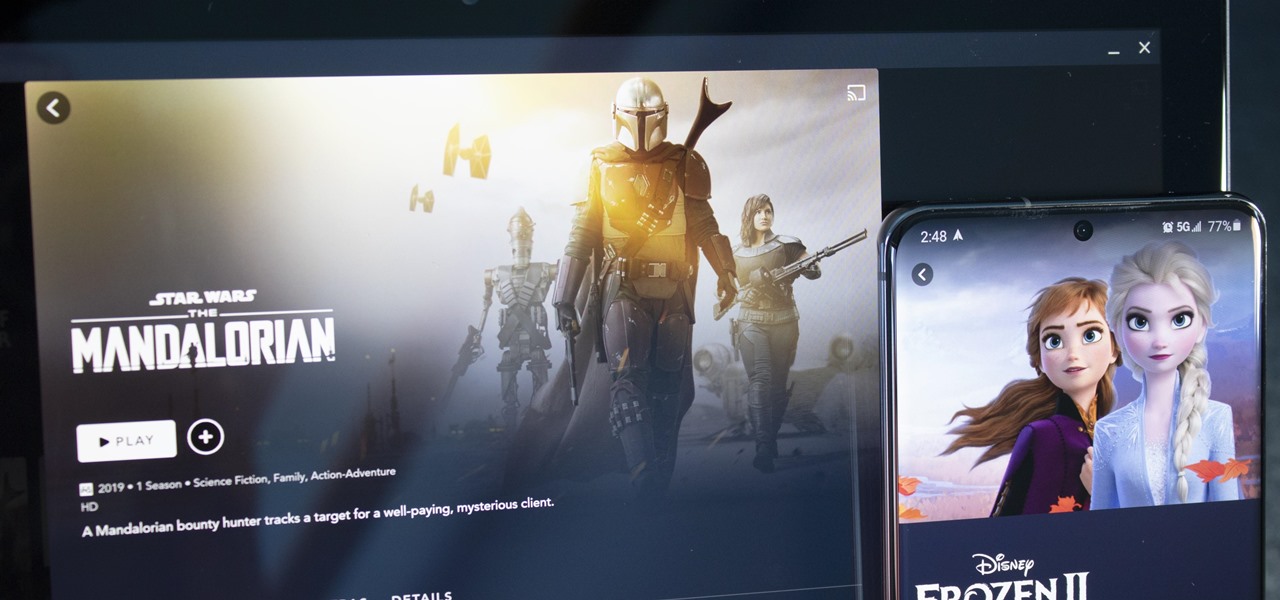
With shows like "The Mandalorian" and movies like "Frozen 2," Disney+ has quickly become a must-have streaming service. However, with Netflix, Amazon Prime Video, and Hulu, adding another subscription-based service can become expensive — but there are ways to trim down the cost.

After leveraging the well-known intellectual property of Rovio's Angry Birds for its first game for the Magic Leap One, Resolution Games is singing a new song with a familiar refrain for its next game for the augmented reality headset.

On Thursday, Magic Leap decided to step up its efforts to foster its developer community by launching the Independent Creator Program.

While last year's revelation that Apple slows down iPhones with aging batteries left a bad taste in users' mouths, the company's $29 battery replacement program was a step in the right direction. However, all good things must come to an end; Apple will soon shut down the program, leaving users to pay the full $79 to replace their faulty batteries.

After a long hiatus, we shall once again emerge from the shadowy depths of the internet to build an exploit. This time, we'll be looking at how to defeat a non-executable stack by using the ret2libc technique — a lean, mean, and brilliant way of exploiting a stack overflow vulnerability.

Ever since Google CEO Sundar Pichai took the helms of the world's most valuable brand, he has made it his mission to bring smartphones to lower-income communities. Born in India, Mr. Pichai has created several programs to address the needs of the Indian market, particularly the lower income families.

During our last adventure into the realm of format string exploitation, we learned how we can manipulate format specifiers to rewrite a program's memory with an arbitrary value. While that's all well and good, arbitrary values are boring. We want to gain full control over the values we write, and today we are going to learn how to do just that.

With all of the Pixel 2 excitement the past few weeks, many Samsung fans are feeling left out on that new software hotness. If you're anxiously awaiting the Android Oreo update on your Galaxy S8 or S8+, that wait may come to an end this week. Users over on Reddit decompiled the APK for the Samsung+ app to reveal multiple mentions of the upcoming Oreo Beta Program for the Galaxy S8 and S8+.

For a company who hasn't released a product and has a reputation for being secretive, Magic Leap sure has a tendency to make waves. Over the past few weeks, they've refreshed their website design, released an abstract YouTube video, and announced a partnership with Madefire to offer mixed reality comics on its device whenever it launches. Next, they are gearing up for another round of funding.

