In this advanced three-part tutorial, learn how to create a beautiful, sweeping animation for Cherry 7-Up. This animation is made using Cinema 4D and will take a bunch of cherries, have them swim together and form the logo for 7-Up. This animation is gorgeous and looks so professional that you'd think it was an official ad for the brand.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

The headsets of tomorrow offer some amazing possibilities in both gaming and work, but what we've seen so far only begins to scratch the surface. The US Navy saw the potential to use augmented reality in a helmet to provide divers with an incredible amount of information we have so far only seen in Hollywood movies.

continuing this series, I will now go in-depth on using advanced search queries. What Is Search Queries Again?

This is an advanced Aikido Ukemi tutorial which explains 11 different exercises seen and unseen. The tutorial includes detailed explanations of how to perform soft high falls from different techniques, various backward rolling tricks and other unseen ukemi variations.

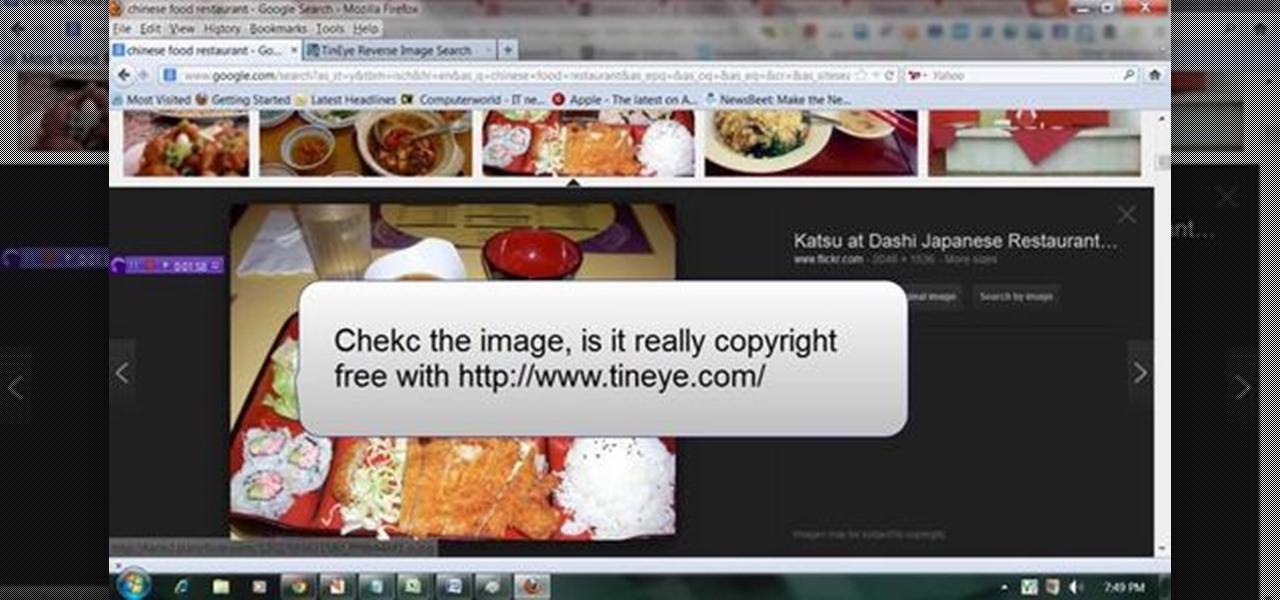
This video will describe you how to search for a Copyright free image. Google advanced image search gives you the opportunity to find free images from any category. Copyright free images are free to use in personal even as commercial purpose. Watch the video and follow the steps.

