RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices.

Virgin Wireless, perhaps best known for Sir Richard Branson and all of his antics, is an affordable cellular option here in the US. Virgin customers can enjoy — if that's the right word for it — Sprint's cellular service, at a discounted rate, however, there are usually some compromises for that. Now, there will be yet another compromise for Virgin customers who don't like iPhones — Virgin will now only carry Apple's phone on their network.

UPDATE 5/12: According to Bloomberg, it looks like the merger is on. Anonymous sources claim discussions have already begun about consolidation. Looks like there might be a new 5G powerhouse after all.

General Motors Co. (GM) is set to expand their fleet of driverless cars in San Francisco, Detroit, and Scottsdale, according to documents filed by the company.

ProtonMail has long been the favorite of journalists and security-conscious professionals, with Edward Snowden the most famous example. But these days, everyone cares about anonymity, so it's no surprise that ProtonMail currently has over 2 million users. And now the service is even better.

You might notice that there's been a few changes around here. All of us here at WonderHowTo have been working hard to create fun new spaces and topic areas to dig our heels into. We've created a few brand new websites, spiffied up our design, and today we're launching the WonderHowTo network.

I've seen my fair share of heartbreaks when it comes to used phones. As a repair tech, I often had to try and help out customers who bought used handsets which turned out to be useless, either because it was stolen or not working on their carrier's network. More often than not, there was very little I could do. To help you from being stuck in the same situation, here are some tips to prevent you from getting scammed out of your hard earned money when buying a used handset.

The Pixel and Pixel XL come with an awesome data-saving feature called Wi-Fi Assistant that automatically connects to open internet hotspots, then creates a secure VPN on your device to keep your data safe.
Hello guys I am ROMEO 64 (sounds weird I guess but who cares. :D).. Alright....Ever wondered what happens when you login to your Facebook account?

Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elliot asked him for some info that were really useful to gain access to his account, the target believed to be someone from the bank and gave him the info Elliot was looking for. But How Is It in the Real World?

Welcome to the Part 2 of the series 'Cryptocurrency'. It has been late because of some errors, where all I typed was lost.

How to do an NMAP scan on Armitage to find IPs within a certain range. Armitage is a gui interface of Metasploit, and advanced hacking/exploiting program. It can be downloaded from http://metasploit.com/ and http://fastandeasyhacking.com/ and you will need NMAP. http://www.nmap.org/

If you haven't read the last article, feel free to stop by and give it a read, but abstaining from reading it will not, for the most part, be detrimental to your understanding.

T-Mobile's "Uncarrier" initiative has done wonders for my wallet and my data usage. Before I had to deal with being throttled down to 2G speeds after passing my data limit, but thanks to their unlimited data plans, I'm free to use as much LTE data as I possibly can. The only downside is, when sharing data through a mobile hotspot (tethering), T-Mobile imposes a 5 GB limit (which was recently upped to 7 GB for some).

Hi there again, aspiring hackers (and veterans as well)! I'm going to explain how to perform a dictionary attack on a WPA/WPA2 protected network with Wifite. Please note that this doesn't work with WPA Enterprise For that end, you'd have to use an Evil Twin to get the "Enterprise" auth attempt, and then crack it.

Rumors have had Google making a foray into the mobile carrier world for quite some time, but today, the Mountain View tech giant finally made things official. The new service, dubbed Project Fi, will be a Mobile Virtual Network Operator, or MVNO, that uses existing Sprint and T-Mobile cell towers.

Collaborating with other people can be a pain, especially if you have to share one device between the entire group. Usually when you're creating a new design or trying to edit a mockup, you end up hunched around a single screen or end up emailing revisions back and forth, which can be difficult when you're short on time.

Sling TV, the new over-the-top TV streaming service from DISH Network, is the first to offer live programing for cord cutters. Available for $20 a month with no contract, Sling TV is the easiest way to end the reliance on cable and satellite subscriptions for getting your content as it airs.

iTunes Radio, Apple's answer to Pandora, provides endless hours of free music streaming, but like other so-called "free" services, every now and then you're going to hear some ads. While you may not be bombarded with them, they can definitely kill the vibe when you're jamming to your favorite stations.

Ever use an open hotspot on your Note 3, only to find out that it's severely restricted to what sites you can access? While getting online with free Wi-Fi is great for those who have a limited data plan, when that one site you absolutely need to visit is blocked, you're left frustrated and sent back into the Wi-Fi menu for another access point.

