EternalBlue was a devastating exploit that targeted Microsoft's implementation of the SMB protocol. Metasploit contains a useful module that will automatically exploit a target, as long as it's vulnerable. But what if we wanted to exploit this vulnerability without Metasploit holding our hand? It can be done using a Python file to exploit EternalBlue manually.

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

Welcome back, everybody. In the previous article, we covered the ideas and concepts of well-known ports and trust exploitation in order to evade a firewall. Today, we'll be building the shell, the part that receives commands, executes them, and sends the output back to the attacker.

UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - https://techkernel.org/2015/12/19/embed-metasploit-payload-in-apk-manually/

We are most certainly not machines. We all need some downtime every once in a while to set our sanity scales back in balance, which in turn, makes us more productive workers. This is a premise that several forward-thinking employers fully understand, but these types of companies are few and far between in corporate America.
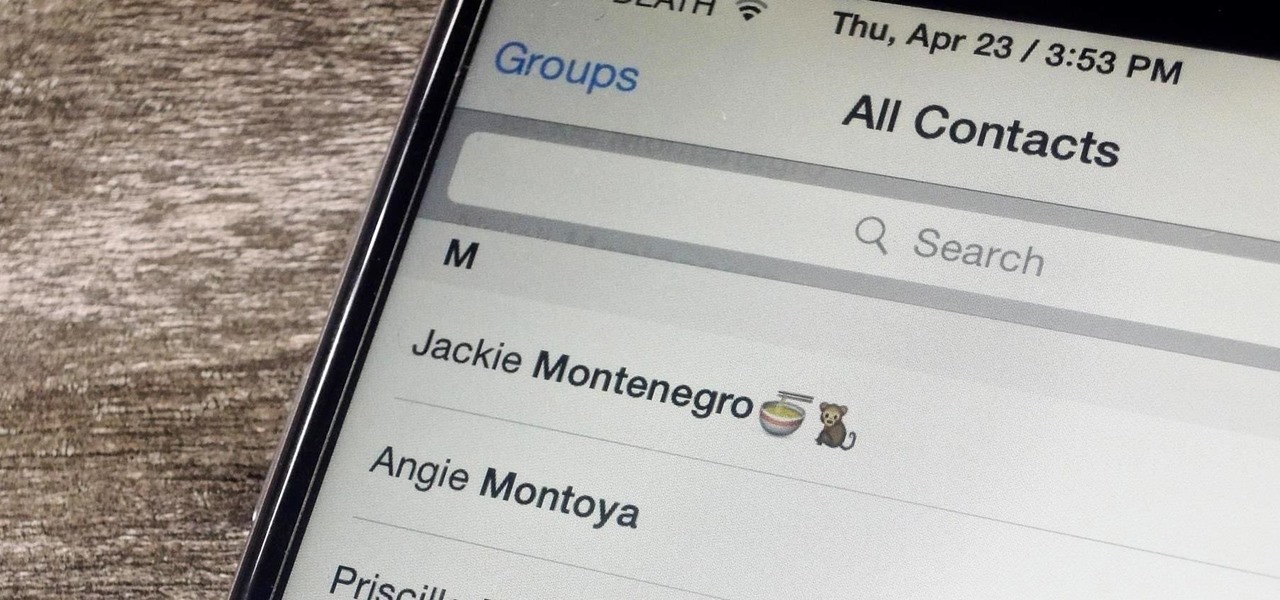
Organizing contacts is a bitch, especially on the iPhone. Some contacts will have multiple entries, you can only delete contacts one by one, and certain types of contacts can't be deleted at all. If that isn't enough to make you pull your hair out, then I don't know what will.

On the latest iOS software, your iPhone comes with significant privacy and security enhancements to protect your data even more than Apple did before. From safeguarding your iPhone to passcode-protecting files to making it easier to browse the web safely, there's a lot you need to know and start using.

The ability for apps and devices to determine the precise location of physical and virtual objects in space is a key component of augmented reality experiences, and the latest advancements in Bluetooth technology may have a hand in facilitating such location services in the near future.

