
How To: Prepare your toddler for a doctor visit
Going to the doctor can be an unsettling event for any child. This program is about preparing your toddler for a visit to the doctor.


Going to the doctor can be an unsettling event for any child. This program is about preparing your toddler for a visit to the doctor.

Learning different coding languages can be difficult. You spend so much time mastering one and getting used to thinking along the channels you need for it that learning something new can sometimes be more difficult than starting from scratch. Starting from scratch, notably, is also difficult.

MATLAB, an acronym for "matrix laboratory," was created over 40 years ago to service the applied mathematics community. The powerful programming language now has over four million users worldwide and is of particular import to engineers, scientists, and economists.

Java is one of the world's leading programming languages thanks to its virtually endless array of applications. Since Java's initial release in 1998, this Open Source platform has become beloved by coders for its speed, flexibility, and dependability.
If you're a frequent Null Byte reader, chances are you're already up to speed with at least one or two programming languages or development platforms. But in a world that's becoming increasingly reliant on high-powered apps and responsive websites, knowing the fundamentals of just a few go-to programming languages isn't going to cut it if you want to be competitive and successful.

It's finally here. After years of rumors and speculation, Apple unveiled the new iPhone SE on April 15. While it doesn't have a 4-inch display like the original SE, it's the smallest new iPhone you can buy today, with the chipset of the iPhone 11, 11 Pro, and 11 Pro Max. So, when can you get your hands on it?

While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of built-in graphical X forwarding for SSH.

While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are all network services, which means we'll write our first remote exploits.

Apple officially unveiled the long-awaited iPhone X, its tenth-anniversary edition iPhone, on September 12. With preorder and release dates just around the corner, you'll want to brush up on all things iPhone X to make sure you get your hands on one as soon as possible. After all, preorders start Friday, October 27.

Gaining access to a system is always exciting, but where do you go from there? Root or bust. Sure, a compromised host is a great way to run a botnet, or do some other boring, nefarious thing—but as hackers, we want root. We also want to take the easiest path possible, search out low-hanging fruit, and exploit them. SUID programs are the lowest of the low-hanging fruit.

Hello fellow gray hat hackers, I wrote a program in python that helps me to fill up my proxychains.conf file, so I don't have to manually enter in the proxies. I figured I will give a little how-to of how I did it and maybe I could help some of you(hackers) out there to stay anonymous.

Greetings my fellow aspiring hackers,

Hello, fellow grey hat hackers and aspiring coders. I'm back again with another python tutorial. Just that this one is gonna be a lot cooler ;-). We gonna make an encryption program, that well you know encrypts all the files on your pendrive or hdd or whatever you want....Also lots of thanks to DrapsTV. They have helped me a lot with Python and making awesome programs. The video is here:

This is a short explanation and tutorial on how to grab saved passwords from Google Chrome, ideally from a meterpreter session. The idea behind this is to understand how saved passwords work and how to keep them safe. Let's have some fun :D Understanding Google Chrome Saved Passwords

Hi nullbytes! I've been recently reading the whole Linux Basics for the Aspiring Hacker series and felt like it was missing some stuff I know, so I felt like sharing it with anyone who might find it useful too.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Welcome to the sequel to the latest post on writing 64 bit shellcode! This tutorial will assume that you are aware of everything mentioned in the last one, as I will try to make this tutorial void of formalities and straight to the point! If you have not read the last one, I suggest doing so unless you are familiar with basic assembly programming and system calls. This is by no means rocket science, so therefore I will simply repeat my TL;DR from last time before we get started, so that the a...

Welcome back, my fledgling hackers! In an earlier tutorial, I introduced you to probably the most popular scripting language for hackers, Python. To become a professional hacker, you need to have some scripting skills and Python is a good choice if you want to master just one. In this latest guide, I will expand your background in Python and offer you a tidbit of Python code to whet your appetite for all of the hacking to come.

Welcome back, my amateur hackers! Over the course of the next year, we will be developing our own zero-day exploits. In my first article in this series, I introduced you to buffer overflows, which are the source of some of the most lethal exploits, particularly the "remote code execution," so we are focusing our exploit development here on a buffer overflow.

