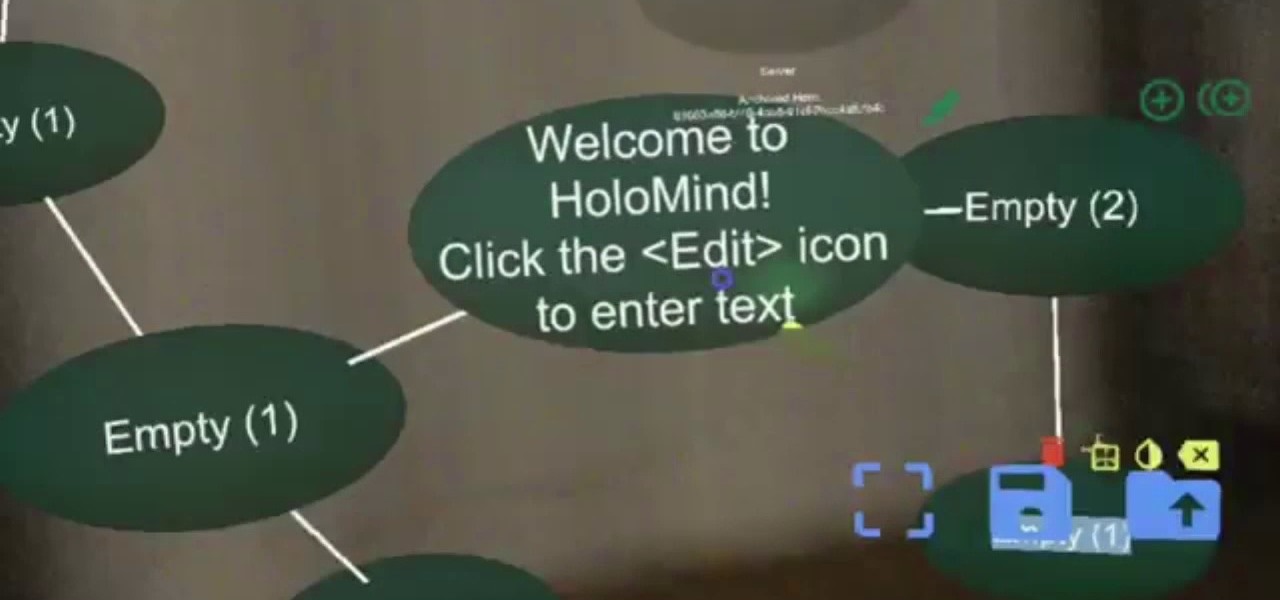
In the world we live in now — a world of complete data overload — new ways to sort through that data moves well past "nice-to-have" and firmly into the needs category. Mind mapping has been one tool that allowed someone to break down large problems into like components and help visualize the problems in different ways. Now thanks to Data Experts gmbh's Windows Store release Holo-Mind, we can do that in 3D on the HoloLens.

Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.

Besside-ng is the hidden gem of the Aircrack-ng suite of Wi-Fi hacking tools. When run with a wireless network adapter capable of packet injection, Besside-ng can harvest WPA handshakes from any network with an active user — and crack WEP passwords outright. Unlike many tools, it requires no special dependencies and can be run via SSH, making it easy to deploy remotely.

