From the people who brought you the Dummies instructional book series, brings you the same non-intimidating guides in video form. This is Mac for Dummies. Just watch this video tutorial to learn how to connect a Mac to an ethernet network, For Dummies.

Fed up with irritating applications, moronic group requests and unwitty Facebook status comments? Why don't you do the good thing and throw in the Facebook towel? Just admit it and say it out loud, 'I hate Facebook!' You don't have to suffer anymore, just follow this advice to quit and commit Facebook suicide!

A network Tarpit, sometimes know by the German word Teergrube, is a service or set of hosts that deliberately try to slow malicious network connections down to a crawl. The idea is to put up unused hosts or services on the network that respond to an attacker, but do things to waste their time and greatly slow their scanning (or spreading in the case of Worms). To follow along with this video tutorial, you'll need a package called LaBrea by Tom Liston and an unused IP address to tarpit. Set up...

A book query letter must be well written and brief. Heading

Have you ever been away from home or on holiday and noticed an open network connection? FREE INTERNET! But then you find out that every search or page redirects you to an "enter password" or "signup here" page. Well, there are ways around this.
If you are looking for ways/opportunities for you to be politically involved you have come to the right place. Here is a series of links that will take you to a webpage of a location where you can volunteer in and make a difference. In each section you will find:

I can't say it's absolutely true, but when it comes to mobile word gaming, there's Scrabble people and then there's Words with Friends people. It feels segregational. Rarely does one play both. At least, that's what I see when it comes to my family and friends.

When you're out and about in the dangerous world of Wi-Fi, it's hard for the average computer user to stay protected, or even know what being protected entails. Little do most people know, Windows 7 has a built-in security that few people take advantage of: a VPN (Virtual Private Network) server and client.

I have had a lot of people ask me, "How does my neighbor keep getting into my wireless?!". Chances are, these people are all using WEP, a deprecated wireless encryption protocol. Either that, or you are using one weak WPA passphrase.

Despite the fact that you may not find this as a necessity, if you do follow this quick guide, you will wonder how you ever managed before. This tutorial is based on the assumption that you're using Google Chrome, so if you aren't, I advise you to download and install it. Furthermore, this tutorial is aimed towards beginners, however advanced users may also learn a thing or two.

How to Write a Wedding Invitation The wording you use for your wedding invitation is very important. Follow these steps to help ensure that your invite is as formal as the big day.

How to Make the Internet Faster in Windows 7 Go to Control Panel.

Successfully Complete Your CNA Training Program You must finish your CNA (Certified Nurses Assistant) training program and must secure a CNA training certification in order for you to be qualified to apply for CNA state exam.

On June 23, 2003, Linden labs created a free client program known as Second Life. This program allows users, or residents, to interact with each other in a virtual world by using avatars. Thanks to this program, residents are able to explore, socialize, and create and trade virtual property, and services with each other. Second Life has become one of the most popular programs used by various age ranges from 16 to 60, but how do you enter this world and get your own avatar?

Justin Rose shows us a method to develop a pre-shot routine. It is very important once a routine is established you do it each time you get ready to address the ball. Create a pre- shot routine.

