If you're not impressed with the current crop of AR content, and you're worried this may put a damper on the industry's growth, these stories should give you cause for some optimism.

While it has been slower to arrive than a walker limping through thick Georgia mud, location-based augmented reality game Walking Dead: Our World finally has a confirmed launch date: July 12.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

At present, consumer-facing augmented reality is a mobile world, and Snapchat is making money on it through advertising partnerships.

China-based virtual reality headset maker ANTVR has decided to enter the augmented reality space, and to do so it's launching its headset on Kickstarter. The company claims that its new Mix AR device has a field of view that surpasses the Meta 2, the HoloLens, and others within a smaller form factor and at a fraction of the price. But there's a catch.

Its official: On May 8, T-Mobile finally released the Android Oreo update for the LG V30 and V30+. Now, every major US wireless carrier has pushed the update. For me, this update is a big deal. Not only does Android Oreo bring some new tools and features, but LG has also included a few additions as well.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

Beginners learning brute-forcing attacks against WPA handshakes are often let down by the limitations of default wordlists like RockYou based on stolen passwords. The science of brute-forcing goes beyond using these default lists, allowing us to be more efficient by making customized wordlists. Using the Mentalist, we can generate millions of likely passwords based on details about the target.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

Before The New York Times brought augmented reality to its iPhone app, the only way Winter Olympics fans could get this close a view to the world's best athletes would be to acquire a press pass.

With the Super Bowl just days away, it seems appropriate to draw parallels between football and the professional sport of technology business, or, more specifically, the augmented reality segment.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

Between Renault Truck's testing of the HoloLens in factories and BMW promoting its newest model through Snapchat, the auto industry is hot for augmented reality to improve internal operations and engage consumers.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

A Russian augmented reality startup wants the next frontier in real estate to be augmented reality estate.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.

The staff at Next Reality News is legitimately excited about the prospects that Google's ARCore could bring not only to smartphones and tablets running Android, but also to Android-based hardware such as smartglasses.

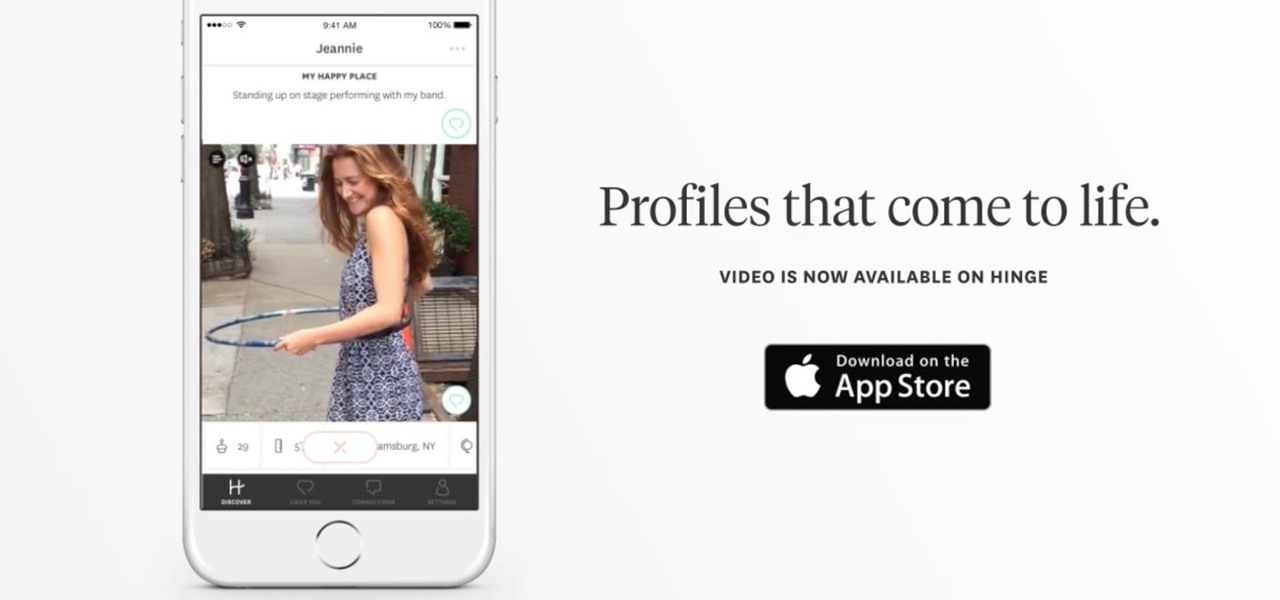
It seems we've come full circle in alternative dating routes. Just like a long time ago when people were able to go to matchmakers and watch videos of potential matches, the dating app 'Hinge' is now allowing you to add videos to your profile.