Screen mirroring app iDisplay has arrived for Vuzix M300 Smart Glasses. With the app installed on the M300 and the companion software running on a Mac or Windows computer, users can mirror or extend the computer's desktop to the headset's display, which is connected to the computer via Wi-Fi or USB cable. The app does not yet appear on Vuzix's app store.
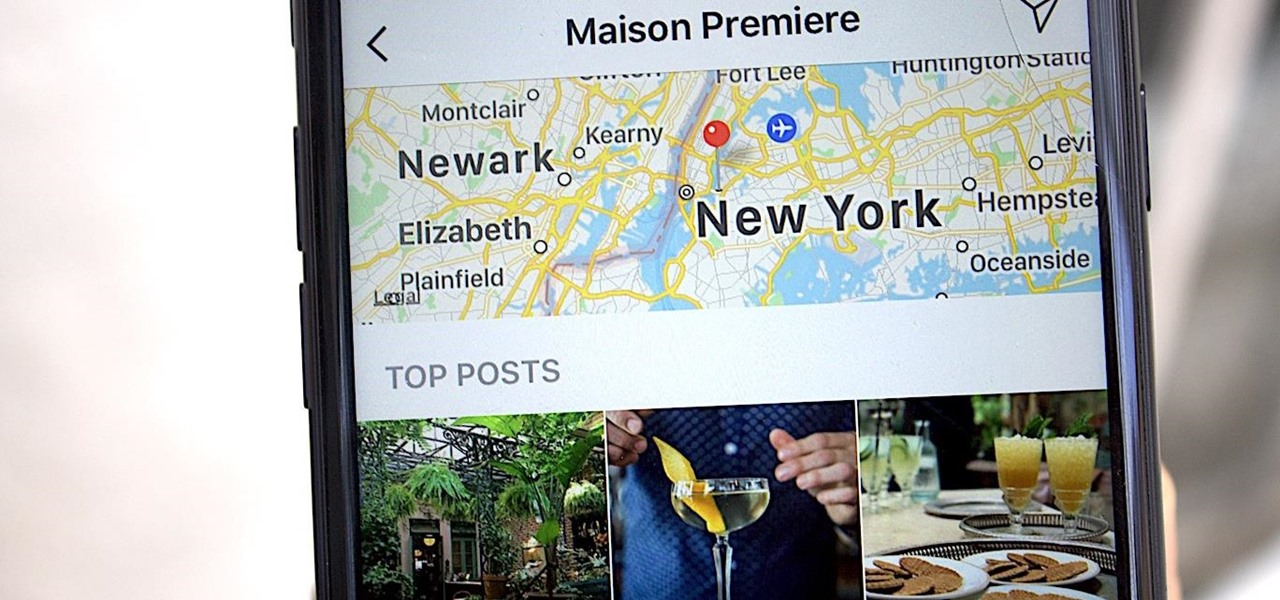
Geotagging your location on Instagram is one of the most undervalued ways to generate traffic to your profile. The beauty about adding your location to your IG posts is that it allows you to be seen by other users than the ones that already follow you.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

Theorem Solutions, a company that helps engineering and manufacturing companies reduce their costs, has taken the next step with their mixed reality technology. The company has now added their own app, called Visualization Experience, to the Windows Store for the Microsoft HoloLens

The new Google Assistant is only officially available on three platforms—newer Android phones (Pixels and those running Marshmallow and Nougat), the Google Allo app, and Google Home. However, most of the Assistant's basic functionality is also bundled into the Google app for Android and iOS, which used to go by the name Google Now, but is now referred to only as Screen Search or your Google app's Feed.

We've seen plenty of good, bad, and weird things that have come out of the worldwide augmented reality game Pokémon GO, including murder and location-based bans, but nothing on a large scale. That was, of course, until Iran decided to ban the game country-wide.

What happens if you unknowingly connect a malicious USB drive and it starts infecting your entire office network? Instead of having a panic attack and working all night to find a fix, you can just put on a mixed reality headset like Microsoft's HoloLens and point.

