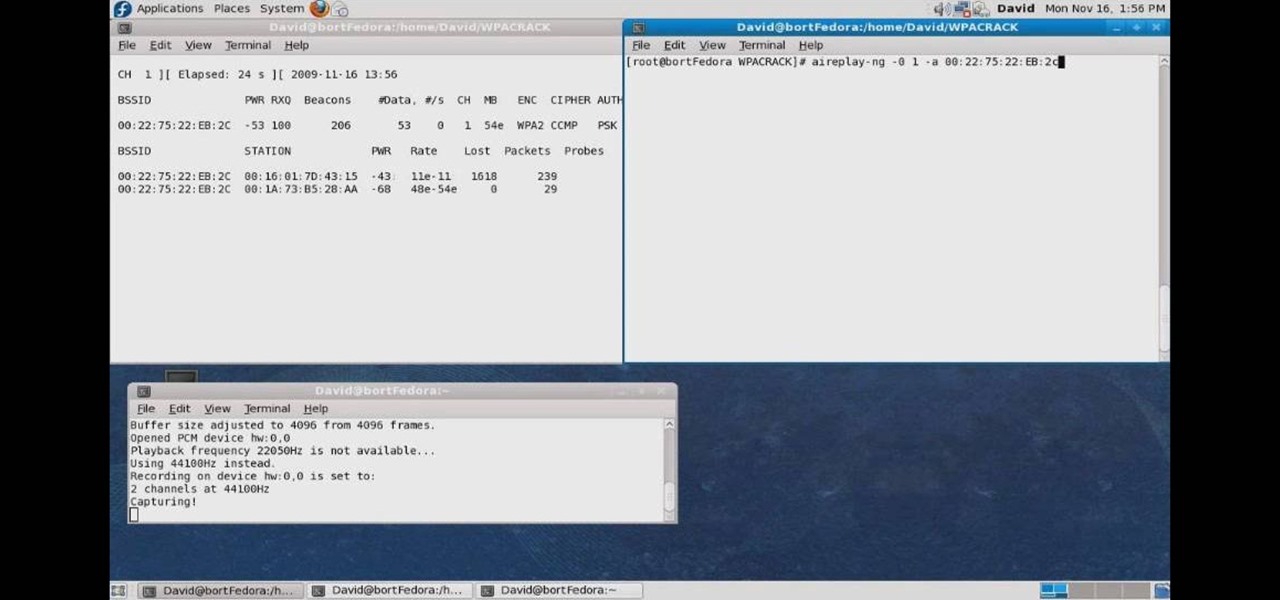
Want to test the security of your WEP WiFi wireless network? In this clip, you'll learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to use the BackTrack Linux distro and the Aircrack-ng WiFi security app to hack a WEP network. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to use the Backtrack 3 Linux distro and Aircrack-ng WiFi security app to crack the password to a WEP-protected wireless network. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.
Interested in setting up a WiFi network in your home or office? This brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, including