Although mainly demonstrational, this video shows you how to play "The Little Beggarman" on the banjo. This video is intended for advanced players who learn easily by watching or listening. Read the useful tips posted below to aid your banjo learning:

Although mainly demonstrational, this video shows you how to play the "Fingerbuster" on guitar. This video is intended for advanced players who learn easily by watching or listening. Read the useful tips posted below to aid your guitar learning:

Although mainly demonstrational, this video shows you how to play a song "Summertime" in D minor on guitar. This video is intended for advanced players who learn easily by watching or listening. Read the useful tips posted below to aid your guitar learning:

Who's heard of Arthur Alexander? He wrote and recorded some great songs but, ironically, it was other artists who made hits with their cover songs of his work. This is "Go Home Girl" - very similar to his other classic, "You'd Better Move On". Play a simple version in D with a touch of Ry Cooder's style on the "Bop 'Til You Drop" album.

Although mainly demonstrational, this video shows you how to play a song "The Japanese Sandman" on guitar. This video is intended for advanced players who learn easily by watching or listening. Read the useful tips posted below to aid your guitar learning:

Although mainly demonstrational, this video shows you how to play "Doctor Jazz" by Joe "King" Oliver on guitar. This video is intended for advanced players who learn easily by watching or listening. Read the useful tips posted below to aid your guitar learning:

Although mainly demonstrational, this video shows you how to play "Stealin'" by Will Shade on guitar. This video is intended for advanced players who learn easily by watching or listening. Read the useful tips posted below to aid your guitar learning:

Although mainly demonstrational, this video shows you how to play "Strolling Down the Highway" by Bert Jansch on guitar. This video is intended for advanced players who learn easily by watching or listening. Read the useful tips posted below to aid your guitar learning:

A field hockey midfielder is the quarterback of the team, and must advance the ball from the defense to the offense. Learn how to play midfielder in field hockey in this video tutorial.

Breathing is a skill to master before trying advanced swimming strokes. Learning to breathe while swimming will enable rapid progress. Get expert tips and advice in this swimming video tutorial.

The LG KF700 Virgo is designed to maximize convenience, enjoyment and productivity, LG’s advanced UI brings new meaning to the word convenience. The KF700 is the only place to get hands-on experience with the magic of its touch as you control your mobile life with simple gestures.

The LG KF700 Virgo is designed to maximize convenience, enjoyment and productivity, LG’s advanced UI brings new meaning to the word convenience. The KF700 is the only place to get hands-on experience with the magic of its touch as you control your mobile life with simple gestures.

The LG KF700 Virgo is designed to maximize convenience, enjoyment and productivity, LG’s advanced UI brings new meaning to the word convenience. The KF700 is the only place to get hands-on experience with the magic of its touch as you control your mobile life with simple gestures.

This four part tutorial teaches you how to dance basic hip hop moves. Learn popping, and gliding moves. These moves are easy to do and are the basis for more advanced hip hop moves. Watch this how to video and you'll be dancing hip hop in no time.

This tutorial teaches you how to do basic swing dance moves for beginners. These moves are the building blocks for more advanced swing dance routines. Learn how to do a basic step in closed position, a tuck turn, send-ins and send-outs as well as many other moves with this how to video. Watch this how to video and you will be swing dancing in no time.

This how to video teaches you some advanced Lindy Hop swing dance moves. Learn how to do an inside turn, an inside turn with slingshot, and a whip to free spin, as well as some other moves. Watch this video and you will be dancing the Lindy Hop in no time.

This five part how to video teaches you the basic steps for swing dancing. These steps are the basis for other more advanced styles of swing dance such as the Lindy Hop and the Charleston. Watch this tutorial and you'll be swing dancing in no time.

Check out this how-to video for a discussion of the card strategy game, Mystery Rummy Case #1 with its designer, Mike Fitzgerald. Mystery Rummy Case #1 is a two to four player game. Take a look at these Mystery Rummy cards!

Get a new perspective on computing with an HP Tablet PC. HP's Tablet PCs are well-equipped personal notebooks, with a significant twist. The display turns around one hundred and eighty degrees, transforming your notebook into a flat tablet touchscreen PC.

