
How To: Load a quilt onto a frame
Need to load a quilt onto a frame but aren't sure how to do it? This ten-minute free video quilting lesson, which breaks the process down into its simple steps, will remedy that situation post haste.


Need to load a quilt onto a frame but aren't sure how to do it? This ten-minute free video quilting lesson, which breaks the process down into its simple steps, will remedy that situation post haste.
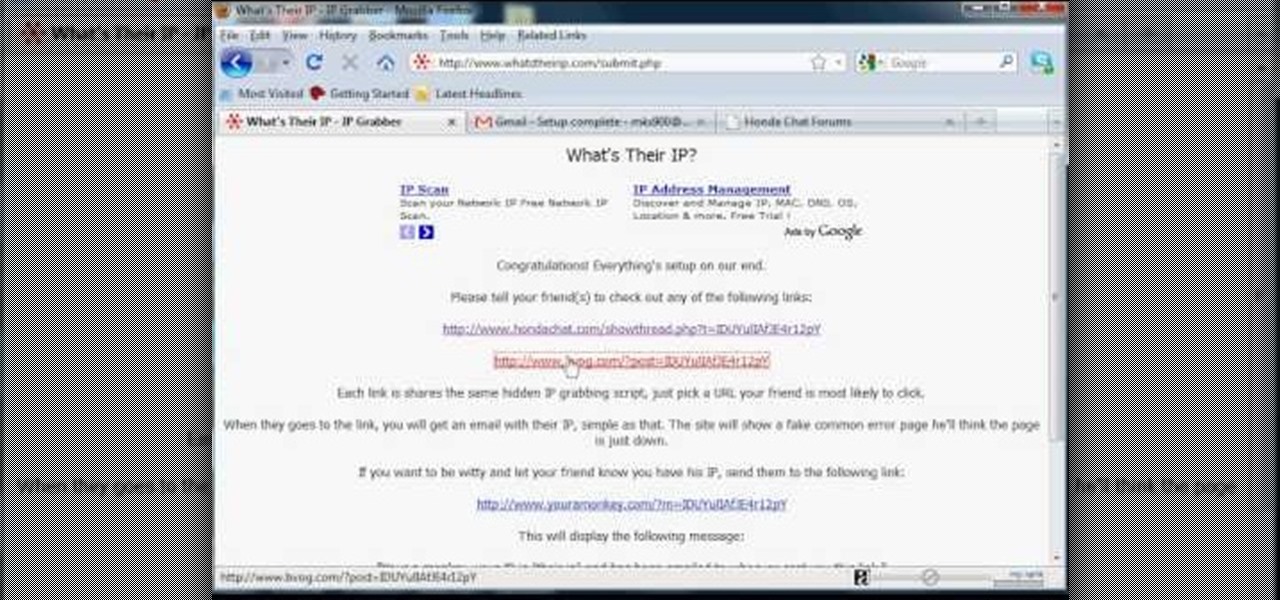
In this tutorial, we learn how to find someone's IP address. First, log into What's their IP. Once you open this, enter your email and click the links that can be sent to your friends. Once they click on these links, the website will email you that person's IP address. You can now look this IP up to see the exact location of that person. There are several different options of pages that can be sent to your friends if you want to track their IP addresses. There is also a page that can be sent ...
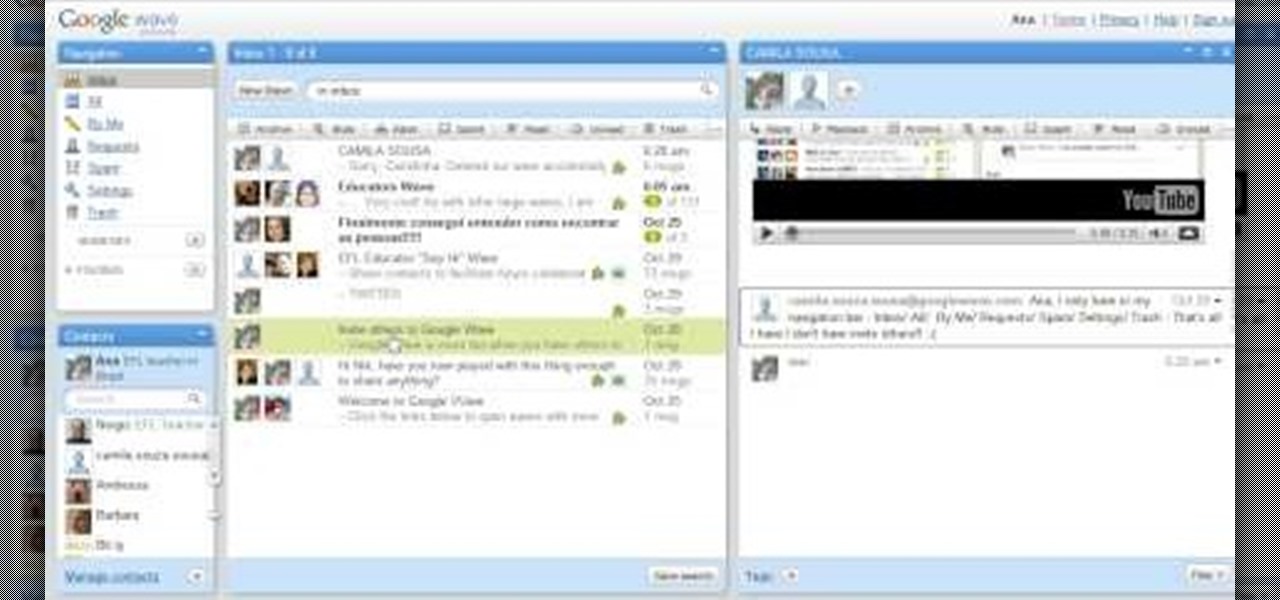
In order to send invitations to other people via email to Google wave do the following: Go to your inbox then look for a wave that says "invite other to Google Wave" then insert the person's email list that you wish to send invitations to for the Google Wave. When entering the email addresses the bottom of the page should have a list of people that you have already invited to Google Wave. You will not be able to resend invites to people if they were already sent an invite. Please follow the d...