It seems that mobile app developers are constantly coming up with new ideas to apply augmented reality, with Apple's ARKit promising to increase adoption in apps exponentially.

It's no secret that devices leak data, but sometimes they do so in ways you may not expect. Your phone, laptop, printer, and IOT devices leak Wi-Fi information that can (and is) used to track you.

In our first part on software-defined radio and signals intelligence, we learned how to set up a radio listening station to find and decode hidden radio signals — just like the hackers who triggered the emergency siren system in Dallas, Texas, probably did. Now that we can hear in the radio spectrum, it's time to explore the possibilities of broadcasting in a radio-connected world.

Things aren't looking good for Uber after its driverless experiment in Pittsburgh soured relations with local authorities. Surprised? Me neither.

Verizon launched the $80 unlimited prepaid plan this week and we've found that it actually isn't as limitless as they would have you believe.

The drama continues! In the latest installment of the feud that has rocked the driverless vehicle industry, Waymo is now accusing Uber of withholding a secret LiDAR device.

Sony has upped the ante for the promotion of Smurfs: The Lost Village, which was released on April 7 in the US, with a mixed reality experience via Microsoft's HoloLens.

Google has a new smartphone, and if you own a TV or a computer, you've almost certainly heard about it. The ad campaign for the Pixel and Pixel XL is approaching iPhone levels of omnipresence, as Google has reportedly spent over $3.2 million on marketing, with that number expected to skyrocket in the coming months.

You're all kale-d out, you've had it up to here with golden milk, and you're on the prowl for the next superfood. Well, get ready for some unicellular goodness: the next superfood is an algae named Spirulina, also known as Blue Majik. (Kudos to the marketing exec that came up with that, am I right?)

We all got a little jealous of the iPhone 7 Plus's dual-lens camera during the Apple Keynote in September. It's okay, you can admit it. But just because your Android doesn't have two lenses doesn't mean you can't recreate the fun bokeh effect of the iPhone's now wildly popular Portrait Mode.

Automated bots are growing on Facebook Messenger, and while they can be helpful, they also have the potential to get very annoying, very quickly. That's because these bots are enabled by default to send you "sponsored messages," or, you know, spam.

Cellular carriers like to nickel-and-dime us out of every bit of money they can feasibly justify, so as consumers, we owe it to ourselves to make sure that we're getting our money's worth.

A little-known company in India is making waves after announcing that it will sell an Android 5.1 Lollipop smartphone for less than $4 (or, more precisely, 251 rupees). The Freedom 251, from Ringing Bells, sounds almost too good to be true. Is that because it is?

Hello people again, I wrote my last post about crypto about 10 months ago, now I will introduce something not fresh for the science, but fresh for the people who wants to learn. In my http://null-byte.wonderhowto.com/forum/cryptography-0161538/ post of crypto concepts, there is just basics, today we will see something that targets wide concepts like Symmetric crypto, Public Key Cryptography, Hashing, Keys etc...