Welcome back, my fledgling hackers! With this first article, I am initiating a new series intended to convey to my readers the skills necessary to develop your own exploits.

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.
This video shows top 10 useful tricks in windows 7. This video includes window key application, inserting program or folders in start menu or task bar, enabling or disabling windows7 features, notification area customization, reliability history etc. These tips will help you to operate windows 7 more efficiently. So please watch the video.
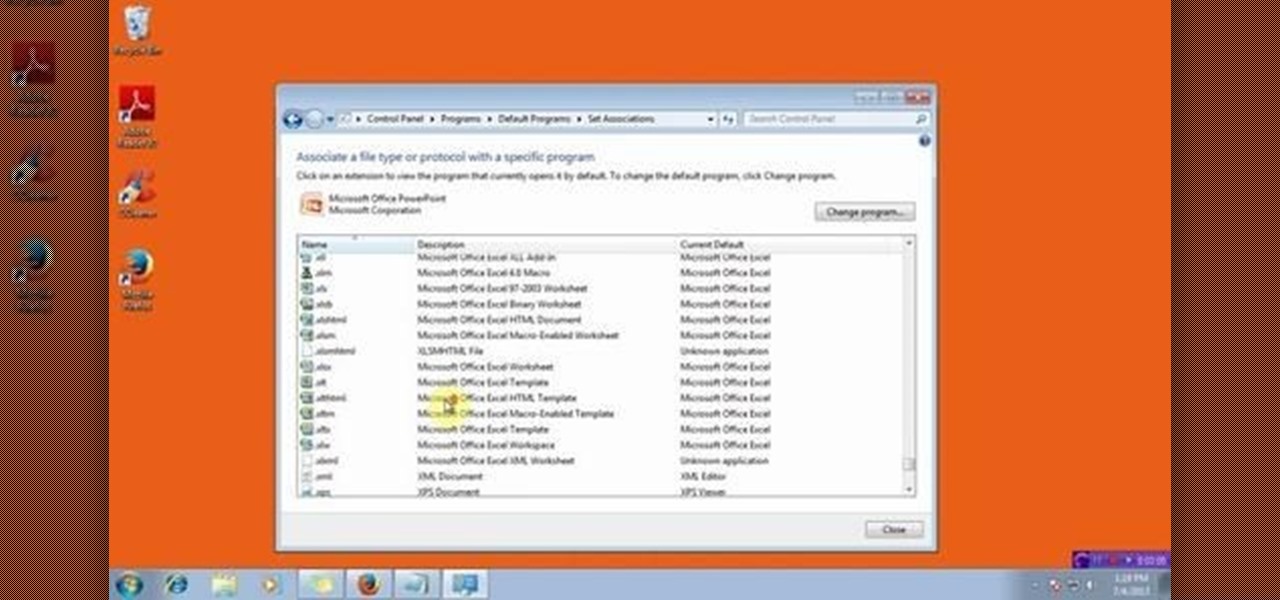
This video will show you how to change the default program for a Specific File Extension in Windows 7.

