Do your children know how to get out of the house in the event of a fire? The best way to prepare your kids for a potential home fire is to have fire drills at your home. This program will offer ideas on how to make fire drills fun for everyone.

Did you know that drowning is the second leading cause of death for children under the age of 14? I worked as a lifeguard and swimming instructor when I was younger and I have seen firsthand too many close calls with kids around water. This program is about basic water safety for children.

This tutorial uses vectors to show you how to create a gel (or glassy) button in Adobe Illustrator. Vectors are an important component of Illustrator and allow for the most flexibility with other programs.
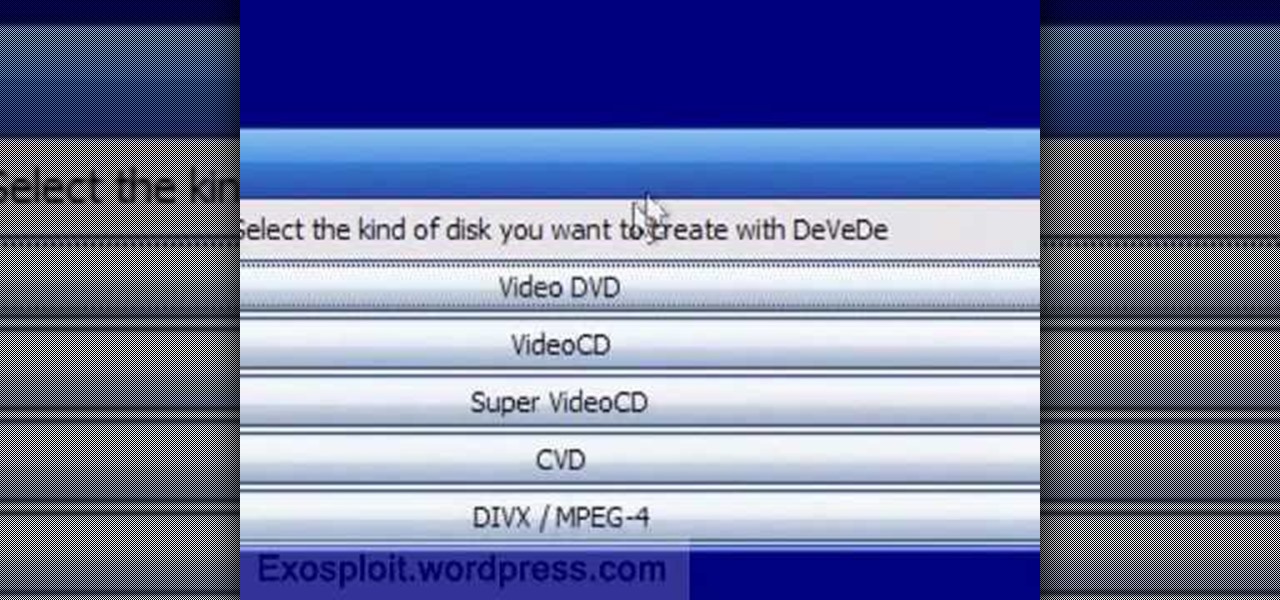
This video explains how to burn DVDs that will play on a standard DVD player in Windows. The programs needed to complete this project include IMG Burn and DeVeDe which has been modeled for Windows. The final burn product created with this program will allow the DVDs to play on computers and actual DVD players. The first step is to hit open to select the file you wish to burn. You must then select burn ISO or Bin file in IMG Burn or DeVeDE. You can then select a title for your burned disk leav...
