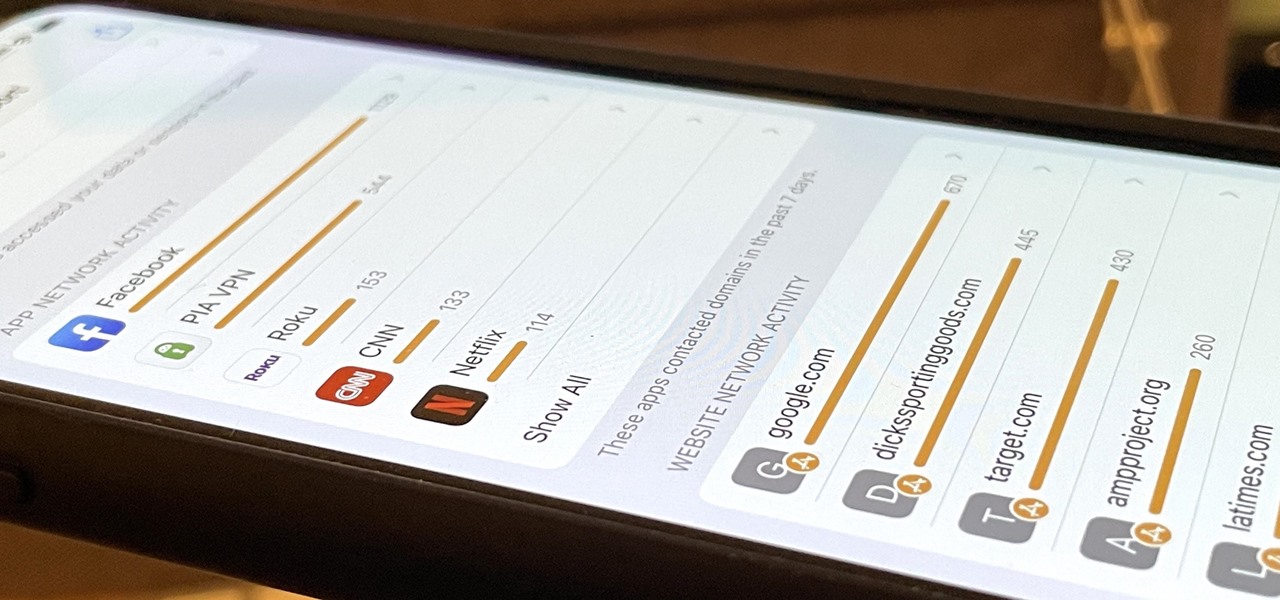
Apps that have no business accessing the internet can share your location, device ID, and other personal information with potentially malicious data snatchers. If you're connected to the internet on your Nexus 7 tablet, you're a potential target for cyber threats.

I can be pretty forgetful. If there's something important to remember, I need to jot it down right away or risk losing it forever.

Welcome back, my greenhorn hackers! In a previous tutorial on hacking databases, I showed you how to find online databases and then how to enumerate the databases, tables, and columns. In this guide, we'll now exfiltrate, extract, remove—whatever term you prefer—the data from an online database.

Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensics. In other words, what can a network forensic investigator learn about the attacker during an investigation and how.

Ever since the FBI took down the Silk Road and Dread Pirate Roberts last month, many questions have been raised about whether Tor still provides anonymity or not, and if it's now broken. I'll try to address that question here today succinctly from multiple angles, keeping it as simple and plain-language as possible. The Closing of Silk Road

Welcome back, my rookie hackers! When Wi-Fi was first developed and popularized in the late '90s, security was not a major concern. Unlike wired connections, anyone could simply connect to a Wi-Fi access point (AP) and steal bandwidth, or worse—sniff the traffic.

