There are a lot of programs which allow opening archives. Alas, most of them are rather complicated to use. The process of the archive opening often takes much time. Hopefully, there are some programs which are simpler to use for regular users.
Gary Rosenzweig and Eve Park take a look at two programs for the Mac that allow you to draw. The first is Eazy Draw, a vector drawing program. The second is Doozla, a drawing program for kids.
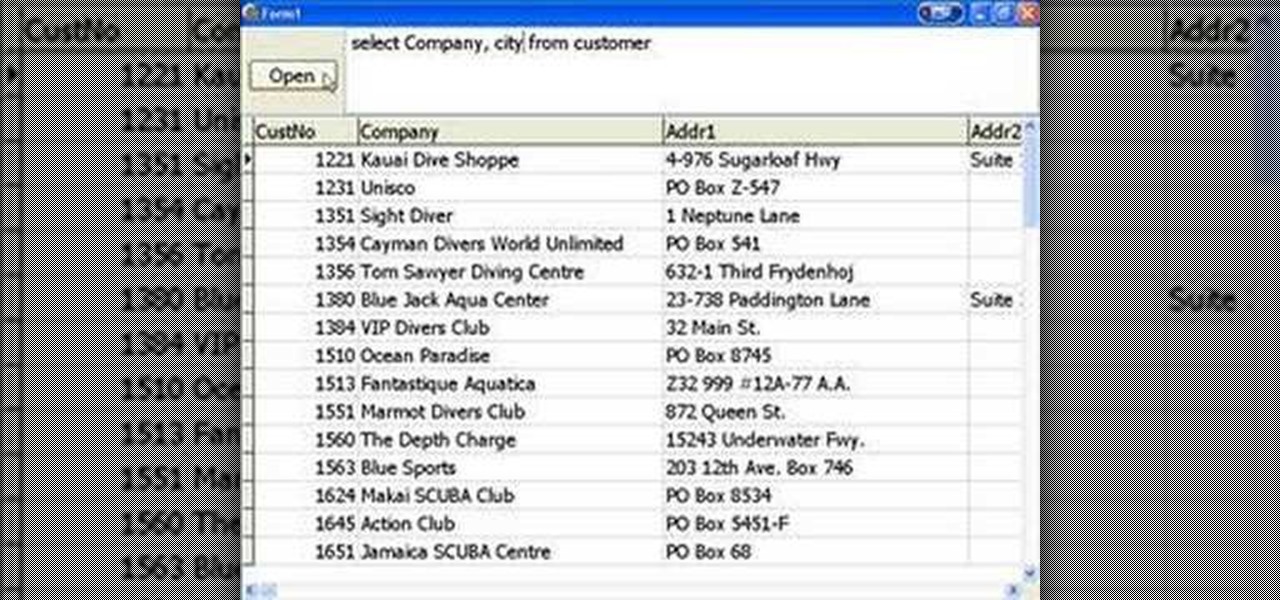
A tutorial on using SQL when programming GUIs in Delphi. Part 1 of 3 - How to Use SQL when programming in Delphi.

The procedure involves downloading a program called "hand brake". Hand brake is free to download. You can find it by searching for "hand brake" on Google. The direct website is Handbrake. You have to install this program on your computer. You must also download a program called DVD43. That program can be found the same way as hand brake, by using Google. DVD43 is also a free program to download. You use the DVD43 program to by pass copy protection on a DVD. You can use hand brake to change th...

