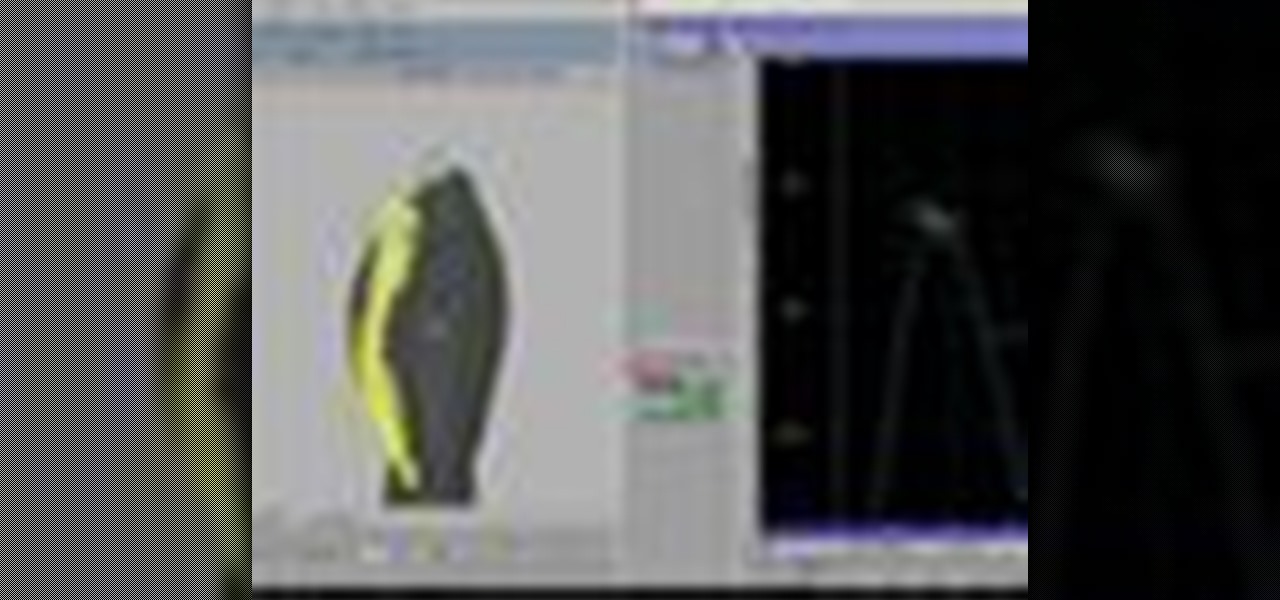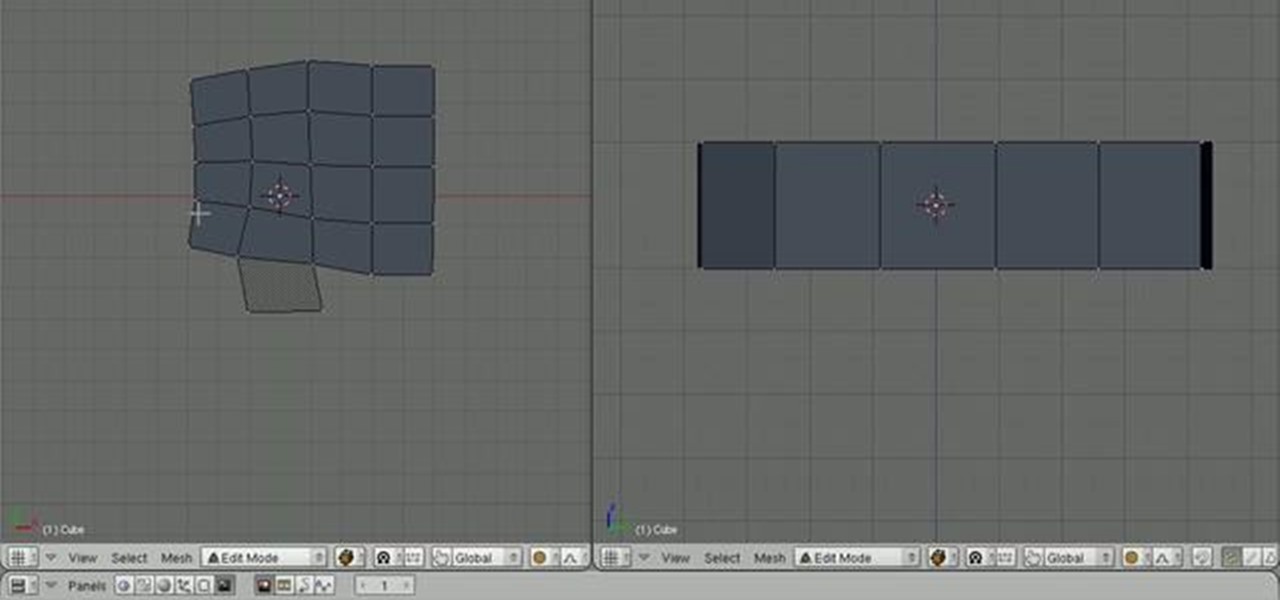
Modeling a human hand is a challenging task. Both to create a natural-looking hand and to create one with good topology. This tutorial is an effort to address both of those issues. In this tutorial you will learn how to model a human hand with some box modeling techniques with clean topology in blender. Whether you're new to the Blender Foundation's popular open-source 3D computer graphics application or are a seasoned digital artist merely on the lookout for new tips and tricks, you're sure ...
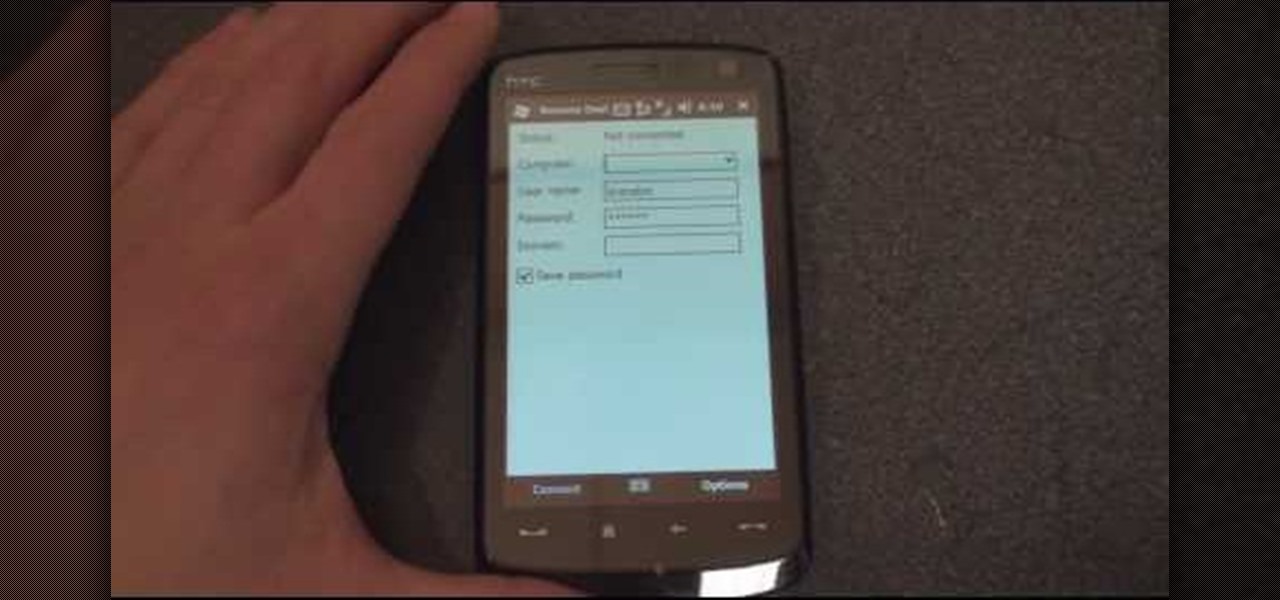
In this tutorial Brandon from Pocketnow.com will show you how to set up and use your remote desktop on a Windows mobile smart phone. Windows mobile remote desktop allows you to remotely