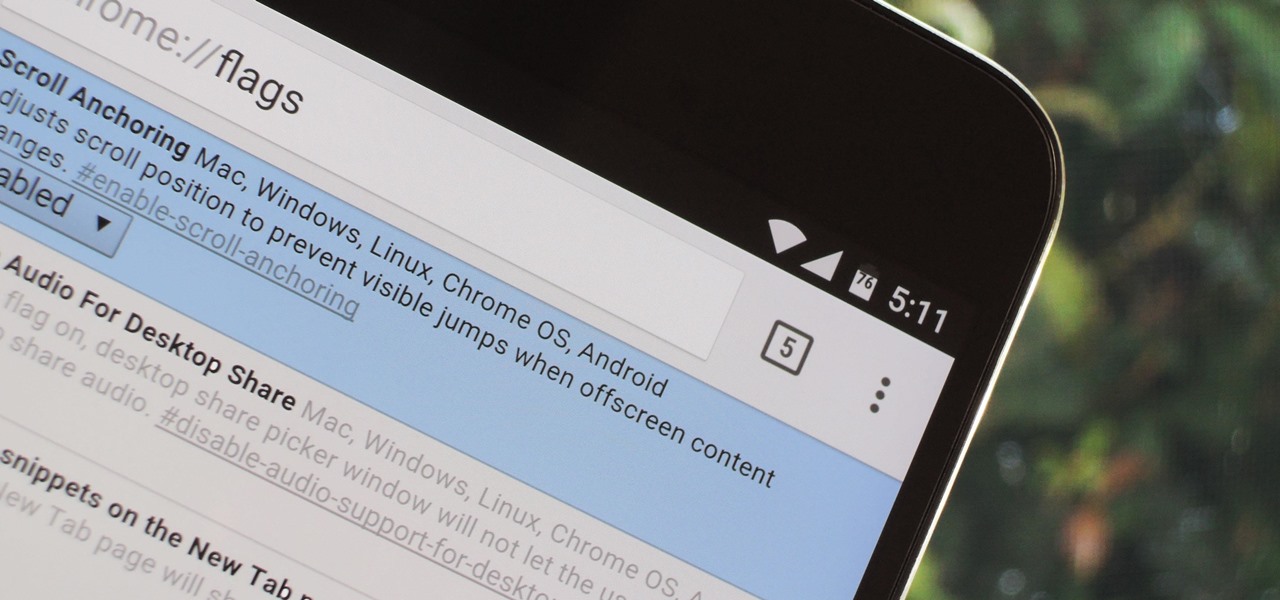
Google's Chrome browser comes pre-loaded on the vast majority of today's Android devices, and it's one of the fastest, most stable, and useful browsers out there. But it does have one major annoyance—while a page is loading, you'll see a link, then reach to tap it, but an element further up the page will load, and the link will jump out from underneath your fingertip.

It looks like Apple is finally going to do something to address all of the complaints about their unremovable stock apps clogging up people's home screens. While bloatware is a bigger problem on Android where you have to deal with apps from Google and carriers, an iPhone can still get pretty cluttered with all those stock Apple apps. I mean, just look at all this crap... AppAdvice noticed two new keys in the iTunes metadata that strongly suggest that you'll be able to get rid of stock apps on...

There may be worse feelings than sitting around waiting for food delivery, but I don't want to know what those are. Especially when your local delivery guy misses your address for the eighth time. But soon, Domino's Pizza will take that stupid human error right out of the equation in the form of a robot that's only 3 feet high.

Hey everyone, this will be a quick post. Facebook does not use HTTP Strict Transport Security (A header that tells the browser to only use HTTPS when communicating with the server) on subdomains of facebook.com. That means, if someone uses facebook in a different language, the browser will attempt to connect using HTTP first. An attacker can intercept that request and serve a different page, including a fake login one.

Researchers have discovered a "severe vulnerability" that allows attackers to use eBay to distribute malware, and the online auction company has no plans to fix the problem.

This Is for the Script Kiddies: This tutorial is about a script written for the How to Conduct a Simple Man-in-the-Middle Attack written by the one and only OTW.

Previously, you'd need to install the Google Cast extension to cast webpages from your Chrome web browser to your Chromecast-connected TV, but as of March 24th, you don't need it anymore. Casting now works natively in Google Chrome (which had been available in the Beta version for a few months), and you can activate the hidden feature right now.

Welcome hackers. Hackacademic.RTB1 is vulnerable machine for training our skills.This machine can be download from free from here. There is many tutorial how to hack these machine but i did always be my self.

Welcome finally, to a tutorial on buffer overflows! At last we have reached an exciting part of this series where I will dedicate the entire article on explaining and exploiting the notorious vulnerability. Grab some popcorn, sit back and enjoy the show.

Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.

This is a quick and easy method for receiving the backend IP (1) of a server who is hidden behind a proxy (2) or a firewall (3).

