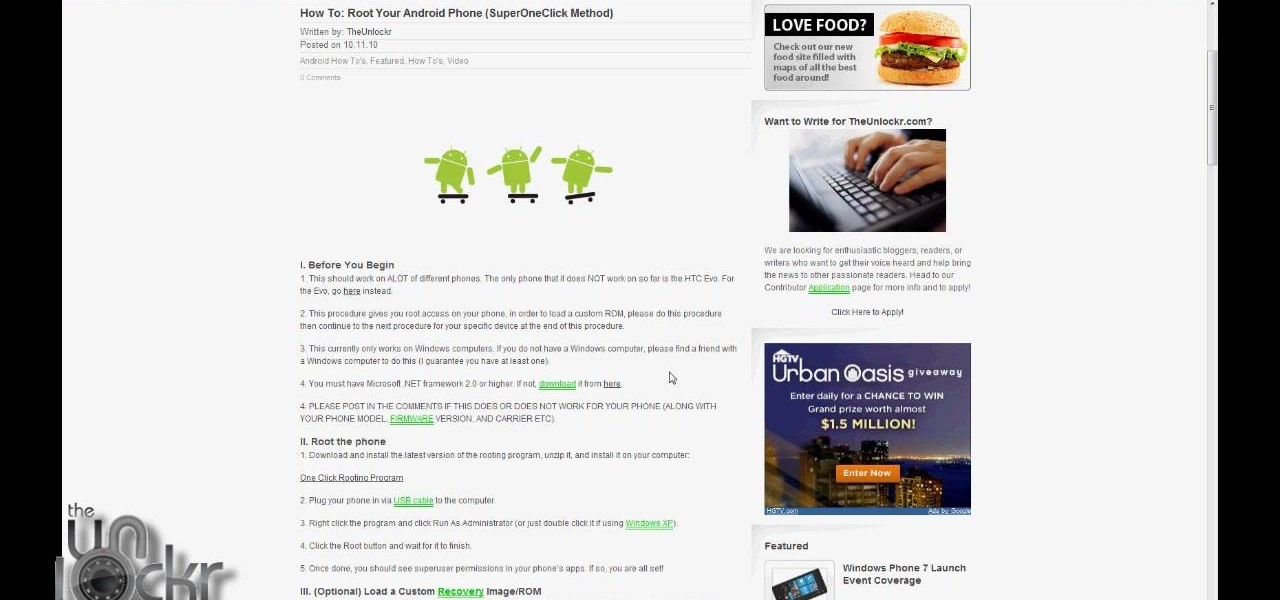
This is, by far, the easiest way to root your Android phone, and it's even got its own name— the "SuperOneClick" method. This is a universal technique that applies to most Android-based smartphones (minus the HTC Evo and T-Mobile G2/Vision). TheUnlockr shows you the secret behind rooting your Droid, so watch and learn. Anyone with an Android-enabled phone can do this.

Is your hatchet in need of a quick tuning? Doesn't quite get the job done anymore? It's time to sharpen it. This also applies to sharpening an axe.

In this language tutorial, you will learn how to use the definite article in biblical Greek (Koine). This is a perfect lesson for those scholars wishing to study this ancient language of Greece. Watch this how to video and you will be speaking biblical Greek in no time.

Apple News. Facebook. Twitter. Reddit. LinkedIn. These are just a few of the apps you probably have on your iPhone or iPad that keep you up to date on today's events. Unfortunately, they can also cause information overload. But a new viral speed-reading tool thinks it can help you process your daily news more efficiently.
If you're like me, you don't have time to sit down and leisurely read an entire article from start to finish — but you still want to be informed throughout the day. Instead of just browsing the daily headlines, there's a free service that will summarize any article you throw at it, giving you a better idea of what's going on without committing to reading an entire article.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.

If you've ever used a heating pad or hand warmer, you essentially know what "hot ice" is. It's supersaturated sodium acetate, and it's actually fairly easy to make at home out of sodium acetate crystals. You can also make it out of vinegar and baking soda (directions at the bottom of this article).

