As soon as you try recording a video in the Camera app on your iPhone, any music playing on your device comes to a halt. Apple Music. Spotify. Pandora. Tidal. Deezer. No matter what you're listening to, as soon as you switch to "Video" in the Camera app, the music will stop. However, if you want background music in your movie files, there's a workaround to avoid having to add an audio track in post.
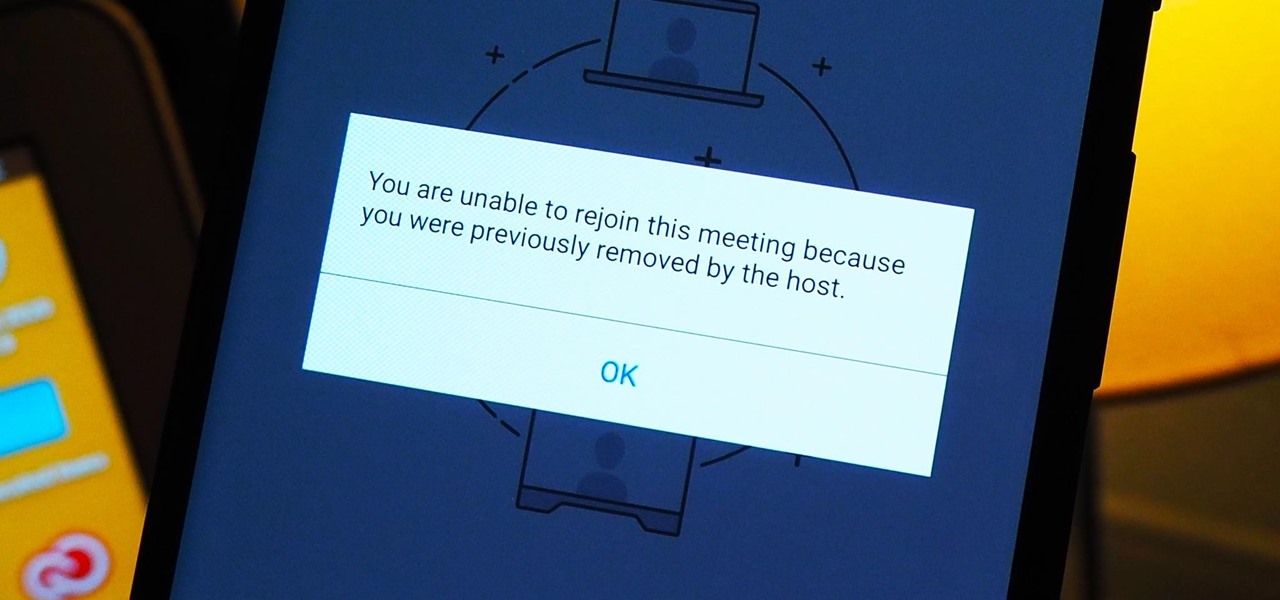
As more and more people use the video conferencing service Zoom, the chances of trolling behavior and attacks only increase. But it's not just "Zoombombers" you need to worry about. A heated discussion between family, friends, or colleagues could turn sideways real quick, and sometimes the best course of action is to remove the participant from the group video meeting altogether.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

An attacker can repurpose public MyBB forums to act as command-and-control servers. It only takes a few lines of code to configure a MacBook to fetch commands and send responses to any website the attacker desires.

Part of the fallout from the canceled Mobile World Congress is that a range of products, ideas, and designs slated for reveal in Barcelona are now being showcased without the framing and context of the massive tech gathering.

While many people may use Bluetooth every day, the majority don't know how it works or that it can be hacked. Bluetooth hacking gives a clear window into the world of the target. Nearly every device has Bluetooth capabilities, and people store a great deal of personal info on their phones and tablets. Hack their Bluetooth connection, and you may be able to access all of that data.

One Instagram creator's augmented reality homage to Disney's deep bench of animated characters has earned him fifteen minutes of fame.