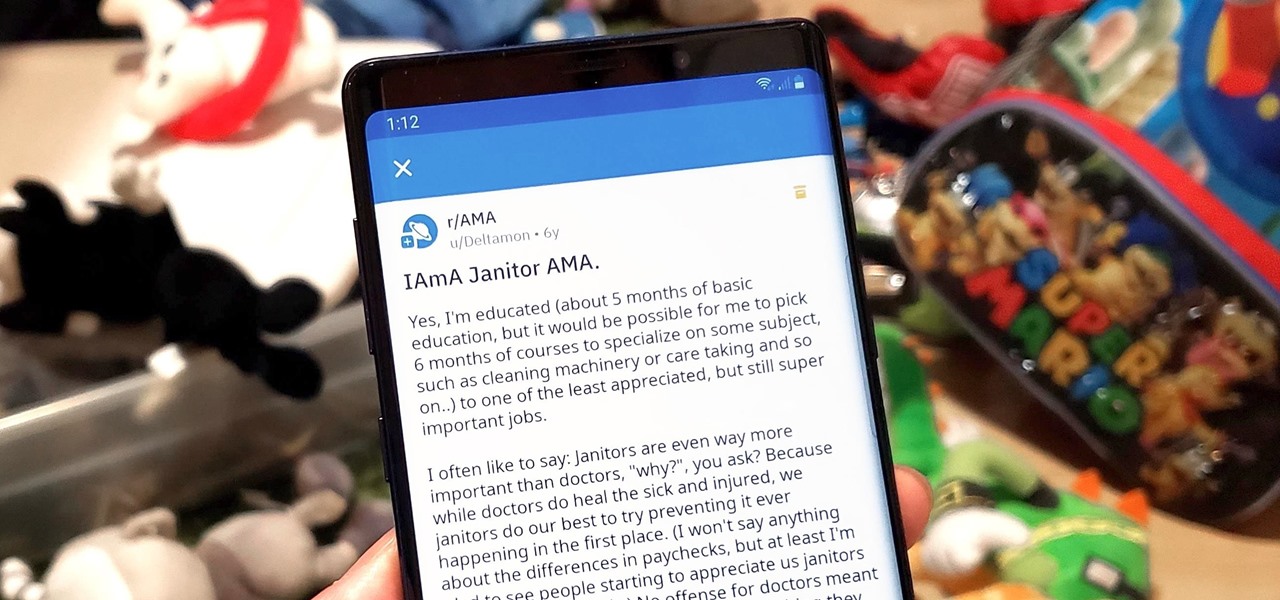
Short for Ask Me Anything, AMA threads are one of Reddit's signature features. They enable you to directly interact with a whole range of interesting personalities, from common folk with amazing life experiences to influential celebrities that help shape politics and culture.

Attention all Redditors: Between June 14 and June 18, Reddit experienced a data breach. The popular website claims it discovered the breach on June 19 and has since made the necessary moves to contain and eliminate the threat. Unfortunately, there isn't much they can do about the data was that accessed and stolen — your user data.

