How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.
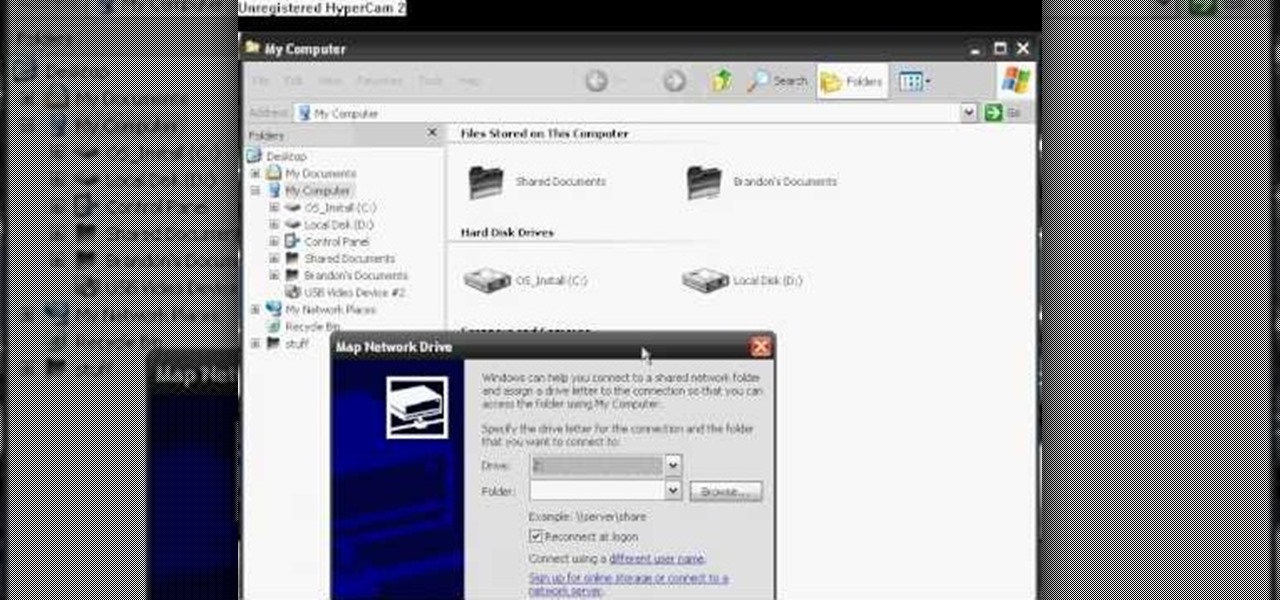
This tutorial will walk you through the steps you need to map a network drive for file access in Windows XP. By mapping your network drive you will be able to store and access files offsite and make computing easier all around.

This video shows you two methods to connect to XBox Live using a laptop. For the first method, go to your start menu and open up your control panel. In the control panel window find the area marked Network and Internet and select the option View network status and tasks. In this new window, select Change adapter settings in the left hand pane. You will be presented with another window that has your network connections listed. Right click on your Wireless Network Connection and select properti...

In this video the instructor shows how to map a network drive in Microsoft Windows XP. Network drive is similar to the disk drive that is present on your computer like C drive, D drive but instead of pointing to a hard disk on your computer it points to a server that has enabled shares. Shares allow you to create or edit files and folders. By mapping that server share to a folder in XP you can use that share as a normal drive. To do this go to start menu, right click on My Computer and select...

Veronica from Tekzilla teaches you how to monitor network activity on Windows 7. Go to ITSamples and download the Network Activity Indicator program. Install it and run it. This will add a new icon on your system tray. It blinks to reflect incoming and outgoing packets. You can right click to see a more detailed report. You also get statistics and a menu for your network and firewall settings. So to get the popular windows XP type network indicator icon all you need to do is follow the steps ...

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

Wi-Fi signals have limited range, so if you live in a two-story house or work in a larger office, you may have set up multiple routers or repeaters to ensure full wireless coverage. Sadly, Android handles the transition between networks pretty poorly.

