With the announcement of Google Glass Enterprise Edition last week, a literal behemoth entered the arena of companies serving augmented reality solutions to business customers. While Google Glass, with the backing of Alphabet, has the potential to be a disruptor, the field already has a number of players who have been in the game.

Tesla has confirmed the EV carmaker has begun to upload videos from models equipped with its latest flavor of Autopilot, as Tesla seeks to "fleet source" data to help improve its cars' machine learning capabilities.

The HoloLens is a natural medium for 3D data visualization, which offers a far more ideal approach over 2D screens to managing multiple resources simultaneously and grasping the bigger picture. We've already seen how management is using holograms to oversee cities, firefighters, and the military, and now training for sports teams is being addressed with VAR Football.

For some time now, there has been quite a bit of speculation as to when the selection of augmented and mixed reality head-mounted displays would begin to trickle out to the public. Pricing, availability, and software selection are all issues that will have to be addressed before widespread adoption will start.

Google has a new smartphone, and if you own a TV or a computer, you've almost certainly heard about it. The ad campaign for the Pixel and Pixel XL is approaching iPhone levels of omnipresence, as Google has reportedly spent over $3.2 million on marketing, with that number expected to skyrocket in the coming months.

Things are definitely starting to shape up with iOS 10. After three developer betas of the upcoming operating system, Apple has begun rolling out the developer beta 4 release for iPhone, iPad, and iPod touch, which focuses mostly on refining some of the cool new features.

Over the course of the past century or so, media consumption has gone from a few readers enjoying their local print publication to billions of users viewing countless hours of video across the globe each day. This was a gradual evolution at first, but recent advancements in mobile connectivity have sent us into a climb the likes of which we have never seen before.

Programming is an essential thing in hacking/pentesting, and at times, I do not feel that it is being addressed enough here, at Null-byte. I understand that this is a forum dedicated for hacking, but I'll address some of the stuff I feel is muy importante about programming. I am not a professional programmer, but I do have experience and I do want to share some of the stuff professionals have taught me.

There's a common bug that affects many Samsung Galaxy S5 users, myself included. The software that drives the fingerprint sensor can randomly fail to load, leaving you without one of the most unique features of your beloved smartphone.

Something special is happening. Maybe it's your child's first steps or their walk down the aisle. Maybe it's a hit-and-run accident, a flaming meteorite, or your buddy spilling a drink all over himself. These are fleeting moments that need to be captured instantly.

Tony Stark is a smooth talking, genius billionaire playboy that occasionally saves the world... what's not to like? The Marvel films starring Robert Downey, Jr. have grossed well over a billion dollars in the U.S. alone, so it's needless to say that Iron Man is a very popular superhero.

Welcome back, my hacker wannabees! Most of my recent posts have addressed using Metasploit’s Meterpreter and what we can do once we have embedded it on the victim’s system. This includes remotely installing a keylogger, enabling the webcam, enabling the microphone and recording, disabling the antivirus software, among many other things. The list is almost unlimited.

Cross-dressing and gender-bending are nothing new, but the realm of Steampunk seems to be especially accepting of role-reversal in dress.

Are you feeling like you've got the hang of Google+? Or do you, as I do sometimes, feel like there are just a few too many quirks to keep track of? Here, I've given you 15 quick tips you should know about Google+ so you can maximize the way you want to use it.

Apple has a few exciting surprises for you in its latest iOS 16 and iPadOS 16 software updates. Released on Thursday, May 18, version 16.5 includes new features, bug fixes, and security patches, and there are even hints of some big things coming in future software updates for iPhone and iPad.

As cool as iOS 14 is, it isn't without bugs. One of those bugs in iOS 14.0 just happens to affect one of its coolest features — choosing default browser and mail apps. When you reboot your iPhone, iOS will reset your default apps back to Apple's defaults, Safari and Mail. Not ideal. However, there is a fix that will stop you from having to choose default apps over and over again manually.