There may be a time when you want to run a program for 24 hours straight. If that app happens to quit unexpectedly, you have some options to get it going again without having to manually reopen it. Check out this video on how to restart a crashed program automatically on Windows. You need WatchDOG.
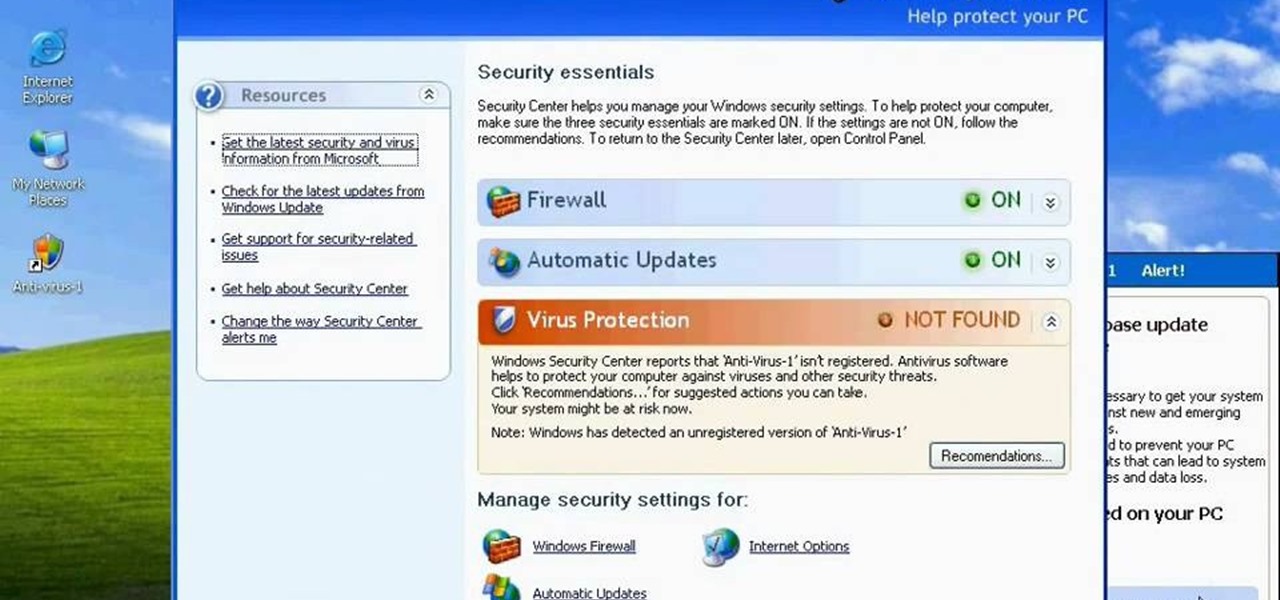
http://www.enigmasoftware.com/support... Having problems with your anti-virus software on Windows?

If you're an aspiring or even well-established web or app developer, the good news is that there's a virtually limitless number of lucrative opportunities waiting for you, regardless of whether you're looking to work for a company or as a freelancer.

Since its release in 1991, Python has become one of the world's most popular general-purpose programming languages. From data mining and web programming to cybersecurity and game design, Python can be used for virtually everything online.

The Internet of Things (IoT) is changing everything in our homes and at work, from security systems and lighting fixtures to smartphones and speakers. An estimated 50 billion devices are now hooked up to IoT.

Android 10 is officially out, but a lot of phones didn't get it in 2019, and others may not get it at all. With this page, you'll at least know when or if.

If you want to carry a variety of network adapters without looking suspicious, a perfect solution is accessing them through Airserv-ng. Tucked away in the Aircrack-ng suite, this tool allows a hacker to plug any number of network adapters into a Raspberry Pi and access them over a Wi-Fi or Ethernet connection.

When you want to install a new tool or game on your iPhone, you go straight to the App Store to do so — but it's not the only place you can get apps from. Some developers use back alleys to get their apps to you, while others can trick you into installing them without giving it much thought. This can lead to malicious software running on your iPhone, software you'll want to get rid of asap.

Samsung isn't known for its timely rollout of major Android updates, and Android 9.0 Pie won't be an exception. If we go by their Oreo update timeline, we can expect Android Pie to officially touch down for the Galaxy S9 and S9+ sometime around November, with the final version rolling out the around the first quarter of 2019. But a leaked version of the beta has already hit the internet.

A new study published by American University demonstrates how Pokémon GO and other augmented reality games can help city governments bring communities closer together.

Bluetooth Low Energy (BLE) is the de facto wireless protocol choice by many wearables developers, and much of the emerging internet of things (IoT) market. Thanks to it's near ubiquity in modern smartphones, tablets, and computers, BLE represents a large and frequently insecure attack surface. This surface can now be mapped with the use of Blue Hydra.

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

The new iPhone X will be released on Friday, Nov. 3, in Apple Stores located in over 55 countries and territories. For those of you who would rather skip the in-stores lines that will start building well before the 8 a.m. local time openings, you can preorder the iPhone X on Friday, Oct. 27, starting at 12:01 a.m. PDT.

User interfaces for computers have evolved over the years, from the introduction of the keyboard and mouse on the personal computer, to touchscreens on mobile devices, to natural voice recognition. However, the same cannot be said for robots or drones—until now.