This video shows you how to tune your guitar, for beginners. A step by step video tutorial for beginner guitar players that will teach you everything you need to know to tune your guitar properly. Andrew Wasson responds to viewers request to make a video for beginners that will properly teach them the steps to guitar tuning. Andrew addresses the fact that many similar videos about tuning completely skip the topic of "intervals". He explains with simple instructions how to tune your guitar to ...

In this video tutorial, viewers learn how to hack the Flash game "Defend Your Honor" using Cheat Engine. Users will need Cheat Engine version 5.5. Begin by starting the first level of the game. Open Cheat Engine, click on the computer icon and select the internet icon. In the game, start a battle and kill an enemy. Type in the money you receive in the Cheat Engine "Value" bar. Continue doing until there is one or two addresses in Cheat Engine. Then, check both boxes and change the value to nu...

Schoolteacher looks into choosing your career path. Helping students and people first looking for jobs, in discovering their best suited career path.
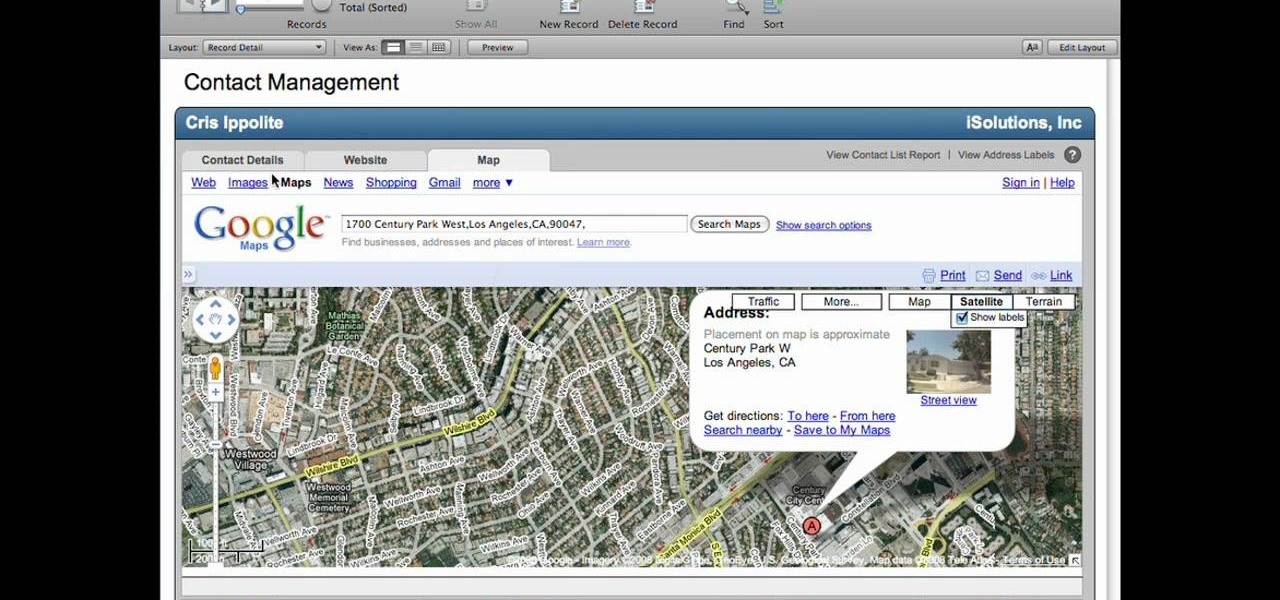
Lyndapodcast teaches you how to create a database using FileMaker Pro 10. You can link one contact with multiple addresses and information and store that into a single database. You can also add content from the web into your FileMaker layout, including maps, pictures and music. You have a security module where you can set permissions for the users using the database. You can also publish the FileMaker database to the web. For this go to File - Sharing - Instant Web Publishing. Another featur...
The video provides you two easy ways to get onto MySpace at school. There is no need to install anything at all. If you have a Windows operation system, open a command prompt window and just ping MySpace. Then copy and paste the IP addresses you found directly into your browser's address bar. In case you have a Mac computer, try search 'ip address finder' on Google and tool sites such as ip-address.com can help you find the same information. Now getting onto your favorite MySpace will never b...

Gourmet Magazine's food editor Lillian Chou introduces cooking enthusiasts to a little-known method to peeling a ginger. She addresses the problem of cooks taking too much of the ginger off with the skin when peeling with a knife. To reduce this wasteful practice and get dependable results every time, she encourages the use of a spoon! This simple tool can take the skin (and only the skin!) off ginger without any hassle. It also is apparently very good at getting the hard-to-peel spots on gin...

This is a great video with a response from "AskDanandJennifer.com" dealing with one of the most challenging topics, how to overcome shyness and ask a girl out. The video is really helpful because it offers what to do and what NOT to do strategies. It also provides feedback from a guy and a girl's point of view, which is also helpful. The bottom line is all shyness in this area comes from a fear of rejection and this video addresses that right up front in an informative and helpful way.

Do the polynomials, or "giant fractions" in your high school math homework have you puzzled? Let Doug Simms, an expert tutor from free math tutoring, walk you through some easy to follow chalkboard examples. He addresses common snags and challenges in the equation simplification process, as well as some great advice about the kinds of problems that you are likely to see on your math exams. There is no reason to go it alone when Doug Simms is waiting to help you in this free video!