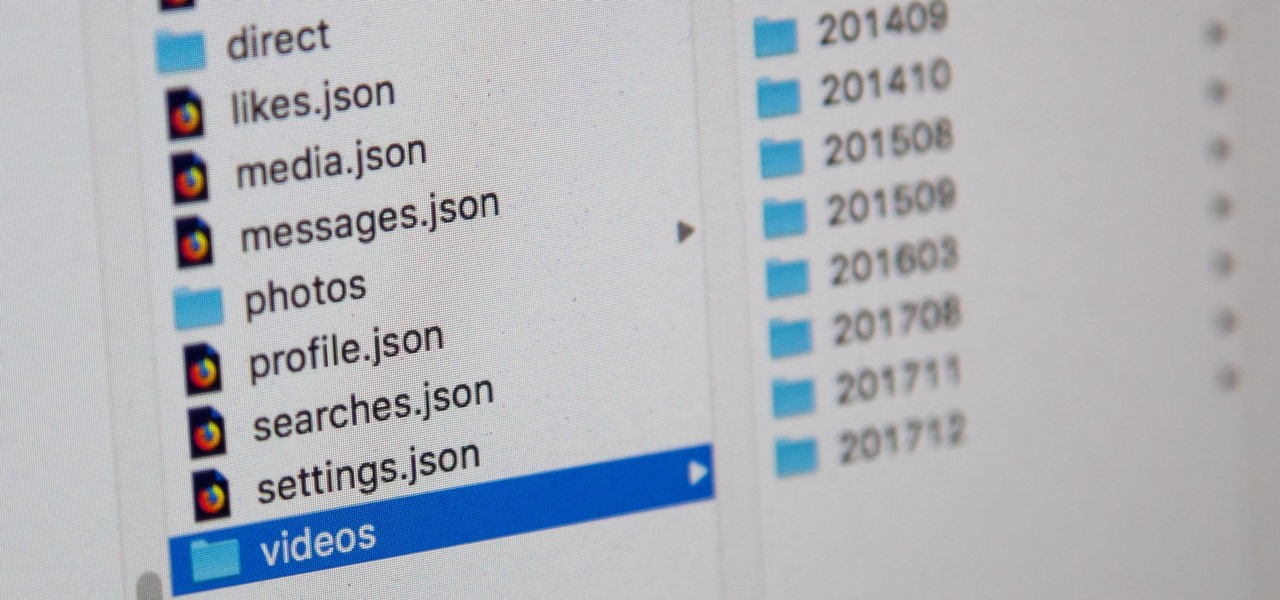
Facebook, parent company of Instagram, has allowed you to download photos and other account data for some time now, but the data request feature is also now available on Instagram to meet the GDPR data portability requirement in the EU — and it's available worldwide, not just in Europe.

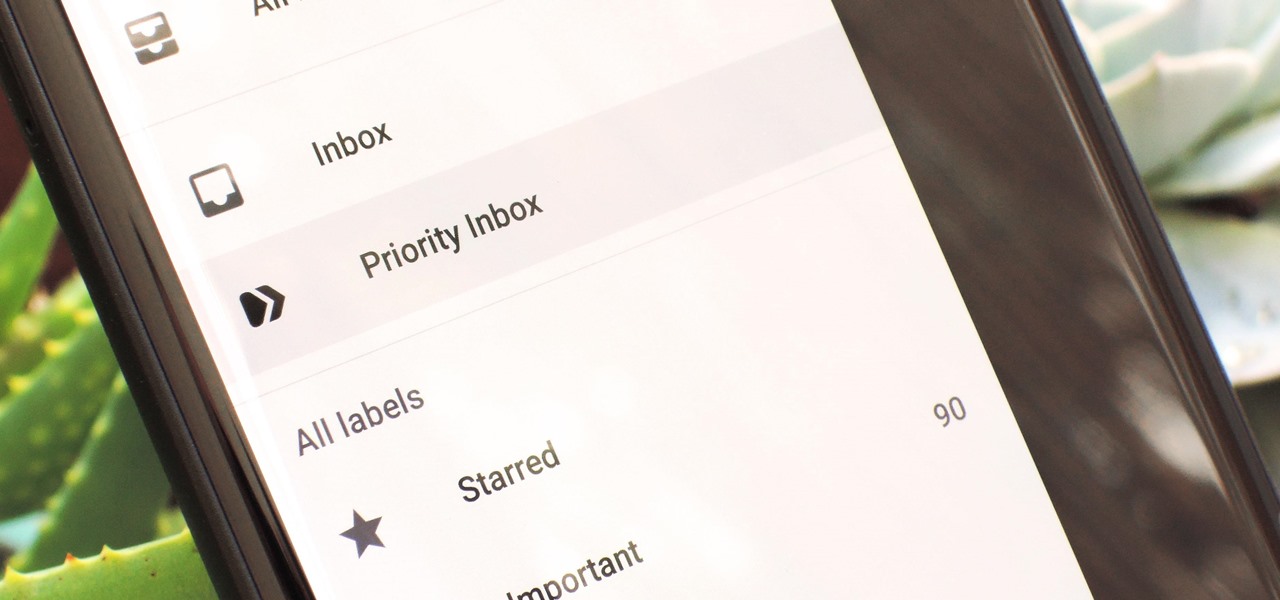
For many of us, getting to inbox zero is the highlight of our day. But if you used your email address to sign up for various sites and services, your inbox is probably cluttered with all sorts of spam, news letters, and unimportant emails. Thankfully, Gmail has a feature that can solve this by using machine learning.