detailed, step-by-step instructions, and to get started configuring your own wireless network, take a look.
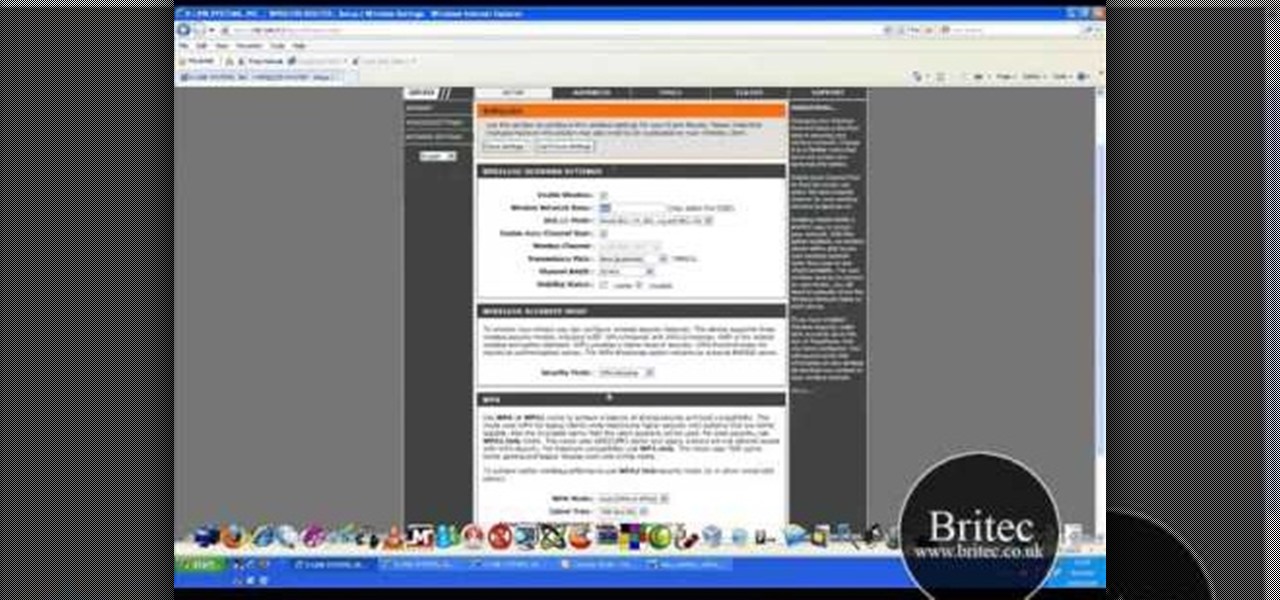
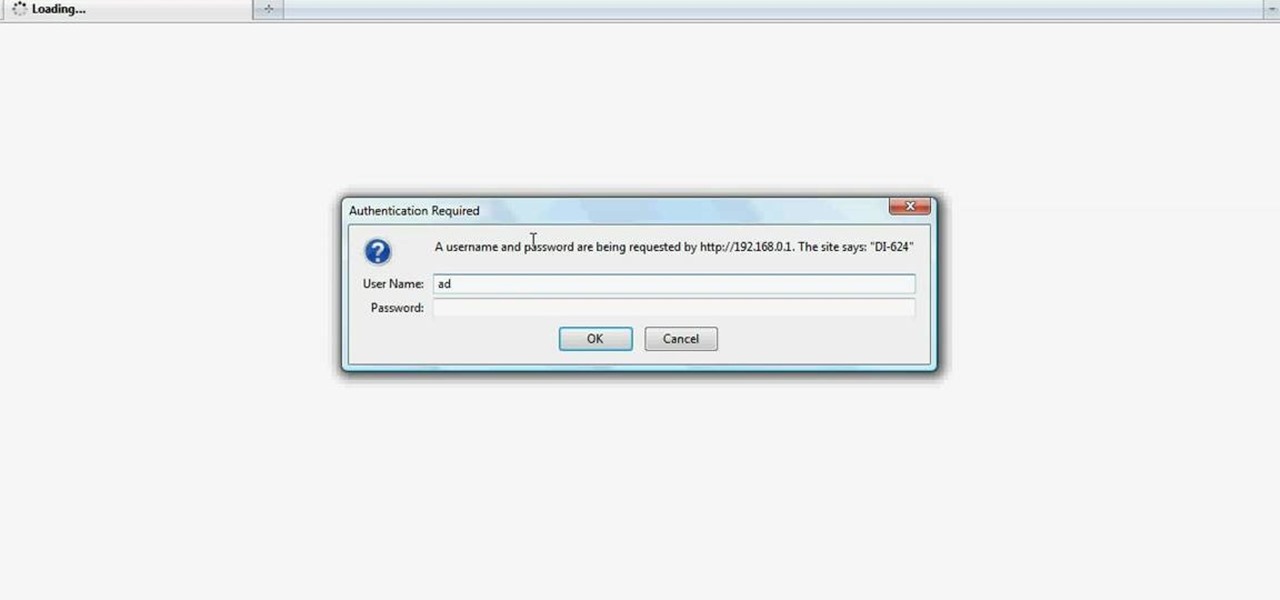
In this tutorial, Brian teaches us how to make your wireless network secure. First, go to the start menu, then go to run and type in "cmd", then type in "iconfig /all". Now a new window will pop up and you will look for the default gateway. Find the IP address to log onto the routers you have. Now, type in your IP address into your address bar on your internet browser. You will be asked to log into your account with your password and user name, which you can find at the manufacturers website....