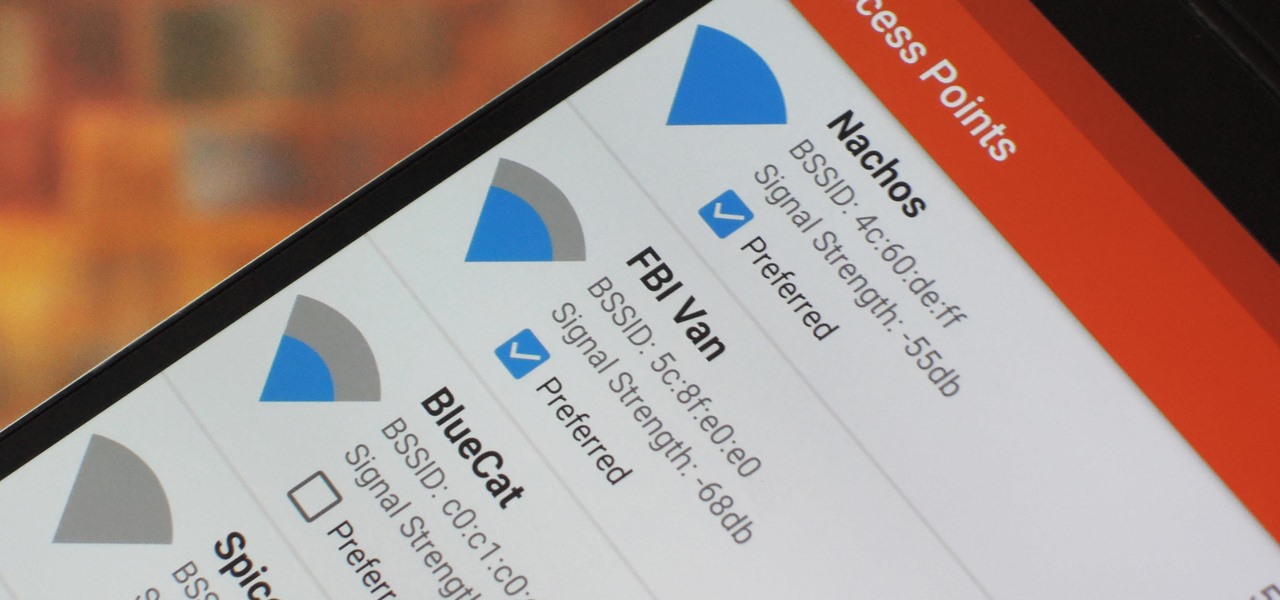
Android has released a new application called ezNetScan, which is a free app that scans the wireless network you're connected to and gives you a full log of all of the devices connected to that network. This isn't new for smartphone users, let alone Android users. Fing has been around for a while and does practically the same thing that exNetScan does. It gathers information such as the IP and MAC addresses, device vendors, and ISP location. But while Fing is a great program, it does lack a f...

In this tutorial, we learn how to map network driers from a remote server. First, go to run on your start menu, then type in the id address or server name for what you want to access and press enter. Now, right click on the folder you want to map and click on map network drives. Choose any letter you want from the drop down menu, then click next to the "reconnect on logon" text. Click on the finish button, then open your newly mapped network drive from your computer. You can do this for any s...

In this Electronics video tutorial you will learn how to tether a laptop to a Droid Smartphone for free Wi-Fi. For this you will need the android wifi tether application. Download the version for your device from here and install it. Then launch the app and press the icon to start tethering. In your laptop, go to settings and then to wi-fi. You will see a new network called android tether. Connect to the network and you will see that it works. As with any other network, you can change the nam...

In this tutorial, we learn how to set up and secure a wireless router. First, take your cable and plug it into your modem from your computer. After this, plug in an Ethernet cable into your modem to a wireless router. Now, plug the wireless router and modem into the wall. Now, look for the icon on your computer that says you have connected a new device to it. Go through the set up wizard to make a new wireless network, once it doesn't find one, connect a USB to the computer. Now, click on the...