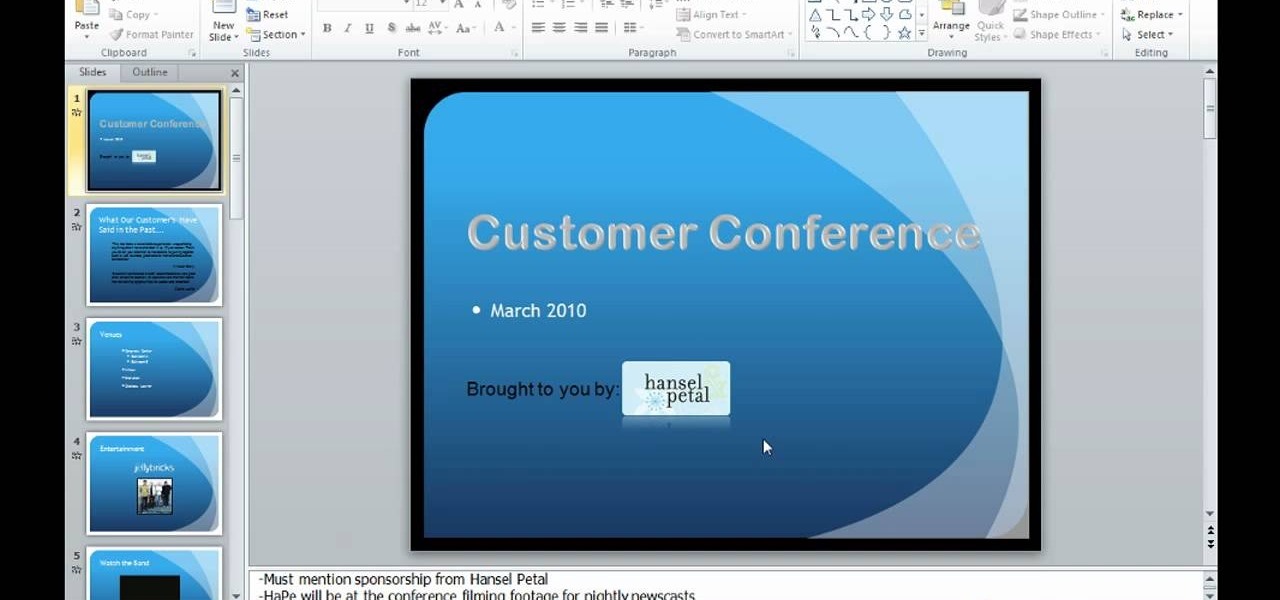
This video is describing how to preview the pasted items such as from another PowerPoint or any other articles. These are all features available in the "Microsoft Office Power Point 2010". We will take the "conference1" presentation in that the first slide and we would like to add some text from another "Document" from another application like "Microsoft Word". So, we click and drop the mouse to select that and click the Copy button on the top of the word file or we can copy by the keyboard i...

Want to learn how you can make some awesome YouTube videos of your own? Maybe your own Internet show or maybe even a short indie film... well, one way to make things easy is a green screen. This two-part video tutorial will show you how to make your own green screen studio and key it out. With a green screen, a YouTube show with special effects is easy!

Do you have a great article that you're really proud of, that was printed in the newspaper? Did something amazing happen, and you want to preserve the newspaper article about it? Newspaper is delicate, and can fall apart quite easily if not preserved properly. Check out this video to learn how to preserve a newspaper clipping.

Turn a 'toy' radar gun into the real thing! Cops don't even have one like this! While this is a completely new and different design, the inspiration for this video is from an article by Ken Delahoussaye in MAKE Magazine. Just watch this video tutorial on how to hack a toy radar gun into a real one.

The video describes the making of Paper doll dress up and a Tin Purse to put the dolls inside. You can use the cartridge paper but regular paper should do. She was sticking to the princess themes in this tutorial. The tin comes from provocraft but creative imaginations also offers one. Instead of purchasing a tin you can find a old tin purse maybe once for a over sized set of playing cards. There is a tab feature you can use on the dolls but which children the might come off. She suggests usi...

Everyone who owns or runs a website needs to know how they can improve traffic, and search engine optimization is the answer. This 13-part video series on SEO basics and strategies will give you more traffic for your site. It's jam-packed full of tons of great SEO tips! Check out each video in the series:

With the whirlwind of noise surrounding the COVID-19 virus sweeping the nation, it's not hard to default to panic mode. One of the best ways to avoid panicking, however, is to follow trusted sources of information and avoid all of the opinions and trolls that don't reflect reality.

Apple seeded the official version of iOS 13 to compatible iPhones on Sept. 19. Since then, we've seen two major updates — iOS 13.1, which, by our count, introduced 22 new features, and iOS 13.2, which also added 22 new features. Today, Dec. 10, Apple introduced the third major update: iOS 13.3.

Low Power Mode (LPM) decreases the amount of battery your iPhone uses by disabling background app refreshing and automatic downloads, locking your screen after 30 seconds, and more. While it's only meant to be used temporarily, if you're struggling with battery life, you may want to enable LPM permanently.

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).

I noticed the neon yellow sign at the new location of Pho Bar in Chinatown right away. The sweeping cursive yellow letters spell out "Crazy Rich Broth"; the same phrase printed on the back of servers' shirts. It's the kind of minimalist but colorful design feature that is especially popular on Instagram at the moment — shots of patrons in front of a glowing sign.

The Google Feed is a great source for relevant news articles from your search history, package delivery updates, and much more. Now known as the "Discover" page, many Android users turn to this useful menu on a daily basis. However, as Google recently pointed out, the all-white theme is not ideal for battery life, nor is it easy on the eyes at night.