Remember the feeling you had the moment you removed your shiny new Nexus device from its packaging and booted it up for the first time? You swiped through the app drawer at lightning speed and thought to yourself, "This is the last Android phone I will ever need, they just aren't going to get any better than this."

I have Verizon, America's largest 4G LTE network, as my cell service provider, but there are times when I find myself with a pretty shitty signal, rendering my upload and download speeds substantially slower than usual.

Welcome back, my neophyte hackers! Have you ever had a neighbor that you're certain is up to no good? Maybe you've seen him moving packages in and out at all hours of the night? Maybe you've seen people go into his home and never come out? He seems like a creep and sometimes you hear strange sounds coming from his home? You know he's up to no good, but you aren't sure what it is exactly.

Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Although far from the most commonly used database (Oracle hold's that title), Microsoft's SQL Server is very often found in small-to-medium sized businesses. Even a few big businesses use it.

For the most part, transferring files from your computer to your Nexus 7 (and vice versa) is a simple process. Just hook up your tablet to your computer with the USB cable and transfer. However, most of the time you'll need additional software on your computer to do this, and then, of course, you need the USB cable.

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

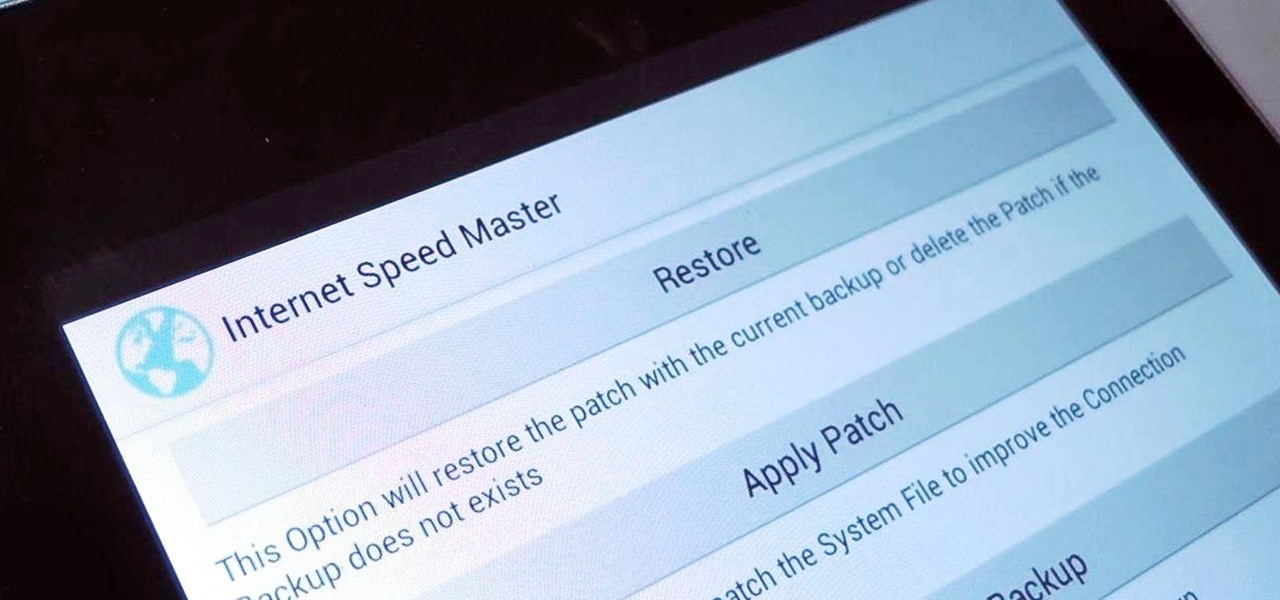
Even if you have the fastest internet connection in the world, it's not going to be fast if your Android device isn't optimized to use all of the bandwidth. I have pretty fast speeds at home, but every now and then my web surfing on my Nexus 7 tablet is halted in its tracks—for seemingly no reason.

Welcome back, my fellow hackerians! Today we'll be hacking Facebook profiles on your local network. You may think, "How is this useful, nobody but me is using my network." Well, you can use this on other Wi-Fi networks that are available for free (like at Starbucks) and crack their precious Facebook profile!

Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. The disadvantage, of course, is that it's limited to only some websites and not entirely reliable.

When LinkedIn first arrived on the scene, I thought it was a great resource for staying connected and getting in touch with those people in your desired career path. Keyword: Thought. Like most businesses, money and shareholders seem to have taken over the driver's seat, pushing the company towards a business-first, users-second approach.