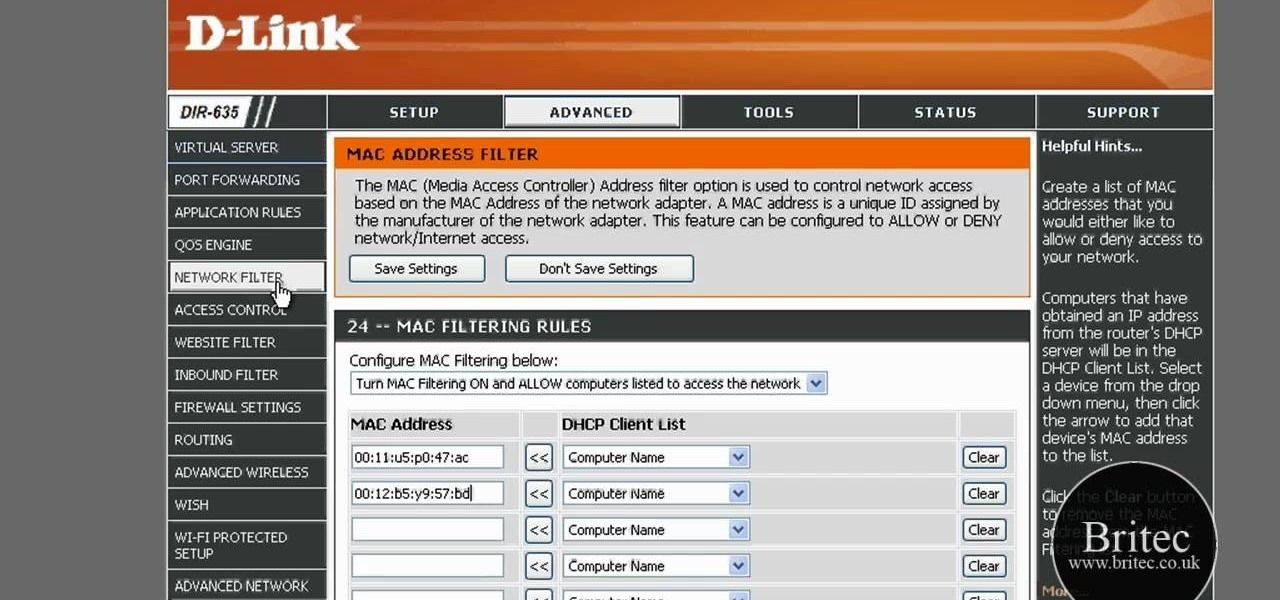
In this tutorial, we learn how to detect all computers connected to your Wi-Fi network. To begin, go to the website, http://msdn.microsoft.com/en-gb/netframework/aa569263.aspx. Once you are on this site, download and install the program. Once it's installed, open the program and then look for the MAC address. Once you find this, go back to the website and enter this into the MAC address line. After you do this, you will be able to see what computers are listed on your network. If you see any ...