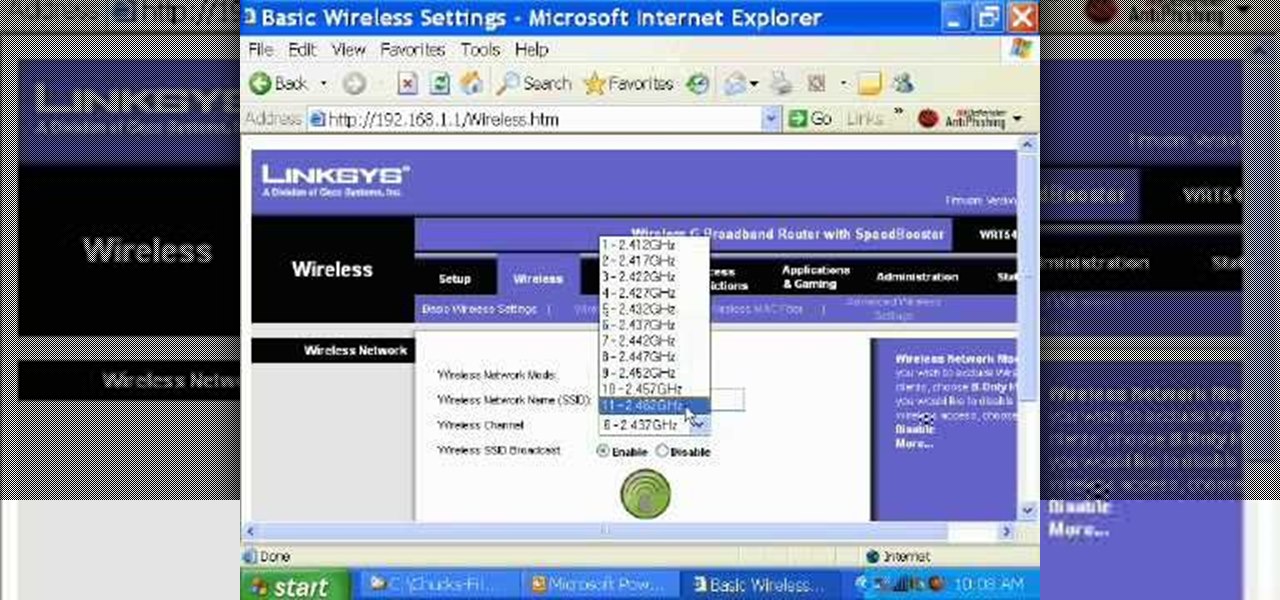
This video tutorial is in the Computers & Programming category which will show you how to set up a Linksys WR54g or WRT54g2 wireless router. First you connect to your Linksys router. Then go to http://192.168.1.1 and type in "admin' as your password in to log in window and click "log in'. then go to the "wireless' tab and enter your wireless network name. In the wireless channel select '11 2.462GHz' and click save. Next go to "wireless security' and type in the wireless network key. This is t...

Wireless networks are really the only way to go these days. With WiFi you can access the world wide web from almost anywhere, at anytime, and not have to worry about annoying wires or cords. In this tutorial, learn how to set up a wireless connection in a Windows Vista based machine.

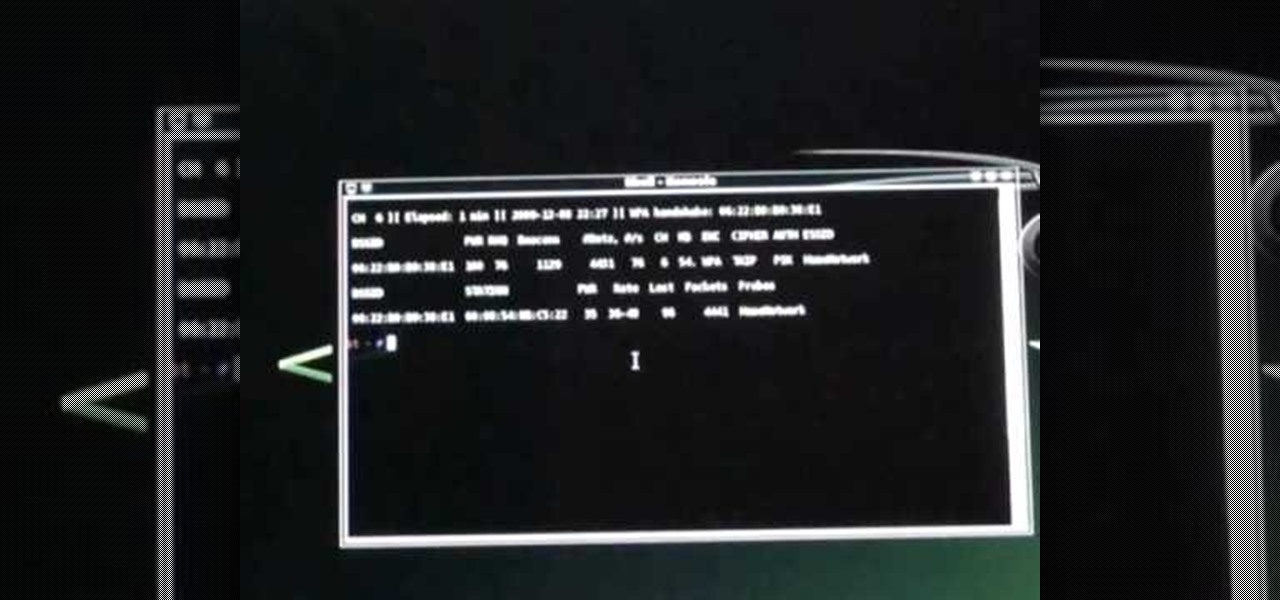
In this video we learn how to crack WPA using Back Track. The first step is the boot into Back Track using a VMware Virtual Machine Image. Next you need to open a shell console. In the console you will type "airmon-ng" and press enter. This does a check to find the wireless guard interface name. Next, type "airodump-ng wlan0" and press enter. This will tell it what wireless card to use and scan for wireless networks. You are looking for the one that comes up WPA. Copy the MAC address then typ...