CyberTimez and the Wounded Warrior Program, using the Vuzix M300 monocular smartglasses, are teaming up to help supply veterans with little to no sight. The overarching goal here is helping these injured service members to find a new level of independence in a sight driven world.

The ride-sharing firm Lyft and Faraday Future, a troubled electric carmaker and potential Tesla competitor, have quietly appointed new top executives, but like the rest of the industry, they struggle to find talent for their driverless programs.

Hulu used to be simple — just a site with all the latest clips and episodes from your favorite shows. Watch some ads, watch some free TV. Easy, right? Not so much anymore. Hulu is no longer free, and on top of that, offers different pricing plans and add-ons.

The common thread between this week's Brief Reality stories is that augmented reality is beginning to prove its worth as a technology that improves workflows and processes. From customer service to healthcare to manufacturing, augmented reality is helping companies improve productivity.

Engineer Anthony Levandowski has officially been kicked off Uber's driverless program by a judge as the company's legal war with Waymo continues.

One thing you don't see often in the driverless industry are partnerships. When automakers are in the news together, it usually means drama. However, an important partnership between Nissan and Mobileye was announced today. One that has the potential to make driverless cars on the road better and safer.

It's March once again, and while that might signify the beginning of spring for some, basketball fans have this month marked on their calendars for one good reason: NCAA March Madness. Though the tournament is already underway, the Sweet Sixteen leg begins Thursday, March 23, 2017. If you fear you may miss the upcoming games, worry not, as free apps for smartphones and tablets are available to help you watch all the action.

If the recent "state sponsored" Yahoo hack wasn't enough motivation for users to stop using their services, the latest news about Yahoo should be. Joseph Menn, a reporter at Reuters, just revealed that Yahoo created a custom email wiretap service for the US government.

The Null Byte community is all about learning white hat hacking skills. In part, this is because I believe that hacking skills will become the most valuable and important skill set of the 21st century.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

Hello there, reader! If you've clicked on this How-to then it means you are interested in learning some C programming or just generally curious about what this page has to offer. And so I welcome you warmly to the first of many C tutorials!

Programming is an essential thing in hacking/pentesting, and at times, I do not feel that it is being addressed enough here, at Null-byte. I understand that this is a forum dedicated for hacking, but I'll address some of the stuff I feel is muy importante about programming. I am not a professional programmer, but I do have experience and I do want to share some of the stuff professionals have taught me.

Hi everyone! In the previous part of this series, I introduced one way to hijack a program's execution flaw, though I only showed you how to crash the program and left you with a little mystery to solve. Today we are giving the solution of that and then introducing shellcode usage and remote command execution.

Hi everyone! Last time we finished analyzing the assembly representation of our vulnerable piece of code (have I ever told you it is vulnerable?). This time we are going to introduce some fundaments about exploitation by demonstrating how to crash a program's execution. If that sounds lame, next time we will see how this crash can in fact be useful to control the program's execution, achieving remote code execution!

Apple announced the successor to Mac OS X Mavericks at their Worldwide Developer's Conference 2014, and it's called Yosemite. Named after California's Yosemite National Park, it will be available as a free upgrade from the Mac App Store for everyone this fall.

I rarely ever turn my desktop off. For starters, it takes a few minutes to boot up, which I hate, and secondly, putting the computer to sleep is perfectly adequate. You really only need to completely shut down your computer every once in a while.

As a former English major, I have a love/hate relationship with many books. And when I saw that this NFC-enabled charging dock project included a little book mutilation, I was suddenly more interested. Now, for those of you who have nothing against books, this is still a great project to add some style to your tech devices.

Having access to your computer from your cell phone is an extremely useful feature. Whether you need to edit documents or send files that are on your home desktop, or you simply want to watch movies you have saved on your computer, access is key.

The convenience of storing things on the cloud can definitely make life easier, but if you're storing sensitive files, it could be a total disaster if anyone hacked your account. Some encryption services can be expensive, but if you just need it for personal use, there are some really great ones that don't cost anything. Here are three programs that let you encrypt your cloud storage for free. BoxCryptor

Spotify is a free, ad-supported program that allows you to listen to music online for free. The music is everything from indie labels to the top 100 charts. This guide will help you learn how to listen to music using a Spotify account.