In this how to video, I discuss three different exercises that have really helped me to tone my waistline. Although you cannot specifically target different fat deposits while dieting, it is still important to perform these exercises to give your core and waist that aesthetic look. These exercises have given me great results, but a solid diet and a good training program is also extremely important to sculpting your body. Enjoy!
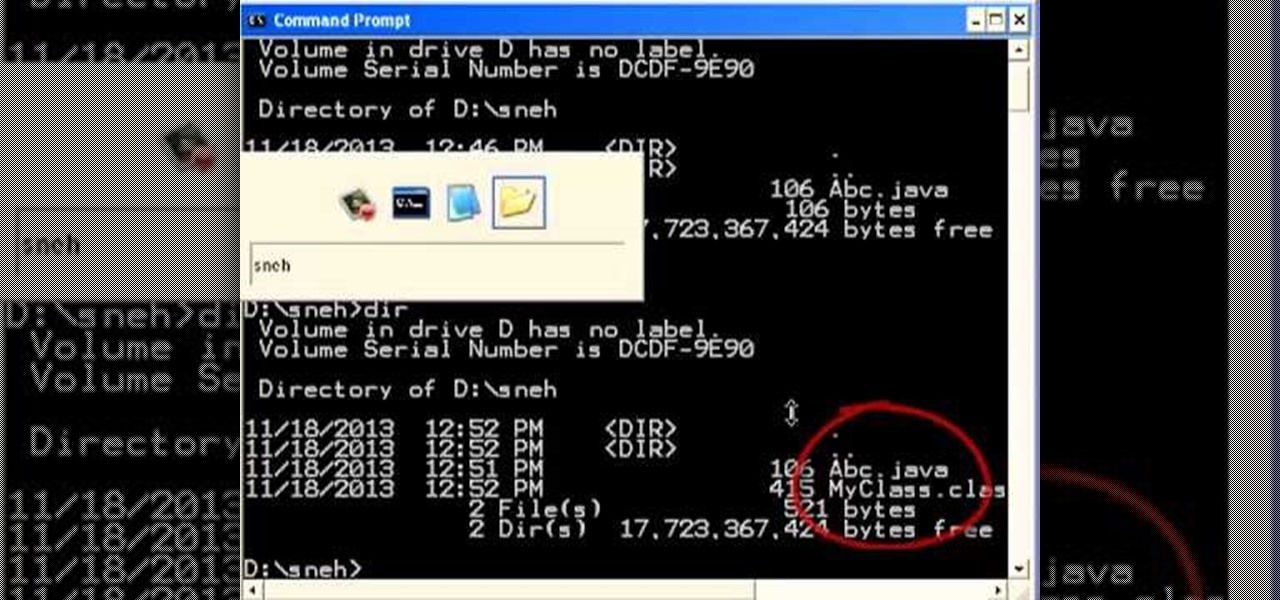
we will learn here, how to write a class, what makes the class to be executable, how to compile the class, what the thing should be kept before executing our java class.
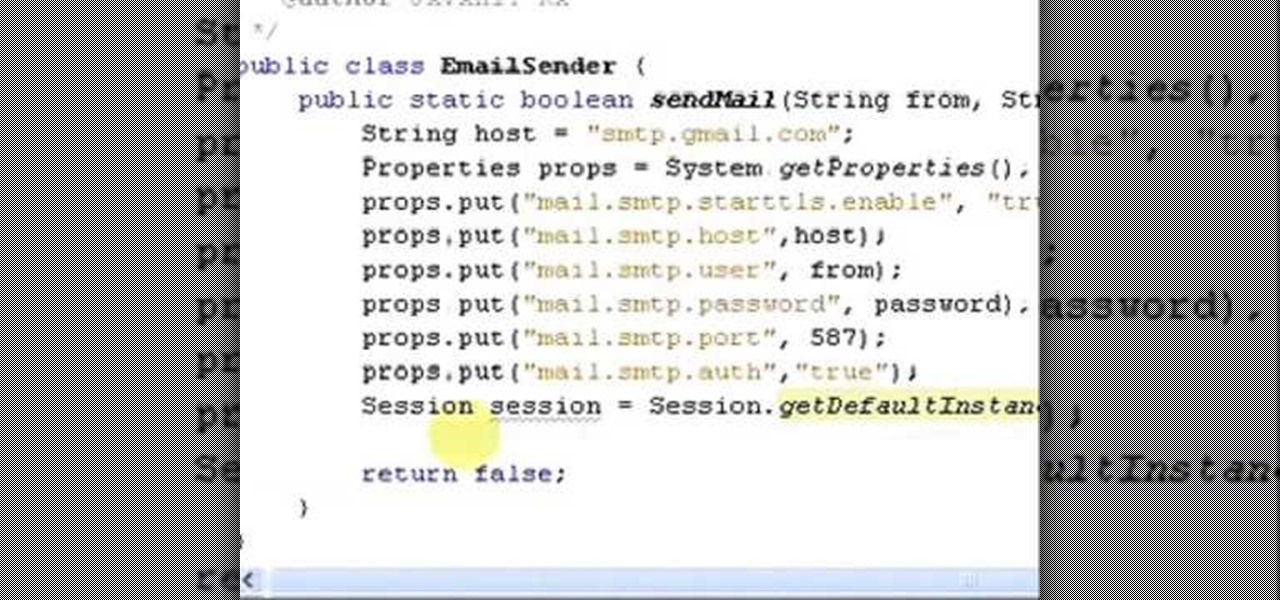
It uses JavaMail API, NetBeans IDE 7.0.1 First download the JavaMail API as shown in beginning of the video then follow the video to send email dynamically from your Gmail account. No need to open your inbox.