access and control your Windows computer from your cellphone device, it is just like controlling your computer but in the palm of your hands. This guide will also show you how to get the Remote desktop software on your cell phone device if you don't already have it. The remote desktop requires for you to have ...
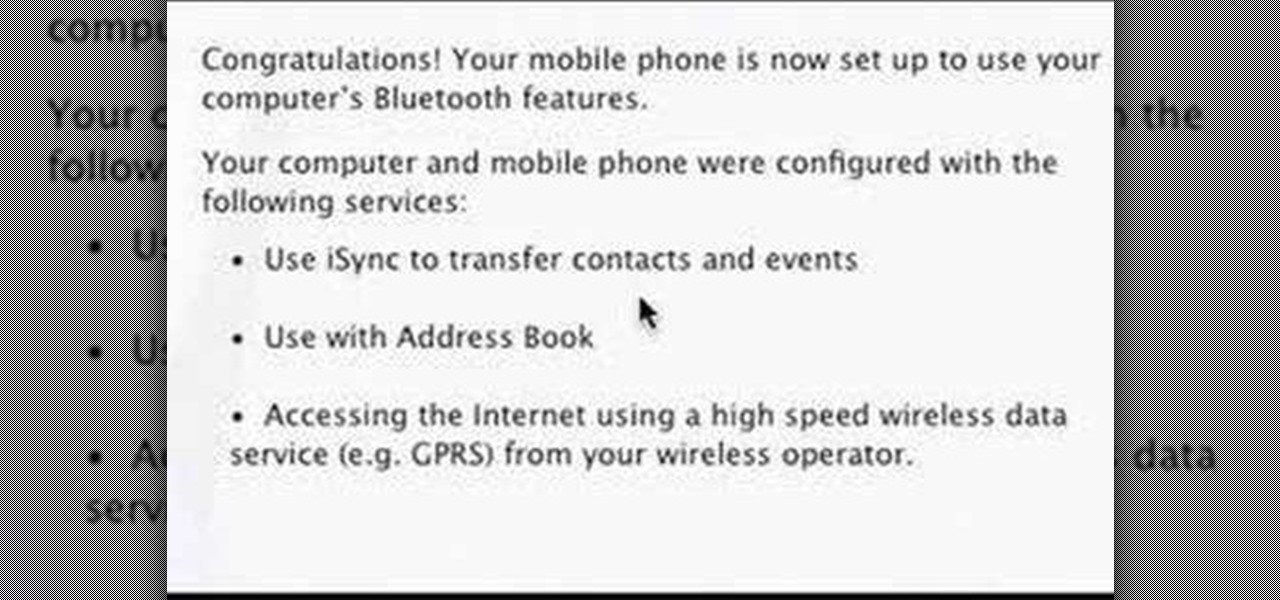
In this video you will learn how to setup a Bluetooth mobile phone in OS X. To do this go at system preferences select Bluetooth click on Discoverable, Open Bluetooth Setup Assistance and Show Bluetooth Status in the menu. Then click Sharing and mark all the options. Now go at devices, select set up new device, mark mobile phone, click continue, wait until the device will find your mobile device, click continue and you will get a pass key. Enter that passkey. A window will pop-up where you ca...