With the world being obsessed with obesity; where does that leave the polar opposite? Malnutrition should be equally important. In this video from the Youth Health Alliance, the concerns of the under weight person are addressed. After watching, you'll have a basic understanding of what is required to gain weight in a healthy way. It addresses the consequences of being underweight. It also describes both diet and exercise for healthy weight gain. It explains which calories are healthy to consu...
You want to use the websites you want to use, regardless of any school blocks or other hindrances, so how? This video tells us by using the IP addresses of your favorite sites. To find this IP address, at your home, or an other unblocked location, in your start menu, you must access Programs, then Accessories, then Command Prompt. When the window pops up, then type in "Ping http://www.myspace.com" without the quotations, for instance. Write down, then, the string of numbers that appears, whic...

Youtube user Vanae, the self-proclaimed love and dating coach, answers subscribers relationship questions with passion and careful insight. This near four minute edition focuses on the oh so complicated on again, off again relationship. Vanae instructs participants in these arrangements to seriously consider the pros and cons of continuing this indecisive coupling. She addresses common characteristics of participants in on again off again couplings. Vanae also counters fears that often encour...

Ever need to text someone, but don't want to use up your texting limits? Or you want to text someone, but your phone doesn't have texting capabilities? As long as you're near a computer, this video has you covered.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to build a web-enable remote controlled tank.

