
How To: Build a Tablet Mount for No-Hands Reading and Movie Watching in Bed
Reading in bed with a book and bedside lamp is so 1990s. As tablets get smaller and content continues to be digitized, reading on an electronic device is pretty standard.


Reading in bed with a book and bedside lamp is so 1990s. As tablets get smaller and content continues to be digitized, reading on an electronic device is pretty standard.

The only bad thing about Portal is that you can't play it everywhere. You can't play it while camping, you can't play it in the car, and you can't play it in the waiting room at the dentists office (unless you lug around your laptop to all of these places. Weirdo).

Nicole Mead and Vanessa Patrick had a bunch of dieters, one at a time, sit and watch a movie, each with a bowl of candy next to him. Some were told they shouldn't eat the candy, while others were told that they should hold off during the movie but could have the candy later.

As we approach the holiday (i.e. gift-giving) season, don't forget to make sure to include the usual notes in your gifts indicating that they can be returned. Otherwise, you'll just cause the recipients to save your gifts until they can be properly regifted onto some other ungrateful chump.

Anything free is cool, but getting a fully upgraded operating system for the great price of nothing is downright awesome. A recent exploit was uncovered that allows users to get a free copy of Windows 8 Pro directly from Microsoft's own website. Seriously.

As a technology writer, phone screenshots can pile up on your computer in no time. Testing out different apps, showing buggy software, and doing step-by-steps can lead to a plethora of mobile screenshots piling up on your computer's desktop. The problem with my screenshots is that they save as photo.png or photo.jpeg, as do many of my other photos. If I haven't finished a project or article, I tend to move them to different folders to save them for later. After a while, the screenshots begin ...

Cooking isn't something that interests me much, unless it results in a fast burning fuel and a successful rocket launch!

Thanks to Flutter, it's now possible to control the music on your computer simply by making a few hand gestures. The app is available for both Windows and Mac and uses your computer's webcam to monitor your hand movements. Through the use of a few simple hand movements, you can play, pause, forward or replay your music. Flutter works with iTunes, Spotify, Quicktime, MPlayerX and a few other programs.

Sea otters are the largest members of the weasel family. When people started hunting sea otters for their fur, their population fell from roughly 225,000 to about 1,500, until the International Fur Seal Treaty took effect in 1911. Since the international ban on otter hunting, the population has rebounded back to roughly 107,000.

Steam is an online platform that lets you download and play over 2,000 video games, from first-person shooters to RPGs, as well as a pretty long list of indie games. You can play on your PC, Mac, mobile device, or even your television, and it has a community of over 40 million gamers. Prices are different depending on the type of game and how new/popular it is, but they're generally about the same as what you'd pay for an Xbox or PlayStation version. They also have a decent list of free games...

Earlier this month, Adam Cudworth, 19, launched a camera attached to a weather balloon into the edge of space. Battling tough winds, freezing temperatures, atmospheric pressure and tumbling speeds, the teenager from Worcestershire, England was able to capture these amazing pictures of the Earth's upper stratosphere. How to Send a Camera into Space

Got an upset stomach or a little heartburn? America's favorite pink pill will cure it right up. But did you know that there's actually metal hiding in those chewable Pepto-Bismol tablets? Yes, metal. Technically, it's a poor metal, but metal's metal, right? Well, we do tend to eat a lot of iron in our diets, because it carries oxygen throughout our bodies, so consuming metallic minerals isn't anything abnormal. But you'd never think that Pepto-Bismol is actually made up of metal.

WonderHowTo has seen its fair share of dragon-related projects, from dragon wings, to dragon kites, to less-complicated origami dragons, but we've yet to see anything quite like this. Radio-control plane builder Richard Hamel built this incredible seven-foot-long, fire-breathing dragon using a JetCat P80 turbine and a 50,000 volt stun gun, with a 2.4-gigahertz touchscreen radio controller to fly it.

Believe it or not, it's possible to make your very own lava—if you have a furnace capable of heating up to 1,200 degrees Celsius, that is. Bob Wysocki and Jeff Karson started the Syracuse University Lava Project to study basaltic lava and give students a hands-on way (hypothetically, of course) to learn about it. Oh, and they also want to use it for art projects. Sign me up for that class! It all starts with 1.1 billion-year-old basalt gravel, which apparently anyone can buy. They put the gra...

Learn how to do single medicine ball on the shelf crunches. Presented by Real Jock Gay Fitness Health & Life.
When you're a writer with work published across various online platforms, building a portfolio of your work can be pretty time-consuming. That's where Authory comes in.

By now, you've probably been inundated with enough Baby Yoda memes to last you a lifetime. But if you don't have the new Disney Plus streaming service on your TV, you're probably wondering where all this is coming from. Well, lucky for you, just in time for the holiday season, we're here to guide you to the best ways to take part in all the streaming fun when you're not glued to your mobile devices.

Google is an incredibly useful database of indexed websites, but querying Google doesn't search for what you type literally. The algorithms behind Google's searches can lead to a lot of irrelevant results. Still, with the right operators, we can be more exact while searching for information that's time-sensitive or difficult to find.

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

Twitter's official iOS app is adequate if you're not much of a tweeter, but if you are, there's a lot of useful features that are missing. Luckily, there are plenty of free Twitter clients available that you can use on your iPhone. These third-party apps have features such as customizable interfaces, post scheduling, and different browser options for opening links, to name just a few.

In 2018, augmented reality went from the vague promise of interesting things in the near future to tangible developments in software and hardware, proving that immersive computing is indeed the future.