All those Apple commercials encouraging people to use their iPhones to make their smartphone movies look amazing, but how can you achieve some of the same looks? That's the question many often ask after plunking down over $1,000 for a brand new iPhone, shooting some video, and getting somewhat mediocre results.

The iPhone's autocorrect feature is wonderful and convenient, but it doesn't always work with informal language like profanity. If you've ever used the F-word, there's a good chance you've had your curse words "corrected" to other words that don't ducking make sense. And with the release of iOS 13, swearing in your messages and on social media could get a little harder.

Until Star Wars-style 3D hologram projection technology becomes commonplace, the near future of certain kinds of remote work is in robotics. Now, a new dynamic is using augmented reality to give this kind of telepresence a kind of superpower.

Although early attempts at consumer smartglasses have employed trackpads and handheld or wearable controllers for user input, its the gesture control interfaces of the HoloLens 2 and the Magic Leap One that represent the future of smartglasses input.

It was a long time coming, but we finally have a meaningful conclusion to the legal case against augmented reality startup Meta Company.

Apple Card has generated quite the buzz since its March 2019 announcement. The iPhone maker's new credit card pairs with Apple Wallet on your device, is simple to sign up for, includes enhanced security over other cards, has zero fees, and provides daily rewards right to your Apple Cash account. And as good as that sounds, the fine print can complicate things real quick.

Every summer for the last 26 years, hoards of hackers have descended on the Las Vegas Strip for DEFCON, the biggest hacker conference in the US. There's a wealth of talks every season (DEFCON 27 has at least 95 scheduled), and there have been some essential topics to learn from in past discussions. We've dug through the last ten years and found the 15 most popular talks you should watch.

Years ago, in 2013, Occipital introduced its original Structure Sensor for iOS, a mobile 3D scanning device for measuring three-dimensional objects. Soon after, in an unrelated deal, Apple acquired PrimeSense, the company that made one of the components for Occipital's scanning device.

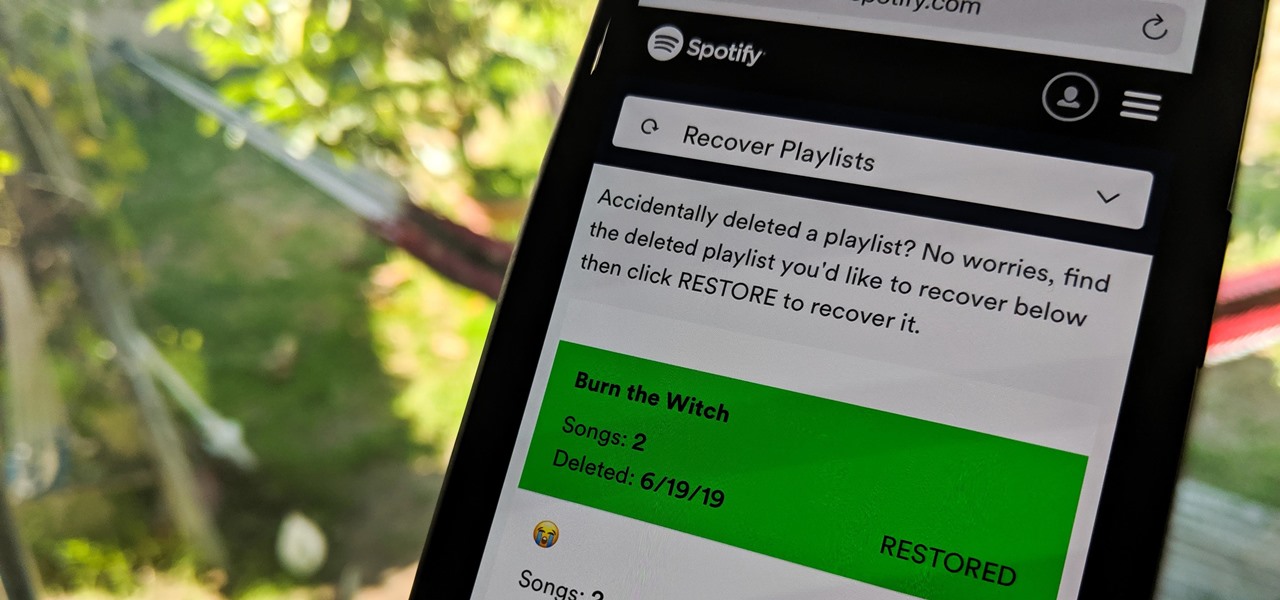
Absentmindedly or accidentally deleting your favorite Spotify playlist — which you spent hours or even days meticulously crafting — may seem devastating because there's no obvious way to bring it back. However, there is a hidden setting in the popular streaming service that can help you recover deleted playlists — you just need to know where to look.

