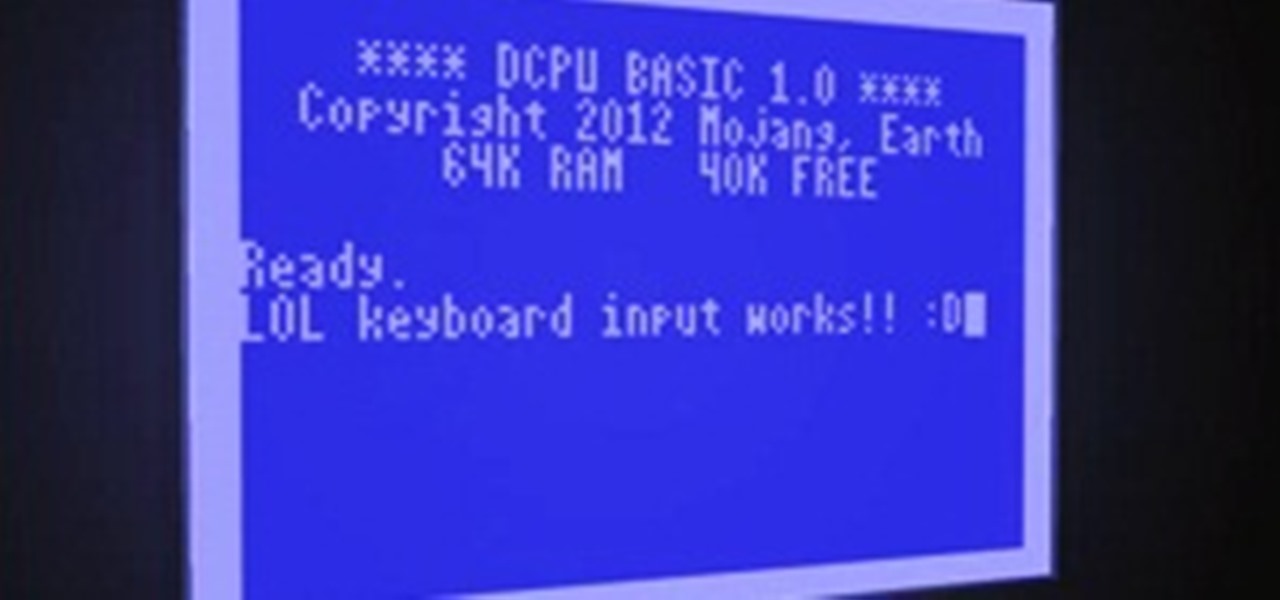
The developer community has already made some incredibly quick progress on implementing assemblers, interpreters, and emulators for the proposed virtual computer in 0x10c, Notch's latest game. But the truth is that the majority of programmers out there couldn't be bothered with spending enormous amounts of time writing anything much more complicated than a "hello world" application in assembly. What's on the top of everybody's mind is creating a compiler for a more widely used language.

G+Me is one of our favorite Chrome extensions here at Google+ Insider's Guide. We love it because it's one of the most comprehensive extensions out there. It attempts to address the "noisy streams" issue, with list mode, and collapsible posts and comments. The creator, +Huy Zing, is very responsive to feedback, and he's been quick to address any issues that arise, including privacy concerns. He's even created a G+Me (Paranoid Edition) extension, for the extra careful Google+ user. And if you ...

Here's a nasty little Null Byte. An open redirect vulnerability was found in both Facebook and Google that could allow hackers to steal user credentials via phishing. This also potentially allows redirects to malicious sites that exploit other vulnerabilities in your OS or browser. This could even get your computer flooded with spam, and these holes have been known about for over a month.

Having an SSH or Secure SHell to tunnel your traffic through is something we have talked about many times at Null Byte. As we know, it allows us to securely route and encrypt our traffic through a remote server, effectively anonymizing us and protecting our traffic from all forms of analysis—simultaneously. We have gone over how to make a home SSH tunnel. However, the question has come up, "How can I get an SSH tunnel to somewhere other than my computer?" This would be useful in a situation w...

I love role-playing games. They tell great stories, require intense strategy, and make minimal demands of my tyrannosaurus-like hand-eye coordination. The idea of an RPG experience, at least on paper, is to allow users to play the role of a character. However, real people do not gain generic experience points for killing things, nor do they pause for each other during combat or have the ability to carry hundreds of potion bottles without slowing down. These can be fun gameplay mechanics, but ...

Private browsing is all the rage with browsers these days. Once you go into private browsing mode, you can traverse the internet without leaving a trail. Your history? Deleted. Your cookies? Destroyed. Your bookmarks and non-private history? Preserved for when you come back to the surface.

Tip If some of your friends did not get the email, find one of the 5-15 people you selected who did, ask them for the link and fix it using the steps below then share it on your feed so it can get clicked by anyone!

