Faraday Future's all-electric super sports car concept attracted a lot of attention at CES earlier this year, but now it is struggling to replace key driverless engineers and program directors who left the company amid its recent financial troubles.

Lyft officially laid its stake in the ground to develop driverless fleets following its Friday announcement, but how fast it is catching up to ride-hailing competitor Uber's driverless initiative remains to be seen.

Oh, Uber. It's not often to hear your name in the news and have it mean something good. You're being sued, you're crashing, your driverless program is falling behind. But I have to hand it to you; when the world is crumbling around you, you continue to fight against it. You've even made it to Canada.

Mercedes-Benz's parent company, Daimler, announced their intention today to put self-driving taxis on the road in three years or less in a partnership with Bosch.

The big Waymo versus Uber trial isn't scheduled until May, but the heat between Uber and Waymo is rising fast; Waymo wants Uber's driverless trials shut down by a court injunction, unless ex-Google employee Anthony Levandowski testifies in court.

Gaining access to a system is always exciting, but where do you go from there? Root or bust. Sure, a compromised host is a great way to run a botnet, or do some other boring, nefarious thing—but as hackers, we want root. We also want to take the easiest path possible, search out low-hanging fruit, and exploit them. SUID programs are the lowest of the low-hanging fruit.

Hello people, I'm back for Part-3. In this part, as promised, we are going to create a client program and then we are going to test it with our server program made in Part-2.

It's been a while since I wrote up an article for this series but I did say that I'd be covering some WinAPI. So if you're interested in programming for the Windows platform, hop aboard and follow along.

We knew it was coming eventually, but this is a bit out of left field—early builds of the next version of Android have been released almost two months ahead of schedule. Android N, as it's being called for now, is already available for the last two generations of Nexus devices, though it's just an early preview build for now.

Welcome back to another episode of Java Tutorials, In today's tutorial, we'll be learning about what methods are, proper syntax when writing Methods, and why they are beneficial in a program's code.

I saw many people asking for a Tutorial about writing their own Remote Administration Tool, so I now introduce you in a basic kind of RAT. This program is not for real use, but for learning how you could write this kind of tool. It will be basicly coded and not very refined. I used Python 3, so you have to install it if you want to use this program unchanged. Also this RAT is for Windows and almost all features won't work under Linux.

Welcome hackers. Hackacademic.RTB1 is vulnerable machine for training our skills.This machine can be download from free from here. There is many tutorial how to hack these machine but i did always be my self.

The digital pen on the Surface Pro 4 and Surface Book is an indispensable tool for serious note-takers and artists alike.
Welcome back Hackers\Newbies!

There are a lot of great tutorials on Null Byte using Python to create backdoors, reverse shells etc, so I thought it might be worthwhile making a tutorial on how to convert these python scripts to exe files for Windows victim machines.

For those unwilling to wait until the Fall for the official release of Apple's latest Mac OS X, El Capitan, you can sign up for the public beta today and get it sometime this summer. If that's still not soon enough for you, there is a way to get it on your Mac right now.

Hi nullbytes! I've been recently reading the whole Linux Basics for the Aspiring Hacker series and felt like it was missing some stuff I know, so I felt like sharing it with anyone who might find it useful too.

Just a few days after unveiling the Apple Watch and pushing iOS 8.2 to their current products, Apple has, for the first time ever, made a beta version of their mobile OS available for the public to test out.

Hello my fellow hackers, Welcome to my republished revision of the ruby programming language, Part 1.

Welcome back, my fledgling hackers! In an earlier tutorial, I introduced you to probably the most popular scripting language for hackers, Python. To become a professional hacker, you need to have some scripting skills and Python is a good choice if you want to master just one. In this latest guide, I will expand your background in Python and offer you a tidbit of Python code to whet your appetite for all of the hacking to come.

This video shows top 10 useful tricks in windows 7. This video includes window key application, inserting program or folders in start menu or task bar, enabling or disabling windows7 features, notification area customization, reliability history etc. These tips will help you to operate windows 7 more efficiently. So please watch the video.