Welcome to a tutorial on crypting technology. In this article, we will be discussing types of crypters, how they work and why they work. After defining these, we will then make our own basic crypter using the function I gave to you as a task to complete by yourself in the previous tutorial.

Hello null_byters, after some time out here we are again with another tutorial, continuing our beautiful series, today we will write our first real world bash script.

We are most certainly not machines. We all need some downtime every once in a while to set our sanity scales back in balance, which in turn, makes us more productive workers. This is a premise that several forward-thinking employers fully understand, but these types of companies are few and far between in corporate America.

Hi there, nullbytes :) I've recently seen many questions regarding VMs with Kali, and personally I prefer using a Live Boot USB to get Kali without removing my system (and for many reasons).

Welcome back, my greenhorn hackers! Digital forensics and hacking are complementary disciplines. The better you are at digital forensics, the better hacker you are, and the better hacker you are, the better you are digital forensics. Unfortunately, few people in either profession cross these discipline lines.

MacBooks are built for creation and creativity. They're built to withstand our careers, our hobbies, and our everyday use. I use mine every day, and there's nothing I'd recommend more for computing needs.

It's rare that a developer listens to the wishes of the masses, but that's exactly what CyanogenMod has done with their new CyanogenMod Installer, which automates the entire ROM installation process on your HTC One or other Android device. Previously, upgrading from the stock HTC One ROM to CyanogenMod required an unlocked bootloader, a custom recovery, the latest CM version, and Gapps. Let's be honest—unlocking the bootloader is a pain the ass, and probably the only reason stopping most peop...

I love cryptography. It is like a great gigantic puzzle for me to solve. However, it is more important than that. It is also how we keep secrets safe. Not just sorta safe either, but really safe.

If I were to lose access to the entire internet for the rest of my life, one of the websites I would miss the most would have to be Wikipedia. Wikipedia has ended countless arguments, informed me of how old and single some of my favorite actresses are, and helped me brush up on thousands of historical topics.

Whether you're in an airport, restaurant or waiting room, the insidious grip of televisions on human life is omnipresent. Sometimes it's nice to talk to other human beings while looking at them directly—actually hearing what they have to say.

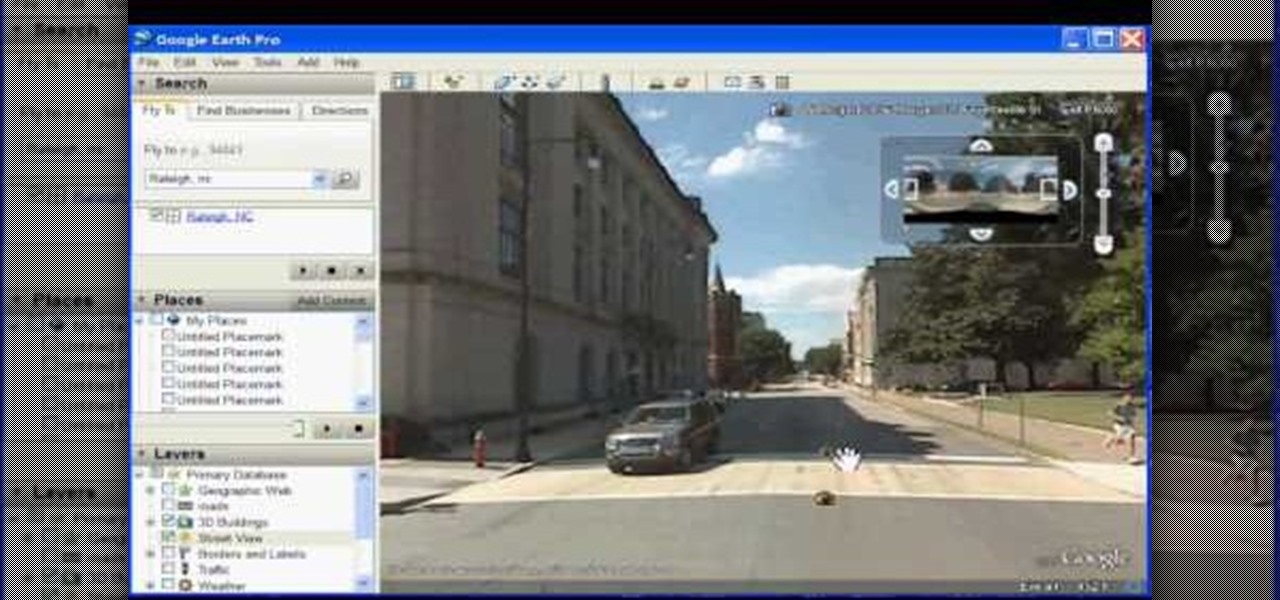
In this how to video, you will learn how to use Google Earth. First, download the program. Type in a city and state in the form. In the lower left, check street view to turn it on. Click the magnifying glass to zoom in. Some cities have 3d buildings. When you get really close, you will see cameras indicating street view images. If you get even closer, you will see spheres of the actual street view images. Click on it and the photo to get into the photo. In the upper right, you see controls to...