Individually addressable LEDs, also commonly called "NeoPixels" after the popular Adafruit product, are a bright and colorful way to get started with basic Python programming. With an inexpensive ESP8266 or ESP32 microcontroller, it's easy to get started programming your own holiday lighting animations on a string of NeoPixels with beginner-friendly MicroPython!

Just like Apple and Google, Facebook has been working to develop computer vision shortcuts designed to give mobile apps augmented reality superpowers.

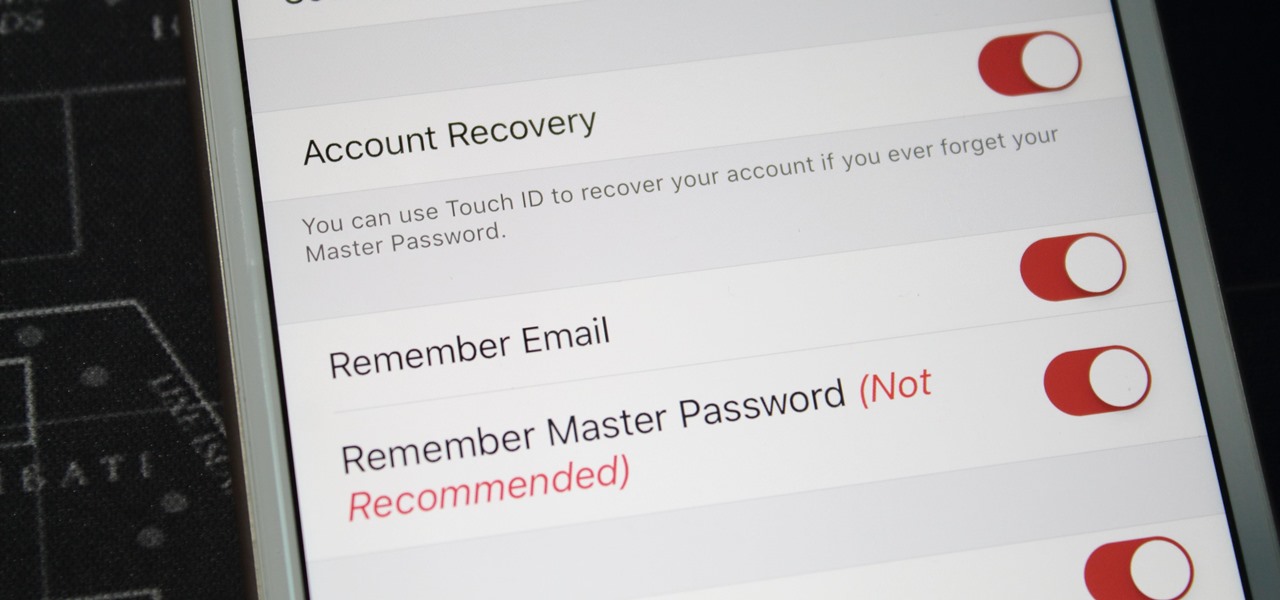
With any password manager, the only password you need to remember is the master password that locks the vault from both hackers and the company. This makes the master password very important. But what happens if you forget this password? Well, LastPass has you covered.

In about 27% of all car crashes, someone was using their cell phone. You may think texting is the big problem here, but many fail to realize that even the smallest smartphone interaction could spell disaster. Thankfully, Google Maps has rolled out an overdue feature that'll help ensure a safer drive.

The last update to iOS 12 featured more emoji, Group FaceTime, eSIM functionality, real-time depth control for new iPhones, and a few other interesting tidbits and fixes. Now, in the latest for iPhones, iOS 12.1.1, Apple brought back a few things that were removed or made more difficult to access in previous updates, and it even has a few new features to offer, albeit small ones.

It wouldn't be iPhone season without a new controversy. Chargegate, Apple's latest PR nightmare, is the name being used for charging issues on some iPhone XS and XS Max devices. If you plug in your iPhone at night — or whenever — then wake up or come back later and see that your iPhone has even less battery power, you're affected. But there is a fix you can implement right now.