It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

As penetration testers, we sometimes need to securely store customer data for prolonged periods. Bruteforce-resistant, vault-like containers can be created with just a few commands to protect ourselves from physical attacks and unintended data disclosures.
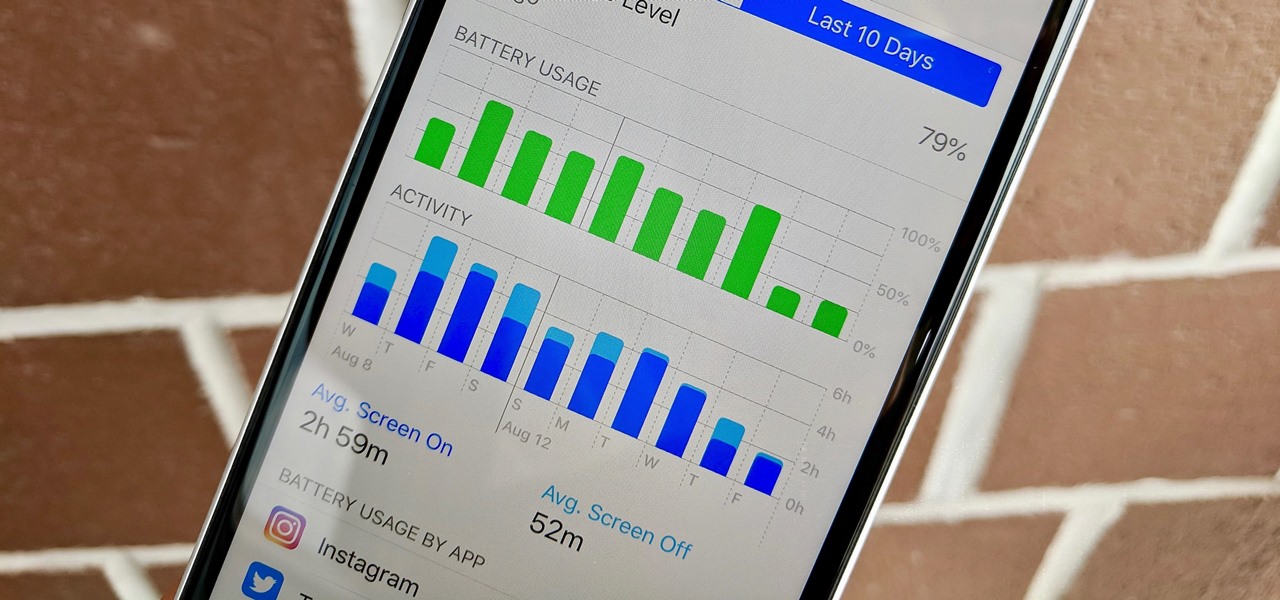
With iOS 12, Apple is making up for mistakes from the past, with iPhone batteries being no exception. The new update builds upon both battery health and performance throttling tools introduced in iOS 11.3 by offering users more information about your iPhone's battery usage than ever before.

In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmless scripts into persistent root backdoors.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even if the computer is off.

The Galaxy S9 is now in the hands of millons of excited users. Getting a new phone is always fun, but it's important to think about protecting your device. Perhaps the most popular cases for the Galaxy S9 are the official OEM options from Samsung. There are a plethora of cases, whatever your preference and needs may be. Let's take a look at each case individually, along with the pros and cons.
If you tend to use the app switcher a lot to open recent apps, then all of the apps you accessed months ago are just sitting there cluttering things up. While force-closing all of the recent apps on your iPhone isn't really necessary, it's sometimes nice to wipe the slate clean and empty the app switcher completely to start fresh.

Every other year, Apple comes out with "S" model iPhones that enhance and speed up their main series models from the previous year. This year, however, because of the highly-anticipated 10th anniversary iPhone, aka the iPhone X, Apple has dropped the "S" and moved straight to the iPhone 8 and 8 Plus.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

Recently, I ran across SecGen, a project which allows a user to create random vulnerable machines. I absolutely love vulnerable machines, since a vulnerable VM is a safe and legal way to practice hacking tactics, test out new tools, and exercise your puzzle-solving skills.

OpenVAS is a powerful vulnerability assessment tool. Forked from Nessus after Nessus became a proprietary product, OpenVAS stepped in to fill the niche. OpenVAS really shines for information gathering in large networks where manual scanning to establish a foothold can be time-consuming. OpenVAS is also helpful for administrators who need to identify potential security issues on a network.

Apple's been hard at work adding new features and finishing touches to iOS 11, and there's evidence of it everywhere. But there's one place where these changes are more noticeable than perhaps anywhere else — Safari.

Months before London-based Jonathan Moon would turn 30, he started musing over how to celebrate. While he had rung in past birthdays at home, he wanted to do something out of the ordinary as a farewell kiss to his twenties. A short ski vacation with friends felt like the perfect idea.

Harry Potter fans got a treat last week when Pottermore, a site created by Harry Potter author, J. K. Rowling, released a test that let users learn what form their Patronus protective charm would take.

Even if you haven't heard of ube (pronounced "OO-beh"), you've probably seen pictures of desserts made with this brilliant purple yam.

The headline above may have some spice addicts shaking their heads, but, believe it or not, there are people out there who either don't like or can't handle a ton of spice.

Welcome back, my neophyte hackers! In the world of information security, the most common intrusion detection system (IDS) you will ever encounter is Snort. As you probably already know, an IDS works similarly to antivirus (AV) software on your desktop; It attempts to identify malicious software on your network and warns you of its presence.

Upon reading the title for this article, I bet you secretly thought to yourself, "Yeah, I've got the perfect way to 'make' roast chicken: I go to the store, and I buy one!" Well, there's no question that there are some really tasty, convenient rotisserie chickens out there, already made and ready for eating or using in recipes.