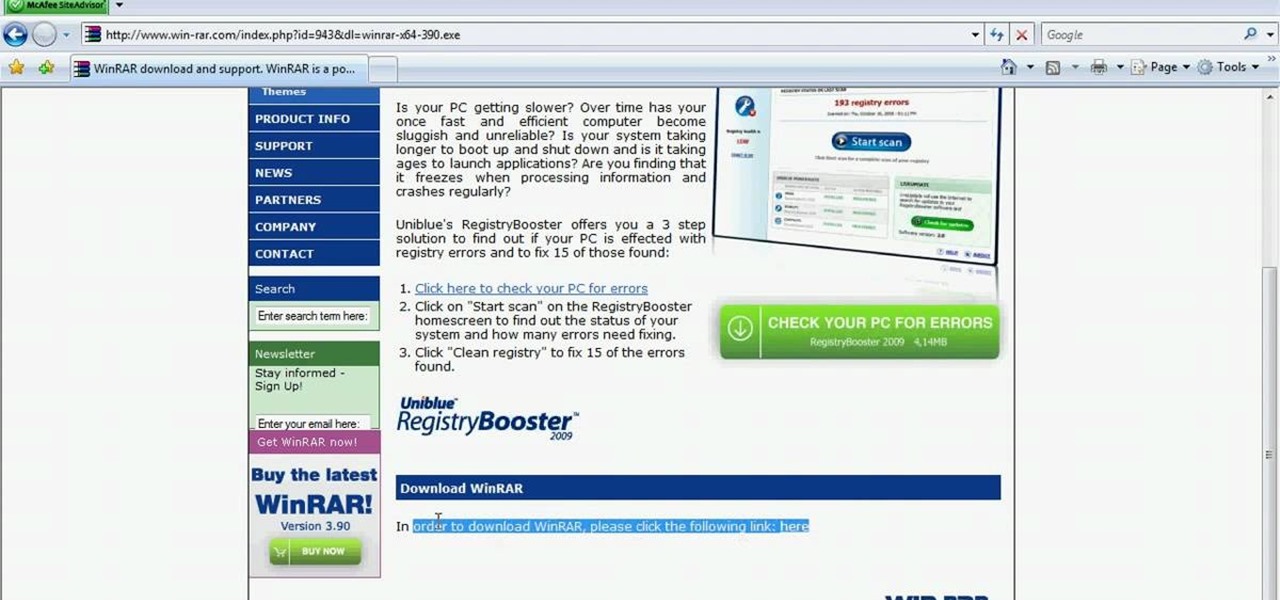
In this video tutorial, viewers learn how to unzip .rar files using Winrar program. Begin by opening your internet browser and download the program from the link in the video description. Wait for the time to pass and click Download. Select 32 bit or 64 bit, depending on your computer. Open the file and install the program by following the instructions. Once it's installed, select the file that you want to unzip. Right-click on the file and select Extract All Files. This video will benefit th...