Many young players have a too tight, smile embouchure with the flute high on their lip and the hole almost entirely covered. Some were initially taught the coke-bottle method of blowing straight across the hole. This video addresses these common problems that many flutists have. This flute playing method is based on the techings of Bradley Garner, who teaches the lower roll out into the flute technique. The angling the air toward the crown idea was taught by Alain Marion. It may feel very str...
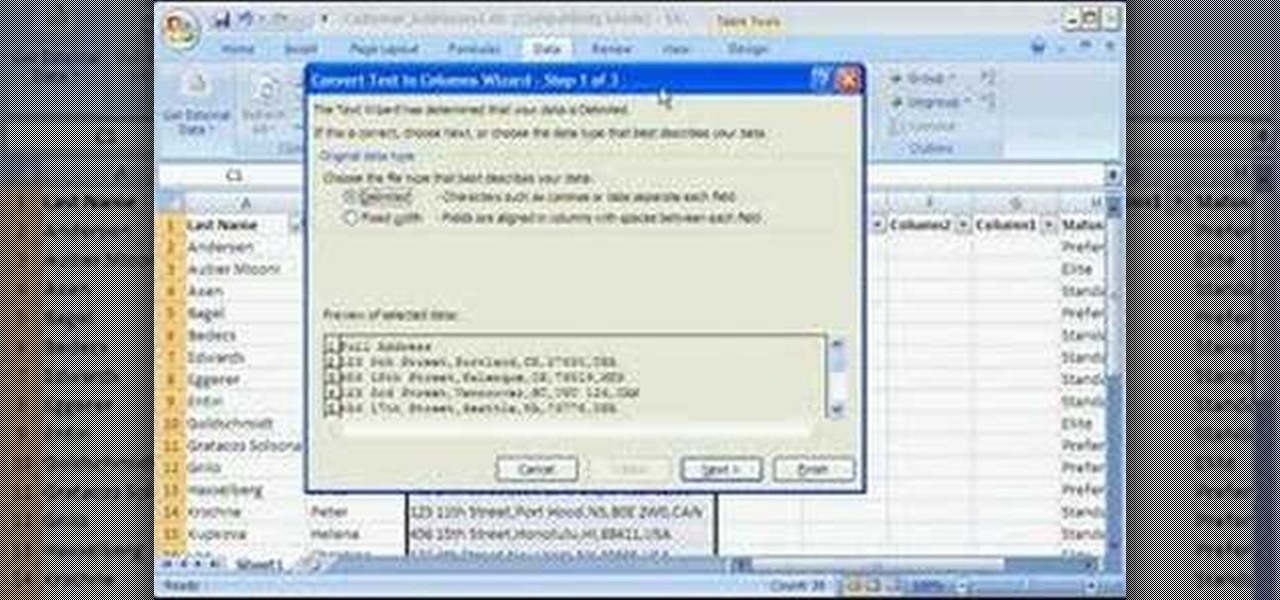
Storing information, such as a full address, in one column can limit what you can do with that information. For example, you can't easily filter or sort by part of the address, such as country/region or city. However, if you break up the address into its parts — street address, city, state/province, postal code, country/region — one for each column, you can remove those limits. Watch this instructional video to see how to use the Convert Text to Columns Wizard to automatically break up a sing...
