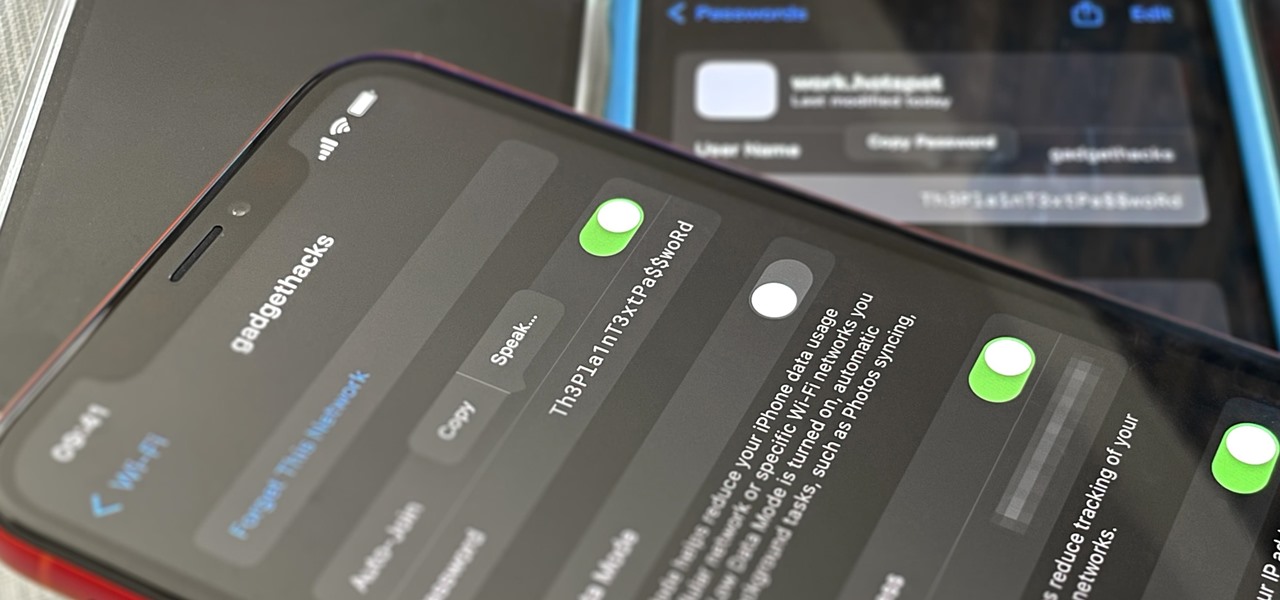
Your iPhone goes with you pretty much everywhere you go, and unless you have unlimited data on your cellular plan, you've probably connected to dozens of Wi-Fi hotspots over the years. Wi-Fi passwords are saved to your iPhone so you can auto-connect to the router or personal hotspot again, but finding the plain text password for a network hasn't always been easy.

We're living in uncertain times. The sudden outbreak of the novel coronavirus and subsequent self-isolation of roughly half the world's population has led to a massive reorganization of the economy, countless layoffs, compromised security networks, and a variety of other significant disruptions that will forever alter the landscape of our daily lives.
It's not so difficult to stay at home during the coronavirus lockdown when there's so much free entertainment to take advantage of. That seems to be the M.O. for many studios and streaming services, as they've made so many shows and movies available to the public for free. That said, they aren't running charities here. These deals won't last forever, so make sure to jump on board before it's too late.

One of the main goals of Google Wifi (and Nest Wifi after it) is to make managing your internet connections as simple as possible. A great example of this is how easy it is to prioritize one device and allot it more bandwidth when your network is bogged down with other traffic.

A virtual private network is a necessary part of your arsenal if you're insistent on surfing the web privately and securely on your iPhone. The App Store is littered with hundreds of different VPN services that encrypt traffic and mask your IP address, but what they all have in common are connectivity issues.

While augmented reality made more of a cameo appearance during Samsung's official grand unveiling of the Galaxy S10 line-up on Wednesday, it's the company's move into 5G connectivity that has huge implications for AR.

