The iPhone's autocorrect feature is wonderful and convenient, but it doesn't always work with informal language like profanity. If you've ever used the F-word, there's a good chance you've had your curse words "corrected" to other words that don't ducking make sense. And with the release of iOS 13, swearing in your messages and on social media could get a little harder.
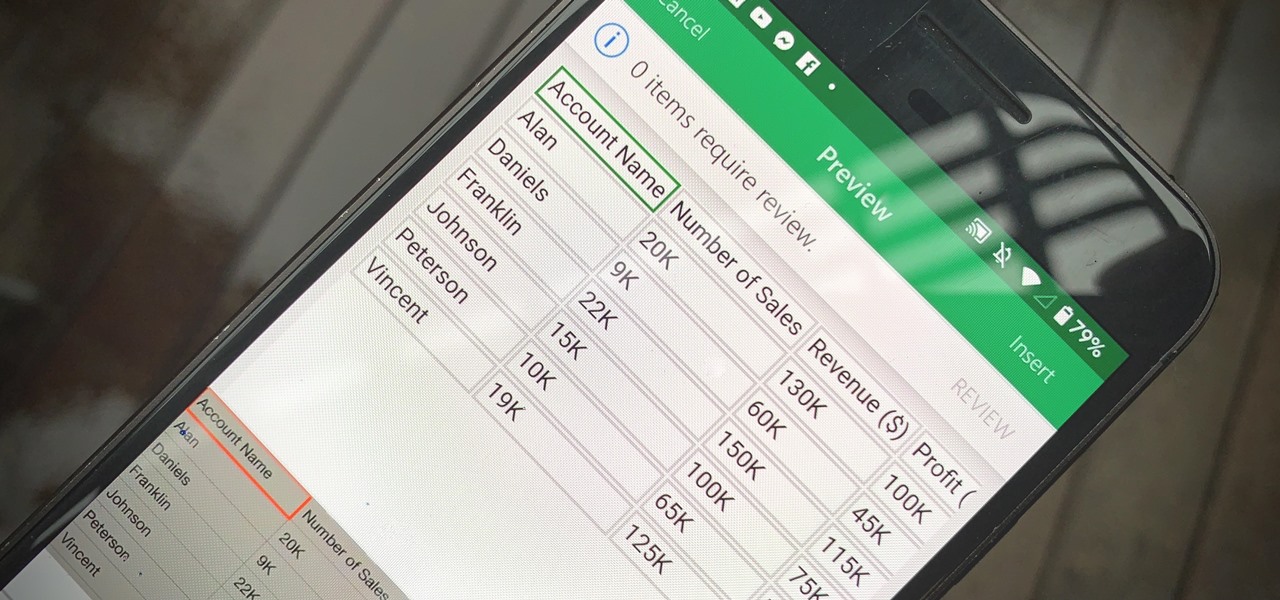
Creating a digital spreadsheet by hand can certainly be tedious, especially if you're copying a printed paper table word for word, number for number. Instead of typing information that's already there, however, use Microsoft Excel on Android or iOS to snap a photo of that printed chart and import it directly into your digital one.

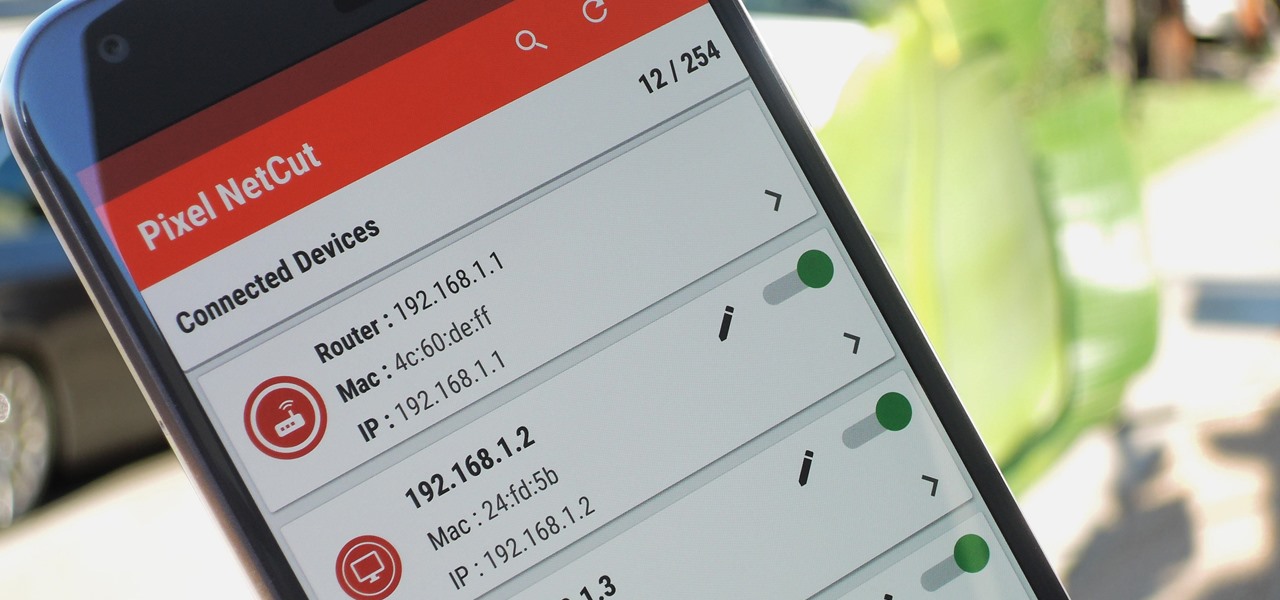
When setting up a Raspberry Pi, it's easy to overlook changing the default password. Like many IoT devices, the Raspberry Pi's default Raspbian operating system installs with a widely-known default password, leaving the device vulnerable to remote access. Using a tool called rpi-hunter, hackers can discover, access, and drop custom payloads on any weak Pi connected to the same network.