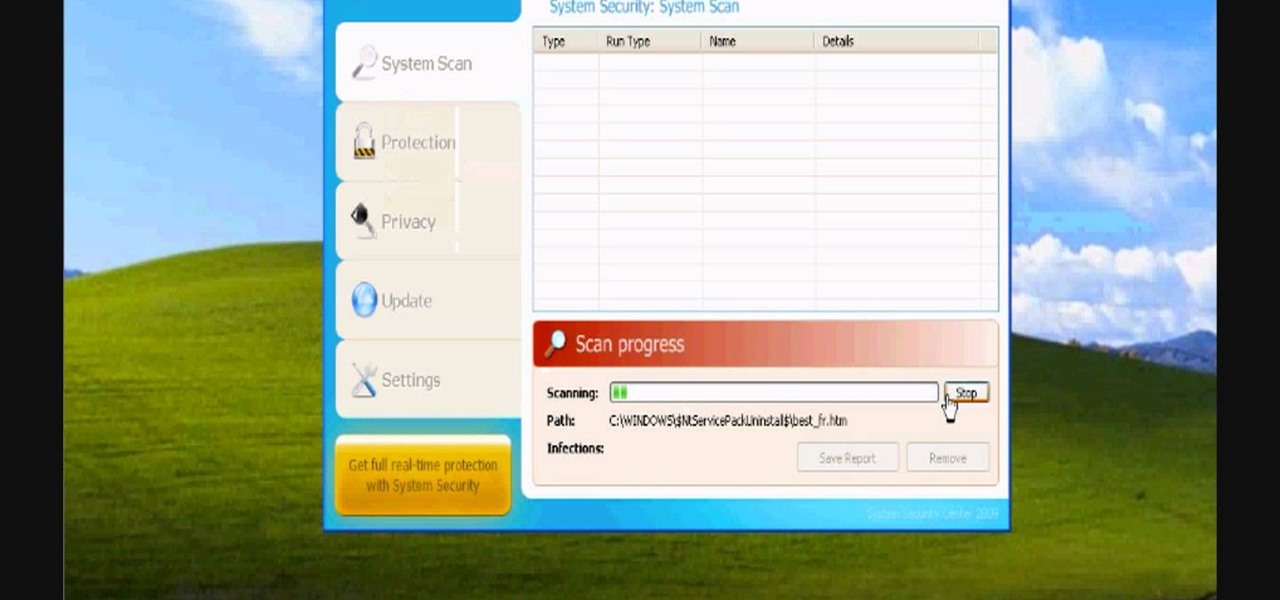
In this video, we learn how to avoid getting infected by "system security". Make sure you avoid the website that show the System Security Anti-Virus. Once you install this onto your computer it will pretend like it is doing a scan, but in reality is hurting your computer. It will pop up showing you that you have problems on your computer, but the alert will never go away. If you delete this, it will just re-install on your computer instead. To do this the correct way, you need to go to your m...
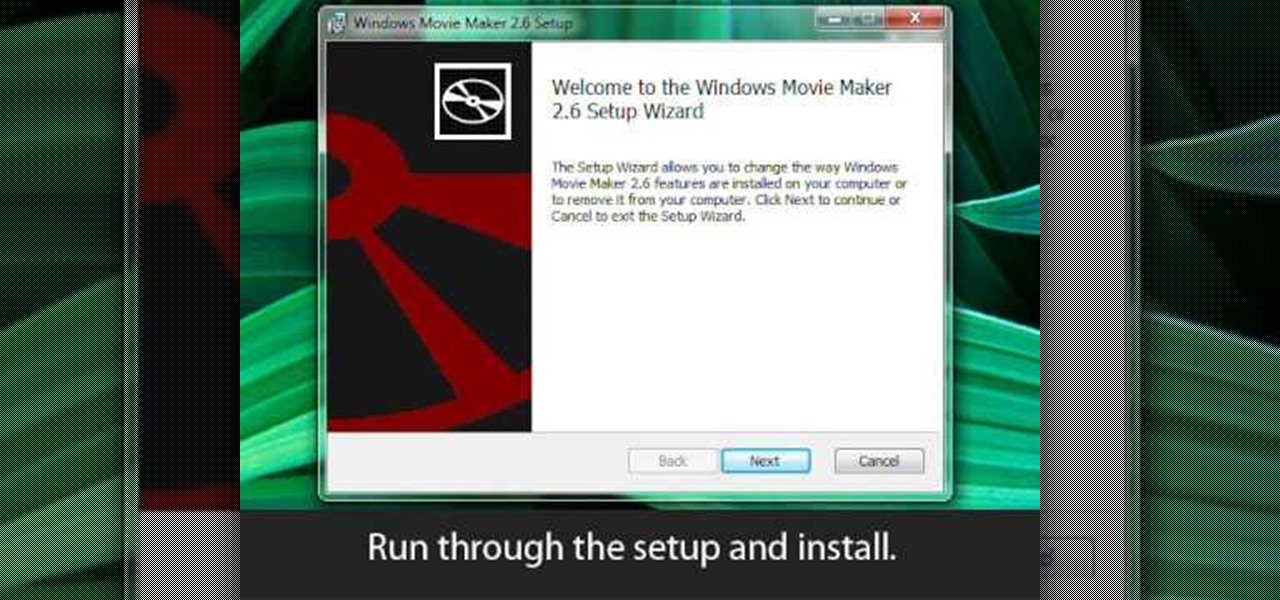
This video tutorial belongs to the software category which is going to show you how to install Windows Movie Maker on Windows 7. Windows 7 RC does not come with Windows Movie Maker. However, you can download the movie maker from Microsoft site that will work with Windows 7 RC. Go to Microsoft Downloads, find the link for the Windows Movie Maker download and download it. Then run the exe file and follow through the steps to set up and install the program. After installation, the program can be...