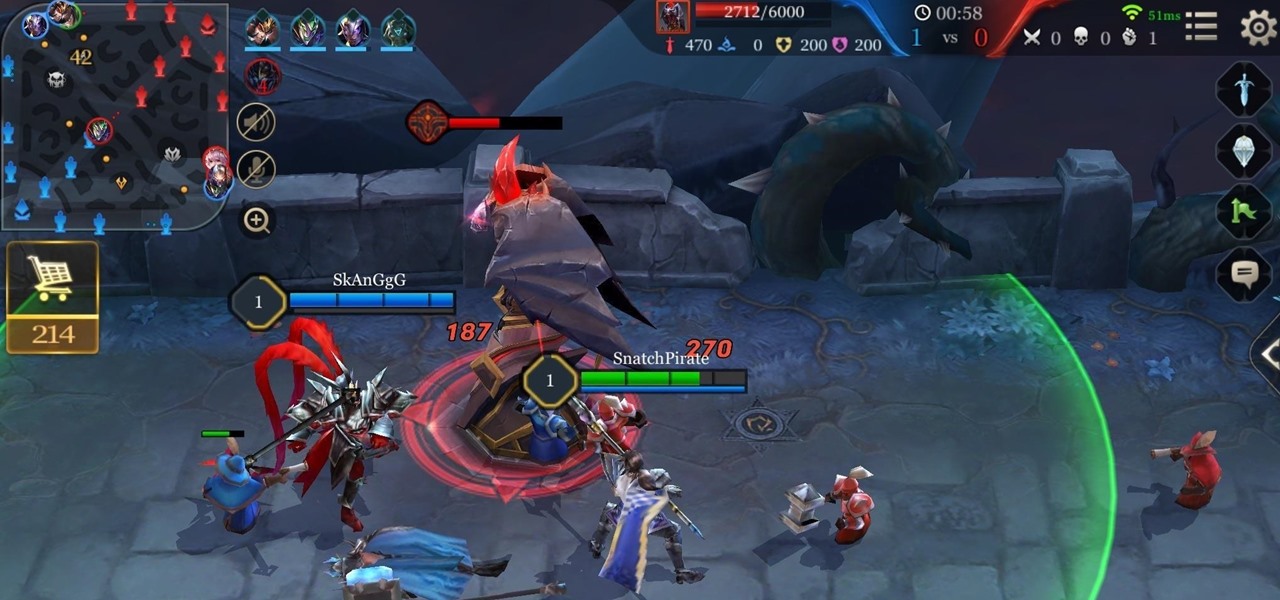
You may have heard of Honor of Kings, the multiplayer online battle arena game so popular that it has the potential to do for mobile what League of Legends has done for the PC in the world of competitive online gaming, but you'll soon hear about its western iteration, Strike of Kings. Tencent, the China-based online gaming giant now looks to expand to the lucrative western market and has released the game to many parts of Europe as a soft launch for iOS devices. Gameplay in Strike of Kings is...