In a leaked company memo, Snap CEO (and NR30 member) Evan Spiegel has made it clear that the future of the company lies not only augmented reality but also hardware that enables those AR experiences.

In iOS 12, Apple included new, Snapchat-like effects and stickers for photos and videos in Messages. While these new options are fun, they're missing something that takes away from the appeal, especially since Snapchat, Instagram, Facebook, and similar apps already let you do it.

This year's big iPhone update, iOS 12, aims to solve many of the issues that arose during iOS 11's controversial, buggy tenure. With that in mind, it may be tempting to jump on board the new software immediately and leave iOS 11 in the dust for good. Here are some reasons why you might want to reconsider joining the iOS 12 beta.

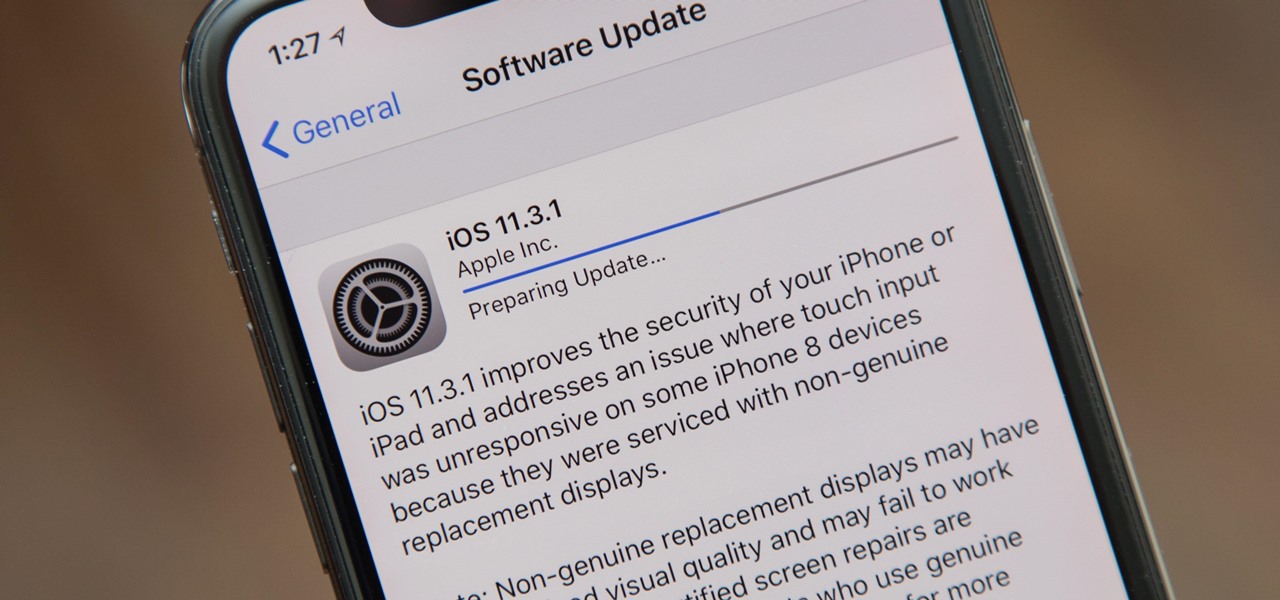
Apple released the iOS 11.3.1 update for iPhones on Tuesday, April 24, 26 days after the official release of iOS 11.3 and eight days after the iOS 11.4 beta 2 update. It is the first minor update to iOS 11.3, and the biggest thing in it is a fix that lets displays fixed by third parties work again.