In iOS, the Control Center is an easy way to toggle settings such as Wi-Fi, Do Not Disturb, and Low Power Mode. Its Android counterpart is called "Quick Settings," which provides much of the same functionality with a few bonuses. If you're curious about how this toggle menu works or miss having it before you made the switch from Android, you can test it out on your iPhone right now.

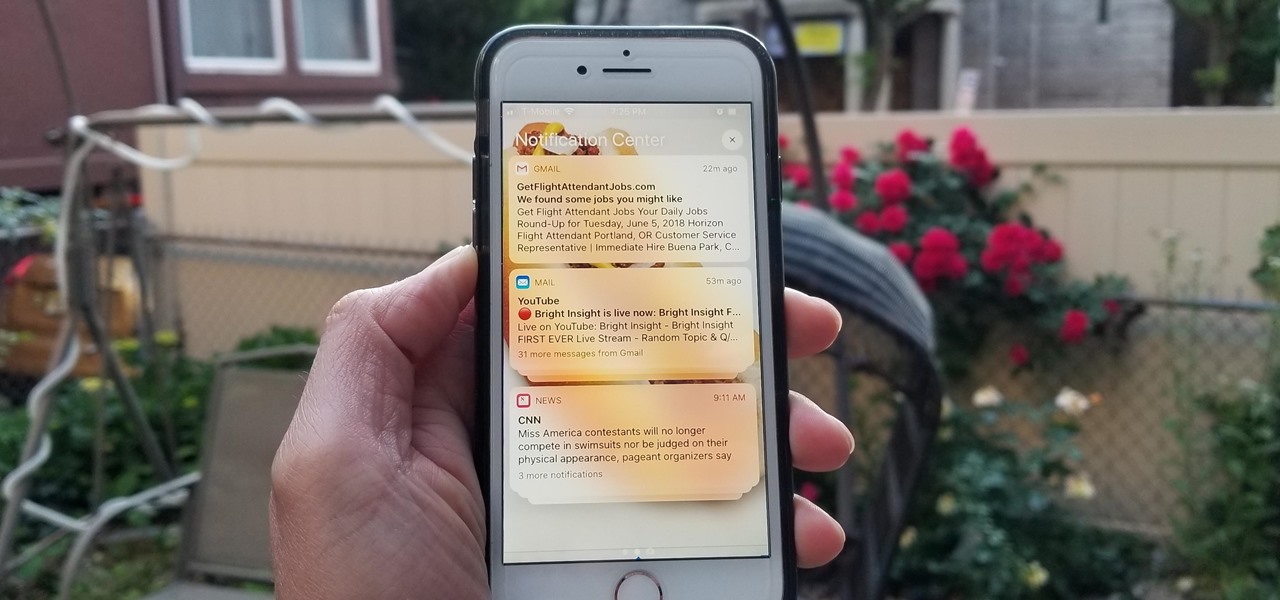
Apple's linear Notification Center has been scattershot at best since iOS 9 when we could group notifications by app. Without any type of grouping ability, the notification history becomes more of a nuisance of random alerts based on time alone, making it a treasure hunt to find the notification wanted. Now, iOS 12 has addressed this issue, bringing back groupings — with improvements.

The default Camera app got a few more tricks up its sleeves when iOS 11 was released, and the best addition by far was the inclusion of a built-in QR code reader since that meant no more third-party apps just for QR code scanning. However, Apple's built-in QR code scanner did have a vulnerability at one point that would let hackers direct you to a compromised website without you even noticing it.

Getting an insider view of the goings-on at Magic Leap is hard to come by, but occasionally, the company lets one of its leaders offer a peek at what's happening at the famously secretive augmented reality startup. One of those opportunities came up a few days ago when Magic Leap's chief futurist and science fiction novelist, Neal Stephenson, sat for an extended interview at the MIT Media Lab.

