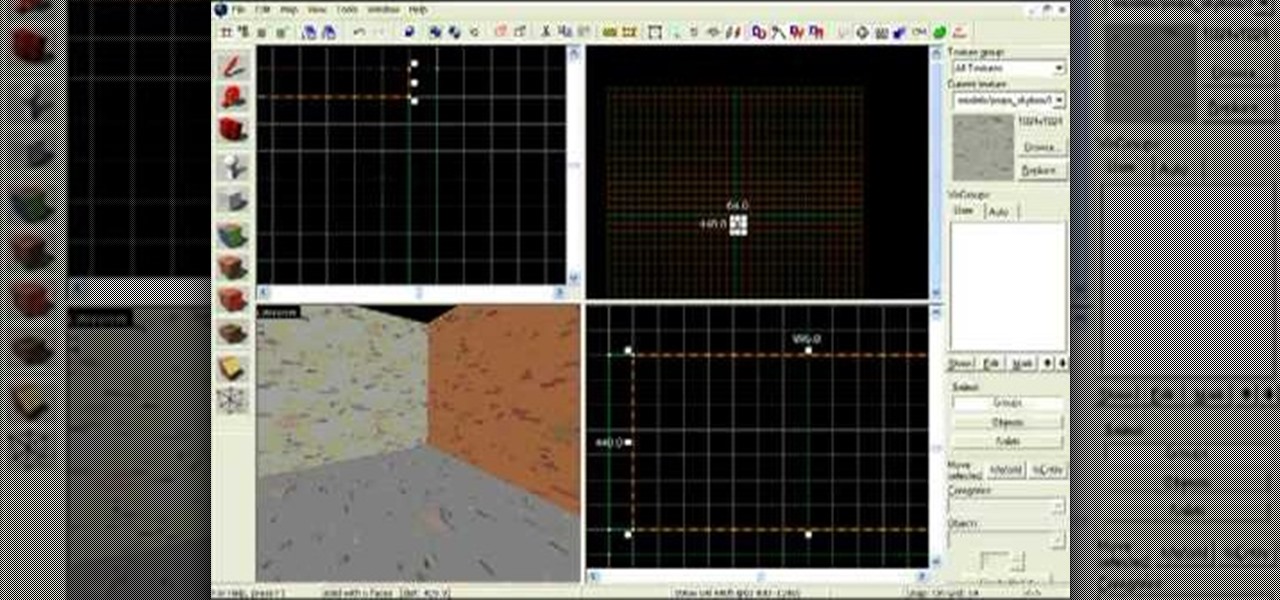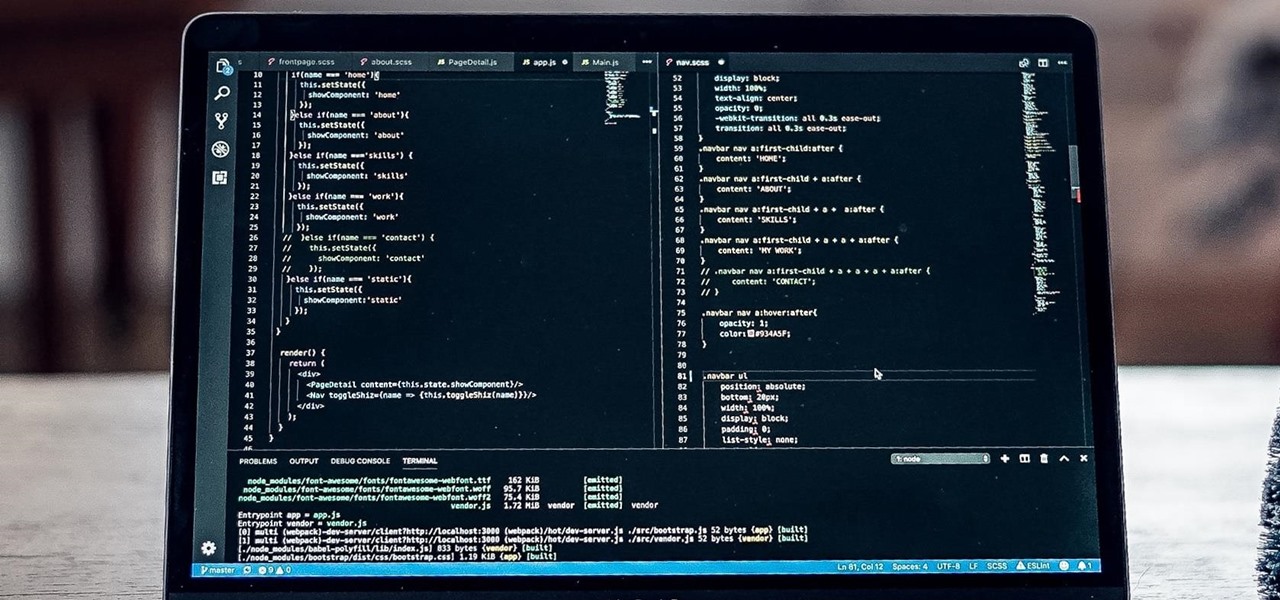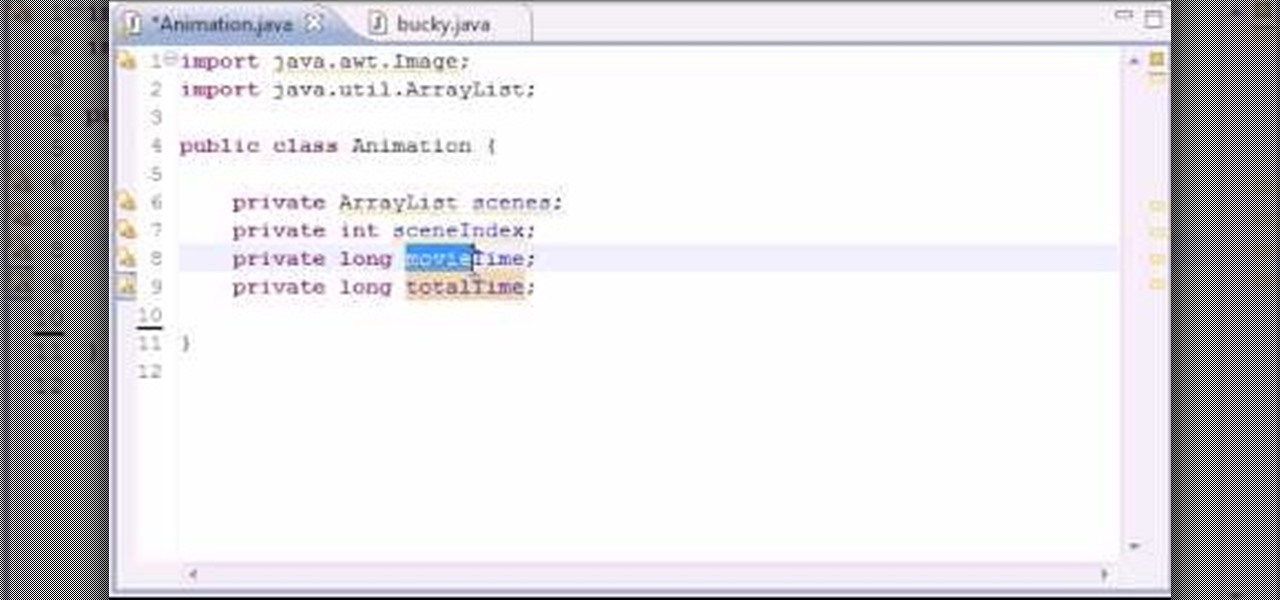
Want to write Java games and applications but don't know beans about object-oriented programming? Never you fear. This free video tutorial from TheNewBoston will help you on your merry way to accomplishing just that. Specifically, this lesson will demonstrate how to make a simple animation loop. For detailed instructions, watch this programmer's guide.
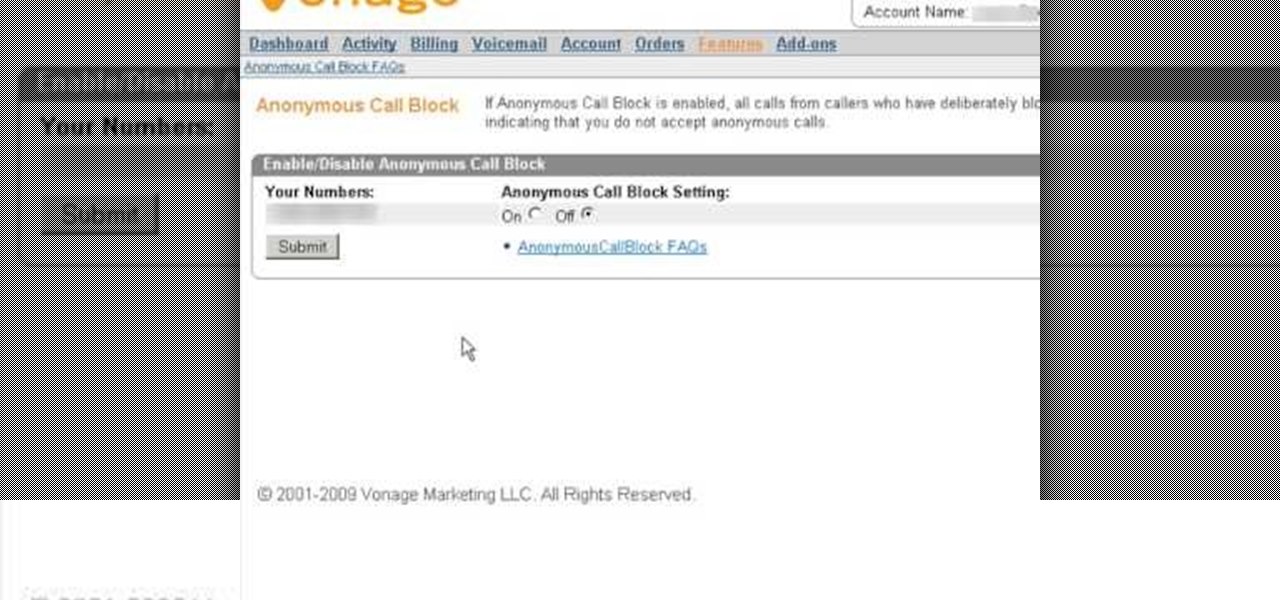
If you are looking for a way to prevent telemarketers and nothing else is working, consider signing up for Vonage's call blocking feature. In this tutorial, brought to you straight from the