When most people first become aware of Kodi (formerly known as XBMC), they hear about its ability to stream illegal content. But the real Kodi community knows that it's much more than just a haven for pirated material — it's an all-in-one media player that addresses the majority of home theater needs, particularly for those that decided to cut the cord.

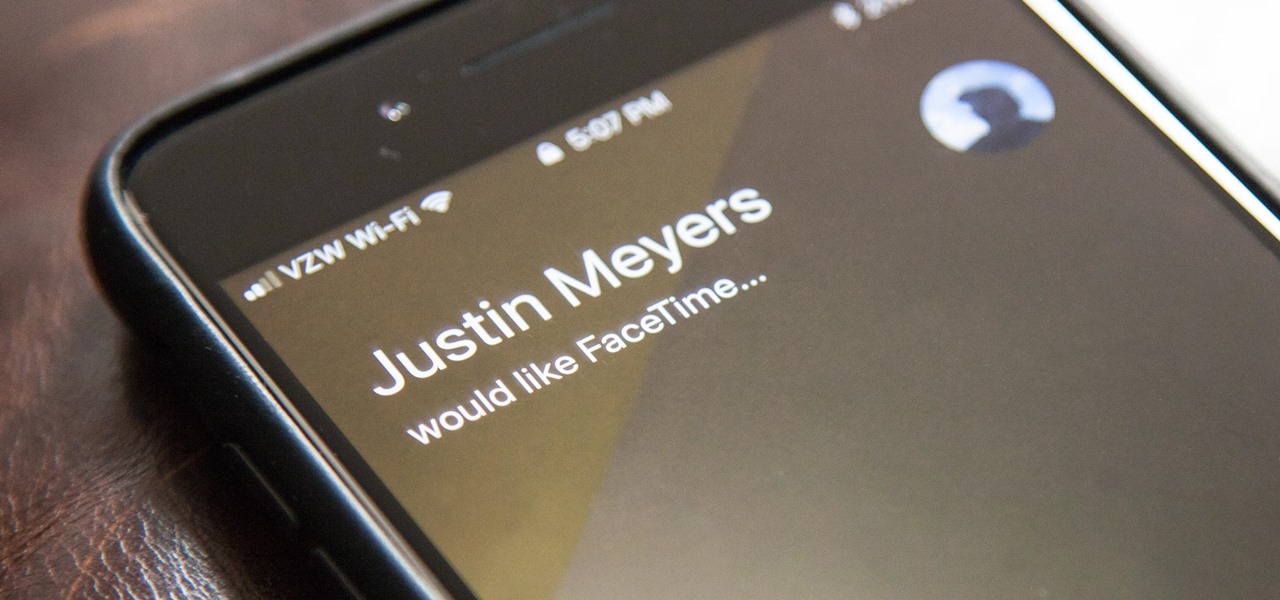
Using either iMessages or FaceTime on the iPhone is a great alternative for coworkers to stay in touch in the event that messaging services like Slack go down. They're also a handy means of communicating between buyers and sellers, as it provides a more intimate way of either checking out or showcasing a product. But you're not always going to want to give out your real number to everyone.