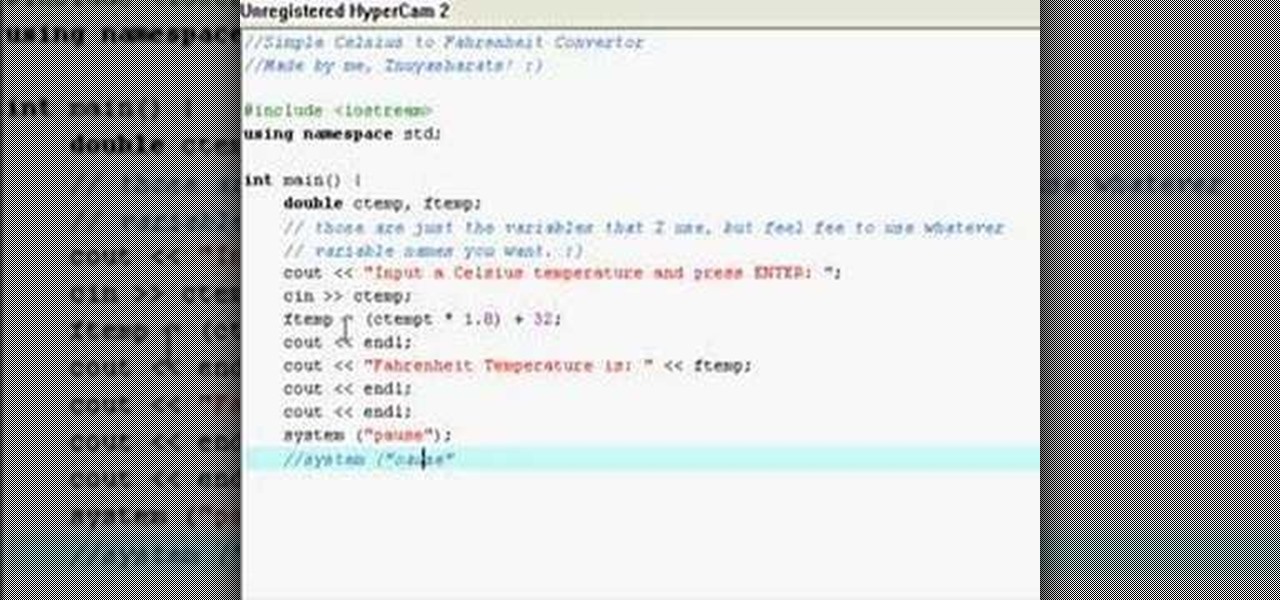
In this video, the instructor shows how to convert Celsius to Fahrenheit using a C++ program. This video shows how to do this by a live example where the instructor writes down the code to do it. First, code the basic structure of a c++ program that contains the include and all other statements. Now accept the value of temperature in Celsius from the standard input. Now multiply that value by 1.8 and add 32 to it to get the value in Fahrenheit. Display the value to the output. Finally, compil...

gotbletu teaches you how to mount an ISO image file in Ubuntu using AcetoneISO2. You can see what's inside a regular ISO image in Ubuntu, but not when it's 'mdf'. The program you need for this is AcetoneISO2. Start the program and at the bottom of the main window you'll see a button called mount. Click on that and choose your 'mdf' file. The program also opens and mounts 'ISO', 'nrg' 'bin' 'img' files. After you've mounted your file you go at the top of the main Ubuntu screen to Places and yo...

In this video the instructor shows how to install a program or a game which is in ISO format. The first thing you will need is the ISO file that contains the game or program. Next you will need a program that can open the ISO file. Use the daemon tools for this purpose. Right click on the daemon tools icon in the notification area. From the menu choose the mount image option and point to the virtual disk. Now browser and select the ISO file that you want to open. This mounts the image to the ...

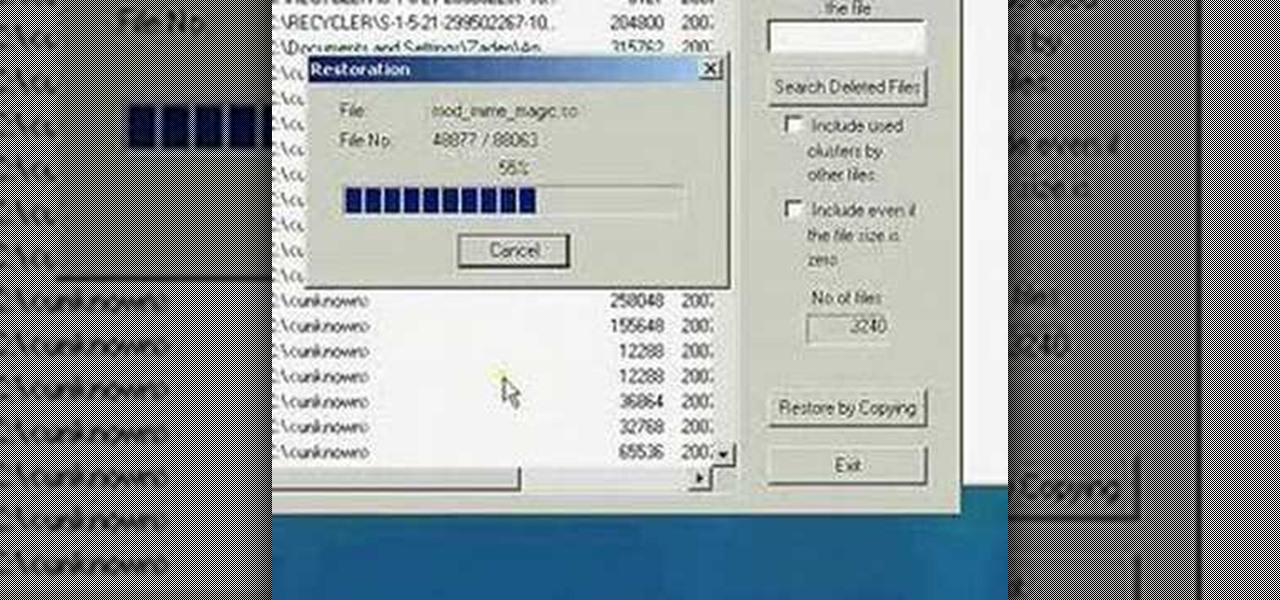
A very unfortunate event is to realize that you deleted some PC files that you need. This happens to a lot of people, but the files can be restored! To do this you will have to download a freeware program called Restoration! After you have downloaded and installed it, start the program, and select the driver for the program to search. The program will search that driver, showing you all of the deleted files in the past. The list will be long, but with a bit of patience, you should find the mi...