As we're all aware, recon is vital to a successful hack. We need to know everything we can about the target in order to perform the best possible attack. Port scanning is a basic recon concept that is introduced very early in learning proper reconnoissance. The issue with port scanning is that is makes a lot of noise. Every connection to every port will be logged. This is where stealth scanning comes in. Also known as SYN or half-open scanning, stealth port scanning is a bit quieter, and is l...

Out of the box, Windows 10 allows you to search the web right from the taskbar. However, the search engine is set to Bing, and there is no option to change it like you can in the Edge browser.

Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see whether we can make it crash or overflow. This process is known as fuzzing. It is often the first step to developing an exploit, as we need to find some variable that is susceptible to overflowing.

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

In this simple tutorial you will be shown step-by-step how to write local shellcode for use on 64-Bit Linux systems. Shellcode is simple code, usually written in assembly that is used as payload in exploits such as buffer overflow attacks. Payloads are the arrow head of an exploit: though the rest of the arrow is important for the delivery of the attack, the arrow head deals the killing blow. In reality, payloads are slightly less exciting yet far more interesting and intelligent than medieva...

I was so Scared to get this procedure done. I let this Callus give me Pain for about 1 year.

Hello readers, and welcome to Null Byte. Before we start, for those of you who may not know me, my name is ghost_; I'm a relatively active member of our community and have been around for a while.

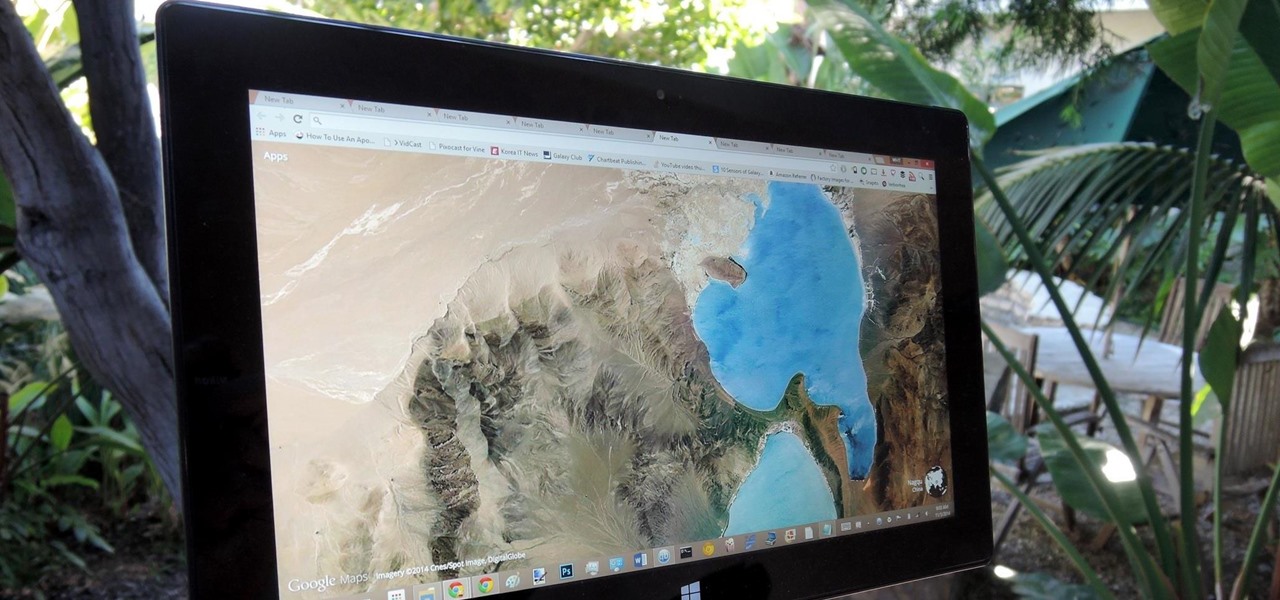
Google Earth has long served as a great tool to explore the furthest regions of our beautiful planet from the comfort of our own homes, but for those with more than just a recreational interest, a bundle of pro features had always cost $399... a year.