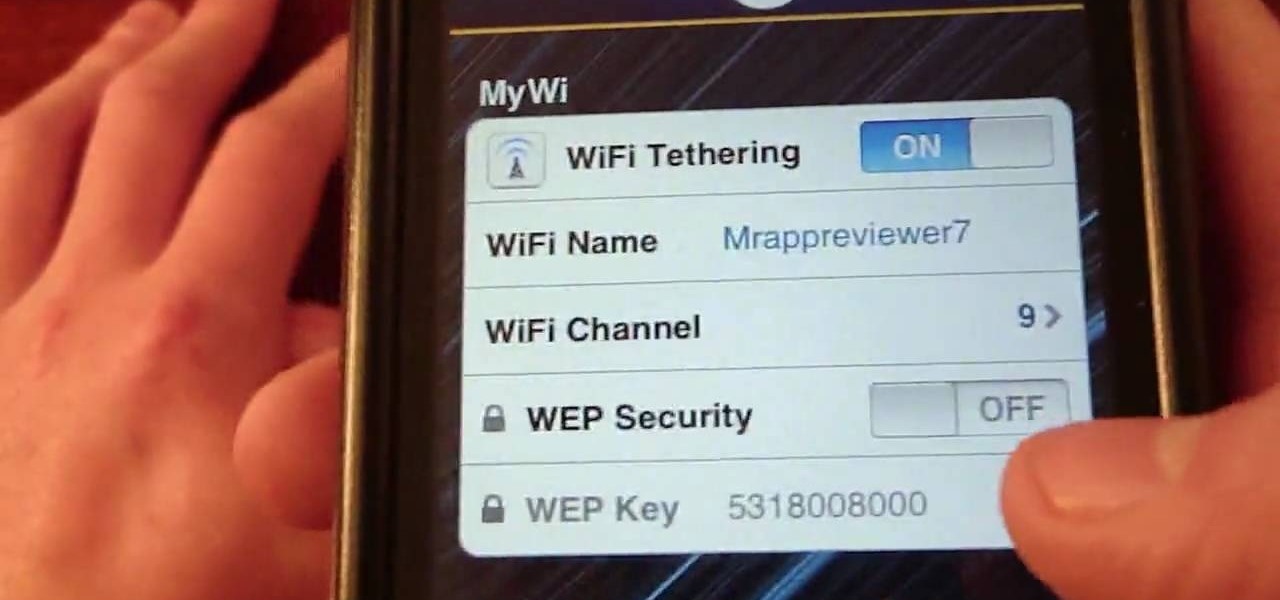
You will need a jailbroken iPhone to make this work (won't work for iPod Touches, sorry). When you get the MyWi app from Cydia, you can turn your iPhone into a mobile hotspot using the 3G network. You can even set up your new hotspot to have a password and protect it. This connection will be a little slow, and is dependent on your reception as well. But now you can take an Internet connection with you wherever you and your iPhone go!

In this video we learn how to use EyeTV to stream live TV on your iPhone. This will allow you to watch TV on your Mac and your iPhone as well as on a 3G network for free. To get started, plug one end of the EyeTV into the USB plug and then into the jack on the hybrid with a cable line. Now, download the most recent version of the software from the update menu. Then, go to preferences and select iPhone. After this, make sure all the buttons are selected, then exit out. Now go to your iPhone an...