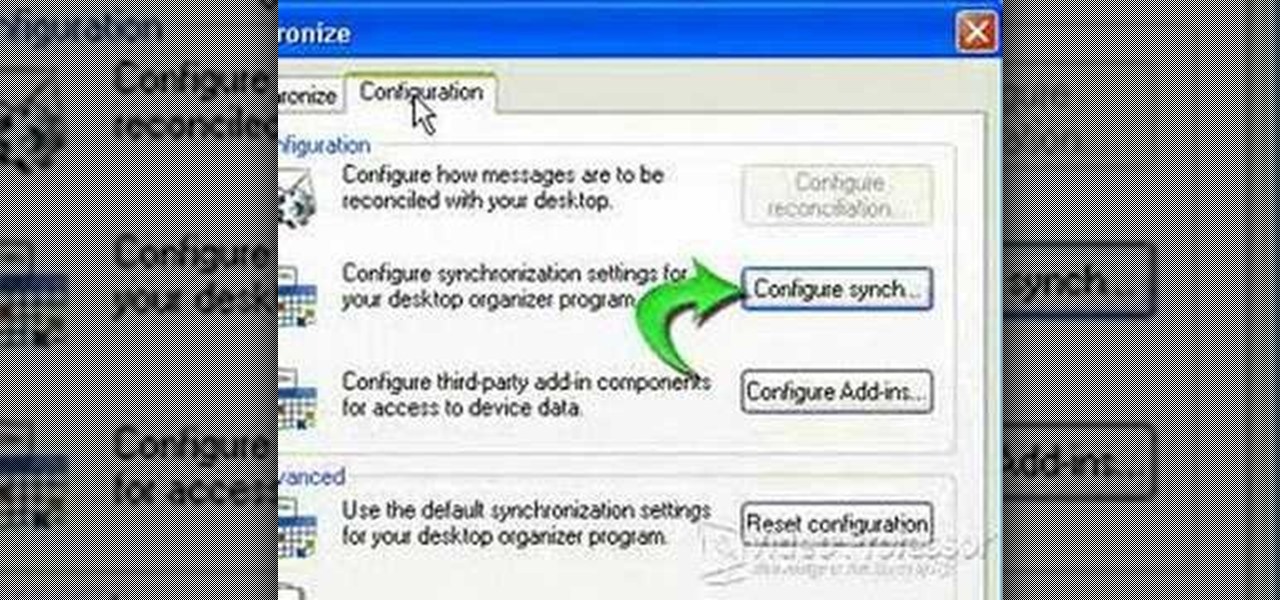
This video shows how to synchronize our blackberry smartphone with MS outlook. First open up the Blackberry Desktop Manager. Let us start by synchronizing the blackberry. Double click the synchronize button to load the synchronization settings. Here we can specify what we want to synch and where we want to synch firm. Click the configuration tab and select configure synch. Our device configuration menu let us pick which application on the black berry to synch and where to synch. Today we are ...
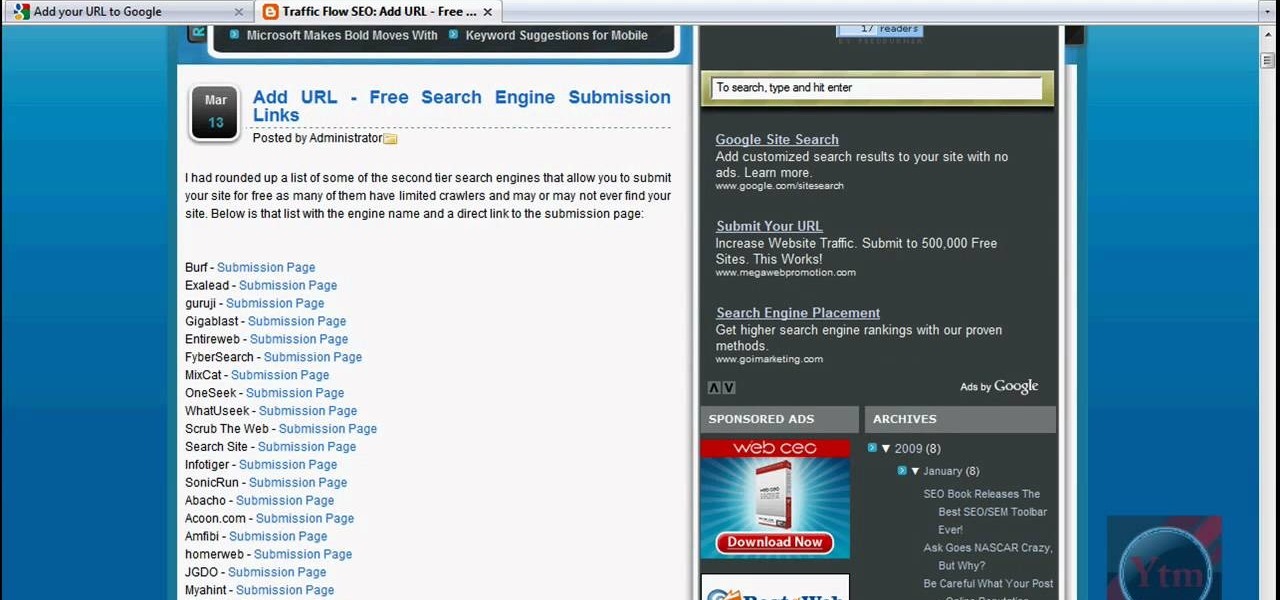
Learn how to submit your website to the Google search engine in simple steps. 1. First go the Google home page and type in the address bar '/addurl'. 