Initially you computer performs at its maximum speed when you install a new operating system. But as time progresses and you install more and more applications the computer slows down due to the various changes in configuration and other settings. So you have to tune up your PC regularly to maintain its performance. Alternatively you can also increase the memory or use a better processor. But even then if you don't optimize your operating system you will face the problem once again. So go to ...

Daemon Tools Lite is a program that helps you install a virtual drive, thereby loading an .iso image into the drive to be used at all times with ease. Download DAEMON Tools Lite by searching on the google. After you download, install the program successfully. This may take some time as the virtual drive needs to be installed. Once installed a small icon appears on the bottom right corner of the screen on the task bar. Right click on the icon and go to ‘virtual CD/DVD ROM’. Select a drive ...

In this video tutorial, viewers learn how to sync contacts between a Mac and Windows mobile device. Users will need to download and install the program, Sync Mate 2. Begin by opening the program and connecting the device to the computer. Under Synchronization in Plug ins, check the Contacts box. Then select the Synchronization direction, Surname and name order and select which contact groups to sync. Then click on Delete all contacts and select to delete the contacts on the computer or mobile...

In this how to video, you will learn how to make custom screen savers and wallpaper for your Mac for free. First, download the SaveHollywood and Wallsaver programs to your computer. Install both of these programs. Next, go to system preferences and click on desktop and screen saver. Click the screen saver tab and select SaveHolywood. From here, click options and press the arrow button. Find a video that you want to use as a screen saver and click okay. Click test to see if it works out. Next,...

Have you ever wondered how to open a .ISO file without the need for the disk? Well with Daemon Tools, and this tutorial, you can learn just that. What you will end up doing is creating a virtual drive on your computer, and mounting the .ISO image onto that virtual drive. It's as simple as loading up the program, right clicking on the icon in your task bar tray, clicking on the empty drive, and mounting any .ISO image you like! In no time you'll be playing your favorite game, or program withou...

O0OMadMikeO0o teaches you how to activate Windows 7 RTM build 7600. For this you will need the program Windows 7 Toolkit 1.7 by Win7Vista. All you need to do is launch the program and check the box that says Activate Windows 7. After waiting 2-3 minutes, this version of Windows 7 will be activated. Note that this type of activation has an expiry date, so it's only a temporary solution. Before the end of that period, another tool or an updated version of this tool should appear that will solve...

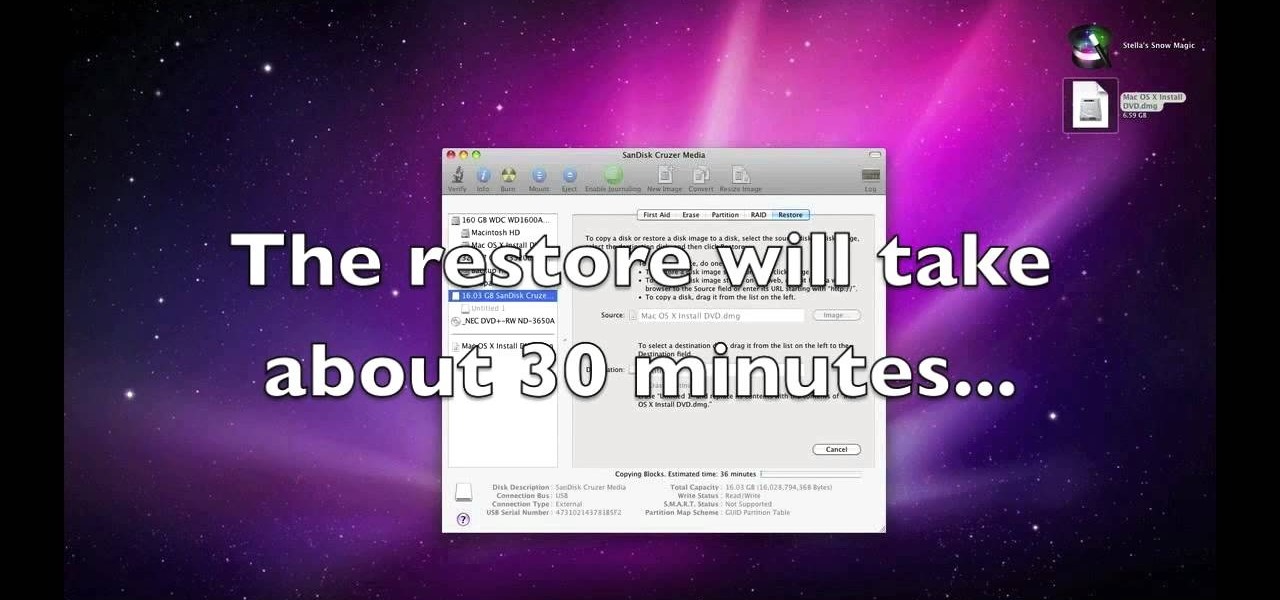
In this video you will learn how to Install Mac OS X Snow Leopard from a USB drive to windows. This does not include how to exactly download Snow Leopard but it does, however, show how to install it from the USB drive. Mahmood23 shows how you first setup your partition and how to restore your formatted USB. Once you've restored the USB, you will be able to install the program. According to Mahmood23, the restore process takes about 30 minutes. Once it's restored, your computer will be availab...