professionals at Vonage, learn how to set your phone to block any incoming call without a number attached to it.
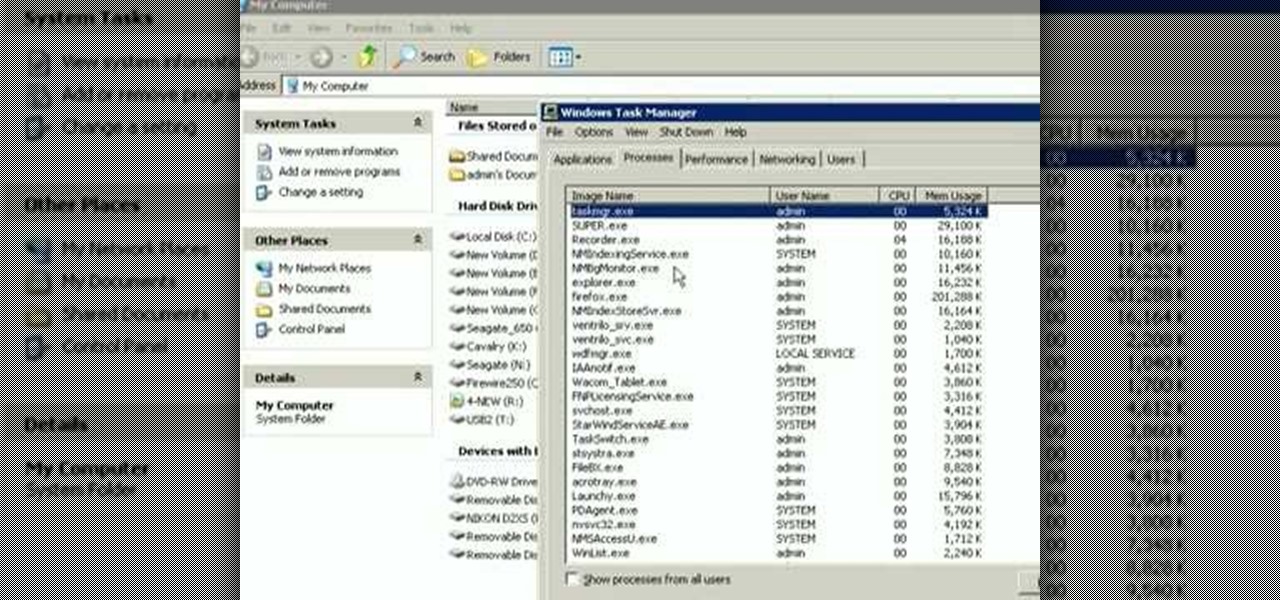
This how to video shows you how to restart Windows without rebooting the computer. Press control, alt, and delete on the keyboard at the same time. Your task manager program will open. Select processes and click image name to sort it. Select explorer.exe and press end process. Click yes in the warning dialog. Your start menu will disappear. This is usually bad considering you cannot do anything when this happens. Go to file and select new task. Click browse and click on any folder and right c...
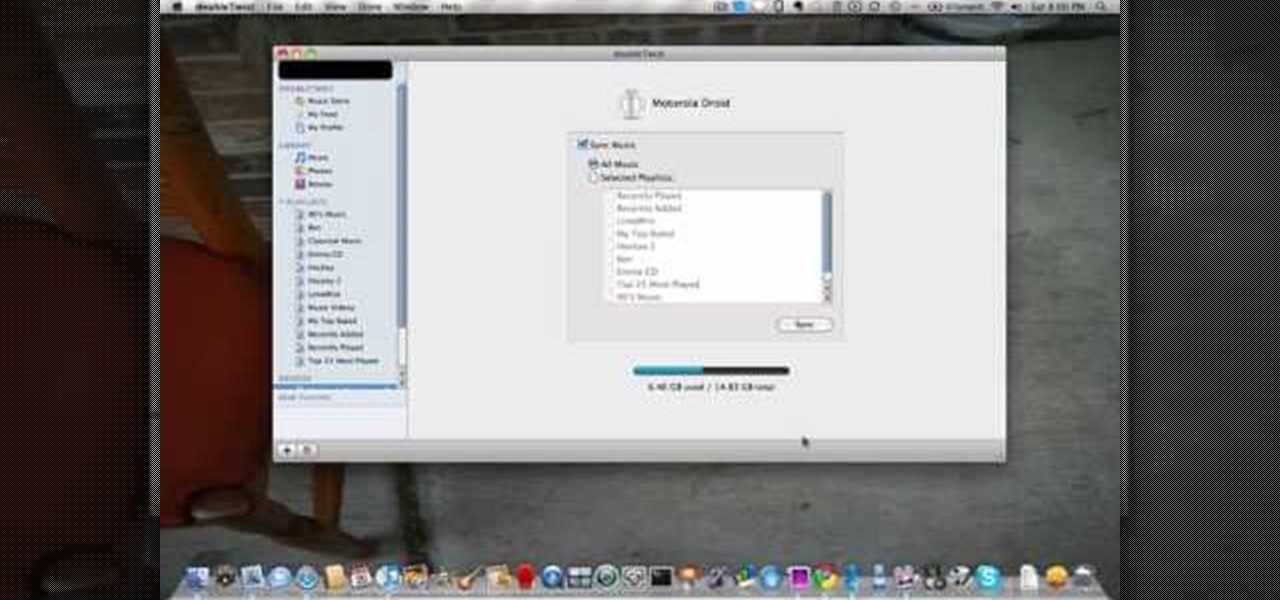