Learn how to create & secure applications with BIG-IP v10. Whether you're new to F5 Networks' popular network appliance or are a seasoned administrator just looking to better acquaint yourself with BIG-IP, you're sure to benefit from this free video software tutorial. For more information, including detailed instructions, take a look.

Want to set up a wireless network in your home or office? It's simple. So simple, in fact, that this free networking how-to presents a complete overview of the process in just over four minutes. Set up a WiFi network with this video guide.

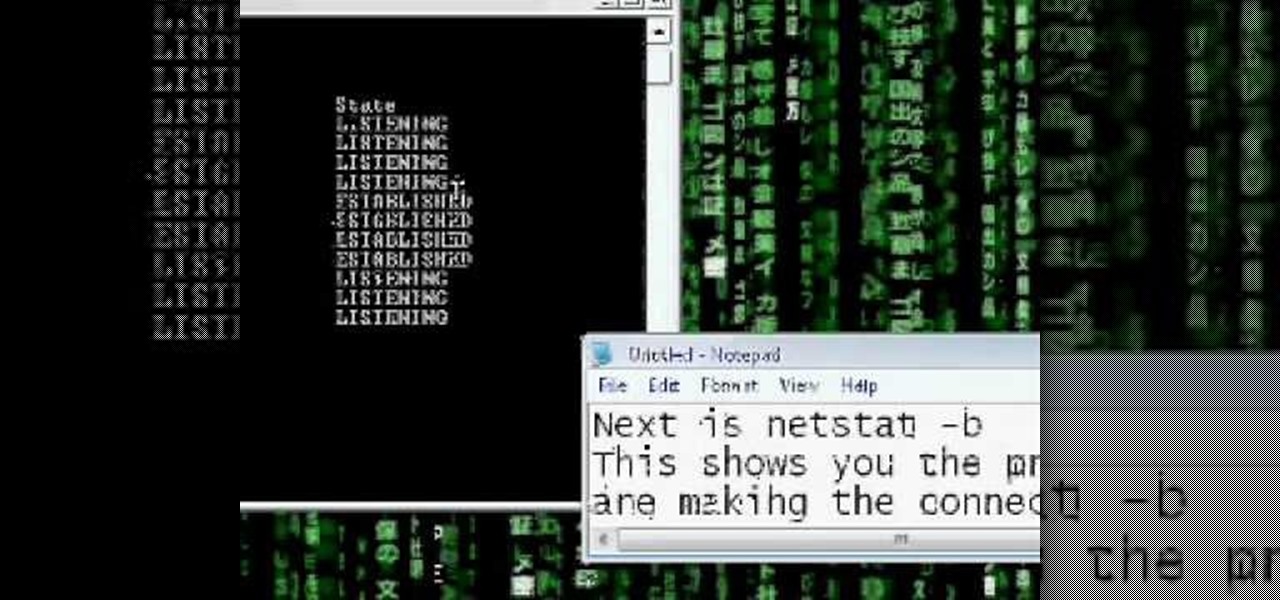
Netstat (network statistics) is a command-line tool that displays network connections (both incoming and outgoing), routing tables, and a number of network interface statistics. It is available on Unix, Unix-like, and Windows NT-based operating systems. This video tutorial presents a basic introduction to working with the netstat tool. Determine whether you've been hacked with this how-to.

So you know how to setup a network in your home, but how do you go wireless? The Lab Rats, Andy Walker and Sean Carruthers show you how to setup a wireless (WIFI) network.

This video tutorial is in the Computers & Programming category where you will learn how to secure your wireless internet connection. If you don't secure your wireless internet connection you are allowing others to enter in to your network. Open the set up CD and first change the network name from the default name to anything that you like. For this go to step 3 of 'naming your network', type in your network name and click 'next'. Then you enable security on the network by choosing 'WPA2'. Nex...

In this how to video, you will learn how to crack a WPA encrypted wireless network. To do this, you will need the Air Crack package for Linux. First, disable the wireless adapter and enable monitor mode. Next, identify the channel in the wireless network and Mac address. Once you have this, you can listen to the traffic coming to and from this point. Wait for the handshake or disconnect something in order to force it to reconnect. From here, you are ready to perform the attack. With any encry...

This video shows you the method to find if someone else is using your Internet connection. There are two methods for this. The first method involves opening the start menu and click on 'Run'. Type cmd in the text box which opens as a result of clicking on 'Run'. Type NET VIEW at the command prompt. This will show all people using your network. The second method involves going to Start menu. Go to Connect to and Show all connections. Click on My network places. Click on 'View workgroup compute...

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to map networks with Spiceworks.

Nmap ("Network Mapper") is a free and open source (license) utility for network exploration or security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they a...

This video will show you how to subnet using CIDR notation. If you're curious about how to determine networks, subnet masks, broadcast addresses and what makes a host range valid. A great video for anyone currently studying computer networking technology.

This video will teach you how to hack a WEP wifi network on a Mac. You'll need to follow the link, grab the prog and follow the steps. It's not too hard, so give it a try. Remember, stealing is illegal!

Want to see whether your PC is being accessed by hackers? Netstat (network statistics) is a command-line tool that displays network connections (both incoming and outgoing), routing tables, and a number of network interface statistics. It is available on Unix, Unix-like, and Windows NT-based operating systems. This video tutorial presents a basic introduction to working with the netstat tool. Determine whether you've been hacked with this how-to.