Ever had router trouble? Got router trouble? Well don,t worry the people over from quickcert.com have made this video to help! More specifically a linksys 802.11g router. All new routers come with a standard Ethernet cable, which must be plugged into one of the four ports on the router and connected to your computer as well. This is necessary to change settings, using Microsoft IE (internet explorer) when the routers IP is typed into the address bar. It is strong recommended to change the def...

Are you serious about becoming a bonafide hacker? Then you simply must learn how to hack SSL passwords using ARP poisoning. ARP poisoning, also known as ARP spoofing, involves attacking an ethernet wireless network by looking at the data frames on a LAN (local area network). Resultingly, you can sniff plaintext passwords, SSL passwords, and even manufacture denial-of-service attacks.

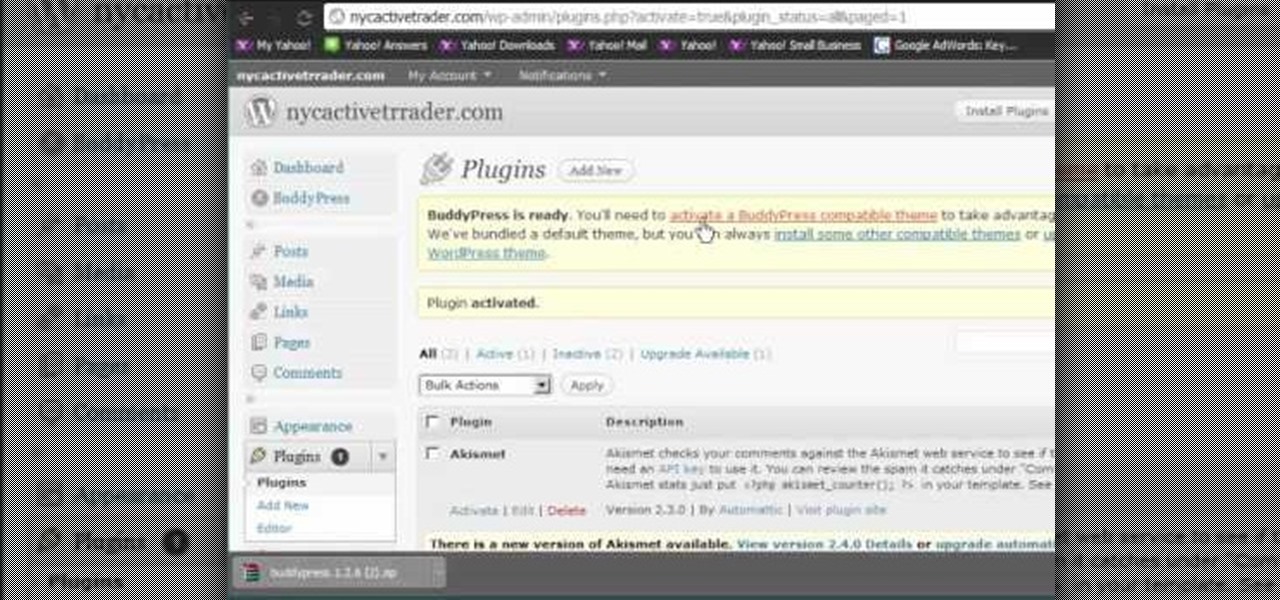
Like Facebook so much that you want to make your own version of a social network, just for you and your friends? It's totally possible, thanks to BuddyPress, a DIY social network for a tight community with the power of WordPress. This video will show you the steps to installing it and setting up your own social network.