Face ID does an excellent job with keeping your iPhone safe, boasting a million-to-one odds against unauthorized access when compared to Touch ID, which is 20 times less secure. However, it's far from being truly hands-free, as you still need to swipe up the lock screen once it detects your face to access apps. But if you have a jailbroken iPhone X, this issue can easily be remedied.

Switching phones has never been easier. Google backs up most of your app data on the cloud, which can then be restored onto your new phone. Sadly, Signal doesn't use this feature since it could compromise your security. Instead, Signal stores encrypted backups locally, requiring a bit of work to restore these messages.

After years of waiting, Microsoft has finally updated its industry-leading augmented reality device, the HoloLens.

Move over, cosmetics companies. The athletic footwear industry wants to be able to give their customers the opportunity to try on products in augmented reality as well.

The iPhone X introduced the world to Face ID in 2017, and now, every new iPhone uses Apple's biometric security system instead of the old Touch ID. It's more secure than fingerprint scanners and it's even more user-friendly. True, it's not without its faults, but at least one of the biggest problems can be fixed.

Two-factor authentication (also known as 2FA) adds a necessary additional layer of security to your username and password in many important apps. On Instagram, 2FA requires you to confirm it's you attempting to log in, with a special code sent to you via text message. Enter the code and you're in ... but what happens when you need to log in and don't have access to your phone?

To hack a Wi-Fi network, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, but you can quickly test one you already own for compatibility, and you can verify that the chipset inside an adapter you're thinking of purchasing will work for Wi-Fi hacking.

Cross-site scripting can be one of the easiest vulnerabilities to discover, but to be successful with this type of attack, it is essential to learn how to get past filters. In the previous guide, we explored some ways to do this, such as abusing attributes and event handlers and tricking the application into accepting unusual characters. Now, let's take a look at more techniques used to defeat filters.

Huawei has been in a losing battle with the US government for around ten years, with the last year being the spike of Huawei's problems. Because of US pushback against some Chinese-based smartphone manufacturers due to security concerns, Huawei is hoping to limit its dependency on US-based companies, and recent rumors of Huawei's very own mobile operating system may be the first step.

If you're hungry for pizza and ordering from Domino's in Australia, you can now see what your pie will look like in augmented reality before placing your order.

This time last year, we got our first taste of what mobile app developers could do in augmented reality with Apple's ARKit. Most people had never heard of Animojis. Google's AR platform was still Tango. Snapchat introduced its World Lens AR experiences. Most mobile AR experiences existing in the wild were marker-based offerings from the likes of Blippar and Zappar or generic Pokémon GO knock-offs.

Starting in iOS 11, Apple introduced a QR code scanner for iPhone that's baked right into the Camera app, reducing the need for a third-party scanner. However, not everyone knew it existed, so a lot of users were still using third-party QR code scanners. In iOS 12 and later, Apple addressed the issue, making theirs much more visible, as well as improved QR code scanning in general.