A highly useful, yet unrecognized and under-appreciated feature in Apple's iOS 8 is the ability to seamlessly convert incoming texts regarding future dates into calendar events. Messages like "Let's chill tomorrow" can be tapped on and quickly added to the calendar. It's convenient and easy, but unfortunately, not available on most Android devices. However, it's pretty easy to get using Inviter (SMS to Calendar) from developer Sergey Beliy.

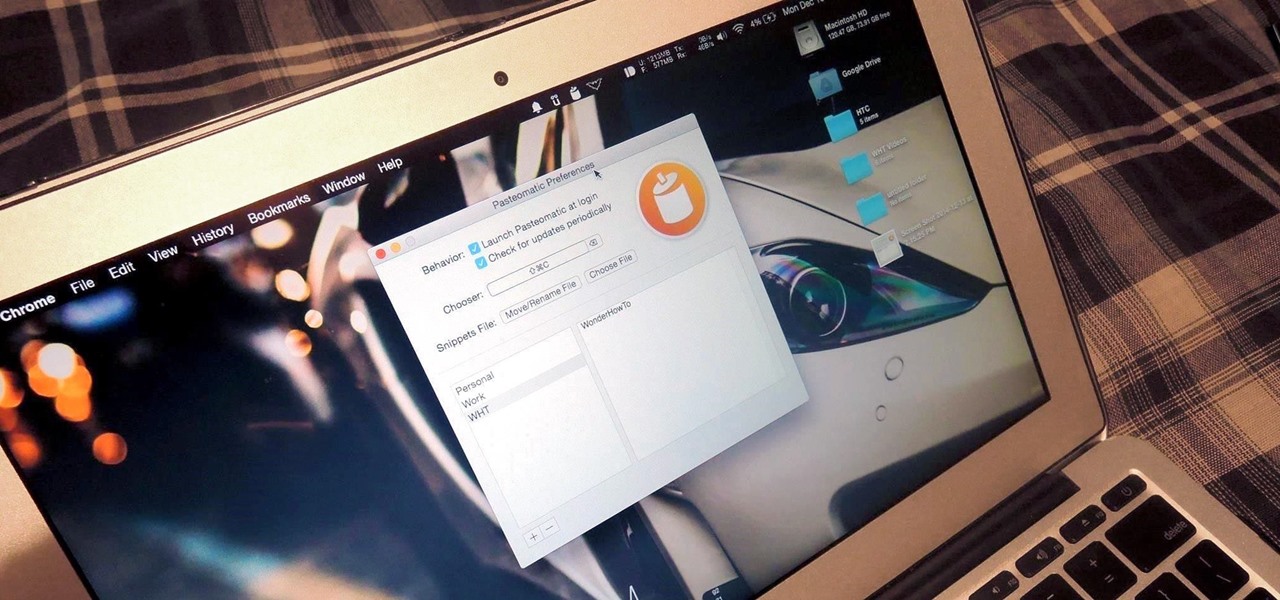
Your Mac's clipboard is great when you are just copying and pasting a phone number or address, but sometimes you end up having to re-copy the same thing over and over every day. To make those phrases a lot more easily accessible, the people over at Tiny Robot Software have released Pasteomatic. With this app, you will be able to use a hotkey to bring up a collection of your most commonly used text snippets and paste them into any text field or document.

Reading articles on an Android phone using Chrome Browser can be a little bit of a battle; it often times requires adjusting the page to fit the screen in order to make it easier to read and scroll through. I sometimes lose this struggle and give up trying to read on my device, saving the article for a later time when I'm on my laptop.

Google Earth is the cheapest way to travel the world, i.e., virtually. Their super satellites give us unbelievable access to images from pretty much any place around the globe, turning us all into would-be world explorers. Plus, these images make for stunning wallpapers.

The release of iOS version 8.1.1 brought some much needed bug fixes to Apple's mobile operating system, but with it came a patch for Pangu's jailbreak method, which worked on iOS 8.0 to iOS 8.1 using a Mac or Windows computer. Luckily, it didn't take very long for a new team of developers to come up with a method for jailbreaking iOS 8.1.1 devices, and much like its predecessor, the process is a cinch.