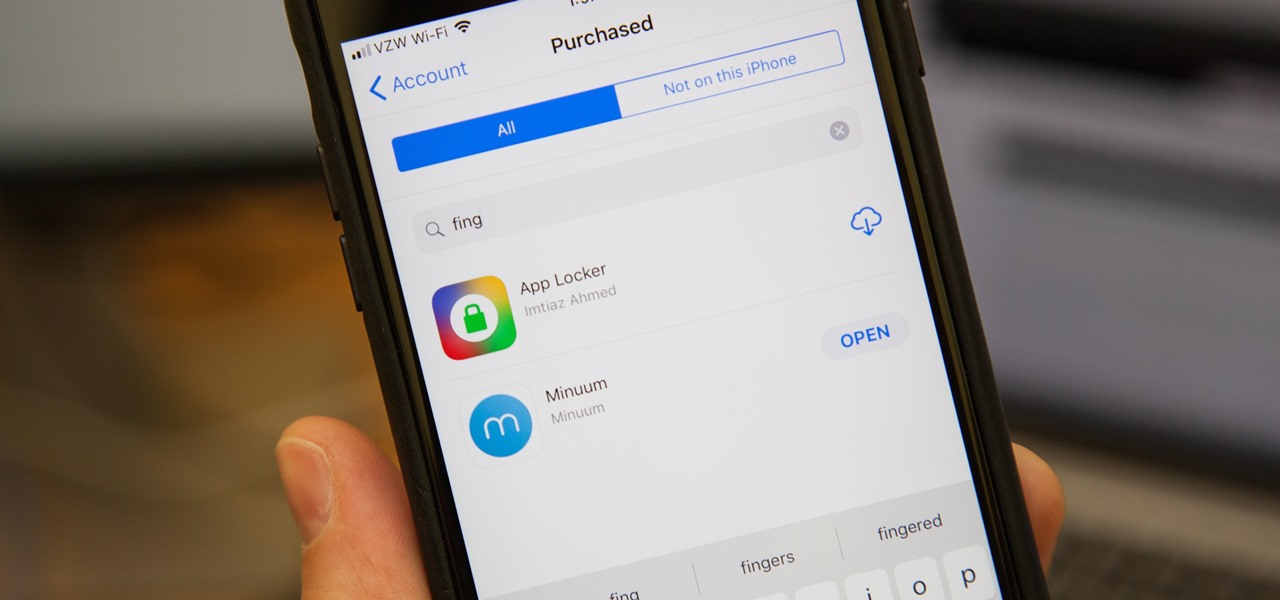
In the new iOS 11, Apple lets you hide purchased apps from the App Store no matter if you have "Family Sharing" turned on or not, which is an interesting change from iOS 10. It's a fairly easy task to hide an app from your list of purchases, but unhiding it is anything but easy.

The Google Assistant comes in several different flavors. There's the baked-in Google app on Android, the dedicated Google Assistant app on iOS, and the Assistant-powered Google Home smart speaker. But no matter how you access it, your Assistant will only get better if you take some time to personalize things.

Whenever you make FaceTime audio or video calls from your iPhone, Apple automatically uses your phone number or Apple ID email address as the caller identification. So when someone that you're calling sees the incoming call, they'll see it's from your phone number or email address. But what if you'd rather it be a different identifier?

It seems like there's a cyber security scare every day. Consumers are growing increasingly concerned about the safety of their accounts, and they have reason to be. Hackers will maliciously attack you anywhere — and we mean anywhere — they can to get your private information.

The first sneak peak of Android O is finally here. The developer preview promises more features, stabilization, and better performance, according to the Android Developers Blog. Furthermore, there's speculation that the latest operating system will be code-named "Android Oreo," so it definitely sounds like we're in for a treat.

Let's say you gave your Wi-Fi password to your neighbor a while back, under the assumption that they'd only use it while they were at your house sharing stuff via Chromecast. But now, your connection is slower than it normally should be, and you have this sneaking suspicion that the dude in apartment 3C is flat-out piggybacking off of your home network.