Apple is widely known for keeping a tight grip on iOS, disallowing open-source and third-party downloads. While there are many reasons for this, the three most frequently referenced are quality control, malware prevention, and of course—money.

In this web design tutorial we will show you how to protect yourself from losing your work just in case the program malfunctions, computer crashes or you accidentally forget to save document and so on. I highly recommend you utilize this Web Design Tutorial especially if you are working on large websites for clients.
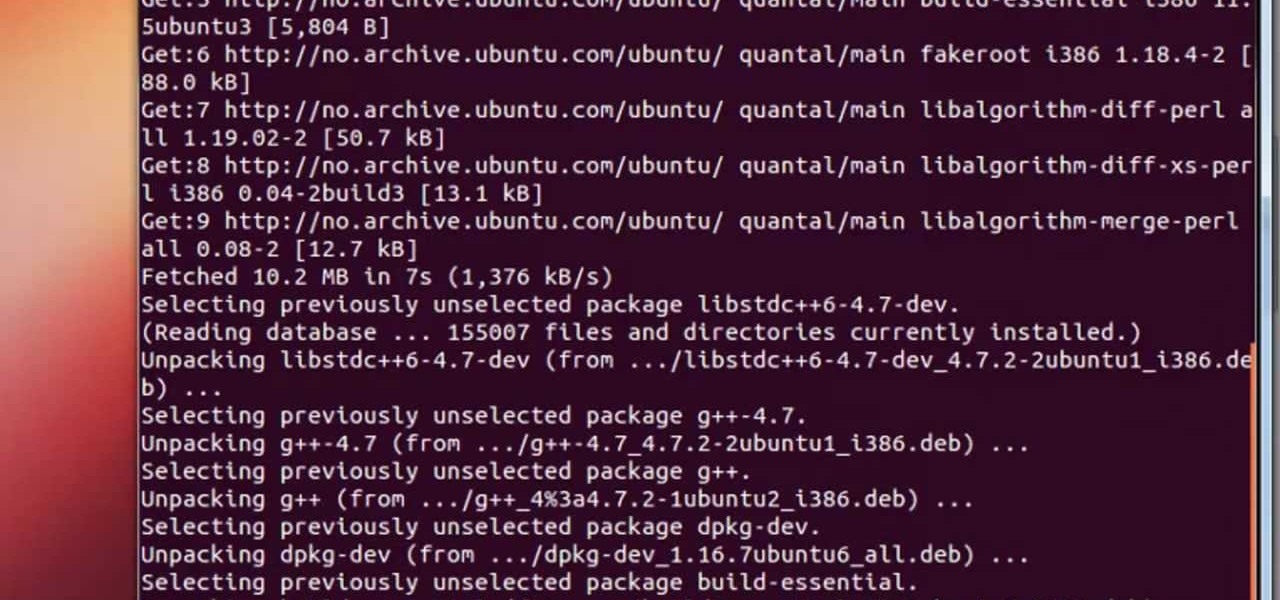
I see that there are a lot of people that want to install and try the Aircrack-ng program for wireless auditing. But have problems because their Linux knowledge isn't that great. This How-To video tutorial explains step by step exactly what you have to do. No loud background music.

