Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. We'll use Wireshark to discover a Wi-Fi attack in progress and determine which tool the attacker is using.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

Ever since 3D Touch's introduction in iOS 9 for the iPhone 6S and 6S Plus, a little-known trick for moving the cursor around and selecting text was built into Apple's stock keyboard. On iOS 12 or later, it works for all iPhone models with or without 3D Touch or Haptic Touch baked in.

The latest Star Wars movie, Solo: A Star Wars Story, has grossed almost $350 million worldwide during its first month in theaters. This is a good opportunity to discuss how hackers can use media hype (in this case, Hollywood movie hype) to disarm an unsuspecting Windows user into inserting an evil USB stick into their computer.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

While iOS 11.3 doesn't have as many new features as iOS 11.2, there's still a lot to love about Apple's latest update for iPad, iPhone, and iPod touch, even if some of the best features we were expecting didn't make the cut.

One of Android's most glaring weaknesses is its lack of an iMessage equivalent. That is, of course, until now. There's one app that will allow Android users to experience iMessage on their non-Apple phone, complete with end-to-end encryption, message effects, and group messaging.

For almost a decade, projector phones have tried to entice consumers with their convenience as media machines. While these devices are alluring, they've never really taken off with mainstream success. The latest effort, Moviphone, sounds tempting if you watch a lot of films and TV on your smartphone, but is it good enough to be your daily driver?

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

Word games can expand your vocabulary skills in all sorts of exciting and creative ways. Because of this, both the iOS App Store and the Google Play Store are awash with word games, making it hard to differentiate between good and bad titles. This is especially troublesome if you're looking to purchase a game, as everyone hates to waste hard-earned cash.

The holidays are stressful. Between traveling, family, and dinner, Thanksgiving weekend can feel like weeks. Many families have traditions that make the days long, but some of us would rather curl up somewhere and watch our favorite shows. But all is not lost — our phones do so much for us now that they can help make the long stressful weekend much more bearable.

The Watch Dogs video game series came out in 2014, enamoring audiences with the idea of a seemingly magical smartphone that could change traffic signals, hack web cameras, and even remotely control forklifts. This may sound like science fiction, but The Sonic uses a customized flavor of Kali Linux to allow you to unleash the power of Kali from any smartphone — all without the need to create a hotspot to control it.

Armis Labs has revealed eight vulnerabilities, called "BlueBorne", which put 5.3 billion Android, iOS, Windows, and Linux devices that use Bluetooth at risk. With it, hackers can control devices, access data, and spread malware to other vulnerable devices through networks. In this post, we will learn about the vulnerabilities, then look at how to find devices that have them.

Surveillance is always a useful tool in a hacker's arsenal, whether deployed offensively or defensively. Watching targets yourself isn't always practical, and traditional surveillance camera systems can be costly, lacking in capabilities, or both. Today, we will use motionEyeOS running on a Raspberry Pi Zero to create a small, concealable Wi-Fi connected spy camera that is both affordable and easily concealed.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with.

In five short years, three generations of ultra-low-cost Raspberry Pi devices have challenged the boundaries of what a person can do with a $35 computer — especially with Kali Linux.

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.