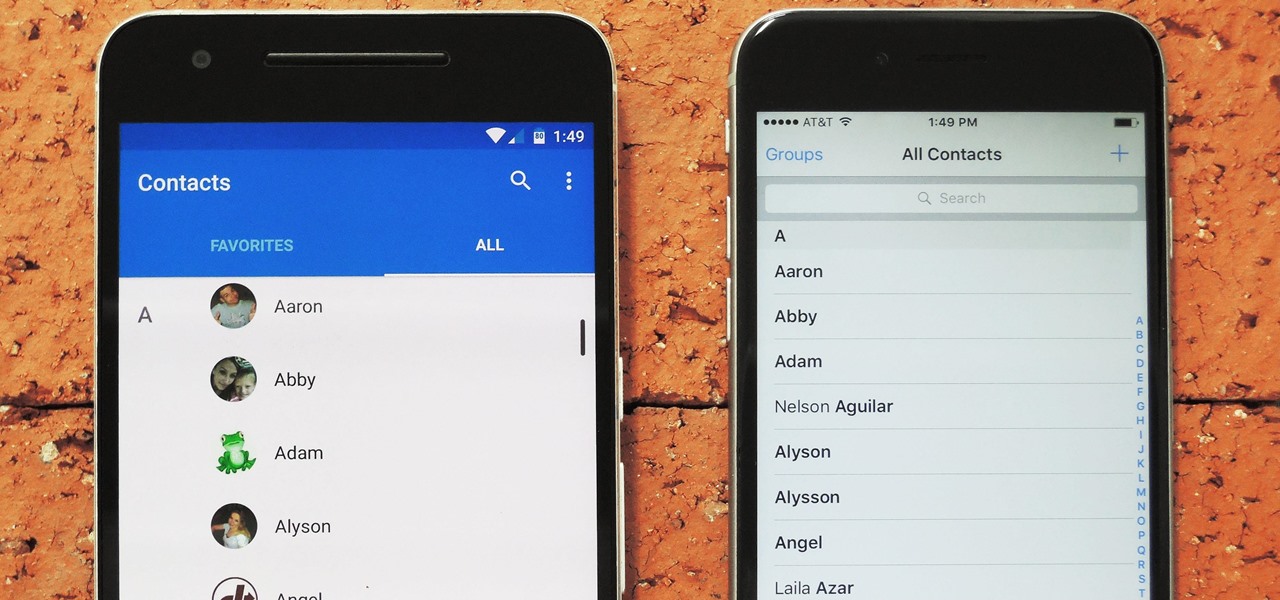
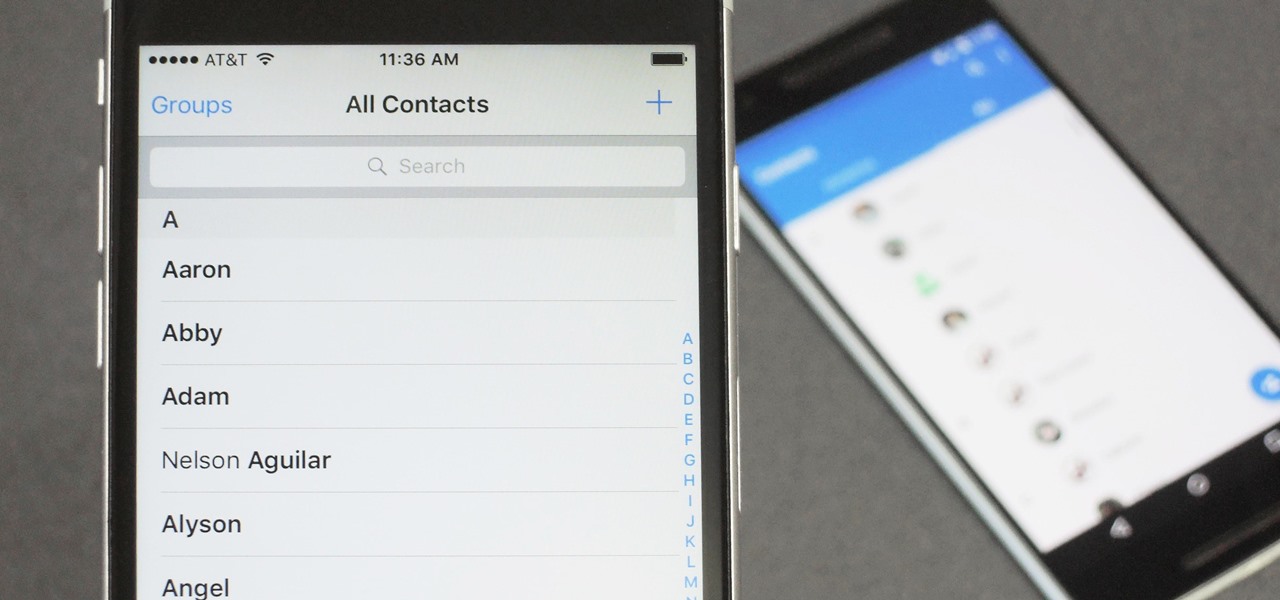
Switching between mobile operating systems is fairly easy, but there are a few bumps along the way that you're bound to encounter. One of the first issues you'll run into is that the contacts on your old iPhone don't easily sync with your new Android device.

When you change smartphone ecosystems, there are a lot of minor hurdles to clear along the way. It's definitely not hard to switch from Android to iOS, but little things like making sure your contacts get transferred over can take a bit of work.

Android's personal assistant is more than just a sassy backtalker—it's a full-on suite of all the information you could need at a given time. Google Now, as it's called, uses data from various sources to predict what you'll want to know before you even search for it, and it's an amazing experience once you've got everything set up.

continuing this series, I will now go in-depth on using advanced search queries. What Is Search Queries Again?

In the last tutorial, we learned how to make functions and how they work on the high level. This time, we will take a peek under the hood again, stare deep into its soul and see its ugliness face to face to see how it works in the lower level.

Microsoft's "Fall Update" to Windows 10, code named Threshold 2, has a lot of new tricks up its sleeve. It's the biggest update we've seen since Windows 10 was released this summer, and it's rolling out to all users right now.

In my last how-to, we built a man-in-the-middle tool. The aforementioned script only established a man-in-the-middle. Today we'll be building a tool to utilize it. We'll be building a DNS packet sniffer. In a nutshell, this listens for DNS queries from the victim and shows them to us. This allows us to track the victims activity and perform some useful recon.

Let's say that we want to see what someone is doing on their computer? In this tutorial, we'll be hijacking cookie sessions to do just that!