In this video tutorial, viewers learn how to play MKV videos on the PS3 using the MKV2VOB software. Begin by downloading the MKV2VOB programs from the link in the video description. Once downloaded, install it on your computer. Now open the program. Go the Configuration tab and change the setting to the same as the video. Then click on the Add File tab and select Browse under Source File. Find your MKV file and select Open. Then under Destination Directory, select where you want your file to ...

In this video the instructor shows how to choose options on a batch file. In a batch file if you write the command '@ echo off', the person running the batch file cannot see the commands being executed. You can use the 'if' condition to make the program execute either of two commands depending on the condition. While writing the if statements make sure that there is space between the 'if' and the '%' sign. If you write 'shutdown -t 30' command in your batch file, then the batch program when r...

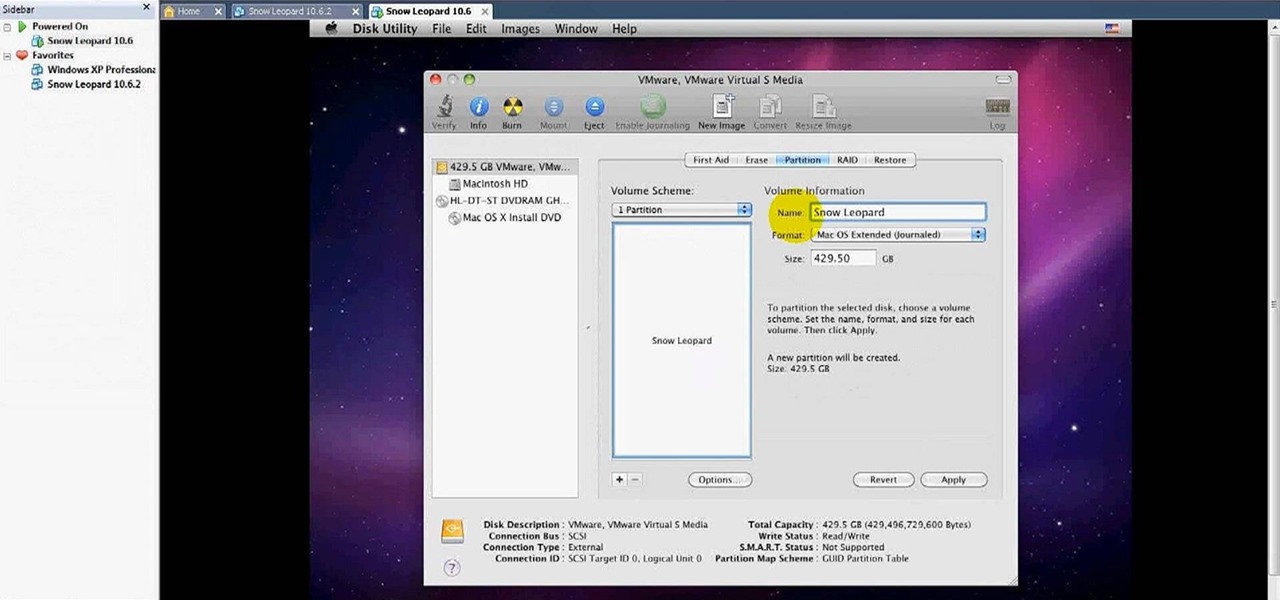
In this video tutorial, viewers learn how to install Mac OS X Snow Leopard in Windows PC using VMware Workstation as virtual machine. Begin by downloading the program from the link provided in the video description. ISO image is made especially for Windows PC users. Mac users can download the DMG file from there too. This is a full video guide on how to install Snow Leopard in Windows 7, XP, Vista using VMware Workstation and download all the software (VMware workstation, Mac OS X Snow Leopar...