The most common Wi-Fi jamming attacks leverage deauthentication and disassociation packets to attack networks. This allows a low-cost ESP8266-based device programmed in Arduino to detect and classify Wi-Fi denial-of-service attacks by lighting a different color LED for each type of packet. The pattern of these colors can also allow us to fingerprint the tool being used to attack the network.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

The pending union between Prince Harry and American actress Meghan Markle is almost guaranteed to set the internet ablaze as millions tune in to experience the spectacle and pageantry of such a momentous event. If you've cut the cord and are wondering where you can stream the royal wedding for free, we've got you covered.

Hashes containing login passwords are transmitted between Windows computers on local Wi-Fi networks. By intercepting and decrypting these hashes using Responder and John the Ripper, respectively, we can learn a target's login credentials which can be later used to gain physical access to their computer.

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.

The Watch Dogs video game series came out in 2014, enamoring audiences with the idea of a seemingly magical smartphone that could change traffic signals, hack web cameras, and even remotely control forklifts. This may sound like science fiction, but The Sonic uses a customized flavor of Kali Linux to allow you to unleash the power of Kali from any smartphone — all without the need to create a hotspot to control it.

When hacking into a network during a penetration test, it can sometimes be useful to create your own wireless AP simply by plugging a Pi into an available Ethernet port. With this setup, you have your own backdoor wireless connection to the network in a matter of seconds. Creating an AP is also helpful while traveling, or needing to share a connection with a group of people.

Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

Toyota is testing blockchain and distributed ledger technology (BC/DL) for data sharing for driverless cars and other applications. This could eventually reassure buyers of its upcoming high-end cars by making sure their sensitive data is secure.

The Shadow Brokers, a hacker group known for its dump of NSA hacking tools in 2016, has just leaked their remaining set of data which implies that the NSA compromised SWIFT, the global provider of secure financial services, to spy on banks in the Middle East.

Copying files from a computer to your Android device has always been pretty straightforward—just connect the two devices with a USB cable, open your desktop file explorer, then move the files over. But what if you didn't need any wires at all?

So you're finally ready to head out on that big trip you've been planning for months, huh? It's an exciting time, but there are plenty of things you'll need to prepare before you head out. For instance, it's hard to imagine life without a smartphone these days, and with useful traveling apps like Google Translate and maps, you'll almost have to make sure that you have a working smartphone when you arrive at your destination.

I have came across a lot of members on the forum that didn't have a clear idea of what port forwarding is and what it does. So...Let's get started...

Welcome back, my tenderfoot hackers! Generally, you will want to perform a vulnerability scan before doing a penetration test. Vulnerability scanners contain a database of all known vulnerabilities and will scan your machine or network to see whether those vulnerabilities appear to exist. If they do, it is your job to test whether they are real and can be exploited.

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.

Welcome back, my tenderfoot hackers! A number of you have written me telling me how much you enjoy the Mr. Robot series on USA Network. I am also a huge fan! If you haven't seen it yet, you should. It may be the best show on TV right now.

Your Apple Watch is a fantastic tool that can help you perform daily tasks on your iPhone. Notifications get filtered through it, you can respond to messages on it, and you can even use Apple Pay to purchase goods and services. Your Apple Watch is also a valuable asset when it comes to finding your lost iPhone, too.

Welcome back, my greenhorn hackers! Before we attempt to exploit any target, it is wise to do proper reconnaissance. Without doing reconnaissance, you will likely be wasting your time and energy as well as risking your freedom. In previous guides, I have demonstrated multiple ways to perform reconnaissance including passive recon with Netcraft, active recon with Nmap or hping3, recon by exploiting DNS or SNMP, and many others.

The international hit Xperia Z2 may be headed to Verizon if a posted, and quickly erased, image is any indication. Take this information with a grain of salt—I certainly am—but this could be Sony's entrance into the non-GSM realm. The image above was posted to Sony's Xperia Google+ page, and very quickly removed. Compared to the Z2 that's currently on the international market (below), we can see that not only has the Sony logo shifted to the bottom, but a Verizon logo rests squarely along the...