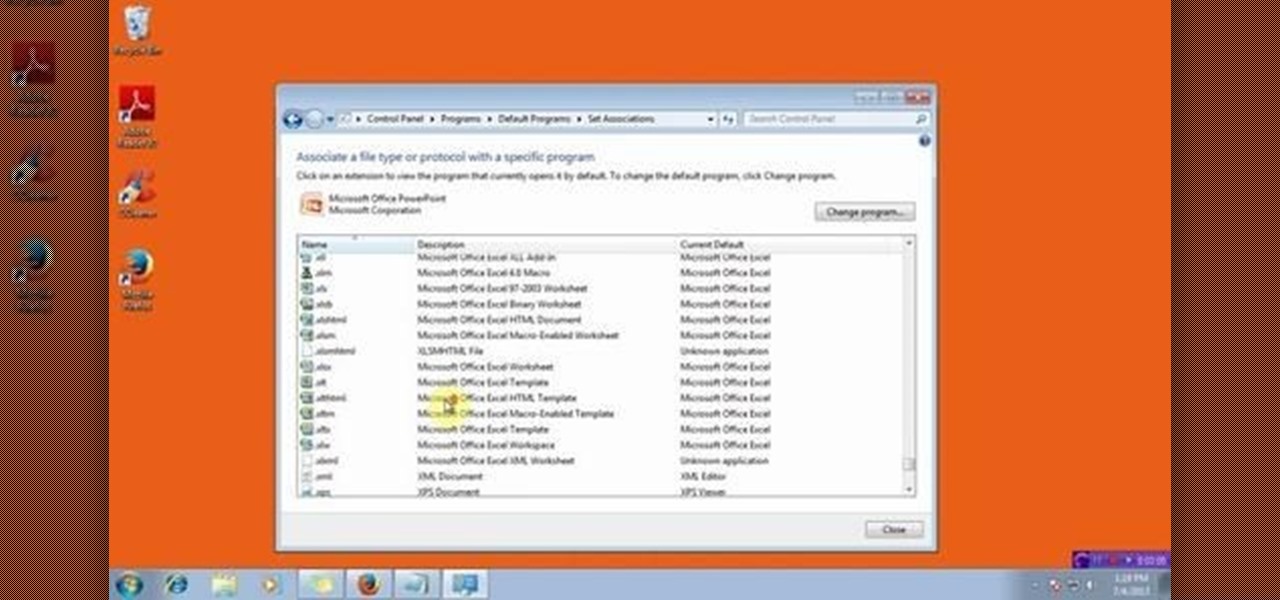
This video will show you how to change the default program for a Specific File Extension in Windows 7.

In this how to video, I discuss three different exercises that have really helped me to tone my waistline. Although you cannot specifically target different fat deposits while dieting, it is still important to perform these exercises to give your core and waist that aesthetic look. These exercises have given me great results, but a solid diet and a good training program is also extremely important to sculpting your body. Enjoy!

Assuming that you're not going to knit a sweater and celebrate New Year's Eve with Ryan Seacrest and Jenny McCarthy on ABC's “New Year's Rockin' Eve," it's a pretty safe bet to say that you're probably going to consume alcohol—a considerable amount of alcohol.

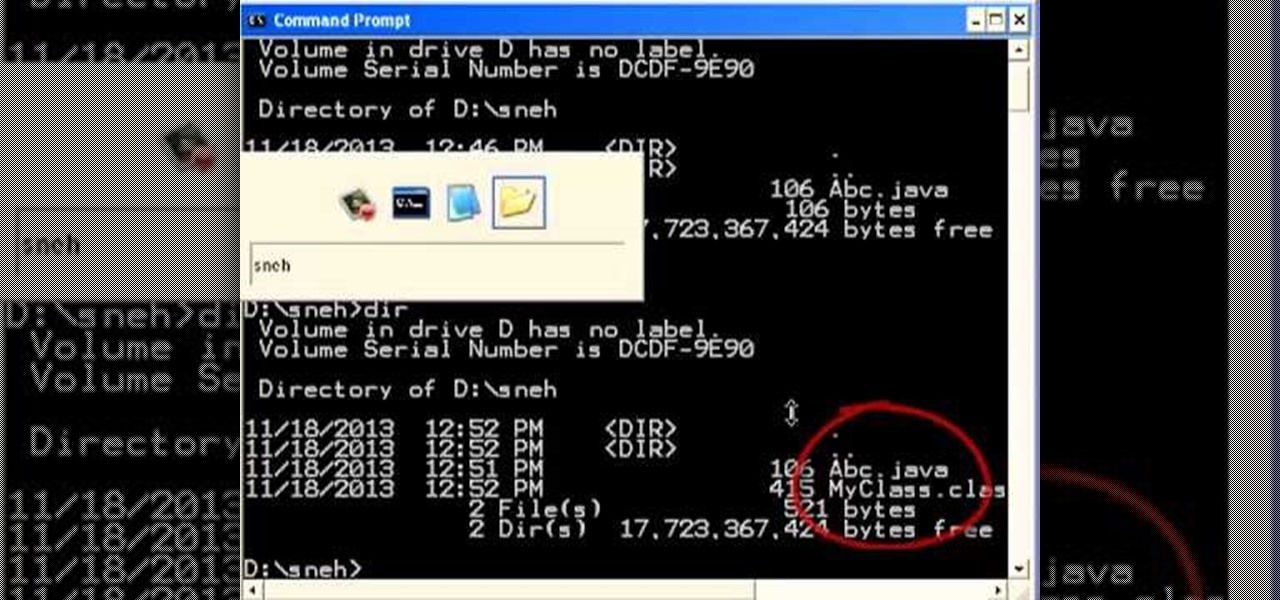
we will learn here, how to write a class, what makes the class to be executable, how to compile the class, what the thing should be kept before executing our java class.