If you're like most people, the only music program you want to deal with is iTunes. But you can't use your iTunes music unless you have an iPhone, right? Wrong! Don't go around thinking you need an iPhone to use iTunes on your mobile device. You can sync up iTunes with your Motorola Droid too! This video tutorial will show you how to sync iTunes on your Droid.
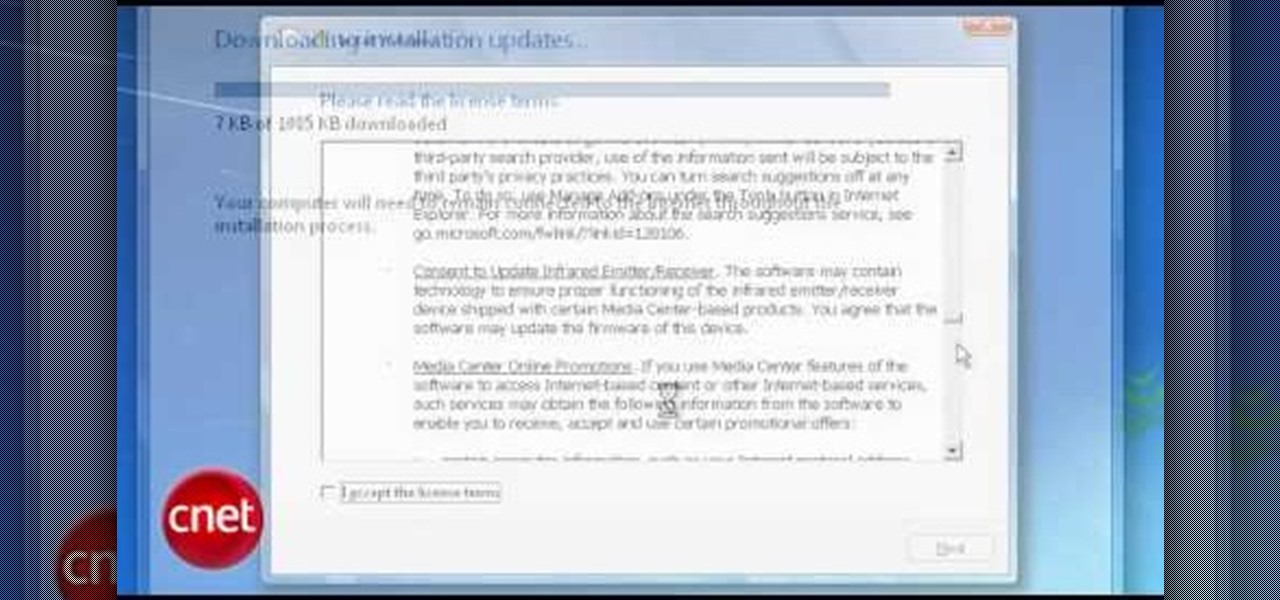
In this Computers & Programming video tutorial you will learn how to upgrade from Windows XP to Windows 7 with CNET. You need to do these 3 things. 1st - run the Windows 7 upgrade advisor to know if your computer can handle any version of Windows 7. 