Now that we have our vulnerable server, it's time to start up BeEF. Getting Started

The only mail I like getting comes in the form of an Amazon package, but when I go to my mailbox, it always ends up being a pile of credit card offers and catalogs I could never see myself ordering from. Those pieces of junk mail usually end up in the trash, which is horrible when you think about all the trees that had to get cut down in order to produce them.

Contacts on your phone can be messy. Keeping all of those numbers, emails, and addresses organized takes time and, even then, they still may not be be as accessible as you want them to be.

Welcome back, my nascent hackers!

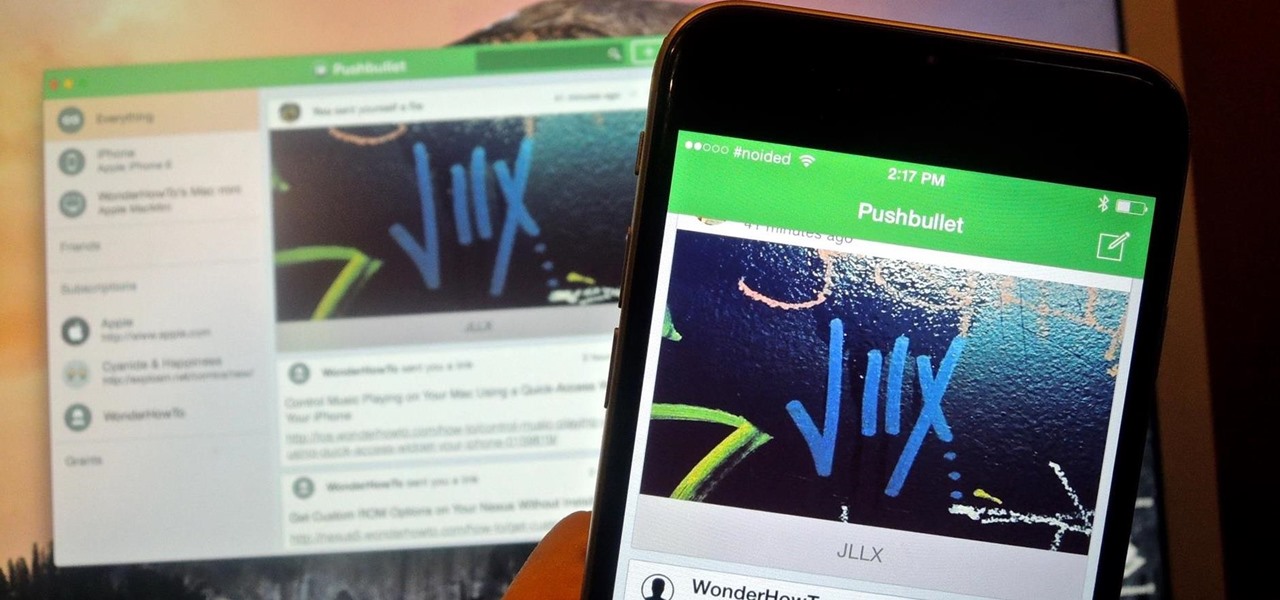
With Apple's Yosemite build of Mac OS X came Continuity, a feature that has allowed us to connect our mobile devices to our computers, letting us access apps, send text messages, answer phone calls, and more while seamlessly switching from one device to the other.

Ah, the age-old problem of sharing pictures with friends and family. Ten years ago, the best method available to us was passing around duplicate photos printed out at the local drug store. As easy as smartphones have made this act, you'd think we'd be satisfied by now.

While we now know that iCloud was not exploited by hackers to steal private celebrity photos, Apple did admit that guessed (aka brute-forced) passwords and/or iCloud security questions were to blame for the breach.