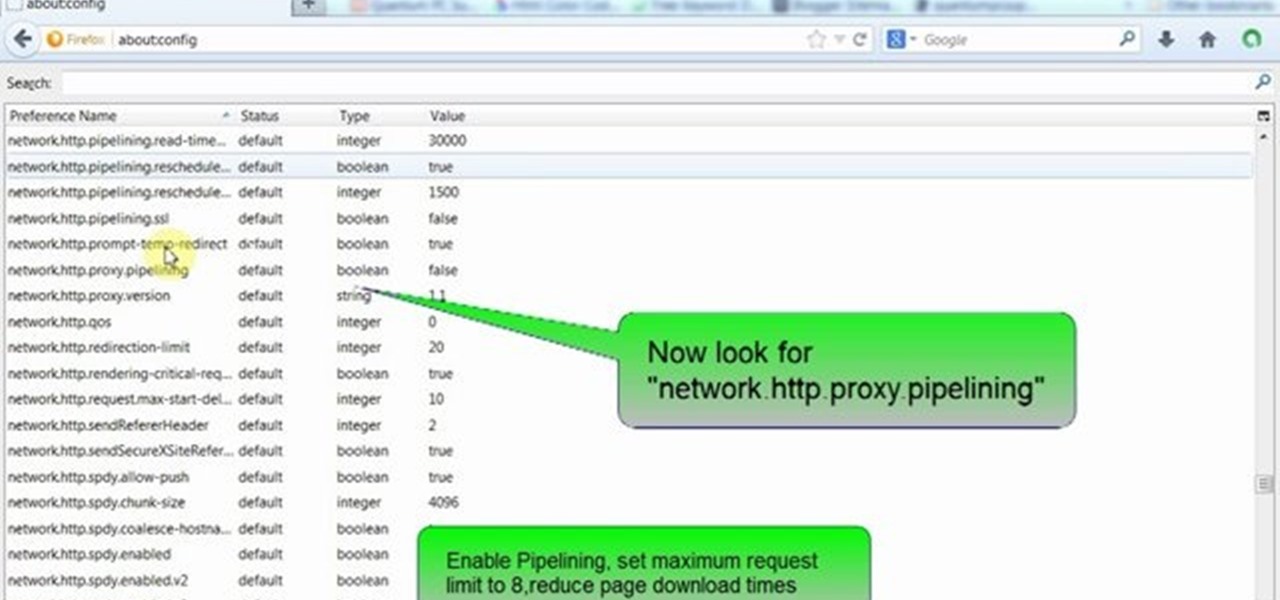
This video will guide you few advanced tricks to speed up Firefox browser. If you apply these tricks it will definitely increase the speed and make your browsers experience sweeter. Watch the video and follow all the steps.

Welcome back! In our last training session, we covered some advanced list topics. We'll be going deeper into the advanced list rabbit hole today with lambda and lambda operators! (And I'm not talking about Gordan Freeman)

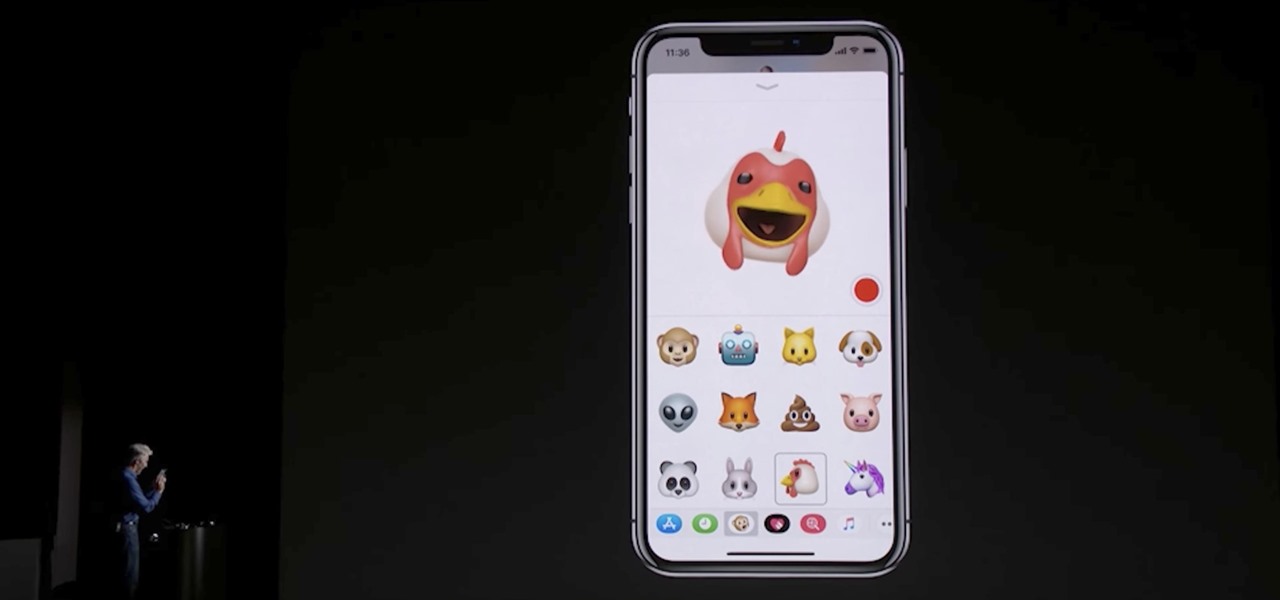
Animoji, short for animated emoji, was a focal point of the iPhone X presentation at the Sept. 12 Apple event. The reactions were split, to be sure, as some considered the attention to this feature on a $1,000+ smartphone to be a bit, well ... too much. As goofy as Animojis may seem at first, the tech behind them is undeniably impressive. In fact, it's possibly the most technically advanced feature of the iPhone X.