Anyone can set up their own wireless network. All you need is a little know-how. You will need a computer with wireless capability, a high-speed modem, a wireless router, and a broadband internet connection. Don't get tied to the wall; a wireless connection will allow you to move the computer freely around your home and still get an internet connection. Watch this video tutorial and learn how to hook up a wireless network at home.

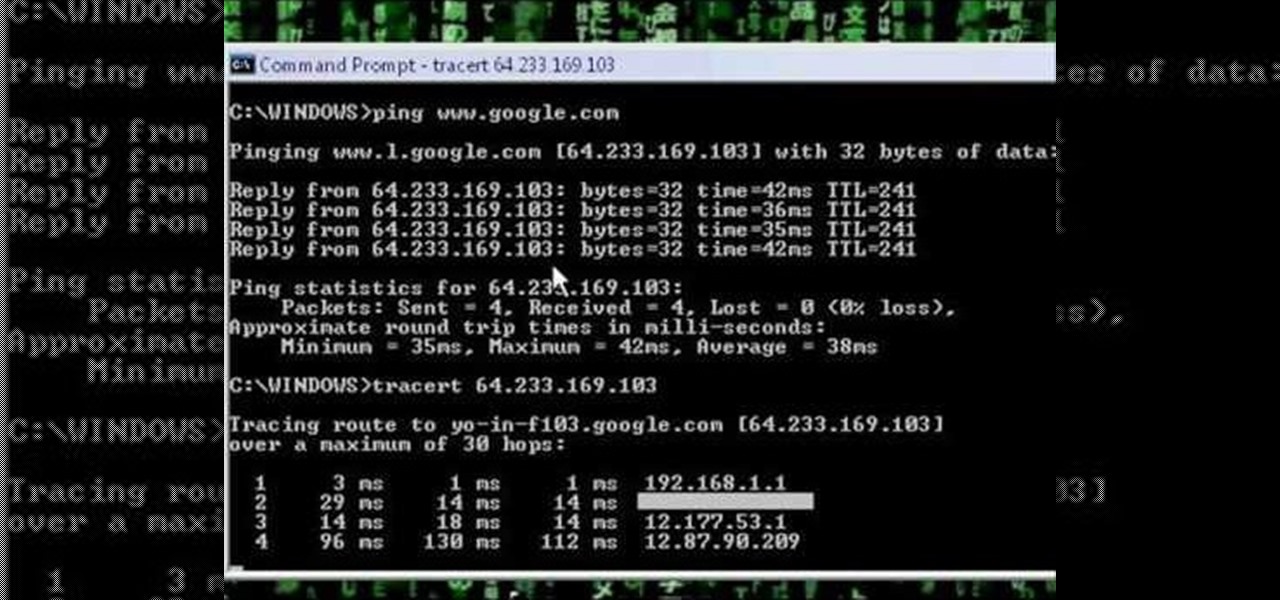
Tekzilla shows you how to troubleshoot network woes with ping and traceroute.

If you want to connect your Mac notebook or desktop to a wireless network, you'll need to set up the wifi connection on your computer first. Take a look at this walkthrough to find out how to find and connect to available wireless networks in OS X. This is a great skill to know if you own an Apple laptop and need to connect to the Wi-Fi networks at different locations.