Yesterday, I talked about what I think is the most immediately mainstream-friendly app on the Magic Leap One is (Screens), and now we'll touch upon the runner-up: Helio.

We've seen all the Magic Leap One glamour shots, and we've even shown you a bit of what it looks like to view augmented reality on the device. But there's something else us super geeks appreciate more than anyone else: the grand unboxing!

Locating and abusing files containing unsafe permissions is an easy and surefire way to elevate shell privileges on a backdoored macOS device. This time around, we'll be more aggressive and attempt to phish a user's login password by prompting a convincing popup message merely asking the target for their password.

For the second time in a row, Apple pushed out a new iOS 12 developer beta on a Monday, and for the first time this round, they've done it only one week after the last one. While the August 6 release of iOS 12 developer beta 6 doesn't contain a wealth of updates, there are still a few things you'll want to know about.

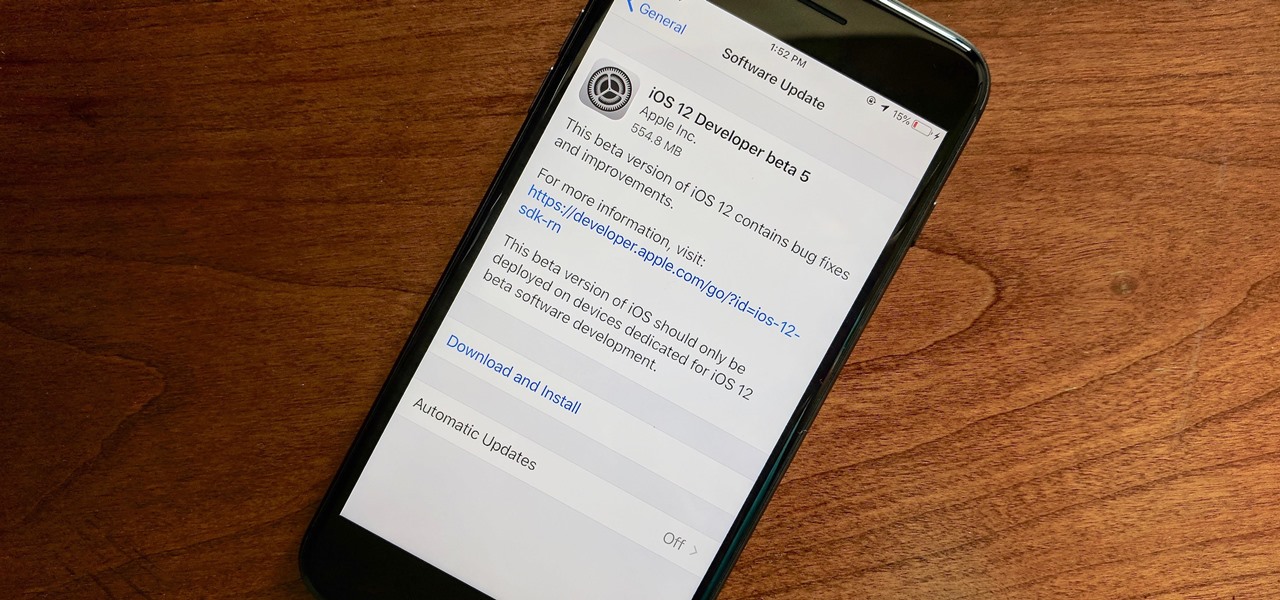
Apple released the fifth developer beta for iOS 12 on Monday, July 30, only 13 days after the release of dev beta 4 and 12 days after public beta 3. Until this release, Apple kept a consistent two-week schedule for developer beta updates, so we were a little surprised to see this one drop one day early.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

Whether you like to go swimming or jump in a hot shower with your Apple Watch on, the chance is pretty high that you'll get water inside its speaker. If you're a big runner, even sweat can get inside there. While there is no way to prevent water from getting inside your Apple Watch's speaker, there is an easy way to get it out so that your muffled speaker sounds brand new again.