Tired of writing addresses on your outgoing letter mail? Well, you can start printing them out instead! But how!?! If you have Microsoft Word, it's a cinch, and it's not just about making envelope address labels, it's about adding your own personal, creative touch to each one.
Whether you're a social type with a loooonnng list of friends or a PR gal with a bunch of people you've got to contact all at once to notify them of an event, it can often get time-consuming to type out the name of every single person you have to send the same email to.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.
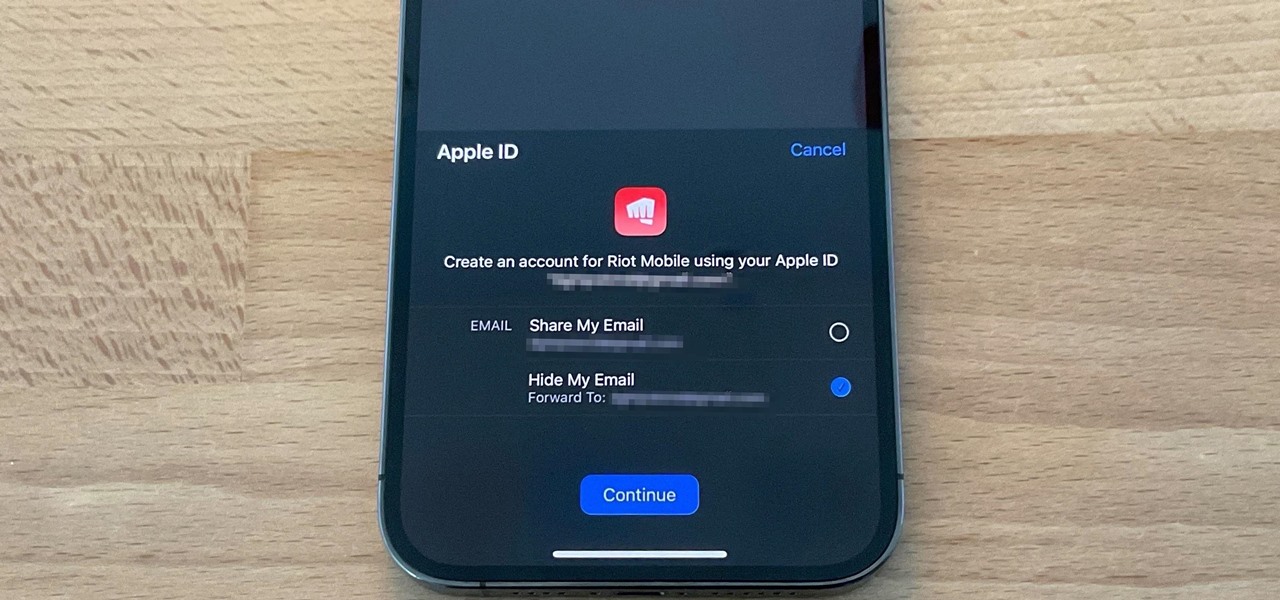
The "Sign in with Apple" service lets you create accounts with third-party apps and websites more easily using your Apple ID. More importantly, it can hide your personal email address using auto-generated disposable email addresses. However, it's easy to lose track of the accounts you use with Sign in with Apple, as well as any throwaway email addresses you used to hide your actual address.