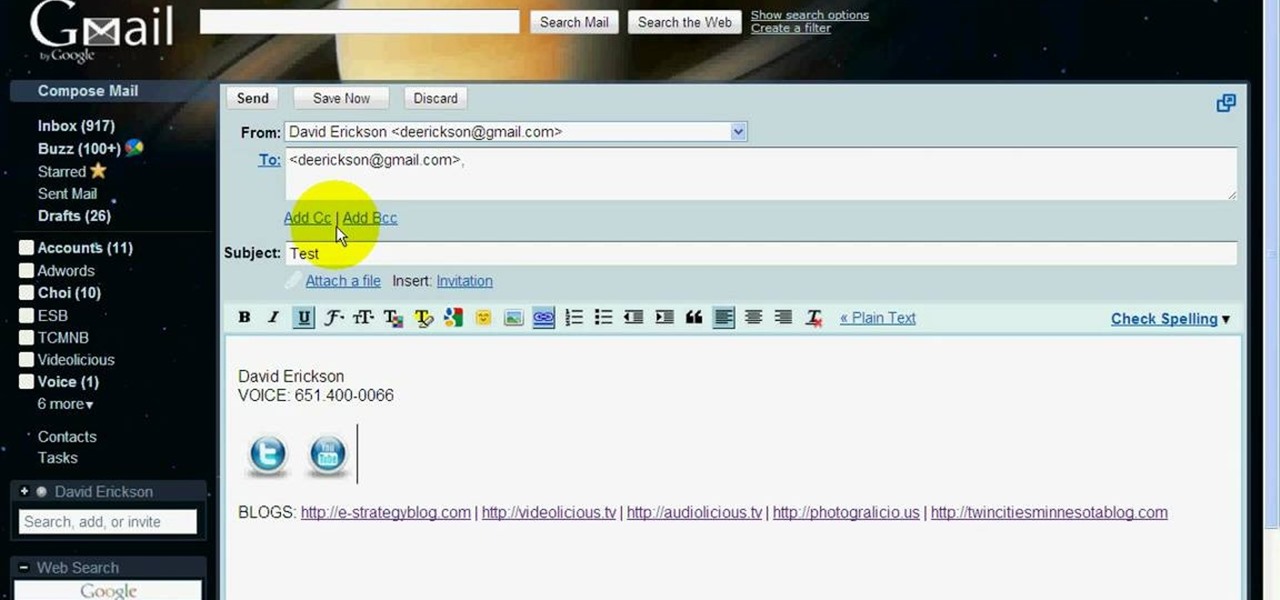
If you're getting bored of the same old same old in your e-mail messages, or if you're looking for an easier way to show off each of your social networking, as well as personal websites, then you will be happy to hear that Gmail has finally introduced rich text signature lines that'll allow you to hyper-link your images in your signature via HTML. All this can be found in the Labs section of your settings in Gmail. In this video you will learn how to set up the signature with the images and h...

According to domestic goddess supreme Martha Stewart, you should always eat fresh, and even grow your own vegetables and herbs in your backyard if you can. But for those of us who are urbanites and don't have as much as a square foot of balcony space, it's not always possible to eat as fresh as we want.

Just hearing "brie" and "baguette" were enough to get us interested in this delicious summertime recipe, but Food Network host Sandra Lee amps up the classic baguette topped with brie recipe by adding raspberry jam.

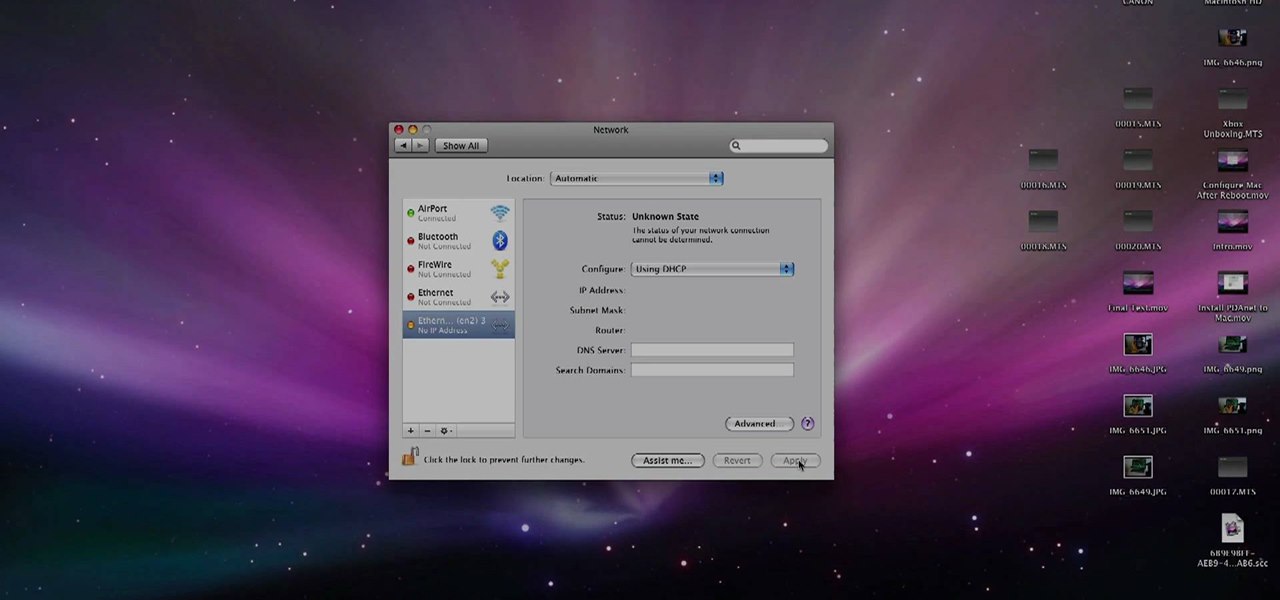
If you have an Android-based cell phone and want to tether it to your MacBook, MacBook Pro, or other computer running Mac OS X software, the secret lies in a little application called PdaNet.