By Ethical Traveler As the world becomes ever more interconnected, being an ethical traveler becomes both easier and more urgent. Travelers today have access to far more information than we did even 10 years ago. We can observe–almost in real time–the impact that smart or selfish choices, by governments and individuals, have on rainforests and reefs, cultures and communities.

We've talked about the deep web before, but we never really covered the details of what's out there. It occurred to me that a nice list of resources would be very helpful to all of you anons out there. Think of this like a helpful brochure to the hidden web.

Readings from The Rattling Wall. Issue @skylight Books Date: March 17, 2012 @7pm Skylight Books.

Previously, we talked about how to secure Firefox. Today, we will talk about securing a Chromium based Browser. Why? Because Chrome recently beat Firefox in holding more customers.

Skyrim really took the cake this year. With its awe-inspiring gameplay, much improved combat and leveling system, and a fresh new look, it's no wonder the game has already received a Game of the Year award. But for hardcore gamers, the fun may be over. You've played the game for thousands of hours, and have exhausted the entire game's main and auxiliary quests. You need more.

Google Reader is ostensibly just an RSS aggregator, a tool that lets you catch up on your favorite blogs. How could Google have anticipated that getting rid of its social features could have angered so many people who were actually using it as their default social network, and who enjoyed it precisely because it didn't function like Facebook or Google+?
Unless you avoid the news entirely, you've almost certainly heard about the hacking sprees that have been taking place over the past several weeks. Tens of thousands of usernames, passwords and email addresses have been released online for anyone to download. Thankfully, it seems that one kind soul has put all that compromised info to good use.

Wondering why your inbox is looking a little threadbare? It may be that you've violated a few unwritten rules of email etiquette. Here are a few basic tips that the web-savvy know by heart.

These Dutch architects fear that those Chinese drivers might get confused! You may think I'm making a cheap joke about Chinese drivers. But I'm not. The Hong Kong-Zhuai-Macau bridge is a 31-mile, $10.7 billion project and this unique design is meant to address a clash of two driving conventions.

Rose Levy Beranbaum is an award winning baker, cookbook author (The Cake Bible), and authority on CAKE! I recently stumbled across a collection of "Cake Questions" on Beranbaum's blog that address a variety of issues that may come up:

Big brother is watching when you're playing around on another system—and big brother is that system. Everything from operating systems to intrusion detection systems to database services are maintaining logs. Sometimes, these are error logs that can show attackers trying various SQL injection vectors over and over. This is especially so if they are using an automated framework like sqlmap that can spam a ton of requests in a short time. More often than not, the access logs are what most amate...

In my recent Darknet series, I attempted to connect the dots on the Deep Web. I covered the two largest anonymity networks on the Internet today, Tor and I2P. While my initial four articles were meant as an introduction, I ended up receiving a lot of interesting comments and messages asking the technical differences between the two. I'd like to thank all of you for letting me know what was on your minds, as you should always!

Circles. They are both the best thing and worst thing about Google+. They're great because they allow you to fine-tune who you're following and who you want to keep in touch with, making it easy to keep your family and friends separate from each other. On the other hand, they can be a pain to maintain, and you can easily become overwhelmed from the "noise" of popular posts, which make it hard to concentrate on some of the people you want to focus on. But if you invest a little bit of time in ...

Three years ago, Scrabble was one of the very first 500 mobile applications to appear on the new iTunes App Store, allowing iPhone users the chance to kill their Scrabble cravings on the go. It was a smart move for Hasbro and Electronic Arts (EA), but it's been two years and eight months since the Android Market opened for business, and they've just now released an official app for Android smartphones—Scrabble Free.
Moscow, May 21 — Some Western countries are still considering a military operation against Iran as an option over its nuclear programme, a Russian minister said Sunday.

You see before you the humble block: This single, unassuming block couldn't possibly hold anything of value, right?

Update: Based on comments from Adam Novak, this article has been updated to better reflect how the video memory range works. You can check out his working emulator (written in c) here.

April is poetry month! During April Planet Poem will host the first Planet Poem poetry competition. People will be able to post two poems to our world. Two groups of four students will vote on the winner. The grand prize winner will win a French Beret!

This is a great opportunity for writers who want their voices to be heard PEN Center USA

There are many websites that let you watch videos, but that don't let you download it for later viewing. Even if there is a download option, most of the time it requires you to pay some amount of money. Luckily for Mozilla Firefox users, there is a way to download the videos you stream for free.

In this article, I'll show you how to make a simple Gmail notifier. Python can do various things in terms of notifications; sending commands to an Arduino unit, playing sounds, opening windows, etc. The code below simply plays some music, but the possibilities of notification methods are endless. If you aren't familiar with python, there are many sites with tutorials like this one, or this one.

As many of you may have noticed, nearly every Google product (i.e. Gmail, Google search, etc.) has gone through a bit of a makeover since the release of Google+. Big blocky buttons and enormous font sizes are apparently the thing of the future, and with a cool JavaScript hack, you can have a goofy YouTube, too! Now, I'm actually just being a bit facetious, the new YouTube is really the only thing that I like out of all of Google's recent redesigns. It looks pretty sleek.