Like a computer, your brain can store and process large amounts of information. It can remember names, solve math problems, and save tips that you might need at a later time.
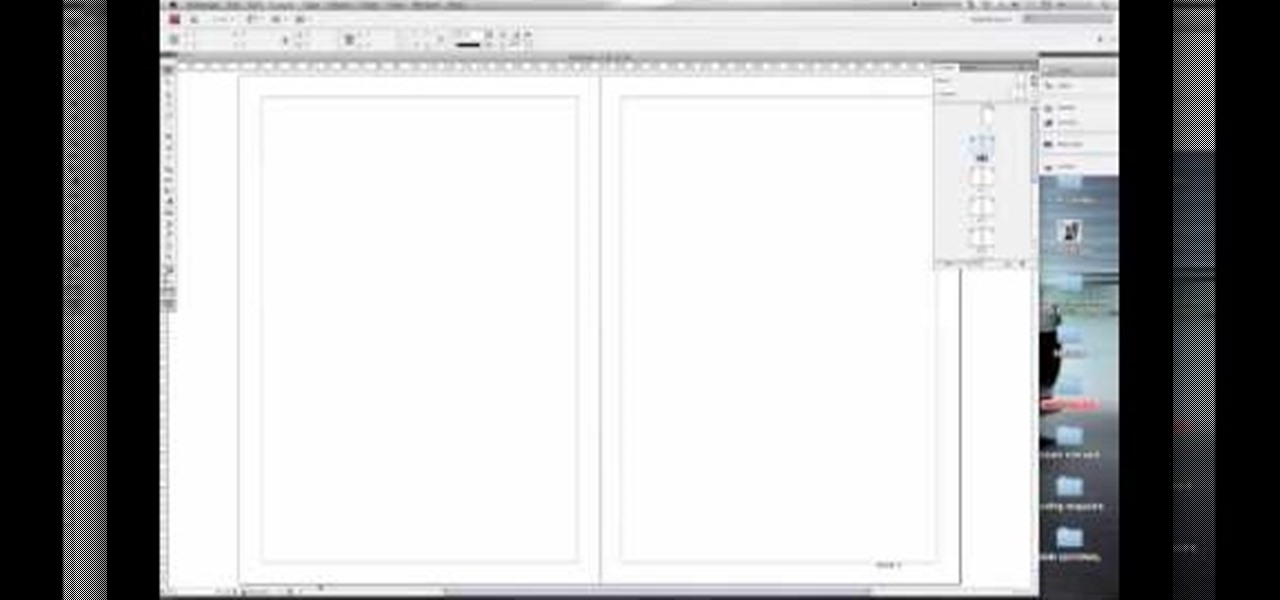
If you're creating a document and with Adobe's InDesign and would like to learn how to number your pages, look no further. This video will show you what to do to make sure you get the numbers you want, where you want them. Though this seems like a simple task, it can prove frustrating to someone unfamiliar with the program. This how-to clears up some of the mystery and lets you get your 1,2,3 on. Adobe InDesign can be an impressive document or presentation tool and this tip will help you get ...