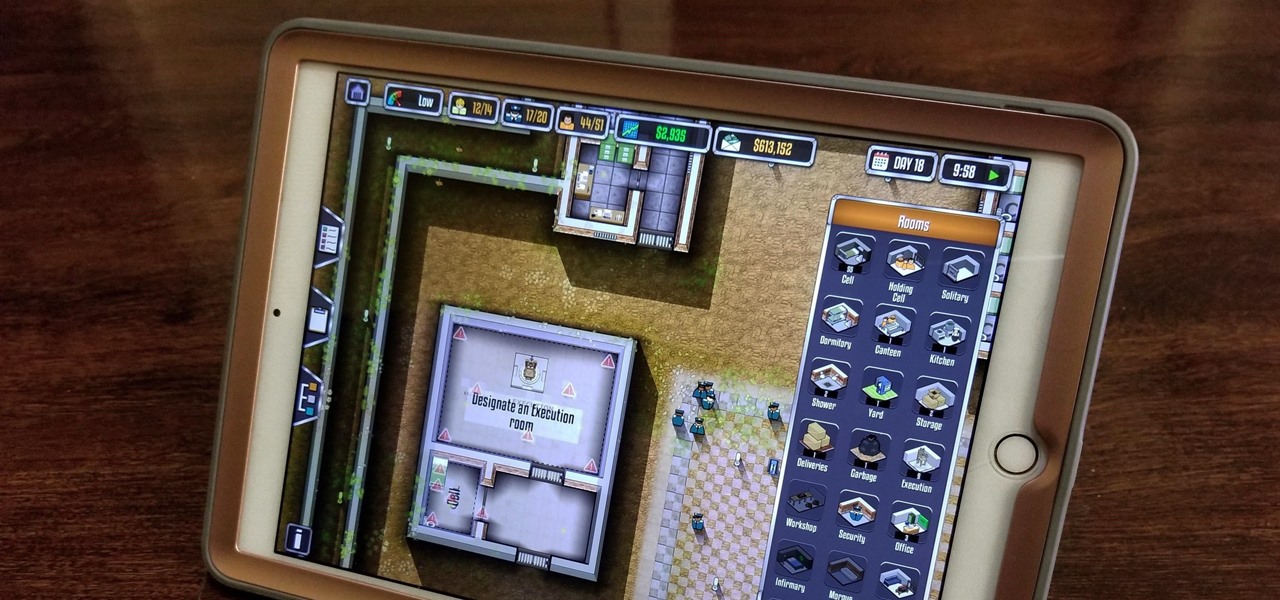
Prison Architect, the BAFTA winner for the Best Persistent Game in 2016, has finally soft launched on iOS. Originally a PC game, Prison Architect lets you build and maintain a maximum security prison. Comparable to running a small city, the game has you manage an ever-expanding correctional facility and contend not only with violent offenders and ever-present prospect of a chaotic riot, but also more mundane affairs like balancing the prison's budget and employee payroll. In addition to the s...

Final Fantasy XV, the latest release in the long-running Final Fantasy franchise, has been a massive success, shipping around 6 million copies worldwide in less than two months. Final Fantasy XV: A New Empire is a mobile game based off this popular console iteration, and has surfaced in New Zealand for download.

Fans of rhythm tap games and traditional one-on-one fighters finally have something to bring them closer together. DuelBeats, a fighting game that lets you perform moves by tapping to the beat of a song, has been released as a soft launch for both iOS and Android in New Zealand, Australia, and Singapore. Just because the game is exclusive to those regions doesn't mean we can't try it out for ourselves, and with a little hackery, it's entirely possible to do so.

Fans of fighting game series such as Street Fighter and Mortal Kombat are in for a treat! Skullgirls has entered the crowded field of the mobile fighting genre and has touched down in the form of a soft launch for iOS devices, which is now available for download in Canada and the Philippines. But don't let this limited release stop you from trying Skullgirls out, as it's still possible to acquire this little gem with a little finagling.

Jam City's Panda Pop was a great success that helped millions of users waste vast amounts of precious time with its bubble-popping panda cuddliness. Not wanting to mess with success, Jam City has now simply re-skinned the game to feature all the beloved characters from Charles Schultz's timeless Peanuts universe, complete with its relaxing soundtrack and a new name—Snoopy Pop.