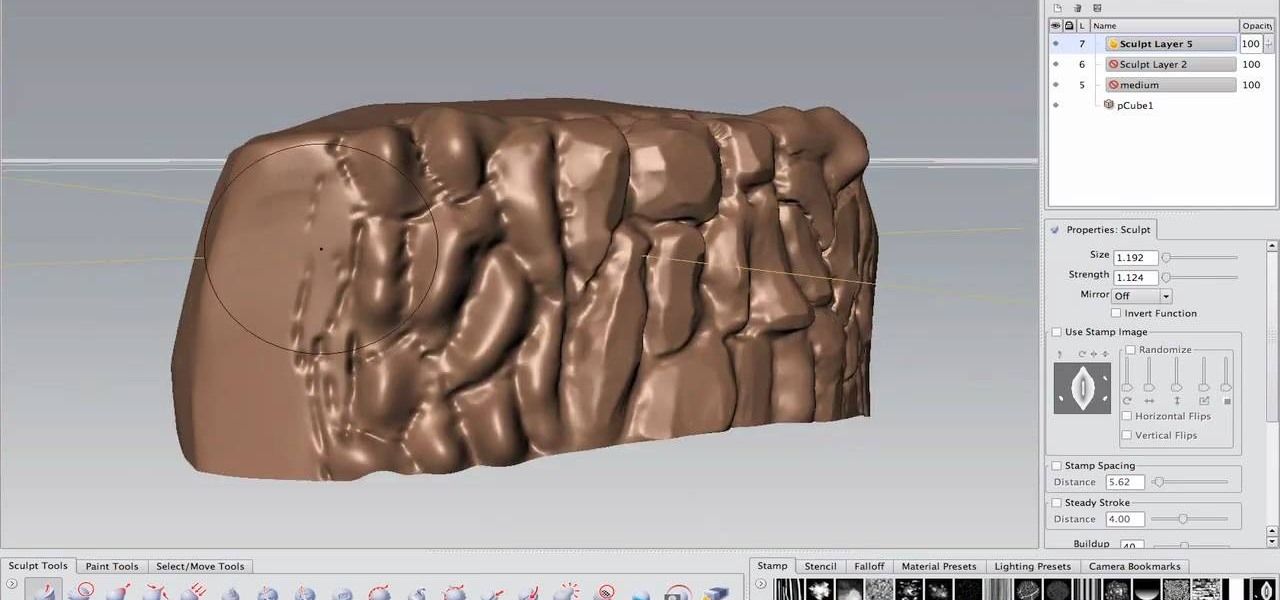
If you're an Autodesk Maya user and you're looking to create rocks, boulders or rock walls, check out this excellent 7 part tutorial and learn how it's done. Maya is a massive 3D creation tool with so many aspects it's really mind blowing. This tutorial will help you improve your skills for your game building or just for you own art.

If you've ever seen something called ThinkPoint Antivirus on your computer, you have gotten one ofhte most widespread and infectious fake antivirus malware programs out there. To get it off your PC, follow the instructions below, or watch this video for an alternate method if this one doesn't work.