Grilled Zucchini Ribbon Salad-Food Network Grilling vegetable is by far one of the healthiest ways to eat them. Grilling certainly beats throwing them in a vat of lard (we're looking at you, Paula Deen) or chucking them in a bread batter to make zucchini tempura (yummy, but not so good for your six pack).

Frittatas are a delicious and healthy meal. They include almost all of your food groups and are packed with fiber. The basic concept behind frittatas are that you can throw whatever leftovers you have into a bowl with eggs and create a unique version every day! In this recipe, Giada De Laurentiis from the Food Network shows you how to make a lighter version with egg whites so that you can avoid some of those calories and cholesterol. Enjoy!

In this clip, learn how to make a perfectly fresh tomato salsa with Ellie Krieger from the Food Network. Ellie walks you through the process of pulling together this spicy sauce in less than five minutes. All you need are your veggies and a blender and you're on your way. So, when you have friends coming over and you've forgotten the dip - no need to worry, whip this up and you'll have snacks on the table before anyone even notices you were gone.

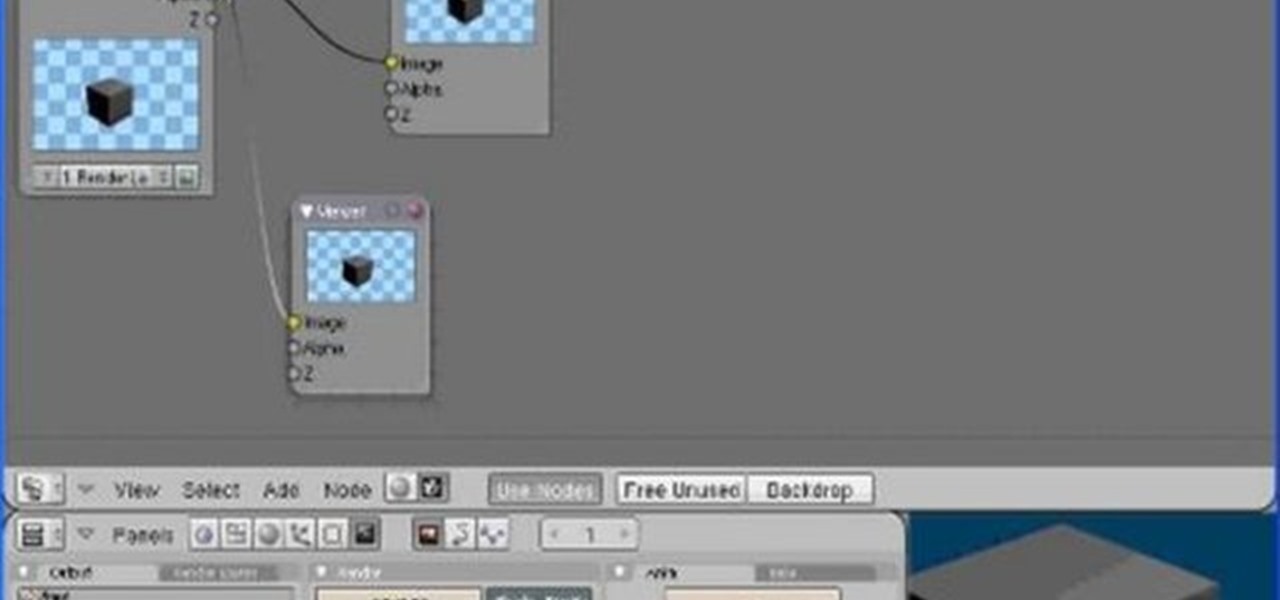
Conceptually, what is node-based compositing and what do nodes do? This clip uses the factory analogy to convey the concept. Blender can process video, images, sequences, and families of images in a directory. Then you'll fire up Blender and talk about threading nodes and how images are duplicated and routed through the compositing network ("noodle"), how threads are created between sockets. Creating threads, cut threads. The clip also points out common threading errors and misrouting threads...