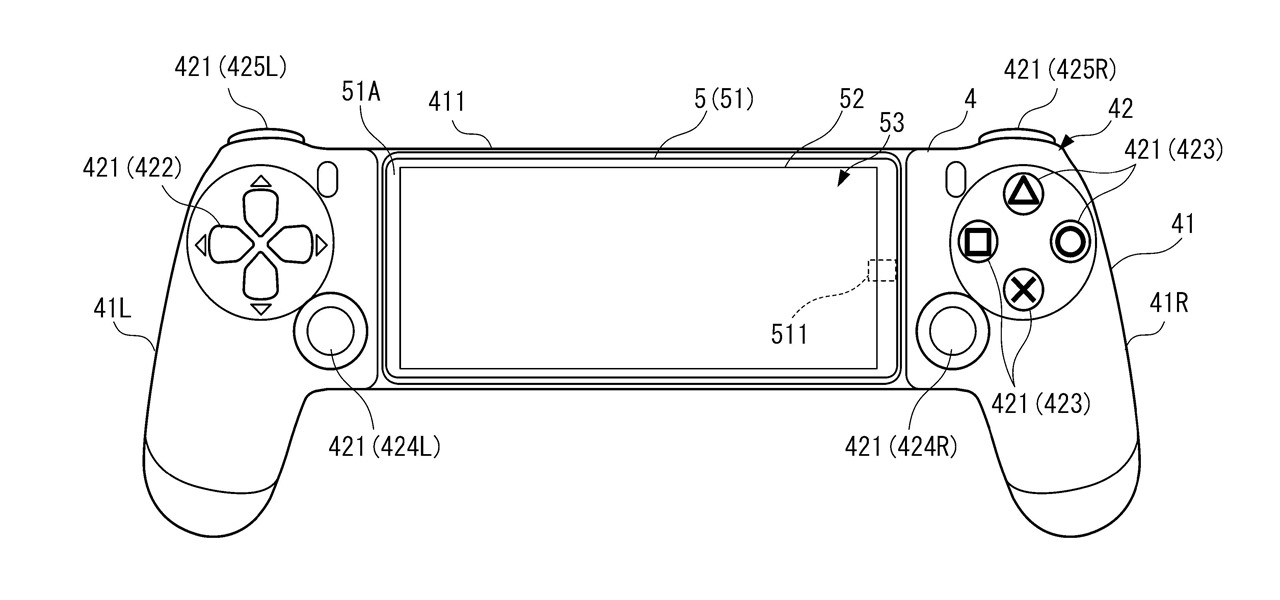
A new Sony patent shows the company doubling down on mobile gaming, and it could mean more advanced controller features for your iPhone or Android phone, similar to those in PlayStation's DualSense and DualShock controllers.

After the mobile augmented reality platforms of ARKit and ARCore moved Google's previously groundbreaking Project Tango (the AR platform that gave us the first smartphones with depth sensors) into obsolescence in 2018, we've seen a bit of a resurgence of what was then a niche component for flagship devices.

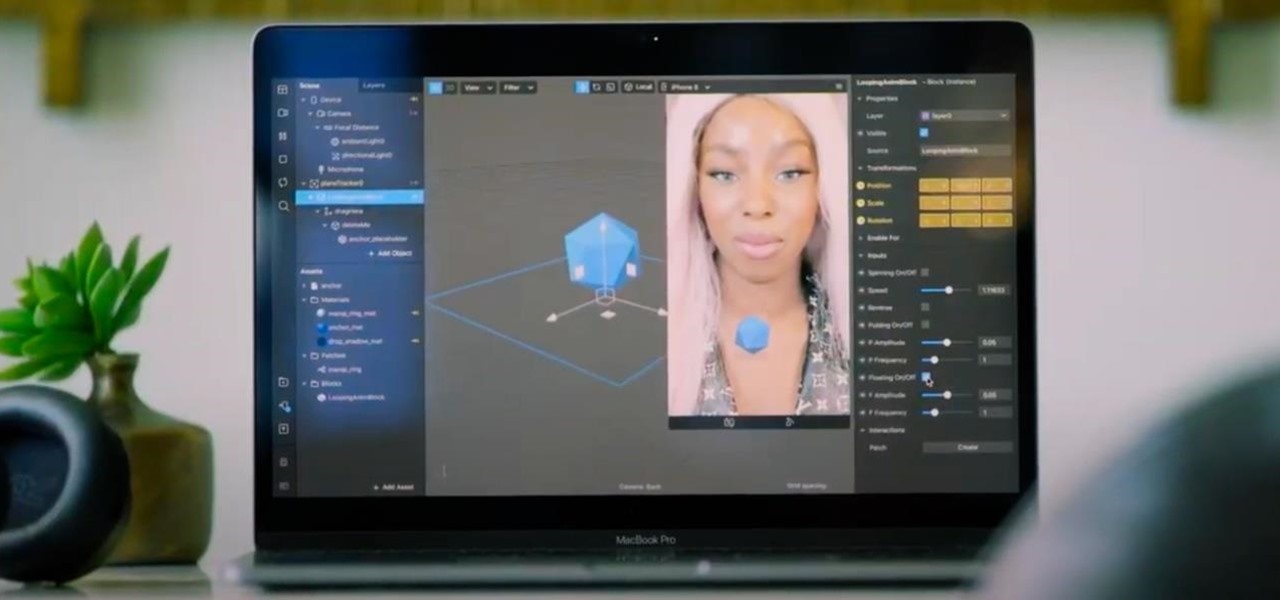
As Apple, Google, Snap, and Facebook wrestle for positioning to lure developers and creators to build augmented reality experiences for their respective tools, Facebook is looking at a learning approach for its Spark AR platform.