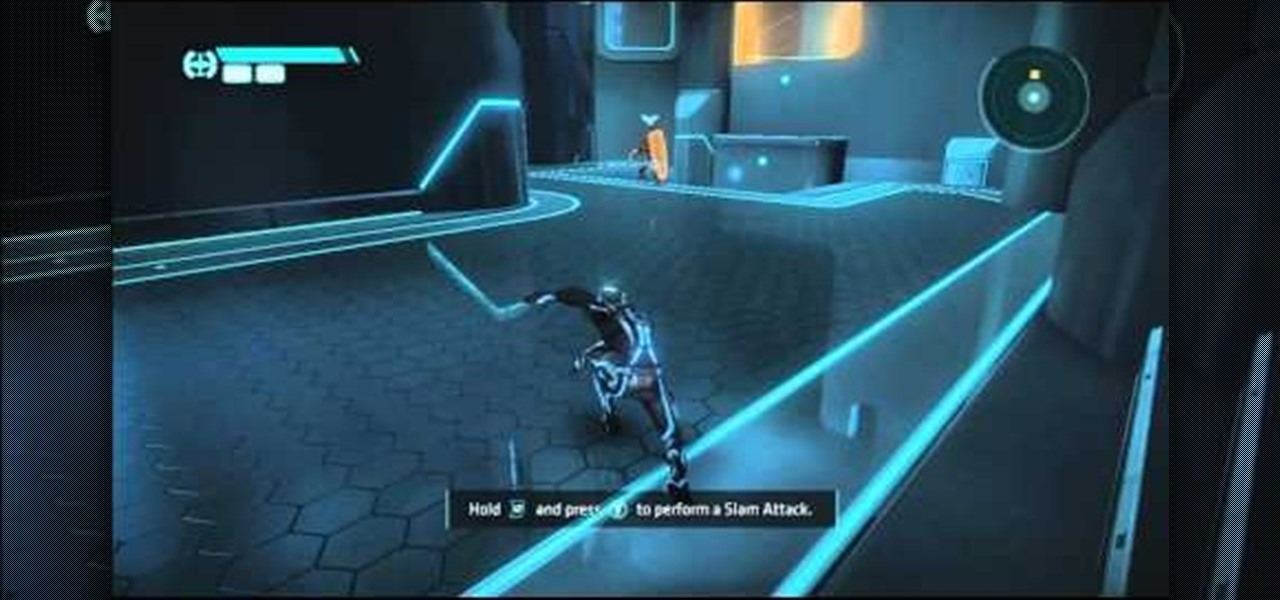
Love the retro Tron movie from Disney? Can't wait for the release of the new Tron: Legacy on November 17th? We've got something to bide your time— Tron: Evolution.

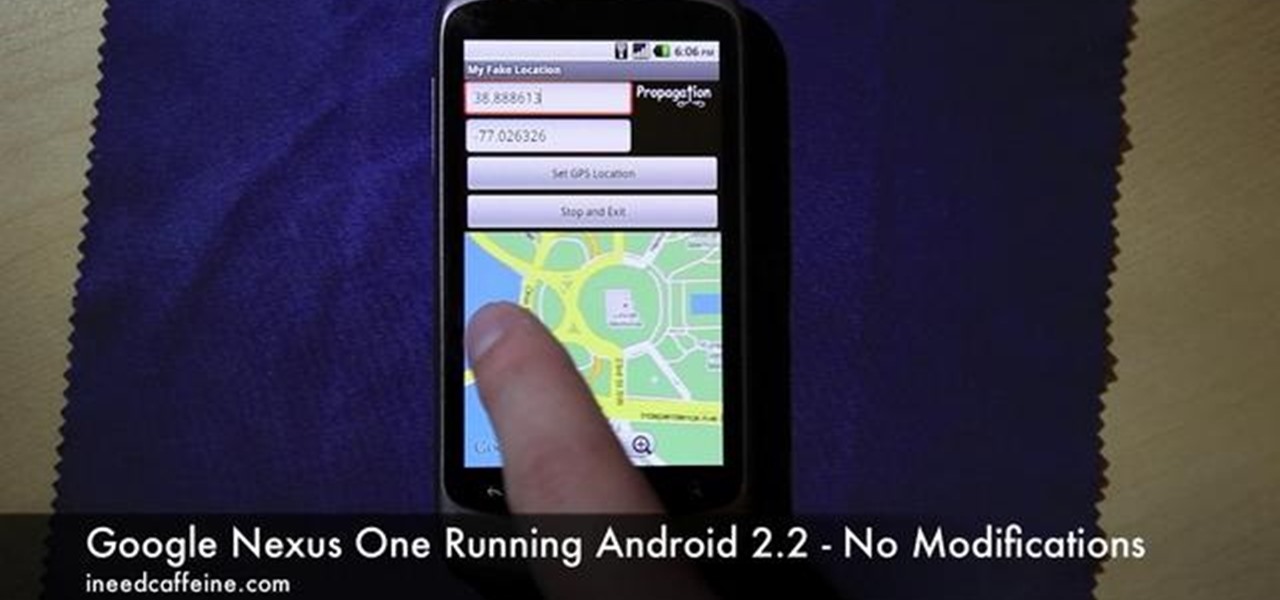
Enjoying the many benefits of Facebook Places? But what if you want to check in somewhere you're not? Your smartphone can automatically detect your geographical location, preventing you from just checking in just anywhere, but like all technology… it's a long way from perfect, even Android mobile devices.