When you hand your unlocked iPhone to somebody so they can use the internet real quick, check out some cool photos, or do whatever, there's a possibility that they could snoop around where they don't belong. If you have some secret recipes, login credentials, intellectual property, or other sensitive information in your notes, you'll want to add some protection to them.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

Boxed brownie mixes advertise their convenience compared to homemade brownies—with only a few ingredients, they promise a moist, chocolatey crumb. However, these "instant" mixes still require fresh ingredients and a baking time that matches that of homemade brownies. When you're craving a chocolate fix but you're coming up short on eggs, oil, and time, don't despair: you can still make brownies using a can of soda. Two Different Methods, One Soda Required

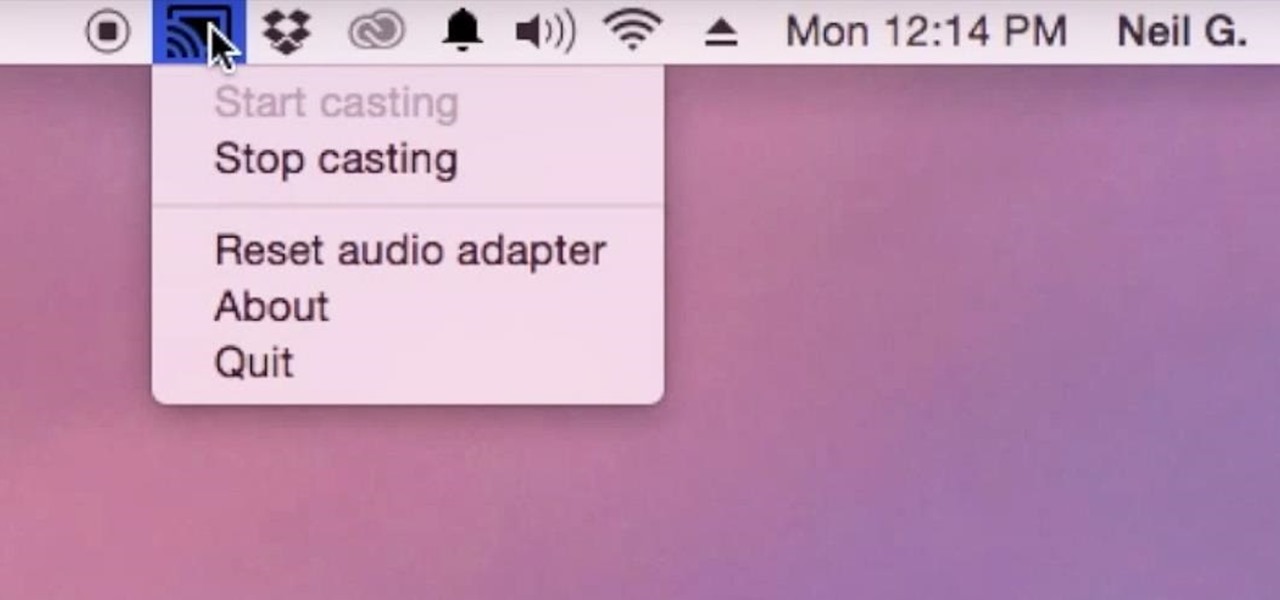
Although I know it will never happen due to Apple and Google's tempestuous relationship, I sometimes wish I could cast iTunes or Apple Music from my Mac to Google's Chromecast. When you don't have speakers to blast your music, the television is a great alternative to amplify your music.

This is a collection of various guides and tools available on the internet. Instead of searching for 1 you can easily find whaht your looking for here.

Ad blocking on Android usually requires root access, but a pair of new browsers based on the open source Chromium and Firefox builds are looking to change this.

Welcome back, my tenderfoot hackers! As hackers, we often are required to get past antivirus (AV) software or other security measures. To do so effectively, we need to have some understanding of how AV software works. In this tutorial, we will take a cursory view of how AV software works so that you can better strategize on how to evade detection by it.

My morning just doesn't start without a cup of coffee and an incredibly hot shower. There's nothing better than sloughing off sleep with a dose of warm, cleansing water. Except, as scientists are pointing out, our habit of showering daily isn't exactly the healthiest choice. Though it feels great, if you have a shower-a-day habit like I do, you're showering all wrong.