2. Now type the URL of your website in the text box correctly and enter some details about your website in the Comments area. 3. Now type in the verification code to finish and add your website to Google. 4. You can even submit your website to many other search engines like Google.
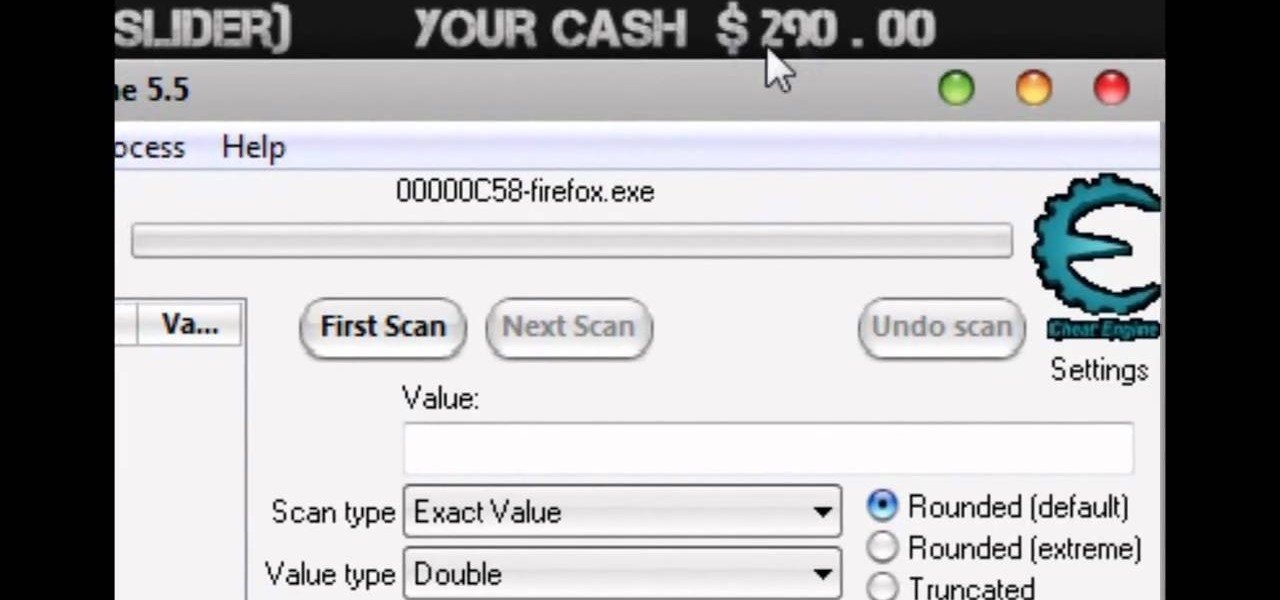
In this video tutorial, viewers learn how to hack the flash game, Palisade Guardian 2: Modern Combat with Cheat Engine. Begin the game by entering your name and play the first level. After that, open up Cheat Engine and select your internet in the process list. Change the Value Type to Double and Truncated to Rounded (default). Enter in the value of your cash and press First Scan. Then buy something to lower your cash and enter in your new value. There should be only 1 address. Check the froz...