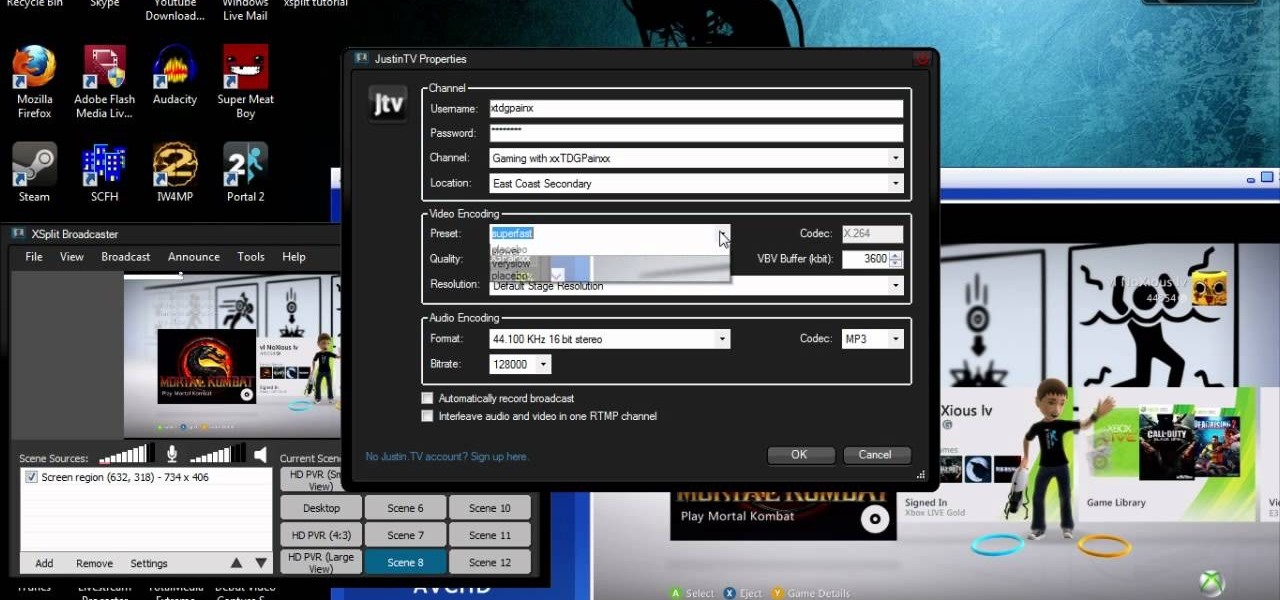
If you want to stream your Xbox 360 and PS3 games online so that others can watch you play console games on Twitch.TV or Own3d.TV, this guide will help. You'll need to own a Hauppauge HD PVR and have access to XSplit Broadcaster, a program that streams video sources from your computer to popular streaming websites.

If you're thinking about getting a piercing, but aren't sure how it will make you look, you can use a program like Photoshop or GIMP to edit in a fake piercing. Start with a photo of yourself, with the area you are considering piercing shown prominently. Then find a picture of someone with the same kind of piercing that you want, and then use some of the editing tools and tricks in photoshops to see how it will look on you!

You will need to create some time lapse footage first. Then, you can use the Magic Bullet software to edit in a fake tilt shift look for your time lapse film. This technique will work on most other video editing programs as well.