Now that it's been a week since Google+ rolled out pages, we've gotten over our euphoria at finally getting the feature after a long wait, and reality is starting to sink it. It's not as flexible as a Facebook page, it seems to be time consuming, and you can't even get a unique URL. On the other hand, your Google+ page will show up in Google searches, and help bump you up a bit. Here's how the search stacks up when I search for "WonderHowTo" in Yahoo! vs. Google (Note: I've turned on private ...

I was working on a different Google+ Insider's Guide post when suddenly, my Google+ stream started filling up with news of Steve Jobs' death. Since that moment, many people in the tech industry have paused to reflect on the legacy that Steve Jobs left behind, and talk about what his vision meant for the rest of the industry, and for them personally. There's no tech sector that was untouched by Steve Jobs' influence, and that includes Google.

Have you been sharing your Netflix password with your friends? How about Rhapsody or Hulu Plus? If you get caught sharing your online subscription accounts, you could be slapped with a fine and even imprisoned.

If you powered up the ol' Xbox 360 last night to watch Netflix, you probably noticed that a new streaming service moved into Xbox LIVE—Hulu Plus. Netflix finally has some competition. Or maybe not. But with a week of free service, they're sure to attract some would-be watchers.

Find a PDF You need a PDF file on your computer to convert, so keep the file path in mind.

This is the last week of an eight-week contest that I just happened upon. One winner is awarded from each week so it's not too late to enter if you have pictures of this theme. The voting starts next week and is open for a week. Submission and the rules are easy for a chance at $250.

If you would like to restrict what appears on your Facebook page, here's a novel way to retain ultimate control, coined the "super-logoff" method:

Gifting links for FrontierVille Please visit FrontierVillePost.com for gifting links!

There have been a few recent developments in Los Angeles that only highlight how dysfunctional the city is when it comes to encouraging their citizens to develop greener habits.

Lifehacker provides a helpful guide for Facebook addicts everywhere. How does one get around an employer's website blocker? The trick is to set up a local web server running from home, from which you can use a proxy to access any site you please.

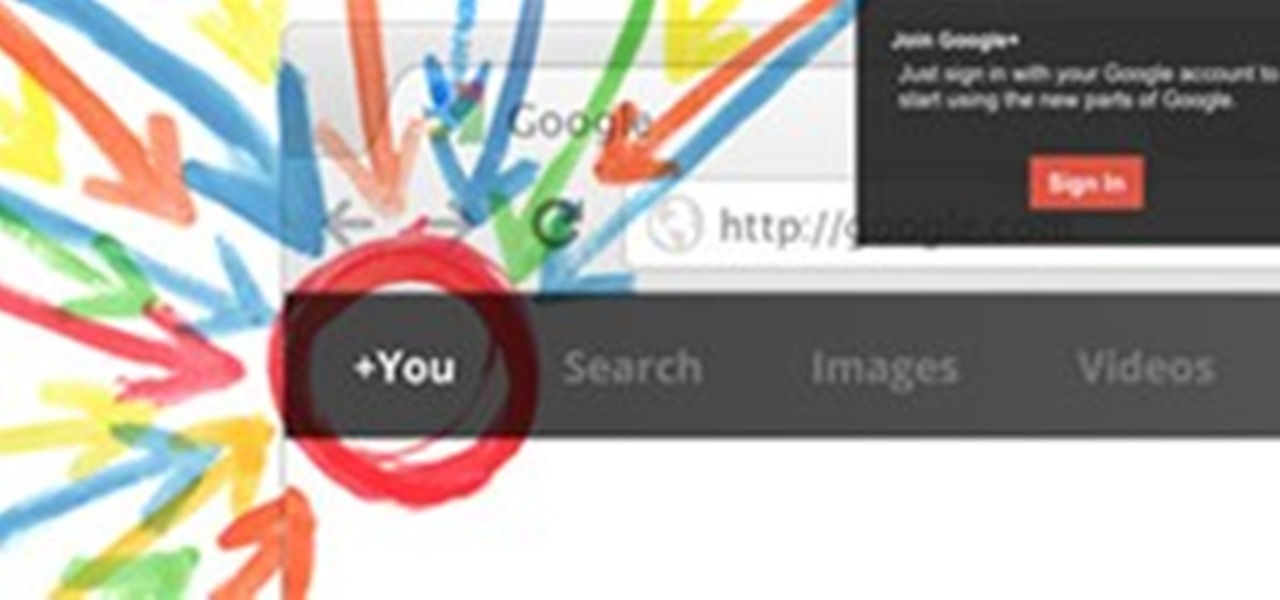
You've finally got an invite into Google+. Now what? At first glance, things can be a bit overwhelming. We've got some great tips to help you get started.