In this video, viewers learn about factory maintenance schedules and how to care for a vehicle. The series explains the differences between repair and maintenance, and the difference between do-it-yourself repair and professional auto repair services. Tips address choosing an auto mechanic and following factory and maintenance schedules. Increasing your vehicle's safety, reliability and longevity through proper maintenance also is discussed. This video will benefit all viewers who own a vehic...

Grilling baby back ribs to perfection has just been introduced with this Step by Step Project from Lowe's. Here you'll find the web address for some printable ideas and tips for grilling. You'll also get easy and great recommendations for cooking pork on the grill. Need to know how to arrange the charcoal on the grate for optimal cooking? Do you know what the internal temperature should be when grilling baby back ribs? The answers are in this short video. Happy grilling!

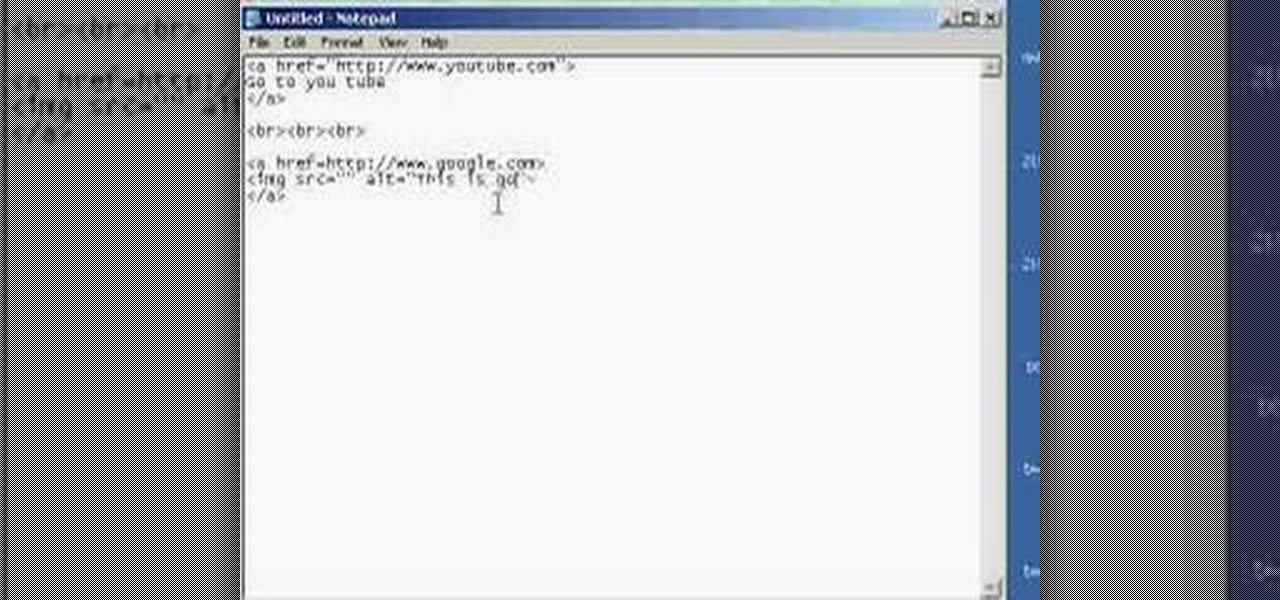
Have you ever gone to websites and seen an entire URL address you have to copy and paste into your browser window? Is the thought of having such an inconvenience on your page making you wish there was a better way? Today is your lucky day because success is going to teach you step by step how to make a HTML hyperlink that user of your website can use to navigate to different portions of your website without the inconvenience of copying and pasting long dragged out links.