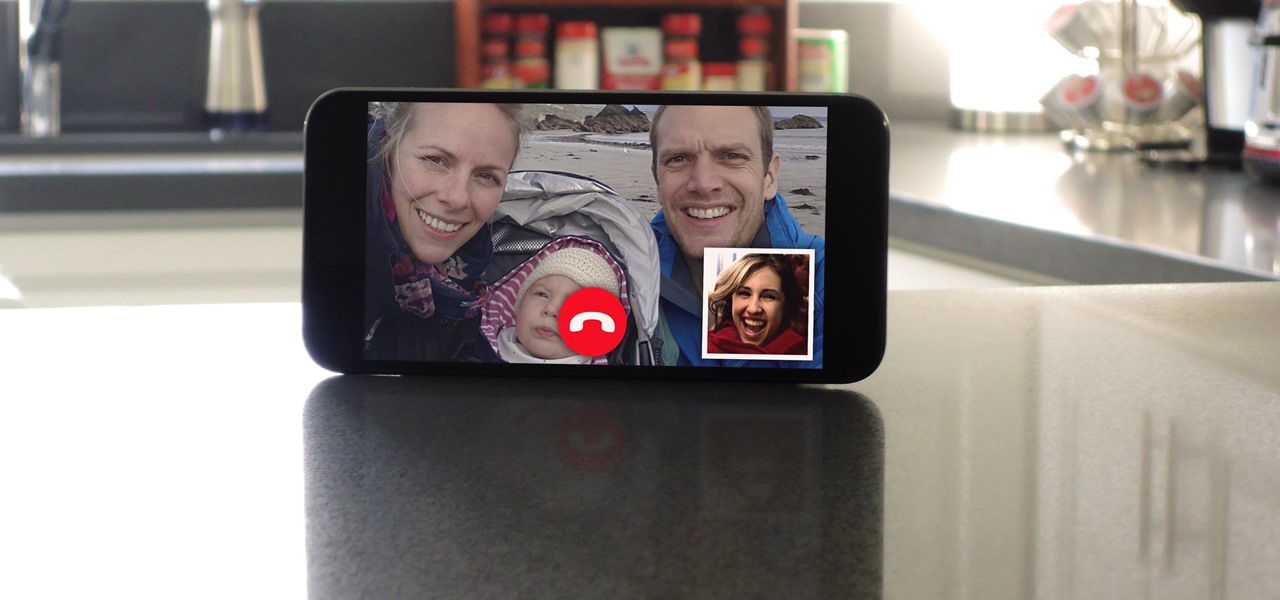
Video chatting has become an important factor in the overall smartphone experience. Even just a few years ago, 37% of teens were making video calls on a regular basis, and that number has surely grown. 85% of households with infants have used video chat apps to call relatives in other cities, and it's been shown that toddlers can create bonds and learn from visual cues in video calls.

When it comes to smartphone screens, there are two predominant technologies—the traditional LCD panel, and the newer AMOLED display. Most phones still use LCD screens, as the tech is more cost-effective due to its longstanding reign as the primary display type in TVs, smartphones, and tablets.

Now that smartphones have ensured that we're connected to the internet 24/7, online privacy has become more important than ever. With data-mining apps hoping to sell your information for targeted ads, and government agencies only one subpoena away from knowing every detail of your private life, encryption has become our last line of defense.

So you finally decided to make the switch from iOS to Android, huh? Well first off: welcome to the world of tomorrow. And secondly: good call, mate.
Hello and welcome to my article. I have made this article for anyone who wants to become a hacker, and wants to know how to get started.

Apple just announced the iPhone 6, and no matter whether you've been with Android for a few months or few years, there's a good chance you're enticed by the idea of switching over to the other side.

It may sound irrational, but I bet a lot of you actually avoid doing any work at work—but not on purpose. You might be simply struggling with motivation, or you might just be overdosing on the caffeine. Whatever the issue, getting focused takes lots of time and effort.

As was mentioned by the great OTW last week, TOR, aka The Onion Router, has had its integrity attacked by the NSA. In an attempt to reduce the anonymity granted by the service, the NSA has opened a great many nodes of their own. The purpose is presumably to trace the origin of a communication by compromising some entrance and exit nodes. Once both are compromised, it is much easier to correlate traffic with a particular individual.

Over the past several weeks, I’ve had the pleasure of test driving Samsung’s next big thing, the Galaxy S4. After putting the GS4 through its paces, I have a clear picture of what this device is capable of. I’ve covered the features of the device before, and now I’ll tell you why I believe it's currently the best Android phone on the market. Initial Impressions

I don't know how many of you had this experience in your youth, but when I was a kid, I used to actively think about what would happen if I suddenly woke up in a fantasy land, or were to pass through a portal into another space and time. I knew it wouldn't really happen, but when you're a kid, these can be important issues to you. So I slept with my glasses on every night, just in case. Photo from George Pal's The Time Machine.

Thrift stores! As a Steampunk, they can be your best friend, but it's easy to make a tragic mistake. This hands-on guide will help you navigate the murky waters of successful thrifting in order to find the hidden gems that will make your Steampunk outfit complete!

Apple's Dynamic Island is an animated, interactive isle surrounding the front-facing camera on the iPhone 14 Pro series. It's a small capsule when nothing is going on but fluidly stretches across the screen for notifications, alerts, and ongoing activities like music, timers, and directions. It can even expand with controls and more information. And now, you can get Dynamic Island on your Android phone.

After the dust settled from Apple's annual iPhone event, there's not a lot to get hyped up about the iPhone 13 lineup, particularly if you upgraded your smartphone last year.