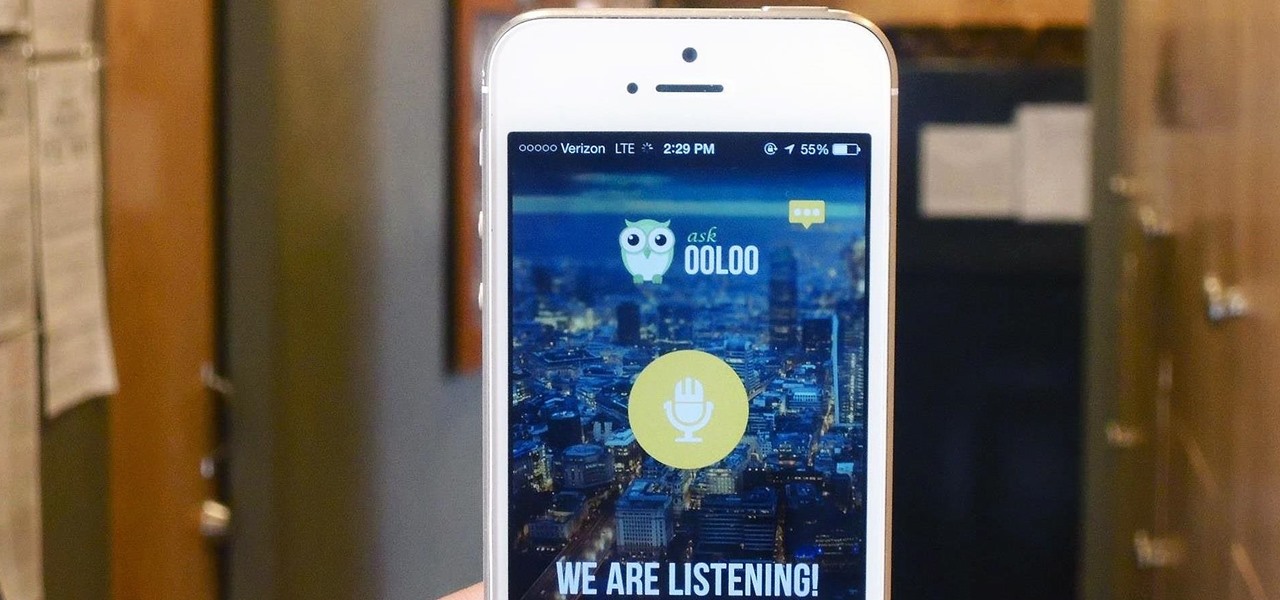
Apple has Siri, Google has its Now service, and Microsoft has Cortana. All of these voice-activated services can bring you information quickly and easily without having to type anything into your smartphone. Speak and within seconds you're provided with either an answer or somewhere you can find it.

Welcome back, my greenhorn hackers! Although we have focused primarily on technical hacks here, social engineering can sometimes be especially effective. This one requires a bit of technical skill, but not too much. In addition, it's limited by how specific a target you can choose—but it will work.

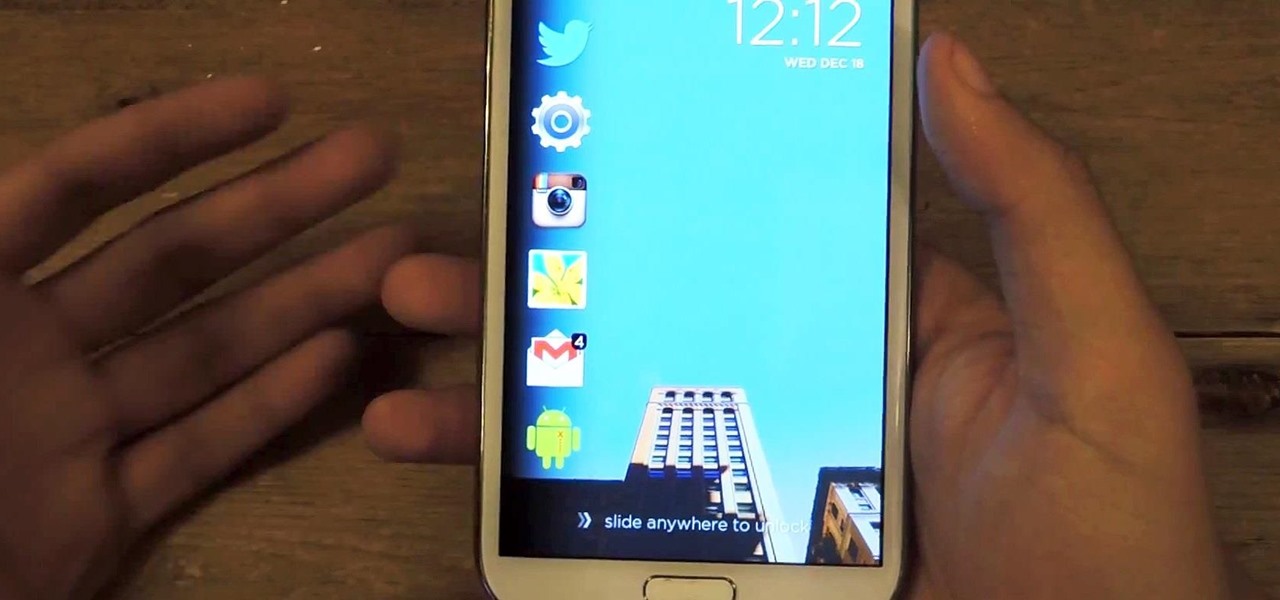
Not particularly good looking, TouchWiz's lock screen adequately supplements the clunky and almost cartoonish-look of the infamous user interface on the Samsung Galaxy Note 2. While there are hundreds of lock screen options in the Google Play Store, I've never quite discovered one that I've thoroughly enjoyed, due to the obfuscation from so many options.