Samsung has legions of loyal fans, and for good reason — their Galaxy S lineup ticks so many boxes that it would be a downgrade to switch to any other phone. Though if you're still rocking an older model like the Galaxy S7 Edge, the all-new Galaxy S9 can tick all the same boxes plus a few more. But is it worth the money to upgrade at this point? That's actually a tougher call than you might think.

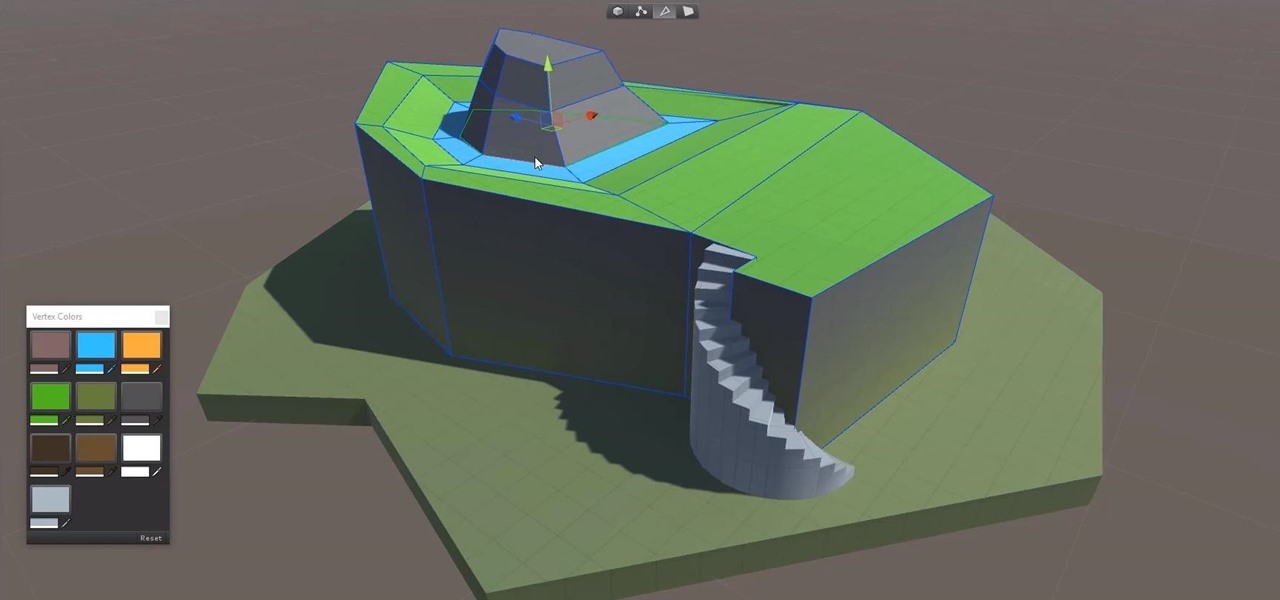
Continuing to take the steps necessary to reign supreme among the top game engines of the world, with a steady stream of major updates, enhancements, and new features, the team at Unity are keeping the user base in a regular state of surprise. At this rate, it's almost like Christmas every few days.

Facing claims of misappropriation of trade secrets and confidential information by Meta Company, DreamWorld, led by Meta's former employee, Zhangyi "Kevin" Zhong, has fired back with a motion to dismiss the lawsuit.

Japan is in the process of curbing its aging population and mature workforce. According to The Diplomat, the country's population has been declining at a steady rate. To meet future productivity demands in commercial and industrial sectors, local officials are turning to self-driving technology, including truck platooning, where three or five vehicles travel autonomously in a string formation. This practice, according to a study by MIT, can reduce fuel consumption by up to 20% (more about thi...

The future of augmented and mixed reality offers many possibilities, mostly because we're still figuring out everything it can do. While Meta is open to exploration, they've spent a lot of time thinking about what the future of this technology will be.