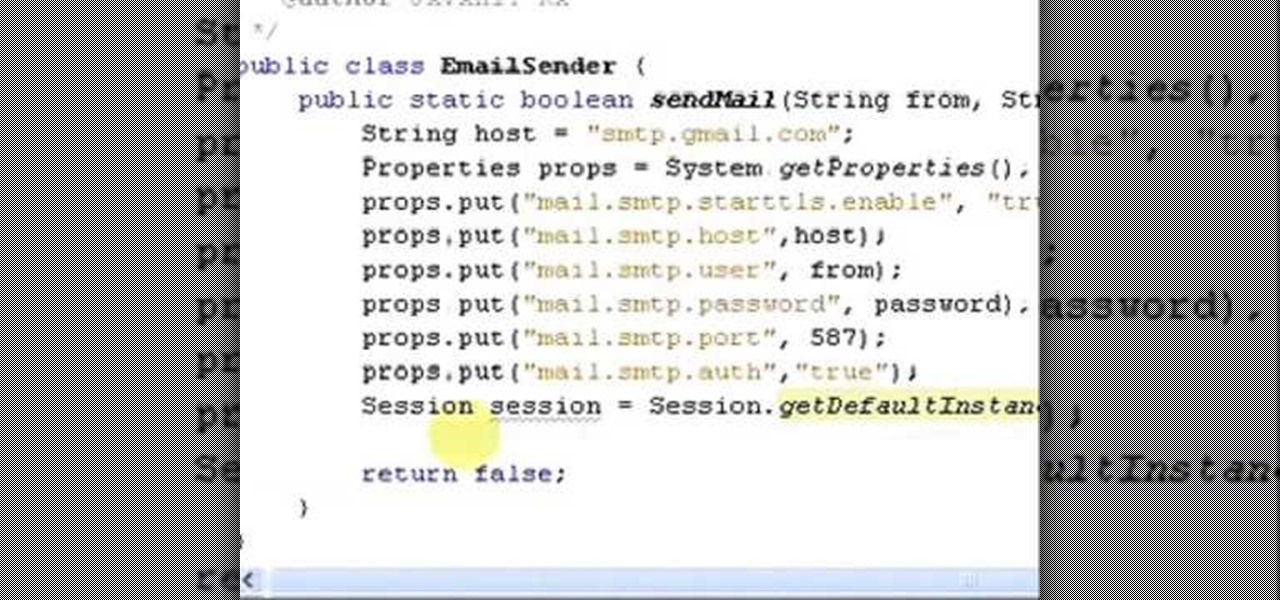
It uses JavaMail API, NetBeans IDE 7.0.1 First download the JavaMail API as shown in beginning of the video then follow the video to send email dynamically from your Gmail account. No need to open your inbox.

For the most part, Xbox Live is amazing, but there is one thing that has been annoying for pretty much everyone, to say the least. Microsoft Points.
When programming an Excel-file with links between sheets and assorted macros for whatever is needed you may want the file to behave as a program so that users can not access the ribbon even by double-clicking on the top bar. Protect the code from being accessed by pressing alt-F8 or alt-F11. Make sure you can run the macro show_sheets_and_ribbon () from the opening sheet before continuing to step 3

Apple is widely known for keeping a tight grip on iOS, disallowing open-source and third-party downloads. While there are many reasons for this, the three most frequently referenced are quality control, malware prevention, and of course—money.

In this web design tutorial we will show you how to protect yourself from losing your work just in case the program malfunctions, computer crashes or you accidentally forget to save document and so on. I highly recommend you utilize this Web Design Tutorial especially if you are working on large websites for clients.