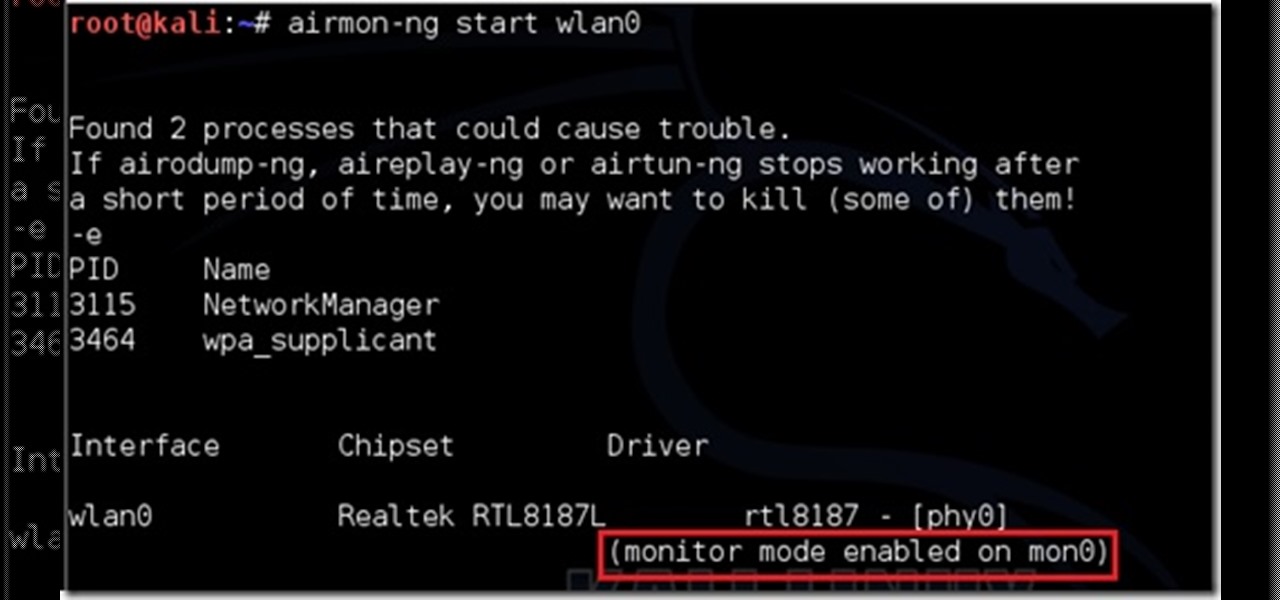
This is my first post please tell me what I can improve. (I don't claim any of the images. I tried taking screen shots but it froze my computer. ) I will be using wlan0 because thats my wireless but use yours.

Wireless networks. Nowadays, everyone uses 'em, but most don't secure 'em. On average, I can drive up and down any block in my city and find at least one or two open or semi-open networks on any given day. With some changed MAC addresses for good measure, an attacker can use your network as a spring board for who knows what. When the police come a few days after, they are coming to your door—and not to talk about how nice your lawn is. Don't be that guy.

Before you start snapping away and submitting your photos, please take some time to read the official rules below!

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.

CRISIS MANAGEMENT PLAN A FORM TO FILL OUT FOR WHEN CRISES ENTER YOUR WORLD

Some of you might be using Tor to host hidden services, and some of you might not even know what hidden services are. If the latter's you, do not miss this article. Why? Because you can host your websites and services on the I2P darknet. It's safe and secure—it's anonymous.

In this video tutorial, viewers learn how to set and encrypt your Wi-Fi password using WPA on a Linskys router. Begin by opening your web browser and type in the address: Click Enter. Now type in your user name and password, and click OK. Then click on the Wireless tab and select Wireless Security. In the Security Mode drop-down menu, select WPA Pre-Shared Key and then type in a password under WPA Shared Key. Finish by clicking on Save Changes. This video will benefit th...

In this video tutorial, viewers learn how to disable their Wi-Fi SSID broadcast on a Linksys's router. Begin by opening your web browser and type in this address: Press Enter to access the page. Then type in your user name and password. Click OK. Now click on the Wireless tab and check Disable under "Wireless SSID Broadcast". Finish by clicking on Save Changes. This video will benefit hose viewers who use a Linksys's router, and would like to learn how disable their broa...

In this Computers & Programming video tutorial you will learn how to establish a Remote Desktop connection in Windows XP. 1st you got to enable remote desktop. To do this go to start, right click on My Computer and click on properties. Then click on the remote tab and click on ‘allow users to remotely etc’ and click on ‘select remote users’. Click add and add your account. Click OK, apply and again OK. Now get your IP. Click start > run and type cmd. In the cmd prompt type ‘ip config’ and not...

Watch this video to learn how to encrypt Wi-Fi using WEP password on Linksys in 4 simple steps. Connect to your wireless network. Open your Web browser and type in the web address http://192.168.1.1. Press enter key. Type in the User Name for your network. Type in the Password, press OK button. Select the Wireless text tab, select the Wireless Security text item. Pull down and select the WEP menu item. Type in a good password. Click the Generate button. Click the Save Settings button. Encrypt...

This video demonstrates how to connect a Mac to an ethernet network. From the people who brought you the Dummies instructional book series, brings you the same non-intimidating guides in video form. Watch this video tutorial to learn how to connect a Mac to an ethernet network, For Dummies.

In this video, Sky Van Iderstine will tell you how to get your IP address e-mailed to you every time it changes by using a freeware program, Wimp. With this information, you can then track your stolen Mac laptop or even desktop's location using www.ip-adress.com (the "adress" is not a typo.) Imagine the look of the police officers when you show them the satellite picture of your suspects location! Locate your stolen Mac laptop using Wimp.