It's finally out. After months of testing, iOS 13 is available to install on your iPhone, which means over 200+ new features you can use right now. The update, released on Sept. 19, can be installed over the air or from a restore image using iTunes in macOS Mojave and older or Finder in macOS Catalina. Ditto for the 13.1 update issued on Sept. 24.
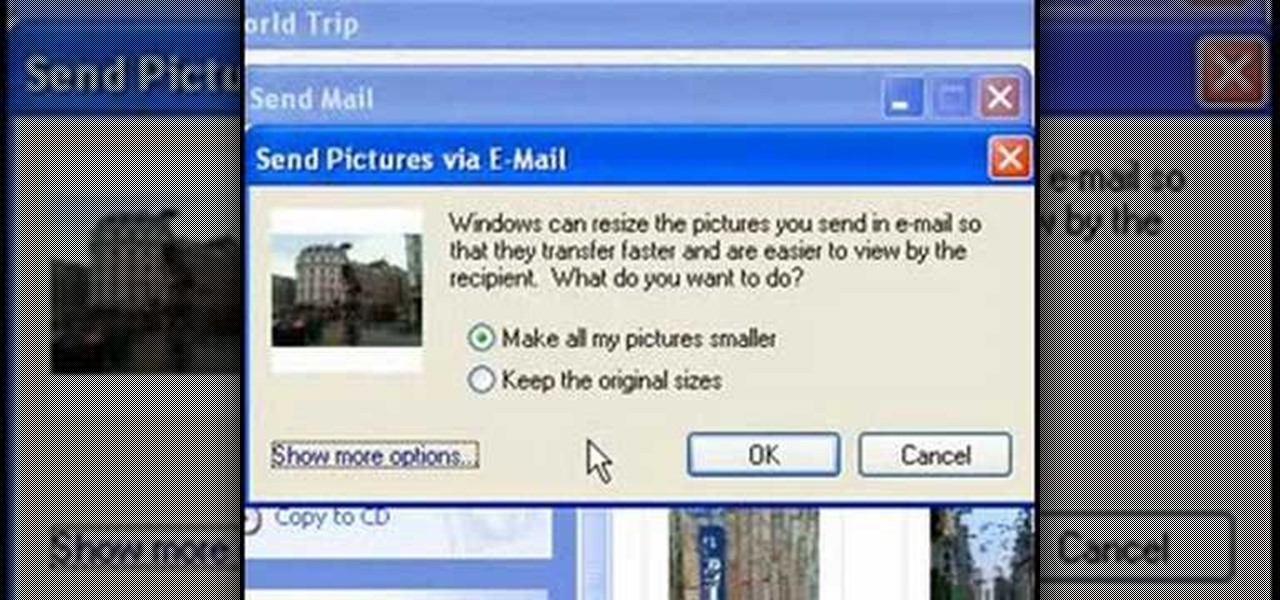
This video tutorial from easycomputercoach shows how to easily attach pictures to email addresses. In Windows XP you can send pictures resizing them in the process, in case you have large file sizes.

This video tutorial shows how to open a port for torrent downloading on your computer. Click Start menu, type cmd command in Search area. In cmd window type ipconfig and press Enter. Remember or write down your IP adress. Type exit and press Enter to close cmd window.

CC, which stands for "carbon copy", is a familiar phrase in email, but can also be used in business letters and legal documents. This can be especially useful for letters you want to spend up a company or organizational chain, letting each recipient know exactly who else received the same document.

Attention aspiring screenwriters! In this tutorial, learn how to sell that script. You may have written the next Hollywood blockbuster – but unless you can finance the film yourself, you’ll need to sell the screenplay to a producer who can make it come to life.

All you need to remotely access your computer's iTunes library is your iPhone. Control itunes with your iPhone with this Howcast guide.

All you need to remotely access your AppleTV library is your iPhone. Learn how to control Apple TV with your iPhone with this Howcast guide.

Thanks to the Freedom of Information and Privacy acts, we’re all entitled to see what the FBI has on us. Learn how to get your hands on your FBI file.

Welcome back, my hacker novitiates! Finding vulnerabilities in systems can be one of the most time-consuming tasks for a hacker. There will be times, though, when you'll find yourself in a position that you know that a particular port represents a vulnerable application or service.