You keep all kinds of important and sensitive information and data on your computer, and if your hard drives crashes, you're done for… unless you've backed it up. CNET has some "Insider Secrets" on how you can backup your system with an external hard drive, network-attached storage, and online services.

In this, the latest family-friendly recipe from the Food Network's Neely's, you will make garlic grilled lamb chops. These chops are irresistible and you will put them together from scratch. You won't have any leftovers after serving this great Southern style recipe. Enjoy!

What could be more perfect for a summertime barbecue than an All-American flag cake? This sponge cake is easy to make and covered in berries to give it a fresh, warm-weather flavor. If you need a dessert for Memorial Day or the Fourth of July, this is the perfect one for you. Start from scratch with the Food Network's Ina Garten, aka the famous Barefoot Contessa, in this clip.

The beauty of the iPod Touch is that it is not only for music. With the iTouch, you can access the Internet as well. You can use this Internet capability to download from iTunes, get e-mail, surf the web and many more options. In this tutorial, learn exactly how to turn your iPod on to a WiFi network so that you can take advantage of all the features your new device has to offer.

Ready to do some deep south cookin'? In this video, learn how to make fried mac & cheese with owner of Lady and Sons and Food Network's resident top southern chef, Paula Deen! ...And this isn't just any mac & cheese! This is mac & cheese wrapped in bacon and fried for a delicious crunchy finger food!

In this tutorial, learn how to make delicious French profiteroles for dessert with Ina Garten of the Food Network's Barefoot Contessa.

If you've already jailbroken your iPhone, but noticed that you are missing your cellular data network tab, check out this video. You will need Cydia, Winterboard, and be jailbroken on 3.0 of course.

Not 100% familiar with all the awesome features that make facebook a great storytelling medium? Check out this instructive how-to video from the cast.

Network sharing lets other iPhoto users view your photos and albums from their computers.

Wi-Fi networks come in two flavors: the more common 2.4 GHz used by most routers and IoT devices, and the 5 GHz one offered as an alternative by newer routers. While it can be frustrating to attack a device that moves out of reach to a 5 GHz Wi-Fi network, we can use an Alfa dual-band adapter to hack Wi-Fi devices on either type of network.

There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture handshakes from both attended and unattended Wi-Fi networks, we'll use two of Bettercap's modules to help us search for weak Wi-Fi passwords.

When joining a new network, computers use the Address Resolution Protocol to discover the MAC address of other devices on the same network. A hacker can take advantage of ARP messages to silently discover the MAC and IP address of network devices or actively scan the network with spoofed ARP requests.

You may not know it, but the IPv4 address of your computer contains tons of useful information about whatever Wi-Fi network you're on. By knowing what your IPv4 address and subnet mask are telling you, you can easily scan the whole network range, locate the router, and discover other devices on the same network.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.

While password cracking and WPS setup PIN attacks get a lot of attention, social engineering attacks are by far the fastest way of obtaining a Wi-Fi password. One of the most potent Wi-Fi social engineering attacks is Wifiphisher, a tool that blocks the internet until desperate users enter the Wi-Fi password to enable a fake router firmware update.

I spend a lot of time helping friends and family with their tech problems, like clearing a browser's cache, scanning a Windows computer for malware, and speeding up a Mac. However, the issue I deal with most frequently revolves around forgotten network passwords.

Leaving your Wi-Fi radio "on" allows your smartphone to auto-connect to trusted wireless networks in lieu of using cellular data, but it also consumes battery power while it's constantly network hunting.

An internet connection has become a basic necessity in our modern lives. Wireless hotspots (commonly known as Wi-Fi) can be found everywhere!

This video tutorial is in the Computers & Programming category which will show you how to hack a wireless network with WEP encryption. This video is intended only as a means of testing the security of your own network. Go to Backtrack Linux, download the backtrack4 and burn it to a DVD. Now put it in a computer with a wireless card and restart the computer so that it boots to the DVD. When it boots up, type "startx" to start the interface. Bring up the command prompt and type in "/etc/init.d/...

If you're not much for office computers, and like using your own powerful PC at your workstation, then chances are, you're going to have to login to the network. Microsoft shows you how to quickly login and join a Domain or Workgroup in an office network.