The Fourth of July, the celebration of US independence, as well as the second paid holiday of the summer, has arrived.

Sure, Microsoft has mostly marketed its HoloLens headsets towards enterprises and developers, but we learned this week that, like every other tech giant, the company is working on a consumer-grade AR wearable. Speaking of consumer smartglasses, Apple made another strategic investment this week that has implications for Apple's AR future.

Apple has a sterling reputation when it comes to managing its supply chain; it's where CEO Tim Cook proved his mettle to succeed Steve Jobs. Now, the company has made a strategic investment with a supplier that will be crucial to its future plans for AR wearables.

One of the smaller frustrations of the coronavirus pandemic is unlocking your iPhone with Face ID while wearing a mask. If you have an iPhone with Touch ID, you won't need to punch in your passcode every time Face ID fails since you can use your fingerprint. But for those of us without Home buttons, unlocking our iPhones just got a lot easier — even if we're wearing a mask.

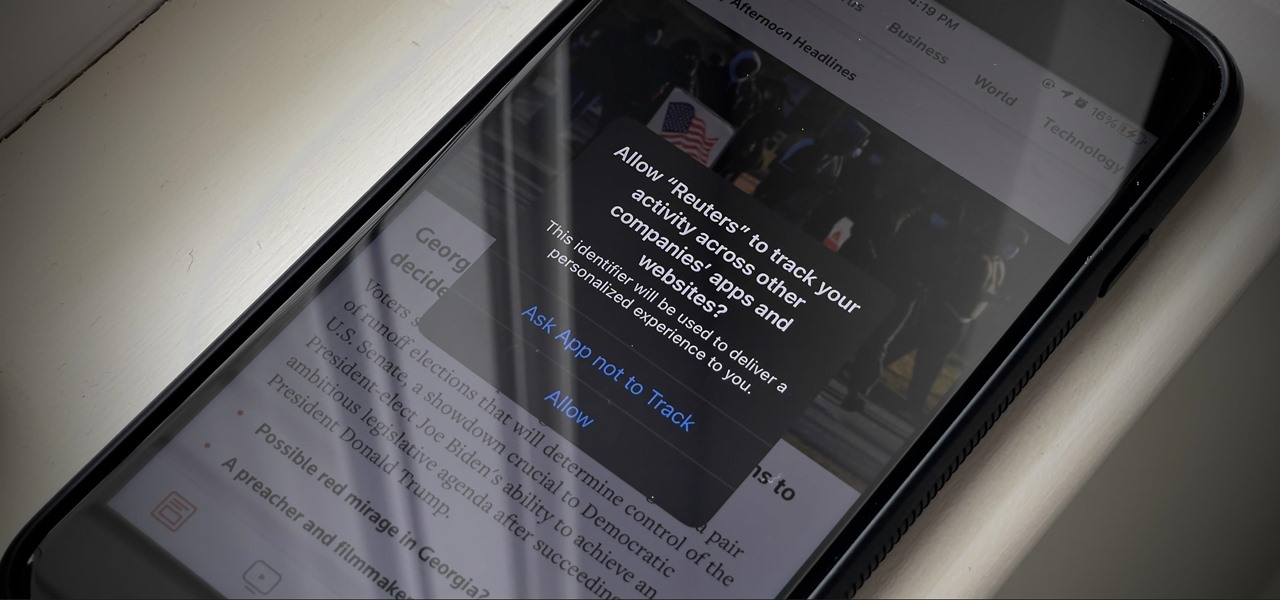
If you're like me, you're not too keen on being tracked. So when an app asks you if it can track your iPhone activity across other programs and websites for ads or data brokers, the answer is pretty much always "no." If you're tired of choosing "Ask App Not to Track" over and over again, there is a way to stop apps from even being able to ask in the first place.

Apple released iOS 14.5 developer beta 1, and the update sports a list of interesting features and changes. Some of those include support for the Xbox Series X and PS5 DualSense controllers, the ability to unlock your iPhone with Apple Watch, AirPlay 2 support for Fitness+, 5G support for dual-SIM setups, and a refreshed Software Update page in Settings.

Compared to Apple's products like the iPhone and iPad, Android phones and tablets are very flexible devices. For instance, you can set a new home screen, replace the lock screen, or even beam files using NFC — but that's just the software side of things, and the flexibility goes well beyond that.