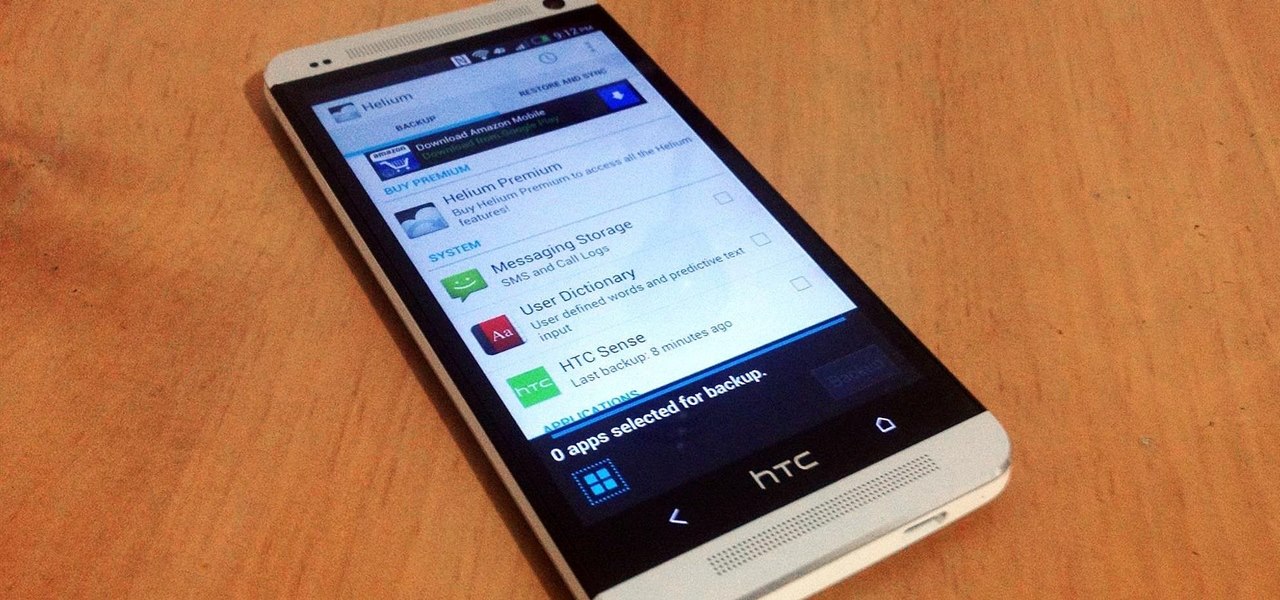
When you upgrade to a new Android smartphone like the HTC One, you can have browser bookmarks, Wi-Fi passwords, and other settings quickly transferred over from your old device using your Google Account backup. However, you'll still have to download apps individually from your Google Play list, and not all of your saved progress will be transferred over. Fortunately, there is a third-party app that will allow you to backup and restore your apps—with all their data.

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.

Wish your home wireless network was faster? You can always buy a signal booster, but if you'd rather not spend the money, here are a few tips and tricks to speed up your wireless connection, including how to make a homemade signal booster with things you probably already have lying around.

If you have just purchased a new Ford Taurus, you may have noticed the new SYNC feature. SYNC is a GPS built right into your dashboard. If this is your first time using a global positioning system, you may need a few pointers. Check out this video and learn how to access step by step directions and get where you need to go.

In this economy being competitive for a job means your application must stand out above the rest. Here's how to write a cover letter to successfully introduce your resume. Make sure your cover letter follows business letter format. Your name and address must be written at the top left corner. The employer's name and address are written just below. The letter should be addressed to a specific person within the company. Paragraphs in a business letter are not indented, but instead are left just...

This how-to video is about how to use command prompt to view the blocked websites at school. This step by step instruction will help one to open the blocked websites at school.

There're plenty of great ways to get traffic, especially this off-site optimization technique using classified ads to point website traffic back into your site itself.

With the holidays right around the corner, it's easy to miss a big software update on your iPhone, and by that, I mean iOS 15.2, which was pushed out Monday, Dec. 13. There's a surprising amount of new features and changes in the updated firmware, and there are a few big ones you need to know about.

Metadata might be a bigger concern than you might realize. In its continuous push to be a privacy-first company, Apple has released several new features with iOS 15 that allow you to adjust and permanently change the metadata stored within the photos and videos you take on your iPhone. But why would you want to do this?

The Digispark is a low-cost USB development board that's programmable in Arduino and capable of posing as a keyboard, allowing it to deliver a number of payloads. For only a few dollars, we can use the Digispark to deliver a payload to a macOS computer that will track the Mac every 60 seconds, even bypassing security like a VPN.

An attacker can repurpose public MyBB forums to act as command-and-control servers. It only takes a few lines of code to configure a MacBook to fetch commands and send responses to any website the attacker desires.

The newest version of macOS has arrived. While everyone's mind is being blown by Mojave's groundbreaking new Dark Mode, we'll be taking advantage of its insecure file permissions to establish a persistent backdoor with a self-destructing payload that leaves little evidence for forensics.

When you can't reach your iPhone or don't have it on you, how do you get help from emergency services? Unless you have one of those life-alert mobile triggers, someone nearby, or some amazing telepathy skills, hope might be the only answer — unless you wear an Apple Watch, that is.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.