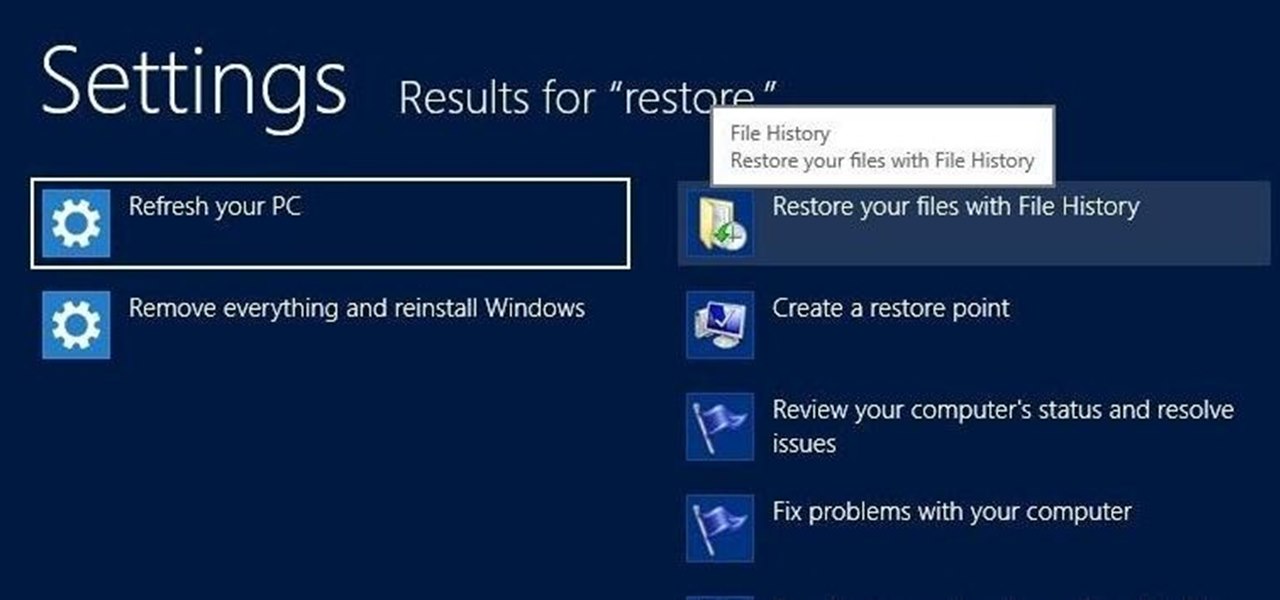
There is nothing worse than losing valuable information or programs on your computer. And if you've ever accidentally deleted a file or document, you know how agonizing that entire process can be.

I see that there are a lot of people that want to install and try the Aircrack-ng program for wireless auditing. But have problems because their Linux knowledge isn't that great. This How-To video tutorial explains step by step exactly what you have to do. No loud background music.

I recently wrote about Twitter's super now app called Vine, which lets people create 6 second video clips that can be embedded in a tweet. Those videos have their own proprietary extension, but if you want to turn those 6 second videos into an animated GIF, you can now do so thanks to developer Esten Hurtle, who created VineGifR, a seamless way to transform your (or someone else's) Vine movies into GIFs.

Being able to run mobile apps on a computer is nothing new. Maybe you don't have a mobile device, or maybe you just like seeing the apps on a larger screen. Whatever the reason, with programs like Bluestacks, you can use your laptop to Instagram, play Angry Birds, and run countless other apps made for smartphones.

Like most new things, the Start Screen in Windows 8 has its adorers and detractors, but either way you slice it—it's here to stay. I'm still getting used to the Start Screen, so I'm not sure if it's a love or hate feeling yet, but I do know one thing—I want my own background!

Thousands of Android users have been disappointed to learn that getting the latest firmware update isn't as easy as it sounds. Some really popular phones like the Samsung Galaxy S III just started getting the Jelly Bean upgrade, with the update continuing to roll out over the next couple of weeks overseas. All of the stateside S3 users will have to wait even longer for Android 4.1.

Archive files are great for portability and saving space, but a lot of people don't know they can also be encrypted. There are a lot of archiver programs out there, but most of them can open a file that's been encrypted using other software, as long as you're using a recent version.

We all expect a little something on our birthdays, so why should those expectations drop when we are talking about our gaming systems? Microsoft has started handing out birthday gifts to its Xbox LIVE Gold members with their new MyAchievements rewards program. Those eligible for the gift will automatically receive the offer on their dashboard. To be eligible for the free gift, you must be:

As if you needed another reason to lock down your Facebook profile, the company's sketchy new partnership with data mining firm Datalogix is geared towards giving advertisers more information on what you're doing—even when you're not online. It's just not enough that they can target ads based on your preferences, now they want to know how those ads are influencing your buying habits in the real world.