2nd – check the Windows 7 compatibility center to know if you need to upgrade your drivers or apps. 3rd – make a copy of your hard drive. Down load and run the ‘windows easy transfer’ wizard. This will back up all your files and settings to an ext...
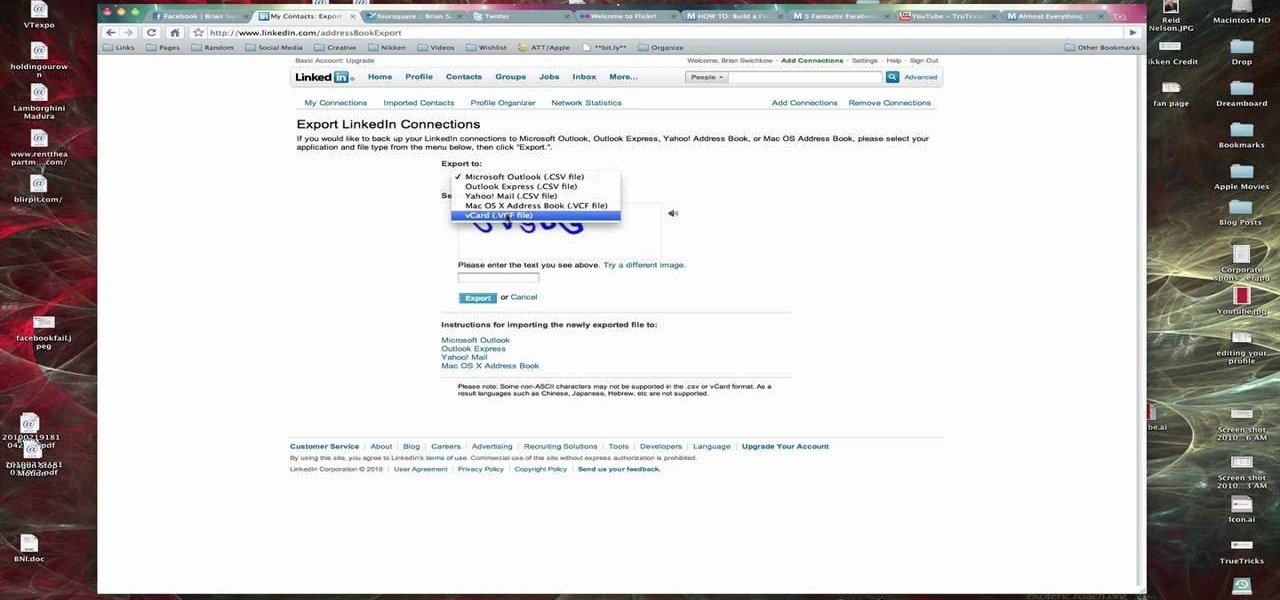
In this Computers & Programming video tutorial you are going to learn how to export LinkedIn contacts to an address book. LinkedIn is great for keeping your contacts in your professional network. To export your contacts go to home page and click on ‘contacts’. Now your full network of contacts will be displayed. On the right hand bottom, click on ‘export contacts’. On the next page select where you want to export the contacts, type in the security code and hit ‘export’ and all the contacts wi...