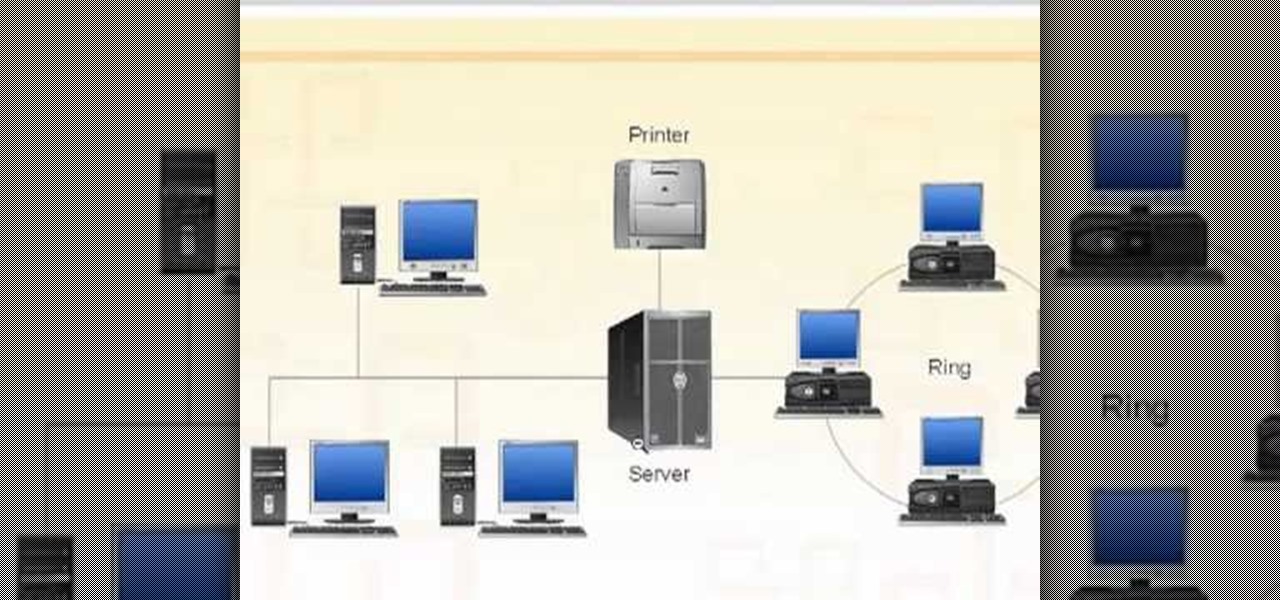
Need some help figuring out the ins and outs of LAN networks? They're easy enough to understand. And this brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, and to learn more about LAN networks yourself, watch this helpful video guide.

The first of a two part series on setting up your linux server and network for external access through your cable modem or DSL. Covers modifying the Linux servers network setting to a static IP address.

Need some help figuring out how to put a password on your wireless router? This home-computing how-to from the folks at CNET TV will teach you everything you'll need to know to do just that. For detailed information, and to get started protecting your own wireless network helpful video guide.

Netcat is a featured networking utility which reads and writes data across network connections, using the TCP/IP protocol.

If you're just itching for an excuse to reuse that retired desktop PC or laptop sitting in your closet there here's your chance. This tutorial offers a look at the basics of installing FreeNAS, an open-source DIY NAS. So instead of spending money on off the shelf options why not save yourself some cash and make use of the stuff you already have and get a super customizable network storage device to boot?

A network security tutorial on using ping and tracert to show th IP of a webserver, your own IP, your ISP's IP, who they connect to, and what computers your request goes through before reaching a destination.

Learn the ins and outs of do-it-yourself network cable installation including how to modify other cables into Ethernet cables.

Do you have an old computer that may be too slow to play video games? You may think it's totally useless, but CNET Video teaches you how to turn it into a network server that functions as a centralized depository for your files!

Who said sports need parity to be fun? For the third year in a row, the Cleveland Cavaliers are facing off against the Golden State Warriors on the NBA's biggest stage, and basketball fans everywhere couldn't be more excited.

WPA-secured wireless networks, or WiFI Protected Access, is a form of internet security that secures your wireless LAN from being accessed by unauthorized users. Safer than WEP, or wireless equivalent privacy, WPA still has weaknesses that are prone to cracking - IF, that is, you know what you're doing.

In this tutorial, you'll learn about the cables required for setting up a small home or office network. Fortunately, cable selection is an easy process and this video presents a complete guide. For more information, including a full demonstration and detailed, step-by-step instructions, watch this helpful home-computing how-to.

In this clip, you'll learn methods for troubleshooting and resolving the most commonly encountered WiFi wireless network problems. It's an easy process and this video presents a complete guide. For more information, including a full demonstration and detailed, step-by-step instructions, watch this helpful home-computing how-to.

In this clip, you'll learn how to set up a simple wireless network in a home or office. For more information, including a complete demonstration and detailed, step-by-step instructions, and to get started making phone calls over your own Internet connection, watch this handy home-computing how-to from the folks at CNET TV.

Need a hand figuring out how to set up a wired home LAN network? It's easy. And this brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, including detailed, step-by-step instructions, and to get started managing your own web pages with Google Sites, take a look.