Welcome to a tennis lesson from FuzzyYellowBalls, the the best place to learn how to play tennis online. Our free video tennis lessons teach you how to play the game in a new way that combines technical analysis, visual learning, and step-by-step progressions.

Learn the important steps necessary for the best printing experience when printing to the Epson 3800. This tutorial is specifically designed to address some of the issues with the Epson 3800 and the MAC OS X Leopard operating system. Here is a detailed explanation of the changes that were made to the 10.0.1 update to Adobe Photoshop CS3. Remember, having all the current versions of Adobe Photoshop, and the Epson drivers is critical to success when printing.

In this tutorial Mike Lively of Northern Kentucky University shows you how to get started with Wireshark. Wireshark is a network protocol analyzer for Unix and Windows. It is used for network troubleshooting, analysis, software and communications protocol development.

In the following lessons you will learn some essential tools and techniques for working with muscles in Houdini. In the first lesson, you will learn how to rig up a simple muscle arm using Houdini's Muscle tool. The Muscle tool uses meta-balls to capture your character's skin with realistic muscle/skin interaction.

Topiaries are no longer just speciality plants. They have become very popular and are showing up in garden centers and nurseries across the country. Topiaries have been used for thousands of years, in places like Babylon and England. Today we take the mystery out of topiaries and discuss pruning trees and shrubs to look like geometric forms. As well we talk about designing topiaries, selecting the trees and shrubs and maintaining them to look their best and show you how to create small topiar...

The SATs are a very valuable college entrance test and could determine if you're accepted or denied to your favorite university. So, once you've learned to ace the SATs and have already taken your test, get your scores as soon as they're out! Don't sit in dreaded anticipation— go to College Board and get your SAT test results now!

In 1998, a Beechcraft Baron was following a Boeing 757, with approximately 3 to 5 miles separation. Air Traffic Control warned the Baron pilot three times with the phrase the phrase pilots hear on a regular basis: "Caution. Wake Turbulence".

Patrick Norton and Veronica Belmont from Tekzilla will show you how to dual boot Windows 7 and download videos from YouTube. The hosts show viewers how to dual boot Windows XP Pro32 bit and Windows 7 RC 1 64 bit. In the first step as always you will want to back up your hard drive and at the very least they recommend to back up your most important files. In the case that something goes terribly wrong you can use a free program called EASEUS to make a complete image of your whole drive, this a...

Videomaker Associate Editor Tom Skowronski explains how four basic steps can be used to improve the lighting effects for a video and give it a more professional look.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

Country Story hacks, cheats, glitches. How to hack Country Story. Watch this video tutorial to learn how to cheat Country Story: dog hack (09/26/09).

Check out this DIY video tutorial from Curbly, the best place to share pictures of your home, find design ideas, and get expert home-improvement advice.

This video will show you how to record video on your Apple iPhone 3G for free! This is a complete guide to installing the iPhone Video Recorder on your iPhone 3G, which also works on the First Generation iPhone.

This tutorial covers the ABC's of getting started in Web Development. Mike Lively shows you how to get a server, a free HTML editor, and free FTP Software.

Want to earn coins and easy experience for your Pet Society pet without, you know, actually having to play the game? It's easy. This video guide show you everything you'll need to know to generate unlimited experience and digital cash money.

If you read my article on the OSI model, you got a good overview on communications from that model's perspective, but how does that relate to TCP/IP? We're going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC address work together? If you want to hijack sessions and all sorts of lulz like that, you need to understand these concepts. Let's get into it, mates!