In this Computers & Programming video tutorial you will learn how to add photos to Facebook using Picasa. The video is from Help Me Rick. Log into Facebook, go down to the lower left corner and click ‘Applications’. Click ‘Find More’ and in the search applications box, type in ‘Picasa’. You will get a list of Picasa applications. Select the Picasa by Alan Lundeen. Here you click ‘go to applications’ -> install now -> OK -> Yes -> Facebook -> Add -> OK. Now you will get a Facebook icon on the ...

In this video from Inner Confidence, they demonstrate how to not get too into a women's personal space. A way to not approach a woman is to approach her head on. It is much less intrusive if you approach her from the side. The girl in the video says that a man's attractiveness depends on his groundedness. Some guys to not realize they are socially awkward. When guys take this program they are more relaxed and the know what to say. She says a big turn off is a guy who is really feminine. A qua...

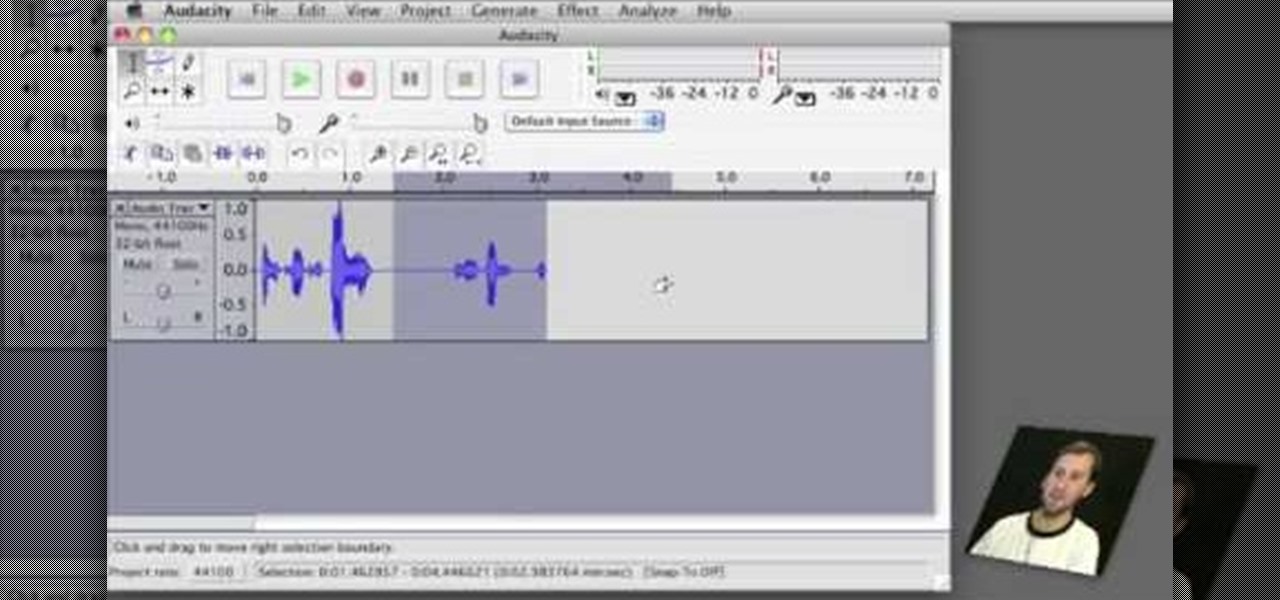
Learn how to edit audio files using Audacity of the MAC. 1 Create an audio file by using the built in recording function in Audacity. Save the file prior to starting your editing. 2 Open the file that you created earlier and test the file by playing it. 3 You can copy, cut and paste different parts of the file by highlighting the section in your file and then right clicking (or option clicking) and choosing what you want to do from the pop up file. 4 You can also add effects by highlighting a...