It seems like every day now that we see a new headline on a cyber security breach. These headlines usually involve millions of records being stolen from some large financial institution or retailer. What doesn't reach the headlines are the many individual breaches that happen millions of times a day, all over the world.

If you're trying to get a new iPhone 6 or 6 Plus, we know you've been struggling to find one, and we're here to help. With Apple's preorder numbers topping 4 million in the first 24 hours, it was nearly impossible to get one during the first wave.

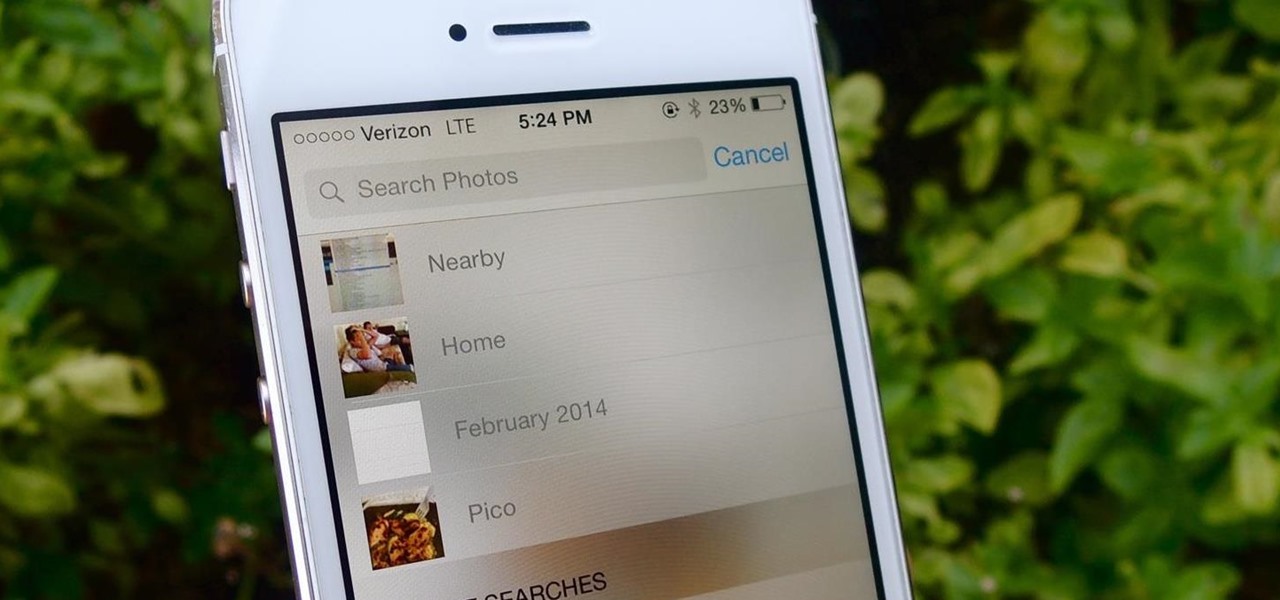
Skimming through the hundreds of photos you may have on your iPhone for that one selfie of you and your friends in Los Angeles can be a tedious task, especially if you were inebriated and snapping pics indiscriminately. Thankfully, as one of the many cool features available in iOS 8, the Photos app now lets you search your images based on date or location.

Canvas fingerprinting is the web's trickiest privacy threat, but it's not impossible to stop. With all the media attention it's gotten lately, it's time we lay out exactly how to detect and prevent this invasive tracking technique.

On a recent trip to Palm Springs, I found myself navigating with Google Maps and virtually exploring my destiniation using its built-in Street View feature. The thing is, using Street View can make keeping track of your exact location difficult as you zoom in, out, and about. It's a little discombobulating.

Android L hasn't made its official release yet, but if you installed the early release using the Windows or fastboot method, you may have noticed some minor inconveniences, like the lack of a battery percentage icon and the absence of a Clear All option in your notification tray.