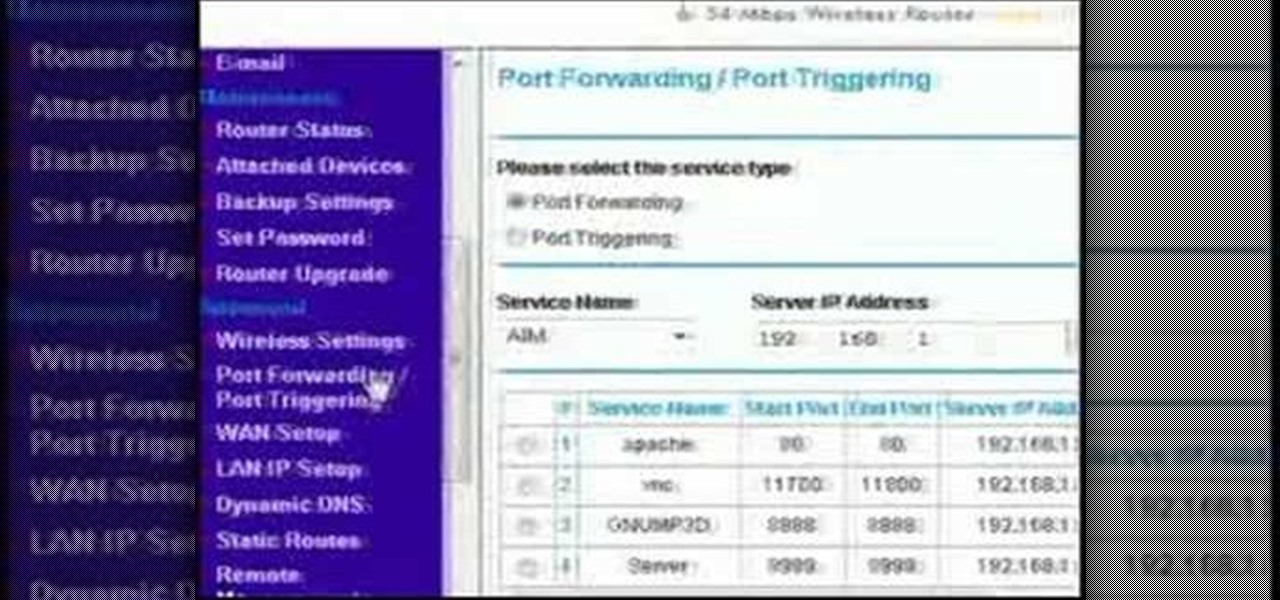
This video discusses how to bypass your router to access your server. In the search window type in CMD to open up a command prompt. Then type in ipconfig to bring up the ip configuration. You want to look for the ip address for the default gateway and the one for your computer. They should both start with 192.168. Once you find them open up internet explorer and type in the ip address for your default gateway and it should then prompt you for a user name and password. Log in and look for a po...

Apple has a few exciting surprises for you in its latest iOS 16 and iPadOS 16 software updates. Released on Thursday, May 18, version 16.5 includes new features, bug fixes, and security patches, and there are even hints of some big things coming in future software updates for iPhone and iPad.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are all network services, which means we'll write our first remote exploits.

Remote Desktop gives you access to your Windows 8 PC or device from wherever you are to run your applications and access your files remotely.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

Hello everybody. I'm back with Part-2 of this series. In this part we will be programming in C our server and i will be explaining one more "key concept" so everybody got a better understanding on this.

One of Android's most glaring weaknesses is its lack of an iMessage equivalent. That is, of course, until now. There's one app that will allow Android users to experience iMessage on their non-Apple phone, complete with end-to-end encryption, message effects, and group messaging.

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.

By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.

Tool is selected, followed by email accounts and a selection is made at the "add new email account" option , the "next" button is clicked. Pop3 is selected and the next button. The required information is filled in such as name, amail address, incoming and outgoing mail server, username; which is the same as the email address and the password is entered. The "remember password" option is selected, along with the "more settings" button. Within the more settings window, the company name and a r...

In this video you are shown how to use proxies and why they are important. Proxies are useful because they shield you and make you anonymous over the internet, it also prevents websites from logging your IP address. To see how important it is to prevent this go to whatismyip.com. It will show you your IP, click on it and go to 'look up'. It will show you all the personal information that can determined from your IP address. The easiest way to proxy are VPN's, which stands for virtual private ...