Welcome back! In the last training session, we covered logical and membership operators. We're going to switch gears and expand our knowledge of lists.

While not quite a true self-driving car, Mercedes is gearing to release a vehicle with a plethora of assistive-driving features, some that might have you excited about what autonomous vehicles can do in the future.

After the mobile augmented reality platforms of ARKit and ARCore moved Google's previously groundbreaking Project Tango (the AR platform that gave us the first smartphones with depth sensors) into obsolescence in 2018, we've seen a bit of a resurgence of what was then a niche component for flagship devices.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

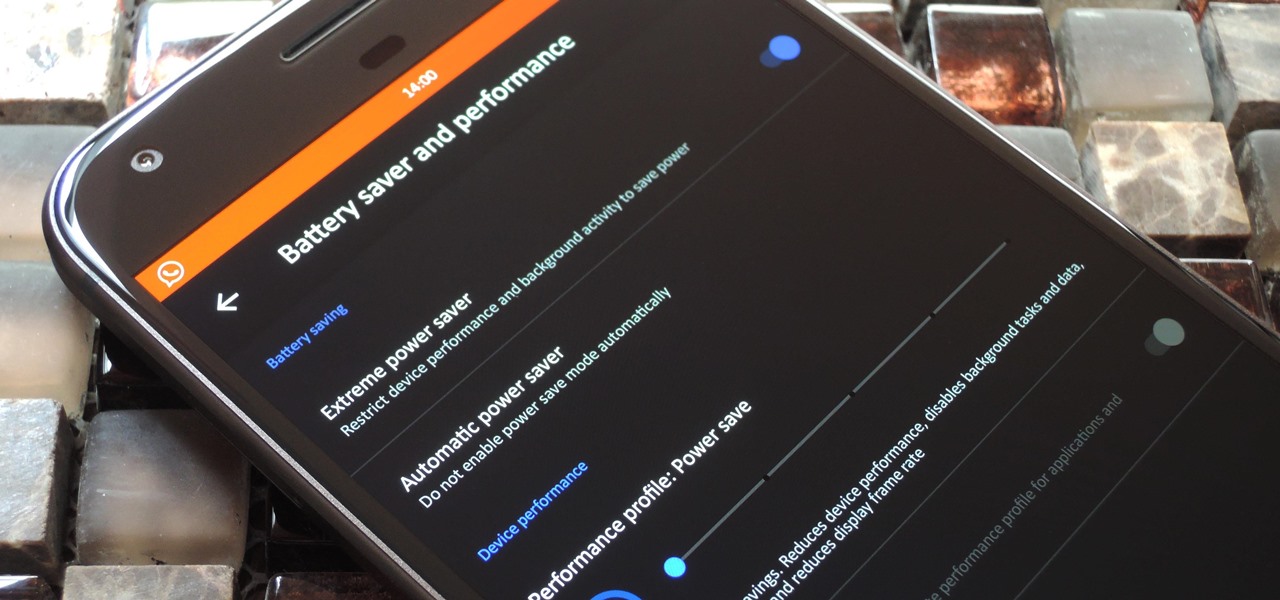
LineageOS, the successor to the wildly popular CyanogenMod custom ROM, is adding an interesting new feature that could potentially save lots of juice when your battery is running low. When enabling "Extreme power saver" mode, which can be set to kick in automatically at 15%, you'll soon have the option of changing your kernel's performance profile as well.
Hello! My name is An0nex. I am an ethical hacker who wants to share the art of hacking with all of you guys!