If you have a long commute, it only makes sense to catch a bit of shuteye while you're headed to work on the train or bus. The only problem with this is that, if you're napping a little too hard, you might end up oversleeping and missing your stop when the subway pulls into your station.

If you need to do some hardcore multitasking on your Windows PC, a second monitor can go a long way towards getting things done. If you opt to "extend" your Windows desktop across a dual monitor setup, it's as if you have two computers side by side, with each display getting its own set of windows and programs that can be open simultaneously.

When you're driving, the last thing you need to be doing is messing around with your phone. But these days, people expect you to be available at all times, so the text messages continue to flow in while you're on the road. It's a terrible distraction, and one that is responsible for 25% of all car wrecks in the United States.

When it comes to sharing files between a smartphone and a computer, there are several solutions available for a Windows and Android pairing. But for those of us with Apple devices, the selection of apps in this category isn't quite as great. You can use AirDrop to quickly share files, but searching for files is not so easy.

I have came across a lot of members on the forum that didn't have a clear idea of what port forwarding is and what it does. So...Let's get started...

A VPN service is almost an essential these days. Good ones can block ads, prevent tracking cookies, encrypt your internet traffic for better security, and even spoof your device's location to bypass geo-restrictions — all things you should be concerned about in the age of NSA snooping and Facebook data mining.

This tutorial follows the same idea as my original tutorial for windows, but I've redone it to work with Mac OS X. Here's how to get a meterpreter session from your victim opening a malicious word document:

Hey everyone, this guide will show the process of stealing your victims Facebook credentials. This is a followup to my previous post.

In my last post I introduced how to use ncat to connect to your Pi remotely, but what's the point to if you can't actually hack? This tutorial I'm gonna show you how to use very simple tools for a much bigger purpose. With that said, boot up our Pi and lets wreck havoc.

If you want to keep your online world secure, your best bet is to have a different password for every site and service that you use, and to make sure each of the passwords are comprised of random characters instead of familiar words or numbers. But this obviously creates a problem—how exactly are we supposed to remember all of these complicated passwords?

So you want to create a meterpreter virus, but you keep getting caught by AV. How do you create one that will go undetected? In this tutorial, I'll teach you how to code your own simple virus that will download a powershell payload from an apache webserver and execute it - bypassing antivirus.

Roughly four years ago, Adobe decided to abandon development of the mobile version of their popular Flash Player browser plugin. Their excuse at the time was that this move would enable them to focus more on HTML5 development for mobile devices and allow them to put more effort into maintaining the fluidity and security of their desktop Flash plugin.

Keeping your online data and identity private is an uphill battle, but with the anonymity network Tor, you have a pretty decent line of defense from prying eyes.

If you read my last tutorial on using SEToolkit, you probably know that SEToolkit is an effective way to make malicious actions look legitimate. But, that was only the beginning... the truth is, Metasploit and SEToolkit belong together, and help each other very well.

Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity!

Hi, my name is Alan, and I am not a script kiddy brat from Xbox Live asking you how to boot someone offline for being mean to me. I am an amateur white hat hacker hoping to learn and teach and this is my first tutorial.