Mike Agerbo explains the benefits from listening to one's music through AppleTV, however it seems that one cannot listen to any music or other audio files unless he/she is using iTunes media. Agerbo explains how you can use Apple TV with other types of media, using a program called ATV Flash. Agerbo believes ATV Flash to be an easy and inexpensive tool to upgrade one's Apple Television so it can use the USB port and download and use other media content. One can also create a Boxee account to ...

Vanessa from Tekzilla Daily gives us a very helpful video guide on how to edit or tweak icons in the system tray on Windows 7. Typing "notification area" in the search box of the Start Menu calls up the Notification Area control panel. This control panel shows the different processes and programs that are on the system tray. It is where you can edit the settings for each process or icon, with options of "always appear, never appear or show up only when needed". You can also control the basic ...

It's good to know the IP address of your computer. With this information, you can track your computers usage online, and will also know how to change it if you want to surf unnoticed. This tutorial will show you exactly how to find the IP address of your PC, so you will never be lost again. There are a number of programs that require your IP address, for example if you are setting up an external device like an XBox live to your Internet connection, you will need to make sure the IP address is...

The world has gone Lady Gaga MAD! Run for cover! ... But run for cover in STYLE with this makeup tutorial by makeup master, Michelle Phan. In this video, Phan re-creates the "big eye" look for Lady Gaga's "Bad Romance" music video.

You can do just about anything in Houdini's 3D animation program. In this video series masterclass, Houdini artist Georges NAKHLE shows how to dissolve an image using Houdini particles. See how to blow an image away using particles!

This is all about vector, swirling rainbows. Have you ever seen those looping, swooshing, swirling rainbow graphics used in all kinds of graphics ranging from logos, and sketches, to grungy and retro illustrations? Well, you are going to create one of them in Illustrator. Watch this Illustrator video tutorial to create vectored rainbows. Also, learn how to export it to a program, such as Photoshop, as a smart object, to utilize it as a smart object so we can both retain vector scalability whi...

Zonealarm not working out? Is it slowing down your computer? Forget those programs and have a home made DIY lag/standby switch!

Watch this instructional video brought to you by Richard Berry to learn how to operate the Nikon D90. This Nikon D90 video tutorial demonstrates how to use the control dial (auto mode, scene modes, program [P], shutter priority [S], aperture priority [A], and manual [M]); read the display and viewfinder; adjust the aperture, shutter speed, focus, spot meter, matrix, exposure compensation, etc.; use the back command dial; and more. Use this Nikon D90 tutorial to familiarize yourself with your ...

Watch this video series to learn how to program a game with C++. This series covers the entire game design process and builds skills that can be used in any game design.

This tutorial is a step by step guide on how to make maps for Team Fortress 2 (part of the Half Life 2: Orange Box) using Steam's Hammer program. Topics covered include:

Want to break free from the confines of DVR land? If you're tired of spending all the money to download program listings from your DVR, then it's time for a change. If you don't want to mess with DRM files anymore, but want to backup your system, then MythTV is the way to go. You'll need to build your own PVR (personal video recorder) with thanks to MythTV, and it will end up costing you less than $500. Well worth the investment. The MythTv software is free and open source, so you just need t...