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

Welcome back! In the last training session we covered how to write and execute scripts. But today we'll be getting back to the code!

Welcome back everyone. As many of you know, reconnaissance is extremely important in any successful hack. Without proper reconnaissance, we won't know what we're about to get into, literally.

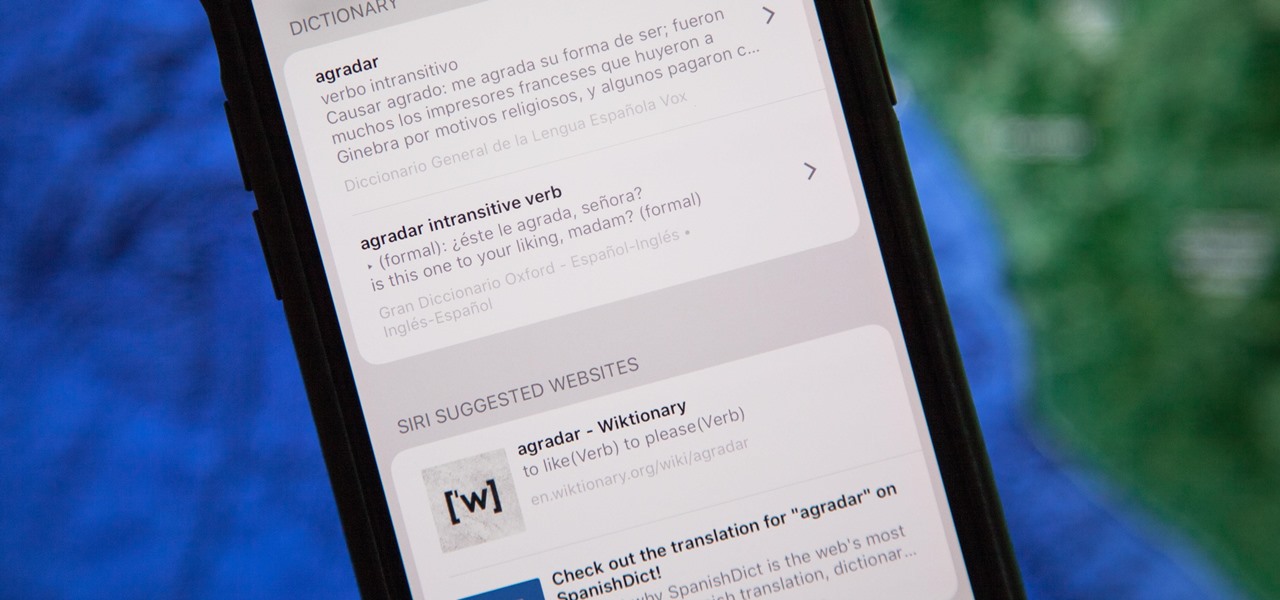
The native dictionaries in iOS, which have been around since 2011, let you define words on your iPhone on the fly in Safari, News, Notes, and other apps. But if you read or write in more than just English, you won't be able to see accurate definitions unless you add those other languages to your list of dictionaries manually.

Hello there, reader! If you've clicked on this How-to then it means you are interested in learning some C programming or just generally curious about what this page has to offer. And so I welcome you warmly to the first of many C tutorials!

Winter and the winter holidays in general are a time of joy, laughter, and love… but not for everyone. For some, the stress of preparing for parties, hosting family, traveling long distances in bad weather, and just keeping up with your daily routine can start to bring you down.

When attempting to compromise a target, we want as much control as possible over the victim. Metasploit's meterpreter allows us to have immense control over the victim, the only issue is that sometimes we can't land a meterpreter. We may only be able to land a standard shell, but fear not, there is a way to upgrade our shell into the all powerful meterpreter!

Welcome back, my novice hackers! This is the third installment of my Python scripting series. If you haven't read the previous two articles, take some time now to go back and read Part 1 and Part 2 before you proceed here.

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.