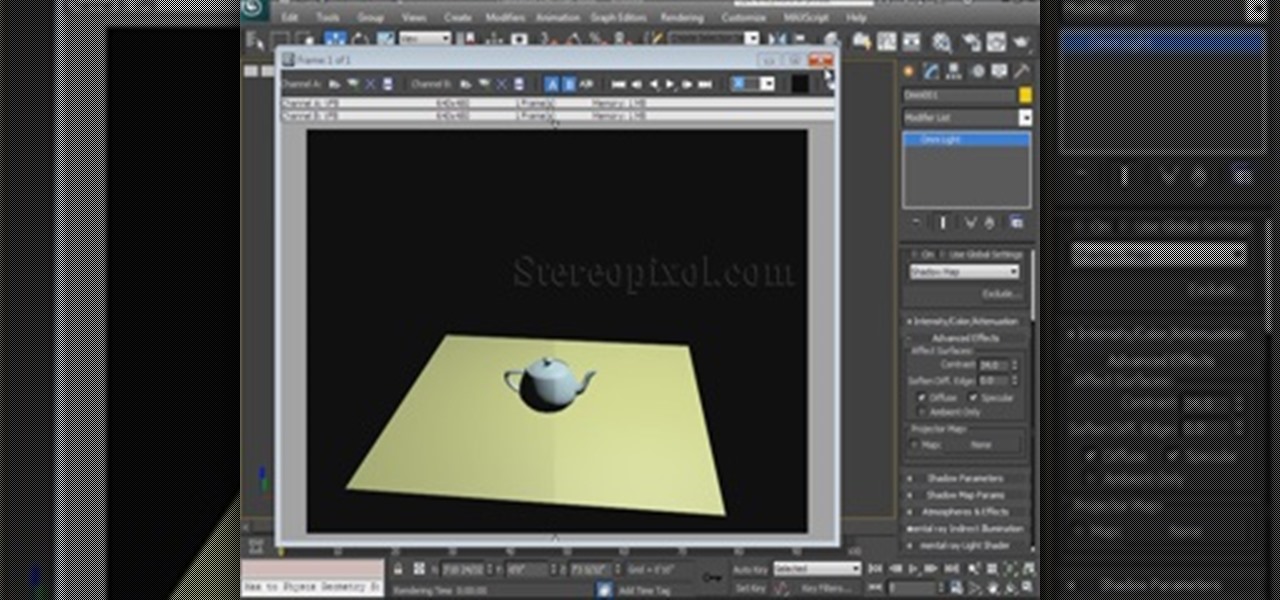
Welcome to the 5th Chapter of the Lighting series in 3Ds Max. In this tutorial, you are going to learn about the Advance effect roll out in almost every lights in 3ds max. In the tutorial we have covered different option like contrast, soften edge, projector map etc. Hope you will enjoy this.

Here is a manoeuvre that you won't see every day. It is intended for drivers in commercial vehicles who cannot see to the rear. By reversing with the flow of traffic it is possible to see approaching vehicles through the front windscreen and the right hand kerb by looking down over your shoulder. This manoeuvre sometimes occurs on the ADI, Part 2 Test of driving ability.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.

