In this video tutorial, you'll learn how to use three Ettercap plugins useful in penetration, or pen-testing. Specifically, this video tutorial addresses the find_ip, gw_discover, and isolate plug-ins. For more information for using the Ettercap plug-ins, take a look. Use Ettercap plug-ins for penetration, or pen, testing.

In this video the instructor shows how to allow email from people you know and block emails from all other users in AOL 9.0 for Windows. To do this, first open your AOL mail box. Go to the Mail Options menu and select the option "Block Unwanted Mail". This pops up an "AOL Unlimited Use Area" screen. You have to select "Yes" to proceed. This opens the Mail and Spam controls window. Now scroll down in the window till you find an "Additional Spam Filters" heading. Now there is a Select Filter ov...

A press release should be about news. It should have a sense of urgency about it and grab the reader’s attention from the outset. A good press release must quickly answer the journalist’s immediate questions:

Before you start snapping away and submitting your photos, please take some time to read the official rules below!

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.
In a bombshell revelation of the depth of the food police state that now exists in LA County, California, NaturalNews has learned that the LA County health department has unleashed door-to-door raw milk confiscation teams to threaten and intimidate raw dairy customers into surrendering raw milk products they legally purchased and own.

Though it's unlikely you'll ever have a need for hostage survival skills, it never hurts to take in a few tips on what to do in the event of being accosted by Somali pirates off the Horn of Africa. Wired has tracked down a HowTo guide that addresses such a scenario. Though most of the advice is fairly general, one important point addresses the dangers of lighting up with the enemy:

There have been a few recent developments in Los Angeles that only highlight how dysfunctional the city is when it comes to encouraging their citizens to develop greener habits.

Often times when staying at a hotel or anywhere for that matter, you'll whip out your laptop and check the local area for Wi-Fi. I know you've all been in my shoes when you find an unsecured network that appears to be public Wi-Fi belonging to the hotel or airport, and you connect to it. You connect fast and perfectly, only to find that when you open your browser, it says you don't have an account, and are filtered from accessing the web. This is because the owners of the network want to keep...

Where To?, the well-known points of interest finder for iPhone, has been updated to a new version including an Augmented Reality view.

Wireless networks. Nowadays, everyone uses 'em, but most don't secure 'em. On average, I can drive up and down any block in my city and find at least one or two open or semi-open networks on any given day. With some changed MAC addresses for good measure, an attacker can use your network as a spring board for who knows what. When the police come a few days after, they are coming to your door—and not to talk about how nice your lawn is. Don't be that guy.
Unless you avoid the news entirely, you've almost certainly heard about the hacking sprees that have been taking place over the past several weeks. Tens of thousands of usernames, passwords and email addresses have been released online for anyone to download. Thankfully, it seems that one kind soul has put all that compromised info to good use.
A few years back, I wrote an article, in fact mostly to my family and friends, titled "The Evil Power of To:". I was referring to all the folks sending emails out willy-nilly to all their friends with no regard for whether or not you or I would want our email addresses boldly displayed on the "To:" line of an email. This article very pointedly explains what BCC: is and WHY you should always use it when sending out emails to more than one person. Check it out!

Wondering why your inbox is looking a little threadbare? It may be that you've violated a few unwritten rules of email etiquette. Here are a few basic tips that the web-savvy know by heart.

In this video tutorial series, you'll find instructions for using the UCSC Genome Browser. More specifically, this video addresses (1) getting DNA sequences, (2) using annotation tracks, (3) locating intron-exon boundaries, and (4) searching with BLAT. For further detail about any or all of the above topics, and to get started using the UCSC Genome Browser yourself, take a look! Use the UCSC Genome Browser - Part 1 of 4.

If you follow the Anonymous, Occupy, and IT security scenes, you have no doubt heard about a dox release. What is it? How can it hurt you? And most importantly, how can you protect yourself from it? Some of these steps might seem common sense, while others will be an ah-ha! moment. Your private info is both your biggest weakness and your biggest weapon in your battle to remain anonymous. You must learn how to use it as both.

If you've gained entry into Google+, one of the first things you should do is adjust your Google account settings. Your settings will now look quite different, and you can adjust your notifications, password retrieval methods, and more. There are many settings that you may not have been aware of before.

Have you ever been away from home or on holiday and noticed an open network connection? FREE INTERNET! But then you find out that every search or page redirects you to an "enter password" or "signup here" page. Well, there are ways around this.