This is an instructional video on how to make a logo in "Inkscape". This video is filmed from the desktop of gamerworld14 and includes oral instructions as well as a step by step guide shown in detail from the computer. In this video gamerworld14 helps you learn by using an example logo he used. This video includes everything from adding text to your logo, pictures, and resizing of the images in the logo. In this paint style program you can draw out your own images to add to your logo. In the...

A tutorial on how to recover lost files once deleted from the recycle bin. The program illustrated in the tutorial is "Restoration". To download "Restoration", go to SnapFiles. The tutorial advises viewers to stop whatever they were doing once they realize a file is missing. Because the file is simply marked as free space, it is still present in the computer's memory but easily overwritten. To recover the file, a user will simply need to know part of the file name (preferably an extension, fo...

On this YouTube video the user Vvistacomphelp shows you how to print screen and crop pictures. The first thing that the user shows is where the Print Screen button is located at on most keyboards so that you can press it on yours. The second thing is go to the start menu in Windows Vista and type in "paint" in the search box on the bottom left then open Paint under Programs. The third thing that is shown is how to make an image appear inside of the paint program so you can crop it. After foll...

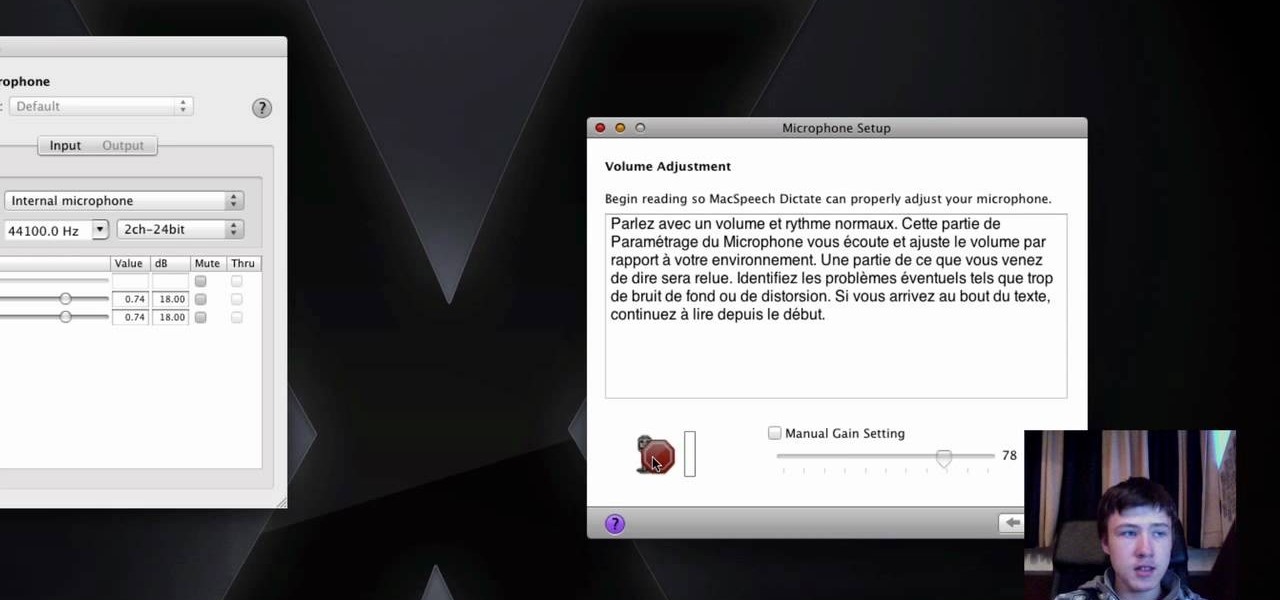
In this video the tutor shows how to use the Mac Speech Dictate with the built-in mic. Mac Speech Dictate is a program that you talk to and it writes for you. Its a dictation tool to which you can dictate and the application writes for you. The negative part about it is that it does not support built in microphone. This video shows how to make it change and work with the built in mic. To do this other than the MacSpeech dictate you will need the Soundflower tool. Soundflower is a really small...