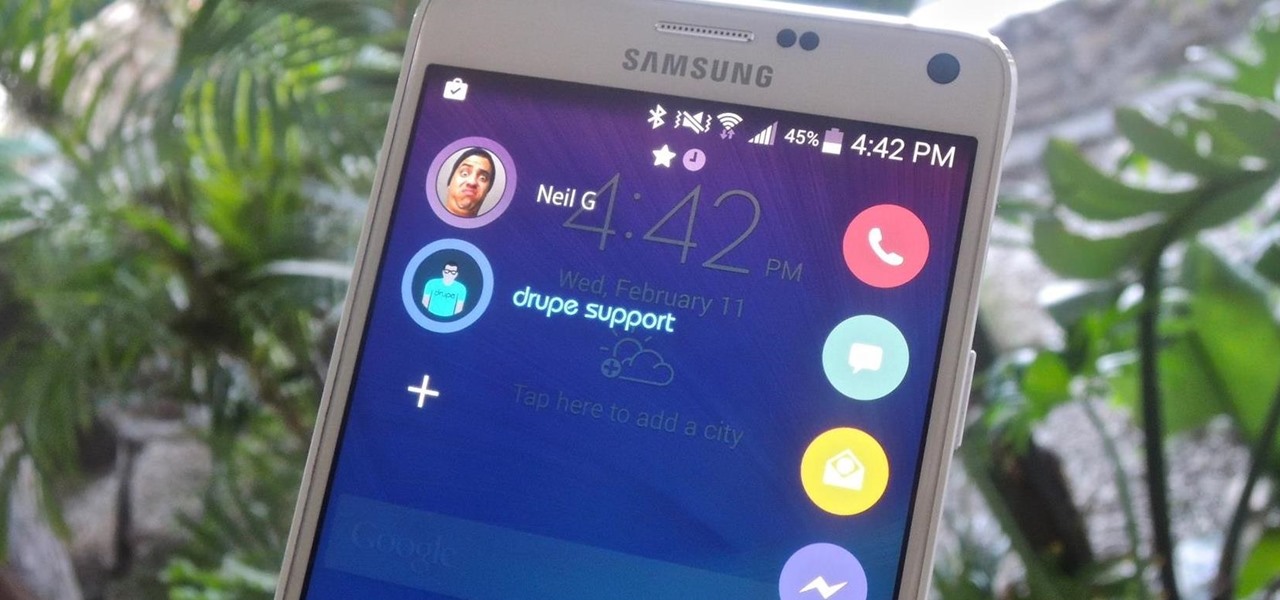
There are some calls you really don't want to miss. Whether it's "I'm going into labor" or "We have some questions about your résumé," not being able to answer or respond to certain messages can cause some serious problems.

According to a new study, the majority of smartphone users check their devices 150 times a day. While that number may seem incredibly high at first glance, the influx of notifications and amount of social media apps available reduce the initial shock and make the number seem not so preposterous after all. Yeah, even on a date.

Welcome back, my newbie hackers! Hackers often are associated with clandestine and illegal activity, but that is not necessarily always the case. Hackers are increasingly being used and employed for law enforcement, national security, and other legitimate purposes. In this installment, we will look at how a single hacker could save the world from nuclear annihilation.

If you have a Samsung Galaxy S3 or Galaxy Note 2, you might not have noticed it yet, but there's an annoying little bug that centers around your clipboard. If you tend to do a lot of copy/pasting on your device, you've probably seen it happen—your phone crashes.

It's no secret that there's a lot of surveillance going on these days. It's easier than ever to end up in a database, and even former government agents are speaking out about the atrocious amount of spying being done against our own citizens. They've targeted our laptops, cars, IP addresses, and now they're coming for our iPhones. AntiSec hackers managed to get their hands on a list of over 12 million Apple UDIDs (Universal Device IDs) from an FBI computer, and they published 1,000,001 of the...

First off, I would like to say two things. One, this is not for beginners; if you don't feel that you understand this how-to at all, do not try it. Second, never ever install random software or change settings if you do not trust the source.

Want the convenience of a throwaway email address without all the hassle? How about anonymous text messaging so you can get to know someone before giving them your real information? Gliph has you covered. Gliph is a service that lets you create an identity around a set of three to five symbols called "artifacts" instead of your name, phone number, or email address. You choose how much information you reveal, and anytime you communicate with someone else who has Gliph, the data is protected us...