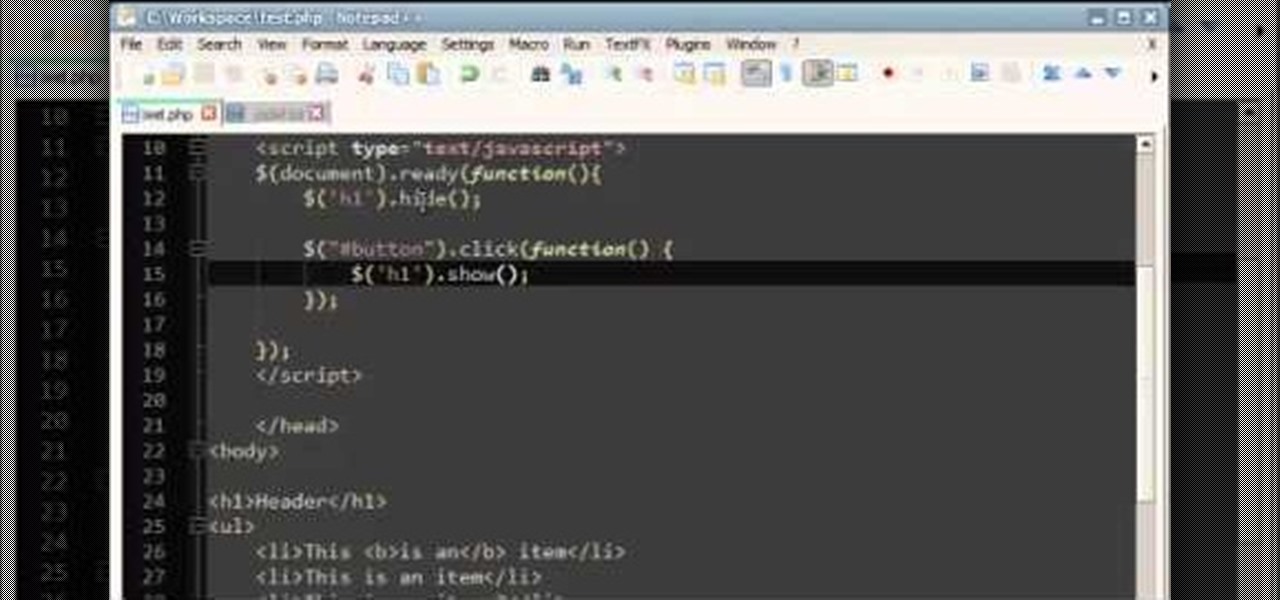
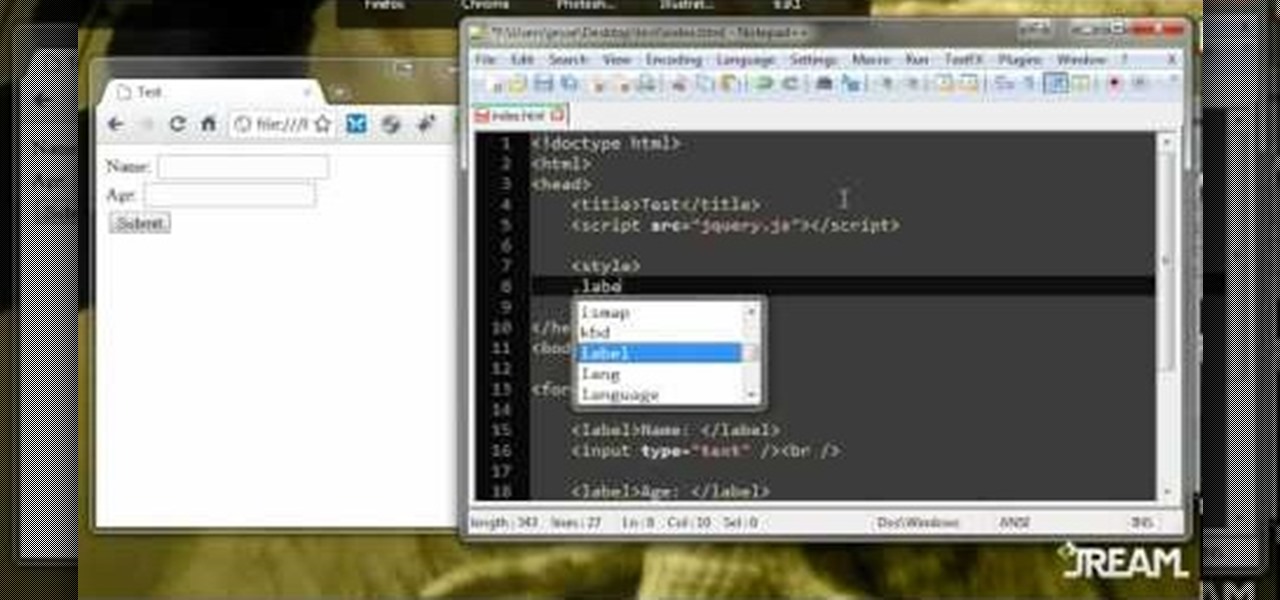
This tutorial gives you a quick rundown on some of the various effects you can play around with in JQuery, such as buttons or alerts. This is a good video for anyone looking to round out their knowledge of JQuery progrmaming.

This form will look like it's been written with AJAX, but the dirty little secret is that it's actually a JQuery script. The reason for doing it this way is greater efficiency in your program, and a little easier to work with.

Wait, a query within a query? This function is possible within the framework of MySQL. Learn how to correctly implement a subquery or sub select in your next database project and avoid a couple perils that will make your program unstable.

If you're concerned that your computer has been infected by spyware and other malicious programs, watch this informational video and find out how to clean and restore your computer back to a normal bill of health. This informative tutorial shows various methods that can be used to disinfect your computer and rid it of those nasty viruses once and for all!

Want to create your own time lapse video, but you don't have the right equipment? You can use Adobe After Effects to fill in the gaps. This is a quick and easy tutorial showing you how to use this program to create your own time lapse video.

Looking for some good study programs? iFlash, an application available for Mac users, allows you to create flash cards, which you can sort by semester, year or subject. Then, export your cards to your iPhone or iPod Touch to study on the go!

Looking for freeware alternatives to Photoshop? If you don't need all the bells and whistles of a huge program like Photoshop, this video shows you where to get free photo editing software with good developer support, like Paint.net, FotoFlexer or the GIMP.

Keynote is a Mac-based software program designed around presentation. While you can use it to make videos, you can also create a Keynote project which is just narrating a slideshow, or present a series of ideas to get your point across.