Whenever a new version of a phone comes out, there's always that one cool feature you wish you had on yours. For me, that's Group Play.

In this short video tutorial, you will learn an easy technique on how to draw Chowder from the Cartoon Network series of the same name. For the full tutorial with step-by-step and speed control, visit SketchHeroes.

Learn how to draw Ben 10 from the famous Cartoon Network animated franchise. For the full tutorial with step-by-step drawing instructions and speed control, visit Sketch Heroes.

I remember how fast my Nexus 7 was the first time I turned it on. Boy, do I miss it. Now my tablet is pretty buggy and crashes happen frequently, and I'm sure that goes for many of your Nexus 7s as well. Even if you upgrade to the new Nexus 7 next week, it will eventually develop similar issues.

Welcome back, my fledgling hackers! In the first part of my series on Wi-Fi hacking, we discussed the basic terms and technologies associated with Wi-Fi. Now that you have a firm grip on what Wi-Fi is exactly and how it works, we can start diving into more advance topics on how to hack Wi-Fi.

A wave of shock and anger swept across the country after Edward Snowden released private documents recounting the U.S. government's secretive mass surveillance programs. Although some of the fear was unwarranted (they don't read your emails or listen to your calls), many scrambled to find privacy of new heights for protection from the all-watchful eye. While the government may not be tracking you down, there are a myriad of other candidates that fill that Big Brother role—and I'm not talking ...

When this problem occurs most Windows users feel desperate because it can happen' at any point, every 10 seconds, minutes, hours - you name it and they don't know how to solve it.

Firewall is necessary to protect a computer network from hostile intrusions. You can easily setup your Firewall setting. This video helps you to do it.

MAC addresses (not to be confused with Macs) are unique identifiers assigned to network devices in order to access the internet. Hotels use these Mac addresses in order to check if a registered patron has agreed to their terms and conditions, how much bandwidth is being consumed, and of course, whether they've paid or not.

Thinking of deep frying a turkey this Thanksgiving? Careful, or this might happen: Video: .

In this video, Food Network's Ina Garten shows you how to make flourless coconut macaroons. First, you need one bag of shredded coconut emptied into a large bowl. Next, pour a 14 ounce can of sweetened condensed milk over the shredded coconut. Then add a teaspoon of vanilla extract to the bowl. Fold the ingredients together with a spoon until they are well mixed. The next thing you need is some whipped egg whites. To do this, you will need about 3 egg whites separated from the yolks. Pour the...

This video takes us through a process of speeding up our internet connection using OpenDNS.com. Open the webpage and go to solutions and click on the icon open the DNS page and it lists computer or router, she selects computer and list of operating system is listed, she selects vista. She goes to start and selects control panel, click on view network status and connection, in that select view status and then click on properties and on the networking page, go to internet protocol version 4 and...

Running out of costume ideas for your next Halloween? How about a tutu-clad ballerina, french maid, pirate or fairy? Or if you're brave enough, why not wear a tutu to the supermarket? ThreadBanger shows us how to make a tutu out of an old petticoat, some tool, and ribbon... This project takes a while to complete, but once done, you'll be the bell of the Halloween ball! And isn't that worth any amount of sewing?

ThreadBanger pays homage to the movie "Fame" by showing us how to make the perfect "80's-tastic" duffel bag out of old umbrellas. With this thrifty idea, you will need a few umbrellas (broken is fine), scissors, a square pattern, a sewing machine, a zipper, and anything handy that will work as a strap. Use your new custom duffel bag to carry all your leotards or dance shoes in, or make a statement on your way to the video store to rent "FAME!"

ThreadBanger's Decor It Yourself show us how to "do it yourself" when making a wine rack using just scrap wood and old belts. At a great size, it's easy to store and great to give as a gift. Looking to fill that wine rack and don't know where to begin? In the later half of this video, the gals from ThreadBanger take us wine tasting and give advice for your next wine shopping excursion.