Right on the heels of the iOS 11.4.1 beta 3 release, Apple pushed out iOS 12 beta 2 to registered developers on Tuesday, June 19. Public beta testers received the same version, labeled as iOS 12 public beta 1, six days later on Monday, June 25. Last year, the iOS 11 public beta opened up just five days after the release of iOS 11 developer beta 2, so iOS 12 is pretty much right on track in that regard.

If you cover a particular area in tech long enough, you develop certain pet peeves, and one of mine happens to be devices that attempt to keep us wed to the Google Glass style of augmented reality. And while I remain mostly uninterested in such devices, one of these products recently earned my admiration and might work for you, too, under the right circumstances. It's called the Golden-i Infinity.

While privacy and security are cornerstones of Apple's ecosystem, your iPhone isn't bulletproof. Creating a strong passcode will protect you from most threats, but there exist tools that can break through even the toughest passcodes via the Lightning port. Luckily, Apple has implemented a new security feature to disable your Lightning port and keep your data safe and secure.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

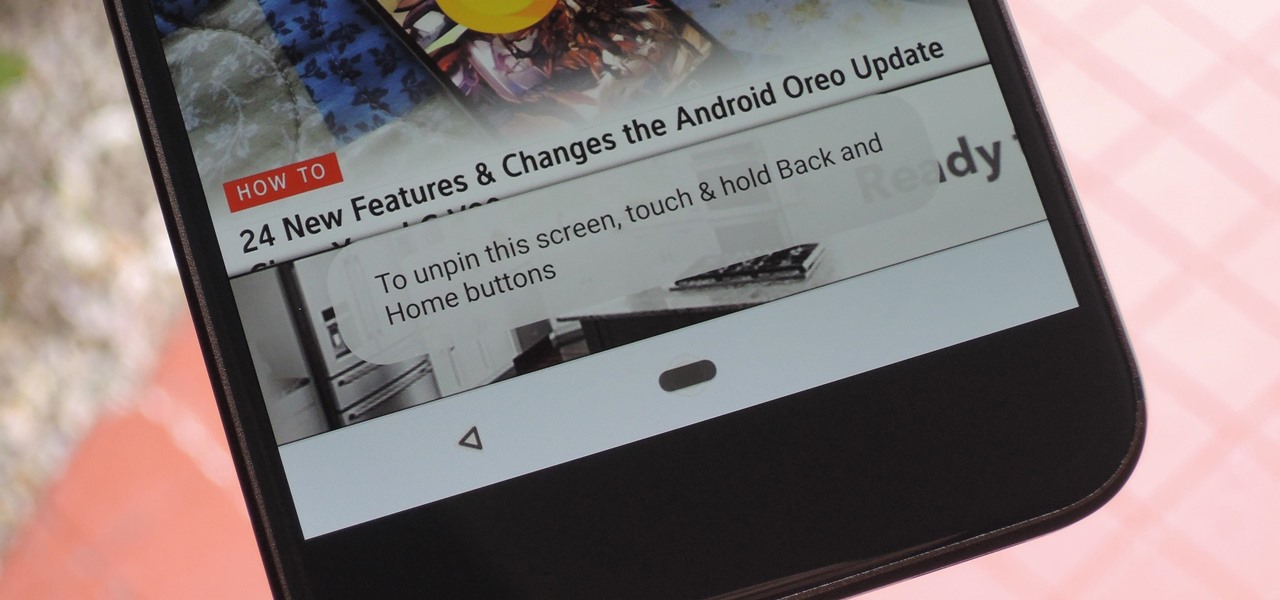
Screen pinning is a fairly unknown feature despite the fact that it's been around since 2014. It's a helpful security tool that limits access to your device to only one app — perfect for those times when someone asks to borrow your phone. While previous versions kept this feature exactly the same, Android 9.0 Pie's new multitasking UI changes the way it works.