Target golf... Nick Bradley explains why excellent alignment at set-up is crucial if you want to hit pin-seeking iron shots.Just a few millimetres out in your alignment at address can equate to yards out when your golf ball lands on the green. And that can make the difference between a birdie and a bogey.Use Nick's aligment drill and you've got no excuse for not hitting irons spot-on, every time. Hit straighter irons.

Social networks like Facebook and Google+ are great for staying connected with family, friends and coworkers—even fans. But sharing and communicating with practically anyone in the digital realm has alienated us from most of the flesh-and-blood beings we see everyday—our neighbors. How well do you know your neighbors?

Have you ever come across a cute YouTube video that you absolutely fell in love with, and wanted to share it with your friends on a big TV? Unfortunately, YouTube doesn't have a "Burn to DVD" button next to every video. But after following the steps below, you won't need one. You'll be able to rip any video from YouTube and burn it directly to DVD, just in two clicks.

In this video the instructor shows how to allow email from people you know and block emails from all other users in AOL 9.0 for Windows. To do this, first open your AOL mail box. Go to the Mail Options menu and select the option "Block Unwanted Mail". This pops up an "AOL Unlimited Use Area" screen. You have to select "Yes" to proceed. This opens the Mail and Spam controls window. Now scroll down in the window till you find an "Additional Spam Filters" heading. Now there is a Select Filter ov...

One of the most simple and cost effective ways to liven up your landscaping is through subtle illumination. Low voltage lighting is simple to install and offers many benefits including ambiance, safety and security. They can be used to illuminate a walkway or to lighten up your home's street address at night. Today's manufacturers are making low-voltage lighting products geared for the do-it-yourselfer, which makes purchasing and installation easier. These low-voltage kits come with a transfo...

One of the most simple and cost effective ways to liven up your landscaping is through subtle illumination. Low voltage lighting is simple to install and offers many benefits including ambiance, safety and security. They can be used to illuminate a walkway or to lighten up your home's street address at night. Today's manufacturers are making low-voltage lighting products geared for the do-it-yourselfer, which makes purchasing and installation easier. These low-voltage kits come with a transfo...

Business owners and marketeers are diverting from traditional marketing techniques, including billboards, radio and TV advertising, brochures, and any other outdoor promotions, to cheaper but effective Internet marketing strategies. Under the new arrangement, business owners reach out to the final consumers through advertising on the World Wide Web.

Haven't you ever wanted to live in a futuristic home? I think that homes are headed towards an era where they will be controlled by our computers and smartphones. No longer will you have to find your keys to unlock your door, or wait until you get home to monitor your security, because X10 is here.

Yesterday, I started receiving emails from Google+ that looked like this: I was really confused. I was confident that I had already gone through my personal Google+ account notification settings, and turned off all email notifications. I noticed that there was a link at the bottom of the email, that said I could change what email Google+ sends you. When I clicked on it, it took me to my newly created Google+ page's settings: +Yum!

If you follow the Anonymous, Occupy, and IT security scenes, you have no doubt heard about a dox release. What is it? How can it hurt you? And most importantly, how can you protect yourself from it? Some of these steps might seem common sense, while others will be an ah-ha! moment. Your private info is both your biggest weakness and your biggest weapon in your battle to remain anonymous. You must learn how to use it as both.

TCP/IP Client / Server Application Hello! Today's blog post will be about coding a very rudimentary Client and Server application duo, which will communicate by using TCP Sockets.

Six months ago, 1.3 million registered users of Gawker Media had their passwords compromised when the site was hacked by Gnosis. The passwords were encrypted, but 188,279 of them were decoded and made publicly available for all to see. Just three weeks ago, Sony Pictures was hacked by LulzSec, with 1 million passwords taken and 40,000 made publicly available. Comparing the two data sets, Troy Hunt found 88 accounts on both sites that used the same email address, and of those accounts, 67% use...

Spam is everywhere and Facebook is no exception. In fact, spammers are constantly stepping up their game by tricking unsuspecting Facebook users to participate in quizzes, games, apps, or "new features" that are actually dangerous computer viruses, spyware, or other trojan horses in disguise. Their attempts even trick people into unknowingly becoming spammers themselves.