Welcome back, my novice hackers! Reconnaissance is one of the most important preparatory steps to hacking. As I have emphasized many times before here on Null Byte, you must know the operating system, the ports, the services, the applications, and sometimes even the language of the target to be effective. If you haven't taken the time to gather this info, then you are likely wasting your time.

Kali Linux is probably the most well-known hacking distribution among penetration testers. However, there are alternative distros which offer versatility and advanced package management systems that are absolutely worth considering.

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

Cross-site scripting can be one of the easiest vulnerabilities to discover, but to be successful with this type of attack, it is essential to learn how to get past filters. In the previous guide, we explored some ways to do this, such as abusing attributes and event handlers and tricking the application into accepting unusual characters. Now, let's take a look at more techniques used to defeat filters.

There is no shortage of defenses against cross-site scripting (XSS) since it is so prevalent on the web today. Filters are one of the most common implementations used to prevent this type of attack, usually configured as a blacklist of known bad expressions or based on regex evaluation. But there is hope with a wide variety of techniques that can be used to defeat these filters.

Considered a huge gamble on the part of Marvel and Disney due to its seemingly small fan base, Guardians of the Galaxy turned out to be well worth the risk, nearing $800 million in world-wide box office numbers. Many may not have known about the comic book prior to the movie, but you can definitely count on plenty of Guardians of the Galaxy costumes this Halloween.

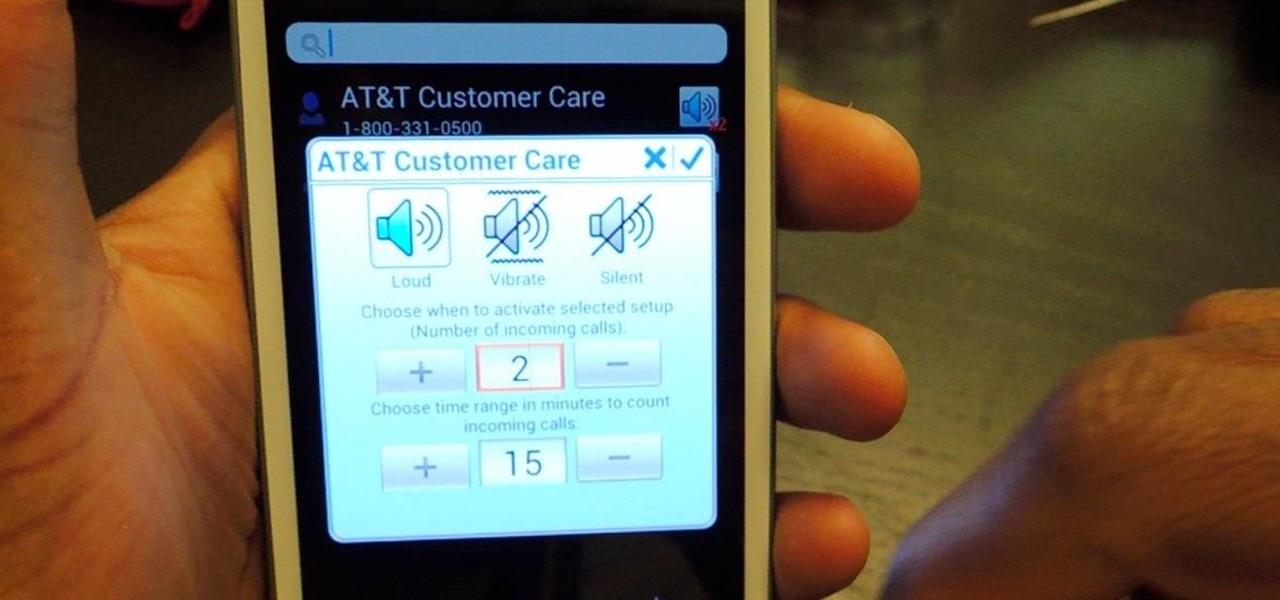
There are two scenarios that absolutely suck when someone calls you. The first is when you accidentally pick up a call you seriously didn't want to take. Debt collectors (thanks college), crazy exes, or that one guy from work. And the other is when you miss a super important call and can't get a hold of them afterwards.

Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.

While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are all network services, which means we'll write our first remote exploits.

One of the main reasons for installing a custom ROM on an Android device is all of the added features. For instance, OmniROM offers a souped-up multitasking mod called OmniSwitch, so instead of the regular app switcher, you get an interface that lets you pin your favorite apps, access settings, view memory usage, and more.

If you're like me, the words 'monostable circuit' mean nothing to you. Until just recently, I had no idea what a monostable circuit did, or why anyone would ever need to use one.

Welcome back! Sorry for the dry spell, but I've been rather busy setting up some side projects! If you remember back to a few training sessions ago, we covered basic file I/O. This is a very important step in making our scripts applicable in a real life scenario, and today we're going to further these concepts.

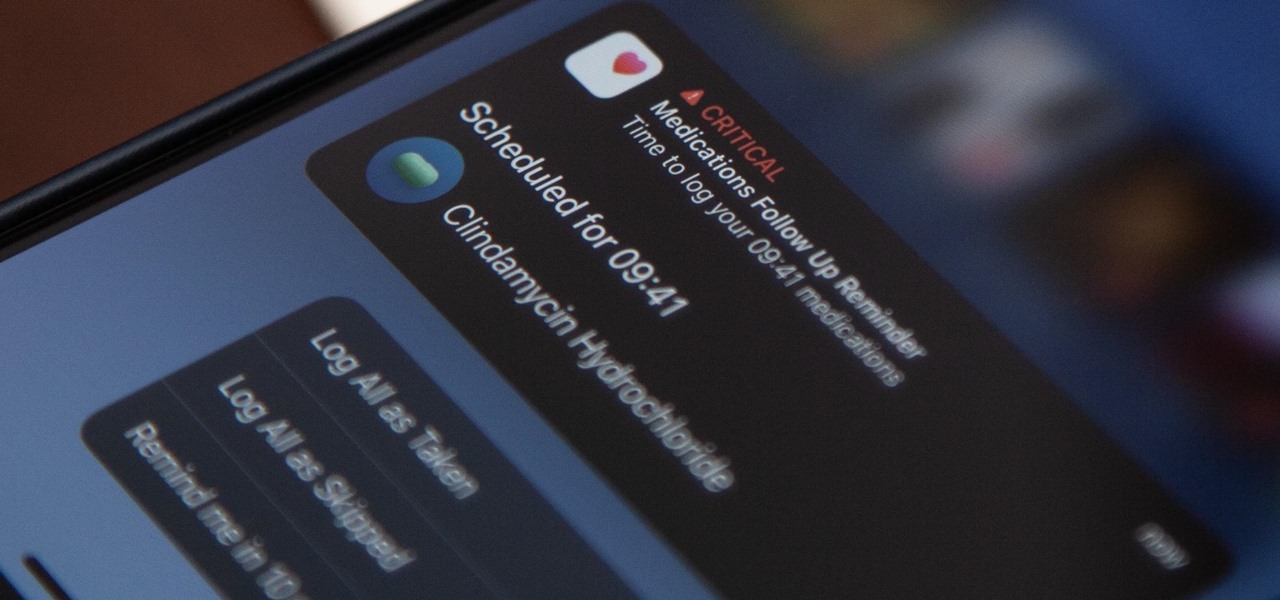
Since iOS 16, you've been able to add and track medication in the Health app, learn about potential drug interactions, and receive dose reminders. With iOS 17, Apple improves that last aspect with even more notification options to ensure you take your medicine on time and never miss a dose.

Hello people again, I wrote my last post about crypto about 10 months ago, now I will introduce something not fresh for the science, but fresh for the people who wants to learn. In my http://null-byte.wonderhowto.com/forum/cryptography-0161538/ post of crypto concepts, there is just basics, today we will see something that targets wide concepts like Symmetric crypto, Public Key Cryptography, Hashing, Keys etc...