Get MMS working on iPhone 3G, iPhone 3GS, MMS on 3.1 for AT&T. Step 1 : First of all, you have to update to 3.1.

Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than others, and a little Python could be used to brute-force any weak hashes to get the passwords they were created from.

After a long hiatus, we shall once again emerge from the shadowy depths of the internet to build an exploit. This time, we'll be looking at how to defeat a non-executable stack by using the ret2libc technique — a lean, mean, and brilliant way of exploiting a stack overflow vulnerability.

Ever since Google CEO Sundar Pichai took the helms of the world's most valuable brand, he has made it his mission to bring smartphones to lower-income communities. Born in India, Mr. Pichai has created several programs to address the needs of the Indian market, particularly the lower income families.

During our last adventure into the realm of format string exploitation, we learned how we can manipulate format specifiers to rewrite a program's memory with an arbitrary value. While that's all well and good, arbitrary values are boring. We want to gain full control over the values we write, and today we are going to learn how to do just that.

For a company who hasn't released a product and has a reputation for being secretive, Magic Leap sure has a tendency to make waves. Over the past few weeks, they've refreshed their website design, released an abstract YouTube video, and announced a partnership with Madefire to offer mixed reality comics on its device whenever it launches. Next, they are gearing up for another round of funding.

Uber's driverless car program lead has quit after just one year working for the ride-hailing company.
Hello everyone! This is my first attempt at a tutorial here. There are a couple great assembly tutorials here, and I wanted to toss my coin in the fountain.

Hello NullByte, it's mkilic! This time I'm here with the C.H.I.P from NTC. Although it is not too popular, the C.H.I.P is a brand new micro computer. It is very similar to the Raspberry Pi or Beaglebone Black. The key difference with this particular board is its cost and size. The C.H.I.P only costs $9 and measures 2.5 x 1.5 inches. In addition to this, the C.H.I.P has built in 802.11 b/g/n Wifi and Bluetooth 4.0. Considering these great specs, what could a Hacker use this for? Step 1: The In...

Hello there, reader! If you've clicked on this How-to then it means you are interested in learning some C programming or just generally curious about what this page has to offer. And so I welcome you warmly to the first of many C tutorials!

Task Manager got revamped quite a bit in modern versions of Windows. First introduced in Windows NT 4.0, it's become pretty popular among more advanced users. In Windows 10, Task Manager is not just a task manager anymore, it's also a system monitor, startup manager, history viewer, user controller, and the list goes on.

Programming is an essential thing in hacking/pentesting, and at times, I do not feel that it is being addressed enough here, at Null-byte. I understand that this is a forum dedicated for hacking, but I'll address some of the stuff I feel is muy importante about programming. I am not a professional programmer, but I do have experience and I do want to share some of the stuff professionals have taught me.

Apple just showed off iOS 9 and its new features at WWDC 2015, including multitasking support for iPads (finally!), a new Low Power Mode to save battery, local area search and transit directions in Maps, a highly improved "Proactive" Siri, a better Spotlight search, new apps, and so much more.

Hi everyone! In the previous part of this series, I introduced one way to hijack a program's execution flaw, though I only showed you how to crash the program and left you with a little mystery to solve. Today we are giving the solution of that and then introducing shellcode usage and remote command execution.

Hi everyone! Last time we finished analyzing the assembly representation of our vulnerable piece of code (have I ever told you it is vulnerable?). This time we are going to introduce some fundaments about exploitation by demonstrating how to crash a program's execution. If that sounds lame, next time we will see how this crash can in fact be useful to control the program's execution, achieving remote code execution!

When it comes to getting your computer and smartphone to work well together, there's no service more robust and capable than AirDroid. For years, it's been the go-to tool for users looking to transfer files between their devices or access contact lists and call logs from their computer.

Apple announced the successor to Mac OS X Mavericks at their Worldwide Developer's Conference 2014, and it's called Yosemite. Named after California's Yosemite National Park, it will be available as a free upgrade from the Mac App Store for everyone this fall.

It's officially the holiday season, which means everyone will soon be traveling home to spend time with loved ones. And anyone who has any knowledge whatsoever of computers knows what else that means—family members left and right asking you to fix their various technical woes.

As a former English major, I have a love/hate relationship with many books. And when I saw that this NFC-enabled charging dock project included a little book mutilation, I was suddenly more interested. Now, for those of you who have nothing against books, this is still a great project to add some style to your tech devices.

In this article, I'll be continuing my series on microcontrollers. If you haven't read part one, I'd recommend heading over there and reading it!