OpenVPN is the open-source VPN (Virtual Private Network) client, used over the PPTP (Point to Point Tunneling Protocol). It allows you to connect to a remote network over a secure, encrypted connection and mask your IP addresses over all ports. Since there is only one "hop," the network speeds are barely effected and are far more secure.

Have an HTC smartphone? Chances are that some of your stored personal data has been hijacked by malicious apps on your device. Android apps that have permission to access the Internet, which is pretty much every ad-supported app out there, can snag valuable information such as email addresses, location history, phone logs, text messages, and more.

One of the biggest complaints people had about Google+ was comments on popular people's posts taking over their streams. Today Google addresses those issues by rolling out the ability to collapse and expand comments. +Jonathan Terleski explains the simplicity of the function - click once to expand, click again to collapse. Check out how the collapsed comments work in the screenshots below. It's as simple as clicking an arrow.

Security awareness seems to be a hot topic these days on the web, with developers making apps and devices that can hack networks and machines with just a few clicks. But these applications aren't only exploiting security flaws in systems and networks, they're being used by amateur and wannabe hackers who want to have a little fun, but don't want to learn how to actually "hack" anything.

On the same day that Google launched their new social network, Google +, a team of Google engineers calling themselves the Data Liberation Front announced their first service on Tuesday—Google Takeout, a product that allows users to easily move their data in and out of Google products, including Buzz, Contacts and Circles, Picasa Web Albums, Profile and Stream (the equivalent of Facebook’s newsfeed).

Remember Grindhouse, the Quentin Tarantino & Robert Rodriguez homage to B films? Well this game is just like that. It could literally pass off as the third feature in that movie. The action looks clunky, the acting is not the best, but it still looks like a fun ride. It comes out tomorrow (June 21st) and I'll have first impressions ready the next day.

For the hefty price of $200 and up, you can be the proud owner of the world's first 3D printed bikini. And not just the first bikini, but reportedly the first functional and affordable item of ready-to-wear 3D printed clothing on the market. Created by Continuum Fashion, the N12 3D printed bikini is revolutionary because it addresses the technical challenge of creating flexible "textiles" with 3D printed material. The bikini is made of a material called Nylon 12, which is entirely waterproof.

E Ink technology is nothing short of amazing. It recently contributed to the world's first bend-sensitive flexible smartphone, and now it's capable of something even cooler, not to mention astonishingly simpler—flashing digital displays on cloth.

Know the saying, "The inmates are running the asylum"? Well, if the inmates actually were running the asylum, we imagine the asylum might look something like this!

There are endless possibilities for eReaders, and lots of amazing things are already happening. But wow-worthy visual tricks aside, how can technology really change the way we consume books? In the video below design company IDEO presents three separate concepts for virtual consumption: Nelson, Coupland and Alice. IDEO groups their virtual experiences into three separate concepts: Nelson, Coupland and Alice. Core77 breaks down each concept:

Facebook games have become a worldwide, web-wide addiction. Just take a look at all the tutorials on WonderHowTo alone. For most of us it's just fun and games (literally), but some have an addiction that merits the attention of the (perhaps officious) Dr. Phil. In a recent episode, Trends for 2010: The Good, the Bad, and the Ugly, Dr. Phil takes on a mother with a serious Farmville addiction.

Wouldn't it be nice to just sit at your buddy's house, plug into his network, and see exactly what he's doing? What if it was as easy as that? What makes packet sniffers like Wireshark such potent tools is that a majority of local area networks (LANs) are based on the shared Ethernet notion.