Traditional media institution The New York Times continues to break new ground in its augmented reality news coverage, this time with a 3D volumetric capture of model Ashley Graham.

Locating and abusing files containing unsafe permissions is an easy and surefire way to elevate shell privileges on a backdoored macOS device. This time around, we'll be more aggressive and attempt to phish a user's login password by prompting a convincing popup message merely asking the target for their password.

The current iPhone lineup inarguably features Apple's best displays to date, but the stock wallpapers don't really do the screens justice. There are plenty of third-party wallpapers you can use, as well as ones you create yourself. However, if you want that typical Apple feeling, you're better off sticking with Apple wallpapers, and the iPad Pro has some beautiful ones that look awesome on an iPhone.

Passwords and data stored in web browsers are extremely valuable to hackers. If not for financial gain, black hat hackers may still leak your passwords and personal information for amusement. Never undervalue what you're worth to a hacker.

Once a hacker has created a PowerShell payload to evade antivirus software and set up msfconsole on their attack system, they can then move onto disguising their executable to make it appear as a regular text file. This is how they will get a Windows 10 users to actually open the payload without knowing they are doing so.

In this series, we are going to get you to the edge of building your own cloud-based, cross-platform augmented reality app for iPhone, Android, HoloLens, and Meta 2, among other devices. Once we get the necessary software installed, we will walk through the process of setting up an Azure account and creating blob storage.

Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve one's abilities to quickly identify exploits and vulnerabilities when scanning servers.

Null Byte users have often requested video content, but the question has always been what format would best serve our community. This week, we partnered with Null Space Labs, a hackerspace in Los Angeles, to test the waters by hosting a series of talks on ethical hacking for students in Pasadena Computer Science Club. We invited students and Null Byte writers to deliver talks on Wi-Fi hacking, MITM attacks, and rogue devices like the USB Rubber Ducky.

Ride-sharing firm Lyft says it will continue to rely on drivers in the near and long term even as it replaces them with driverless cars, Taggart Matthiesen, Lyft's director of product, said during a Podcast with Recode.

The USB Rubber Ducky comes with two software components, the payload script to be deployed and the firmware which controls how the Ducky behaves and what kind of device it pretends to be. This firmware can be reflashed to allow for custom Ducky behaviors, such as mounting USB mass storage to copy files from any system the Duck is plugged into.

We all know the internet isn't exactly a safe place. While plenty of its users are innocent and kind, you won't last long unless you treat every new screen name like a criminal (we're all this cynical while surfing the web, right?). Well, that cynicism is proven correct today, a post on Medium uncovered a group of scammers on the iOS App Store that are costing victims up to $400 a month.

Onshore, or on a boat, have you ever wondered what swims below in the dark water? Using standard equipment and a new process, marine scientists can now get a good look at what is swimming by—just by analyzing the water.

I fry foods a lot. A LOT. We're talking wings by the dozen here. As a result, I go through a ton of frying oil. Now, frying oil isn't the most expensive ingredient out there, but it adds up when you fry regularly. Of course, I always reuse my oil, but straining it can be a huge mess and it gets to a certain point where enough is enough. It's time to start fresh.

If you're standing in a foreign city, surrounded by signage in a language you don't understand, you won't suddenly be able to read it. But with a clever feature in Google's Translate app, your smartphone can.

This is my first article on here, it's based off of a project that I'm working on at school which is on three ways to bypass windows user password's. If all goes as planned and you all would like I'll work on part two and part three and post them as soon as I can. I do have to give credit to Puppy Monkey Baby and The Defalt, both of whom are my classmates at college and have helped me with writing this article.

What's up guys? Welcome to a sort of general walkthrough on how one might approach a reversing and analysis on a crypted malware. This is by no means a universal technique so don't assume that this will occur in every scenario, it's more of a demonstration than anything really.

Welcome back, NB community, to my series on sorting. I introduced in my last article the concept of complexity. When I say complexity, I'm talking about time complexity.

Hello ladies and gentlemen, I'm back with another informative(hopefully) article for you all. Once again I would like to apologize for my absence for about a week or so. I have some stuff going on with my life and university and I haven't found enough time to make a fully in-depth article. In this article I'm going to walk you through one of the main networking protocols when it comes to communication across the Internet between programs, aka UDP(User Datagram Protocol).

This article is to all the newbies on here wanting to become a hacker. Since I have seen many newbie questions on here, I need to address this.

Welcome back! Sorry I've been gone for so long, but if anyone has been keeping up with these articles, you'll know that when I get quiet, something is cooking under the surface. In other words, I've been working on a project lately, so I haven't had much time!

I mentioned in 2015 I wanted to start a 'DoXing' series, and since I havent seen this on Null Byte, I am now going to introduce this to the community.