Written language began with one of the most pedestrian tasks imaginable: accounting. The basis of poetry, epic mythologies, and novels initially involved marking down trades between livestock owners and grain suppliers. We rightfully think that literature is essential to the human spirit. But when contemplating how societies operate, spreadsheets are king.

As one of the world's largest and most powerful cloud computing platforms, Salesforce is used by countless companies to manage customer relations, deliver services, and innovate solutions to complex problems.

No longer strictly relegated to the realm of science fiction shows and novels, artificial intelligence can be found behind important technologies that are driving innovation throughout the world. From space exploration and self-driving cars to data science and marketing algorithms, AI is the driving force behind many technologies that are moving humanity forward.

Since its original release as a spreadsheet program called Multiplan in 1982, Microsoft Excel has become the world's premier business software. If you think that it's only good for spreadsheets, you haven't been paying enough attention.

If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?"

Apple's Mail app has always been a stylish yet simple way to check and send emails. Third-party apps up the ante with powerful tools and features to help keep junk and spam mail out of your eyesight. But with iOS 13, you don't need them since Apple gave the Mail app some much-needed superpowers. One of those being the ability to block senders from emailing you.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

The idea of squeezing your phone might have sounded a bit out there when it was new, but it's now a hallmark feature on Pixel devices. As useful as it is for summoning the Google Assistant, however, it certainly would be nice to be able pick and choose what action is triggered by squeezing the phone. Well, now you can.

Over the past decade, Marvel Studios has been a dominant force at the box office, raking in more than $21 billion dollars. Averaged out over that span of time, the yearly earnings of those movies outweigh the gross domestic product of some countries.

Cross-site scripting can be one of the easiest vulnerabilities to discover, but to be successful with this type of attack, it is essential to learn how to get past filters. In the previous guide, we explored some ways to do this, such as abusing attributes and event handlers and tricking the application into accepting unusual characters. Now, let's take a look at more techniques used to defeat filters.

There is no shortage of defenses against cross-site scripting (XSS) since it is so prevalent on the web today. Filters are one of the most common implementations used to prevent this type of attack, usually configured as a blacklist of known bad expressions or based on regex evaluation. But there is hope with a wide variety of techniques that can be used to defeat these filters.

No matter how good a display is, the idea of perfect color calibration is subjective — some prefer warmer more saturated colors, while others prefer the calmer cooler side of the color spectrum. It is almost impossible to create a single color calibration that everyone can agree on out of the box. The display on the Pixel 2 XL was specifically calibrated with a more realistic color profile in mind.

For some Android users, this guide is sacrilege — but for others, iOS is just an attractive operating system that can be admired without feeling like you've betrayed your own phone. If you're one of those Galaxy Note 9 owners that have peeked across the aisle and desired an interface as clean as the one on the iPhone XS Max, you can configure your Note 9 to look like its rival with some tinkering.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

Many of us rely on our smartphones for all our media needs. Now more than ever, we're using Bluetooth connections to play audio over speakers, headphones, car sound systems — the list goes on. If you own a Samsung smartphone like the Galaxy S9, there are a number of Bluetooth tweaks and hidden tricks that can maximize your audio experience.

For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.

The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you need to have a solid grasp of ... you've guessed it ... SQL.