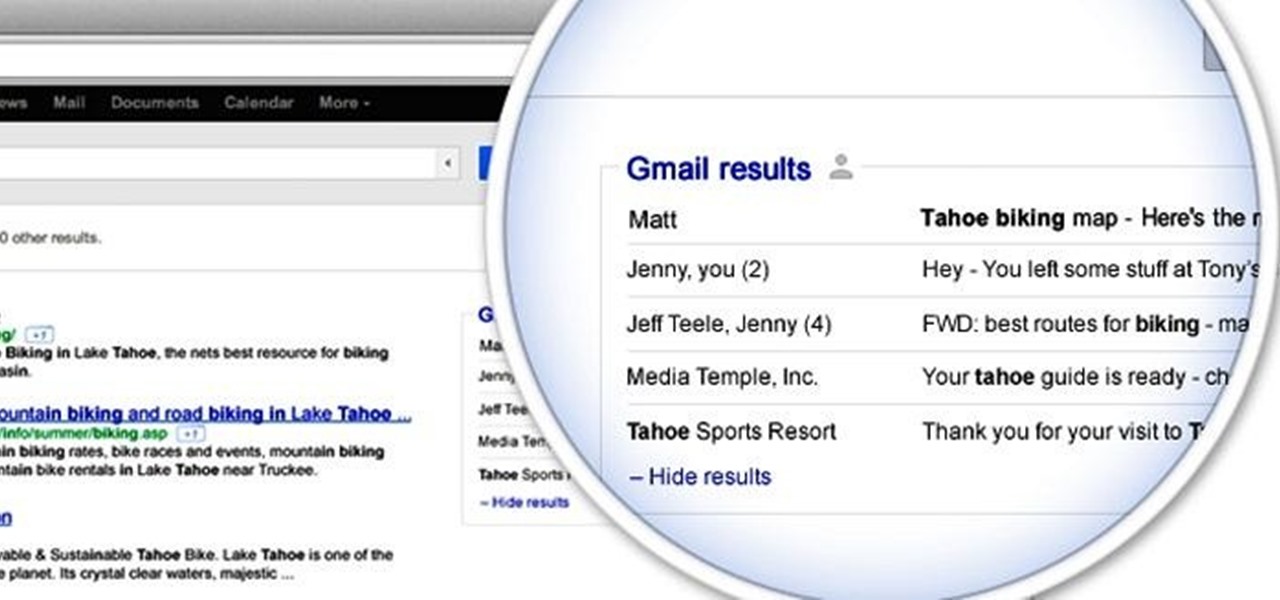
Google is rolling out a new feature that will integrate your Gmail account with Google searches. The feature will add results pulled from your email correspondences to create more "personalized" Google search results. Google is currently doing a test run of the service. To activate it for your account, head on over to this page to sign up. It's currently restricted to the English version of the site, and for those with @gmail.com email addresses (not available on Google Apps accounts). And be...

When you really think about it, registering for any website is a little scary. Not only do they now have your name, email address, and a username/password combination you might've used elsewhere, but certain sites and services ask for quite a bit more private information. From phone numbers to addresses to birth dates and more, that company now has all of your information stored.

Here's a delicious Byte of information for you. A proof of concept program on Linux was coded to exploit a known bug in how the Linux Kernel (versions 2.6.39+) handles permissions for the

Watch out Instagram, there's a new free, sociable photography filter app that hit the iTunes App Store recently, and it just might be some good competition. It's called PicYou and might sound familiar to some of you photo sharing fiends out there. That's because it's been a successful web-based alternative to Instagram for about six months now.

Social networks like Facebook and Google+ are great for staying connected with family, friends and coworkers—even fans. But sharing and communicating with practically anyone in the digital realm has alienated us from most of the flesh-and-blood beings we see everyday—our neighbors. How well do you know your neighbors?

You may not know him by name, but Eric Leebow is the man we can all thank for inventing social networking. At least, that's what he thinks.

Children under the age of 13 possess insight that can blow the minds of their elders, but not the wherewithal to make important life choices for themselves. This is exactly why there are strict rules against marketing cigarettes to them. In 2000, a law went into effect called the Children's Online Privacy Protection Act that institutes similar consumer protections for our youth's online identities, prohibiting companies from soliciting personal information from children under 13 years of age ...

Six months ago, 1.3 million registered users of Gawker Media had their passwords compromised when the site was hacked by Gnosis. The passwords were encrypted, but 188,279 of them were decoded and made publicly available for all to see. Just three weeks ago, Sony Pictures was hacked by LulzSec, with 1 million passwords taken and 40,000 made publicly available. Comparing the two data sets, Troy Hunt found 88 accounts on both sites that used the same email address, and of those accounts, 67% use...

In a recent survey of more than 5000 UK jobseekers by TotalJobs.com, it was found that 60% spend less than two hours working on each application following a job search, all inclusive of the time it takes to write a CV and covering letter, and to prepare for an interview.

If you've read my darknet series, you've probably got a pretty good idea of what I2P actually is and is capable of. One of the features of I2P is that it's designed with P2P file sharing in mind. Using a built-in service called I2PSnark, you can host and seed torrents quickly and easily!