This video tutorial instructs you on what a key logger is and how to make a key logger which records your computers key strokes for later review. There are software or hardware based key loggers that intercept the connection between the keyboard and computer. Hardware key loggers consists of a micro controller for data logging. Software key logger is a script that runs in the background then processes and saves the key strokes to a text file. To make a key logger you'll need to know a program...

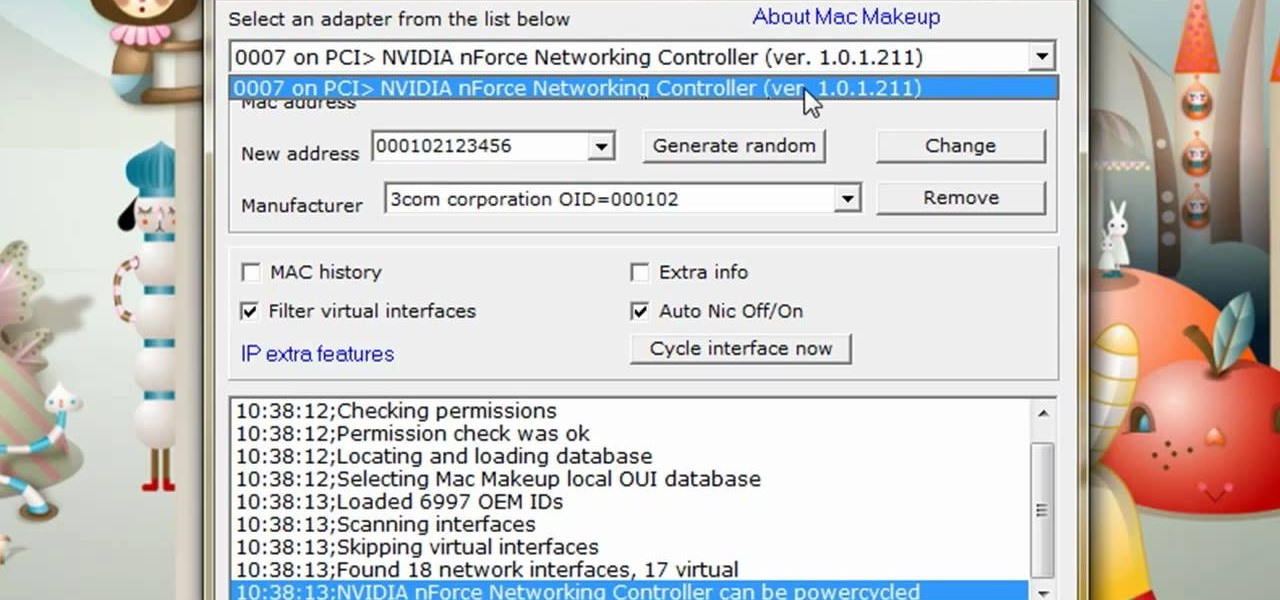
The video is about how to change the IP address. MAC address is the unique identifier a site of the most network adapters. MAC address is used to determine what IP address the computer will have and one way to change the IP address is by changing the MAC address. The method is only applicable for the windows systems and for the MAC systems you need to look at the link provided. In Windows in the start menu, type cmd in the run/search box, which will launch the command window. Type ipconfig/al...

Windows 7 is the hot, new operating system replacing the past XP and Vista systems. Windows 7 is the most simplified, user-friendly version that Microsoft has developed - ever. Get acquainted with your new version of Windows straight from Microsoft.

New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install additional brushes for GIMP on Ubuntu Linux.

This is a guided video tutorial on how to install Rockbox onto your Apple iPod. In case you don't know what Rockbox is... it's a program for your iPod that you can play games, programs, Game Boy games, and more!

Second Class Boy Scouts work on building their outdoor survival and camping skills. Compass work, nature observation, camp tools, and swimming are areas where new skills are mastered and demonstrated. A second class scout, having completed all the requirements, should be able to lead a hike, care for his own equipment, set up a campsite, and perform basic first aid.

As a Boy Scout, when the First Class rank is attained, a scout has learned all the basic camping and outdoors skills of a scout. He can fend for himself in the wild, lead others on a hike or campout, set up a camp site, plan and properly prepare meals, and provide first aid for most situations he may encounter. A First Class scout is prepared.

I may be a bit weird, but I enjoy listening to music at night as I fall asleep. Sure, you could create a playlist of songs so that it stopped after all the songs finished playing, but I have a rather extensive database of music and I enjoy listening to them randomly. Also, I like to ensure it terminates after a specific amount of time (I don't want it playing all night). Or sometimes I use it when I am cooking so that when the music stops, I know I need to check on my food, etc.

A flaw in WPS, or WiFi Protected Setup, known about for over a year by TNS, was finally exploited with proof of concept code. Both TNS, the discoverers of the exploit and Stefan at .braindump have created their respective "reaver" and "wpscrack" programs to exploit the WPS vulnerability. From this exploit, the WPA password can be recovered almost instantly in plain-text once the attack on the access point WPS is initiated, which normally takes 2-10 hours (depending on which program you use).