Interested in setting up a network over your power line? This brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, including detailed, step-by-step instructions, and to get started setting up your own home network, take a look.

In this tutorial, we learn how to set up an HP wireless printer. First, click "setup" on the printer, then go to "network", then "wireless setup wizard". The printer will now go through the setup process and show you available wireless networks in your area. If your network requires a password, enter it by typing it in with the keypad. Now, install the software to any computer and wait for the blue wireless light to turn on. When this is done, you will be able to print wirelessly from any com...

Learn how to use BIG-IP Live Install on F5 gear quickly and simply. Learn how to upgrade BIG-IP with Enterprise Manager 1.8 quikly and simply. Whether you're new to F5 Networks' popular network appliance or are a seasoned administrator just looking to better acquaint yourself with BIG-IP, you're sure to benefit from this free video software tutorial. For more information, including detailed, step-b-step instructions, and to get started using Live Install yourself, take a look.

In this video tutorial, viewers learn how to secure a home wireless network. There are 3 types of security protocols for connecting devices. The 3 types of security protocols are: OPEN, WEP and WPA. Users should use passwords that are secure but no so obscure that they are unusable. The password should not be dictionary words. They should be mixed with casing and contain the user's phone number. Go to your router's website and log into the website. Find the setting for wireless security and e...

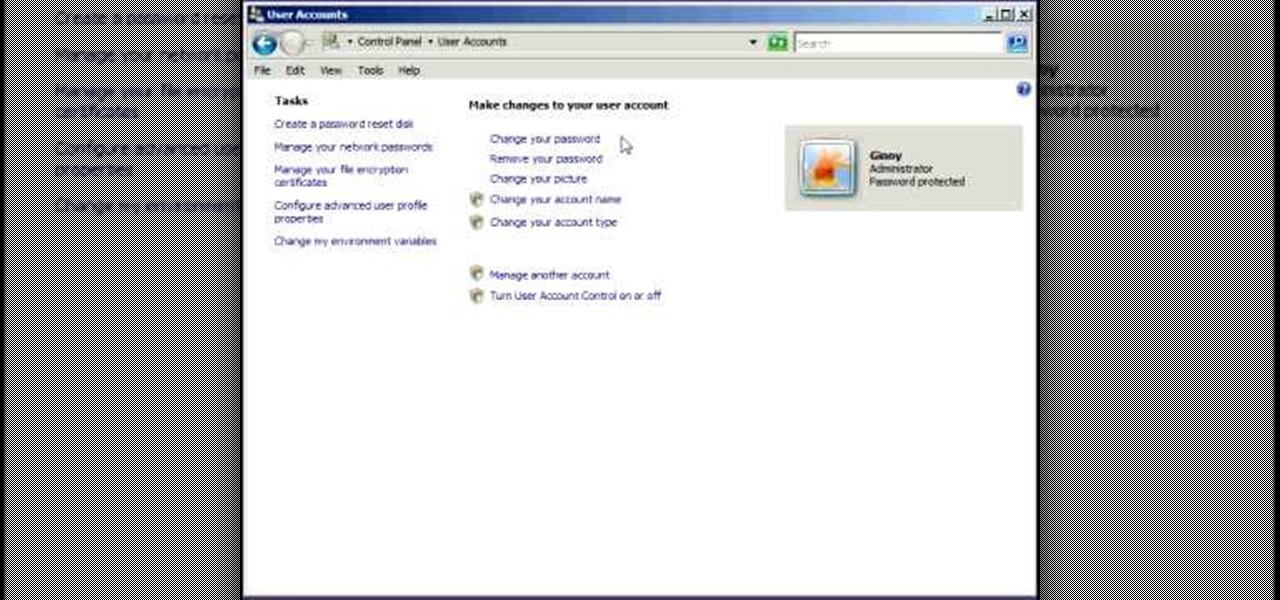
Remote desktop is a windows feature which can be used to access a windows computer from an other windows computer over the internet. Note that to access a windows computer using remote desktop the computer must run on Windows Professional or Ultimate version. Remote desktop does not work if the remote computer runs on Windows basic home version. However you can remote from a computer that runs on home version of windows. Another requirement is that the two computers must be connected over an ...