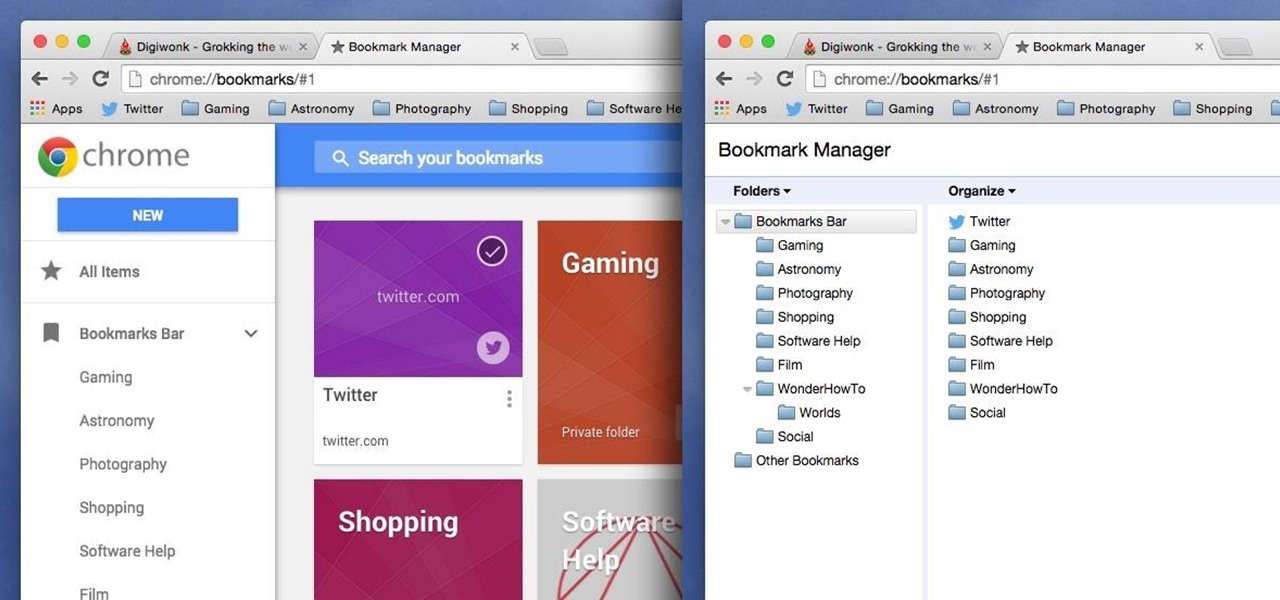
Chrome has been pushing out a lot of new changes lately, but not all of them are as good as they think they are. Earlier this year, there was an update that changed how user profiles worked, which made it harder to actually switch profiles. Luckily, there was a way to get back the old profile management interface, but now there's another "improvement" that you might want to change—Chrome's new Bookmarks Manager interface.

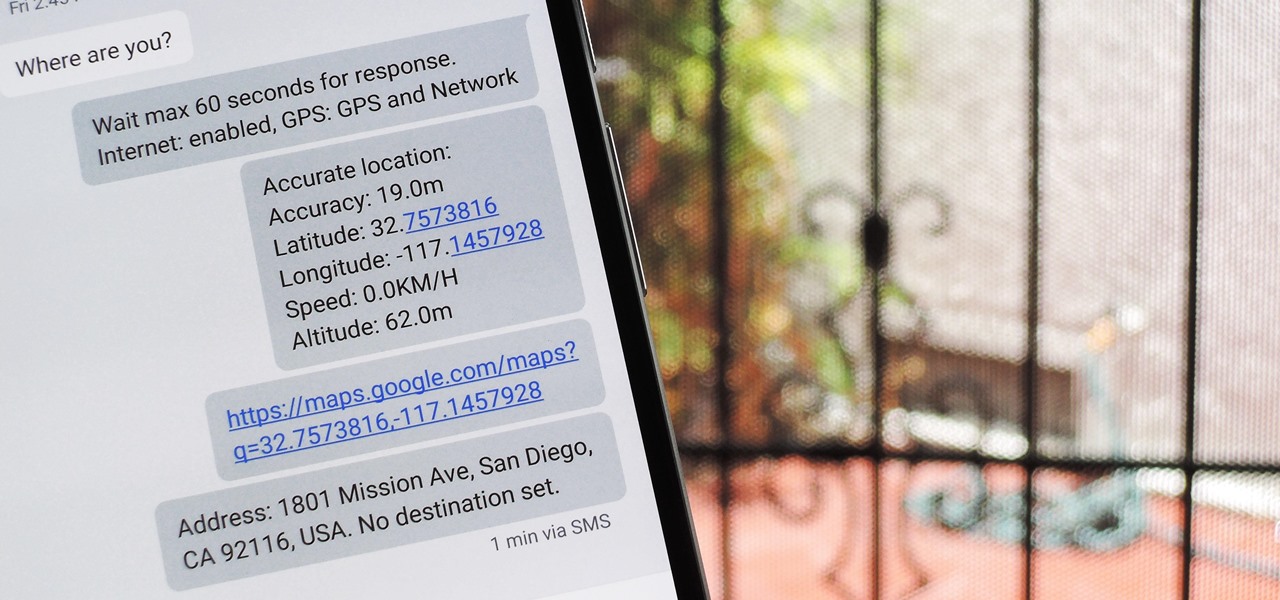
Smartphone users often wish for a privacy, where no one is able to poke his/her nose in their personal stuff. Unfortunately, none of the smartphones have been able to guard their privacy in this fashion. Smartphones usually come up with none or almost negligible built-in security to serve your purpose.