If you have not used your eRecovery system in a long time and have forgotten the password, have no fear. This video is here to help you retrieve your details and use your program again. In this clip, learn how to recover any lost passwords with Acer's eRecovery Manager for Linux.

Learning different coding languages can be difficult. You spend so much time mastering one and getting used to thinking along the channels you need for it that learning something new can sometimes be more difficult than starting from scratch. Starting from scratch, notably, is also difficult.

MATLAB, an acronym for "matrix laboratory," was created over 40 years ago to service the applied mathematics community. The powerful programming language now has over four million users worldwide and is of particular import to engineers, scientists, and economists.

Java is one of the world's leading programming languages thanks to its virtually endless array of applications. Since Java's initial release in 1998, this Open Source platform has become beloved by coders for its speed, flexibility, and dependability.

If you're a frequent Null Byte reader, chances are you're already up to speed with at least one or two programming languages or development platforms. But in a world that's becoming increasingly reliant on high-powered apps and responsive websites, knowing the fundamentals of just a few go-to programming languages isn't going to cut it if you want to be competitive and successful.

Few things are more important than being well-versed in data analytics and interpretation when it comes to succeeding in today's increasingly data-driven world. As a data scientist, these skills are the key to a high-paying career. For hackers, there's no better way to defeat the enemy than to become the enemy.

Since its release back in 1988, Microsoft Office has been the top client and server software suite for businesses around the world. Office's domination is thanks to both Microsoft's extraordinary foresight and their continual updates and innovations to ensure that companies always get what they need.

While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of built-in graphical X forwarding for SSH.

While Magic Leap World gets its share of fun apps for playing with Porgs, watching TV, and exploring the ocean's depths, developers are making a strong business case for the Magic Leap One as well.

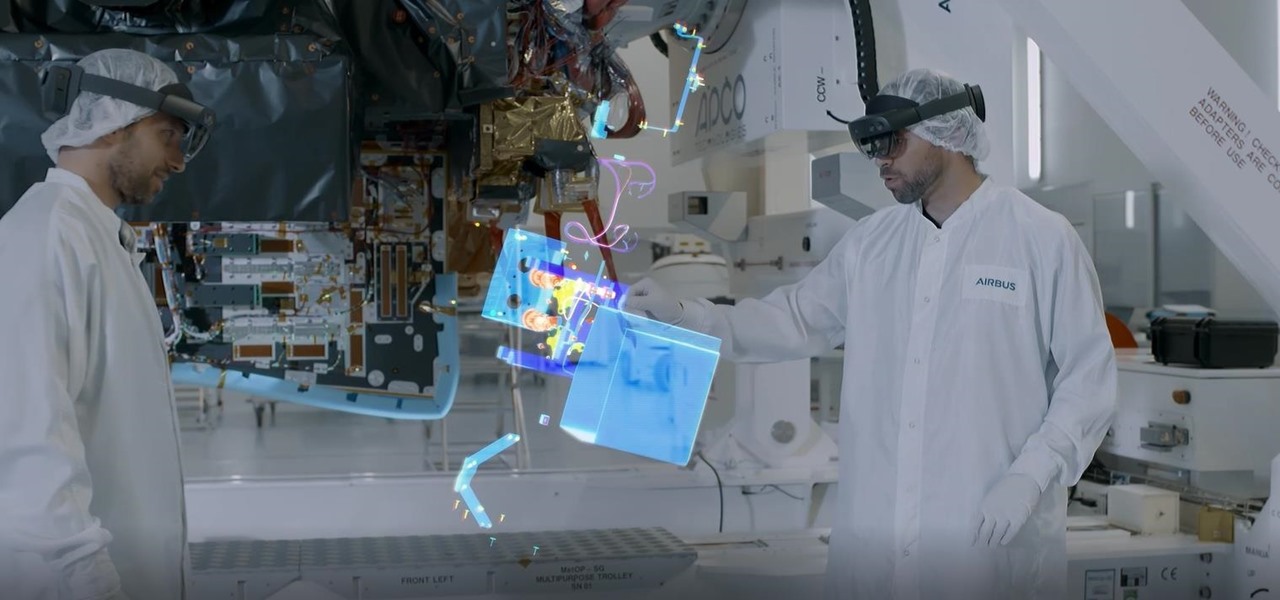
Aircraft manufacturer Airbus is so impressed with the boost in productivity it has gained from Microsoft's HoloLens, the company will begin offering augmented reality software to its customers.

While hackers know and love the Raspberry Pi, many don't know of its cheaper cousin, the microcontroller. Unlike a Pi, which can be used more or less like a regular computer, microcontrollers like the Wi-Fi connected ESP8266 require some necessary programming skill to master. In this guide, we'll build an Arduino program from scratch and explain the code structure in a way anyone can understand.