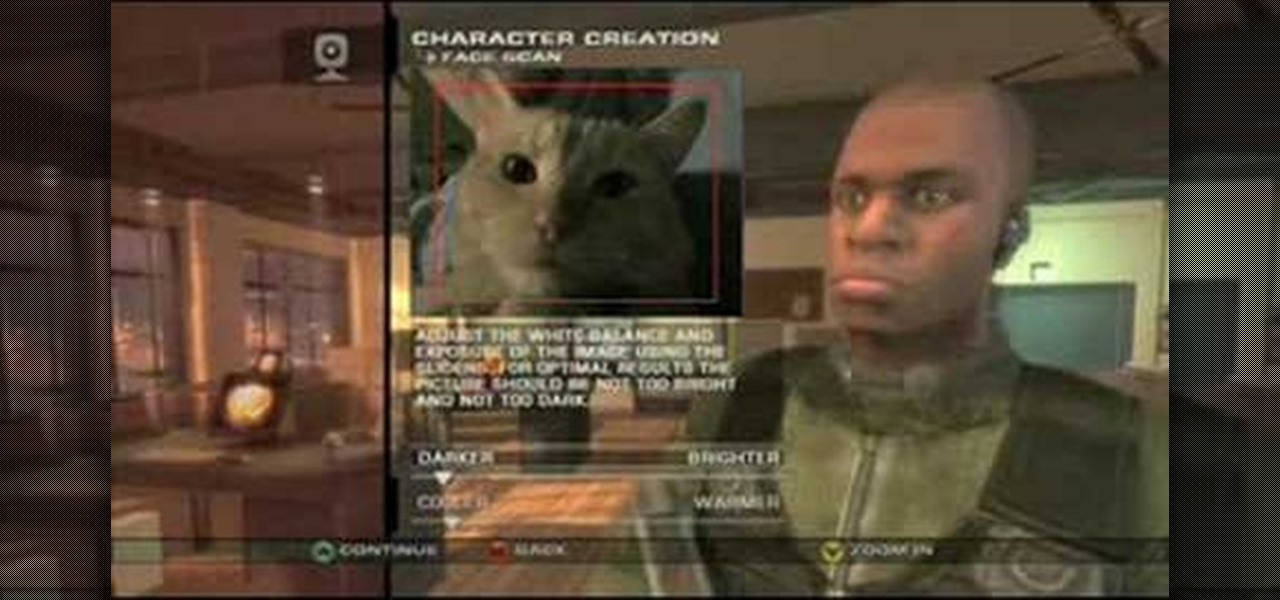
This process requires XBox2 live with vision camera. We are going to create a character. First, you go to multiplayer mode, options and then choose character creation. If you haven't created a character, you will start from scratch here. If you have created a character previously, you will make some adjustments to the character for this presentation. Now, go to player information and then service record. As the program already has a character, we are going to change the appearance of the char...

There are several different kinds of disc drives that come in different iterations of the XBox 360, and each one has to be hacked a little differently. This video will show you how to flash the ms28 drive used in some systems, the second part of the video will show you how to determine what model of drive you have. It is very detailed, and should have you well on your way to hacking you beloved XBox 360 and maximizing its potential.