One of the many unique features that sets Android apart from other mobile operating systems is its live wallpaper system. Instead of the same old boring static image, this system lets developers create apps that provide dynamic home screen wallpapers.

Contacts on your phone can be messy. Keeping all of those numbers, emails, and addresses organized takes time and, even then, they still may not be be as accessible as you want them to be.

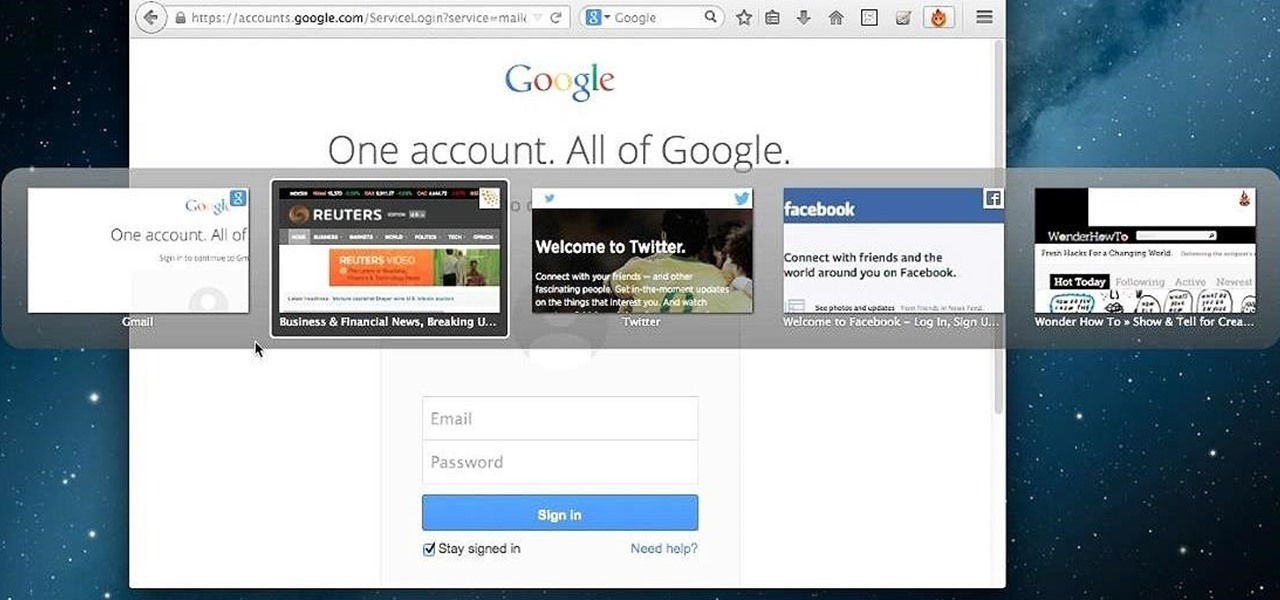
Tab previews—you can do it on an iPhone or an Android device, so why not on your Mac or PC? It's about time you take your browsing game to the next level and learn how to toggle between previews of your tabbed webpages.

One thing I absolutely cannot stand is lag when I'm gaming. Every time I'm about to beat my killstreak record on Call of Duty, my internet connection drops and I'm a goner. It never fails. This usually happens because someone else on my Wi-Fi is streaming a movie or downloading a huge file.