A man-in-the-middle attack, or MitM attack, is when a hacker gets on a network and forces all nearby devices to connect to their machine directly. This lets them spy on traffic and even modify certain things. Bettercap is one tool that can be used for these types of MitM attacks, but Xerosploit can automate high-level functions that would normally take more configuration work in Bettercap.

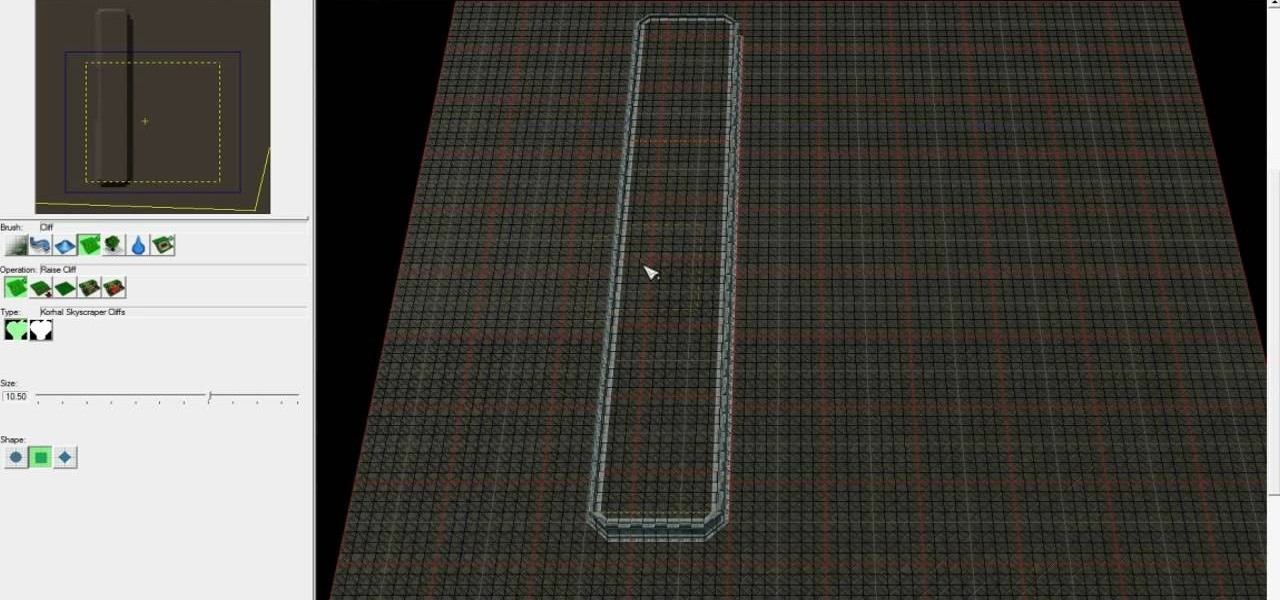
Starcraft 2, like it's predecessor before it, has a very robust level editor that allows you, the DIY modder, to create nearly any scenario within the bounds of the Starcraft 2 engine that you could imagine. We have compiled videos on how to do all sorts of fun things with it, from making RPG's and Tower Defense games to just making you dream Starcraft 2 level. This video will teach you how to create a complete and advanced Tower Defense game in the Starcraft 2 editor, allowing you to create ...

The beautiful game, Football (Soccer for those of you in the US) is full of all sorts of unique and advanced techniques that you can use in FIFA 11 to defend with! Things such as a Secondary Press, Jockeying and even Running Jockey. If you're still getting scored on and are looking for more advanced techniques to try, check out this video for some advanced tactics for defending.

If you are already really good at using Photoshop, good for you! You already know what the dodge tool, blending modes, and all the different brushes do? Well then watch this video! It offers help for advanced Photoshop users on working with lighting for design and abstract art. Novices need not apply.

The Amazon Kindle 2 has changed the way millions of people read books, but many of you aren't taking full advantage of your device's many advanced features. This video will show you how to use some advanced features of the Kindle 2, including how to highlight text, annotate text, and add a bookmark.