Thinking of selling your car on the internet? Make sure you don’t get taken for a ride. You Will Need

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.
This video shows you how to control your computer from your iPod touch. 1. Go to UVNC. Click on Installation. This will take you to download options. Download the latest stable version. 2. Install Hamachi, which helps you find your computer's IP address. Click on Download Here link, fill in the registration information, and click submit. 3. Install a VNC listener on your iPod so it can connect to your desktop. Jailbreak your iPod, and open the installer. Click All Programs; scroll down until ...

Apple released iOS 13.4 to public beta testers on March 18. The update comes the same day we learned that iOS 13.4 would be made available March 24. The sixth beta is iOS 13.4's GM (golden master), even though Apple refers to it as "beta 6."

Apple released iOS 13.4 to registered developers on March 18. The update comes just hours after news broke that iOS 13.4 would hit all compatible devices on March 24. The update is the GM (golden master), which makes it the same build as the official release we expect to see on March 24, although Apple does refer to it as "beta 6" on the dev site.

Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through URLs on our behalf to retrieve information of value to a hacker.
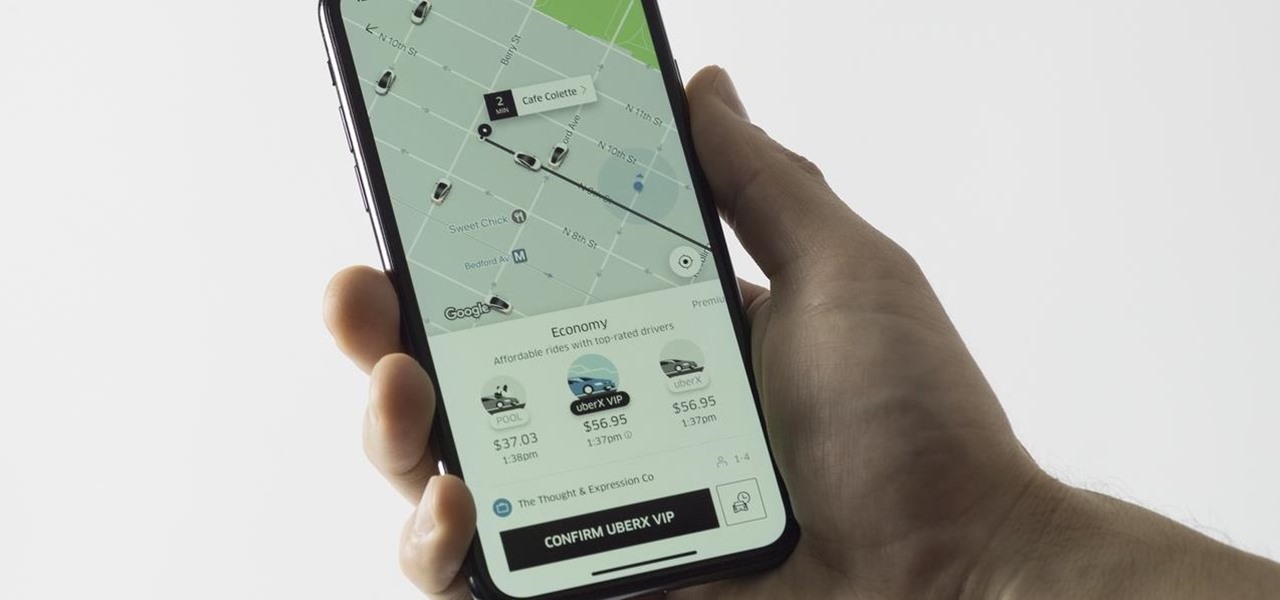
Uber is one of the best ride sharing services out there, allowing you to travel without needing to be tethered to a car of your own. Still, if you're a frequent flyer, you may get tired of entering the same few locations into your app every time you use it. Fortunately, Uber lets you streamline this process.

In general, hacking and information security is not just one discipline, but a number of them, and today we will look into some of the networking concepts.

Hello there! This will probably be the final tutorial on functions where we will be looking over a method called pass by reference. This technique allows us to modify large amounts of data without the overhead and return multiple values. Let's go!