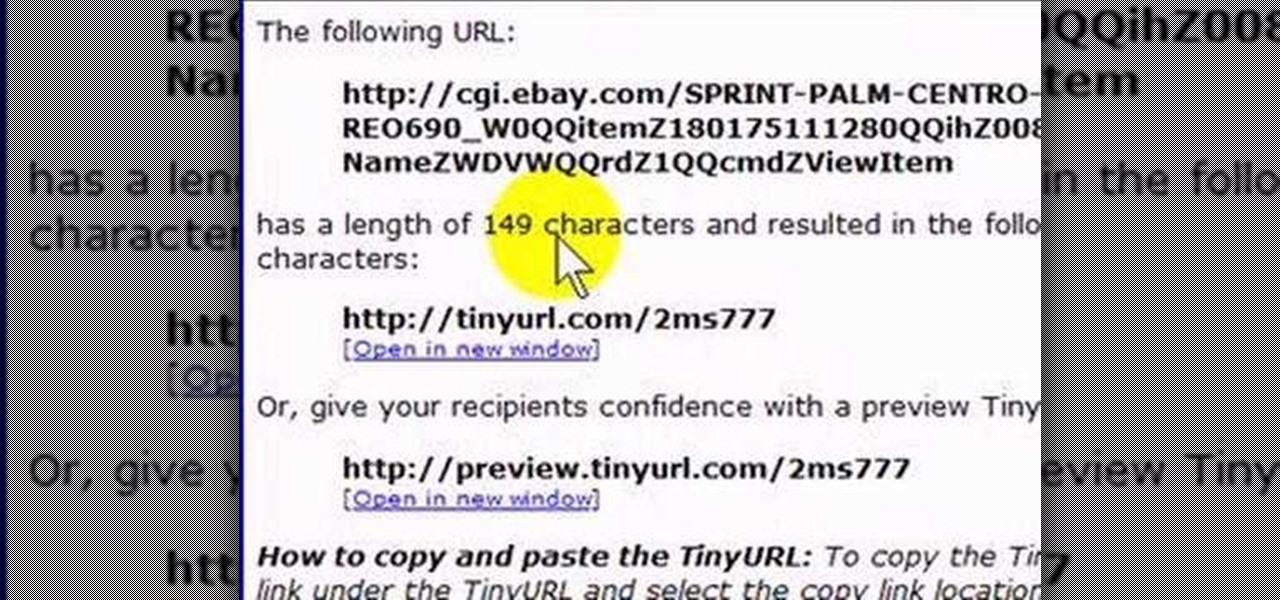
If you like to share websites via email, are a writer who needs to share email in her stories, or just need to make a quick written note of a website address, you need to know how to use web address shorthand. Some URLs can be hundreds of characters long and therefore too tedious to reproduce in writing. To make an easier-to-communicate link, you'll need to use a URL minimizer, like TinyURL. Learn how with this address-minimizing how-to!

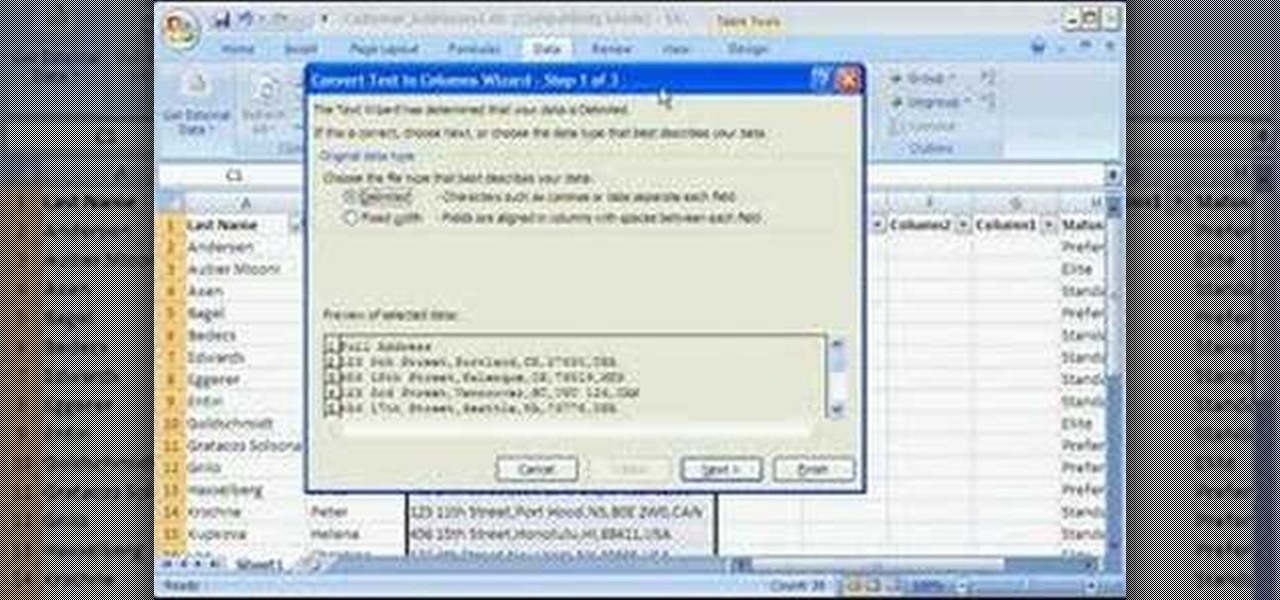
Storing information, such as a full address, in one column can limit what you can do with that information. For example, you can't easily filter or sort by part of the address, such as country/region or city. However, if you break up the address into its parts — street address, city, state/province, postal code, country/region — one for each column, you can remove those limits. Watch this instructional video to see how to use the Convert Text to Columns Wizard to automatically break up a sing...