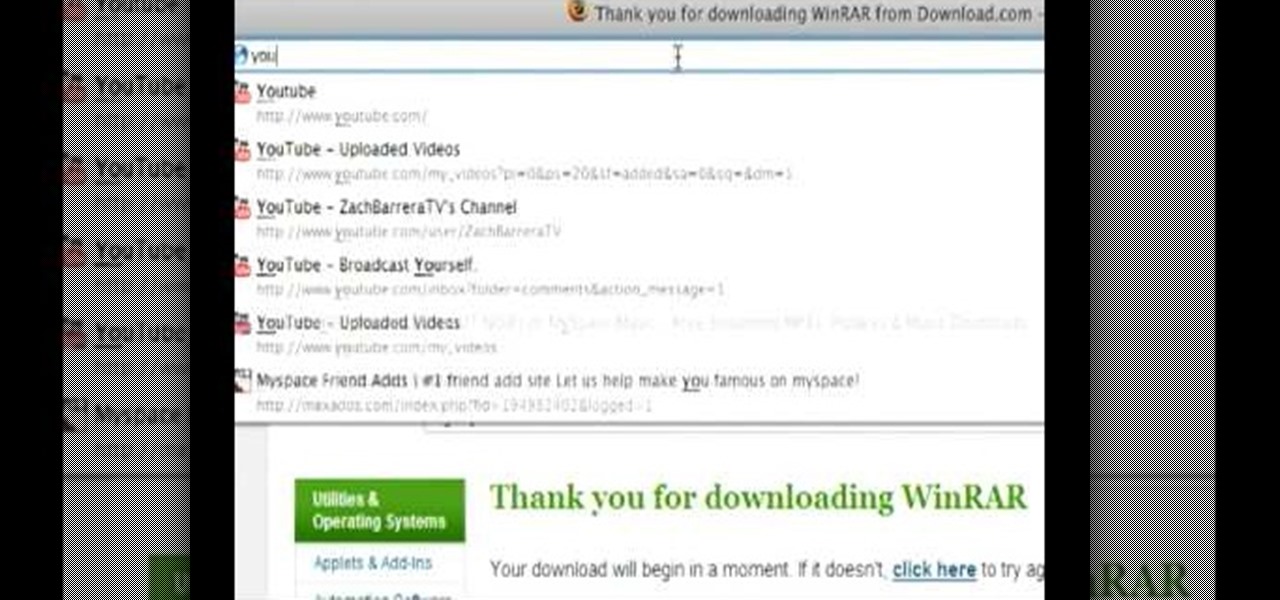
When the amount of memory on your computer sucks, you either have two options: Buy more RAM, or make use of the storage space you've got by compressing your files. One program that will become your new BFF should you choose to do the latter is WinRAR. WinRAR is a compression and packaging software that makes it way easier to store large files on your computer.
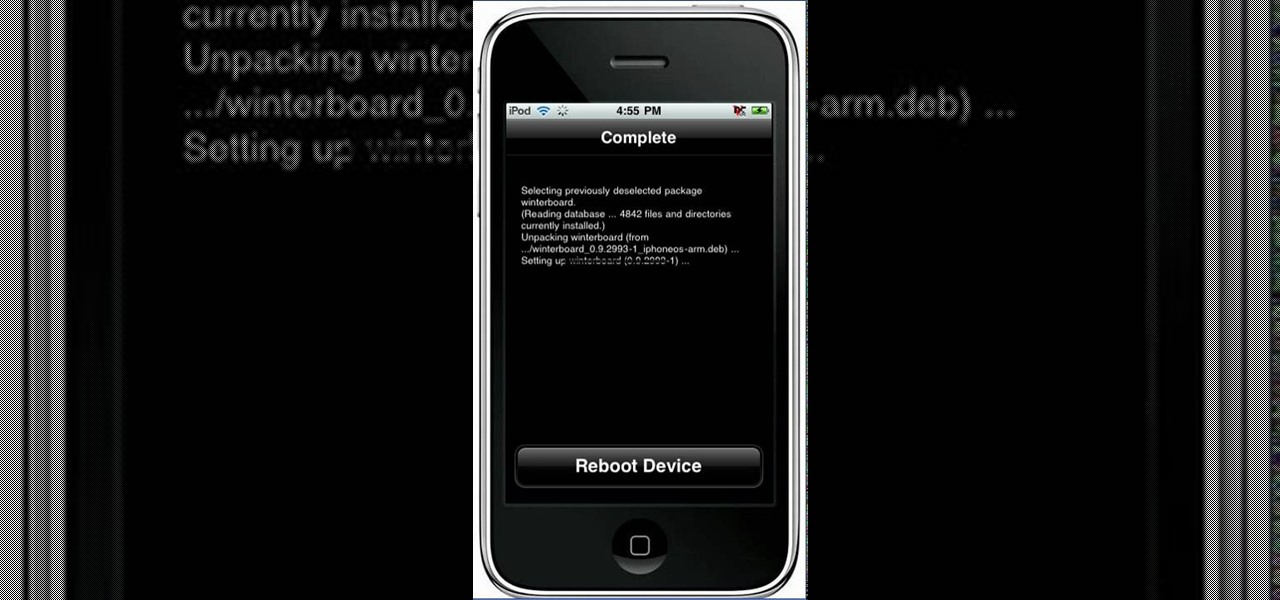
Winterboard sounds like some special type of snowboarding you can only do with a special snowboard, but in actuality Winterboard is a special application on your iPod and iPhone that lets you create pretty background themes, movie backgrounds, and lockscreen changes.
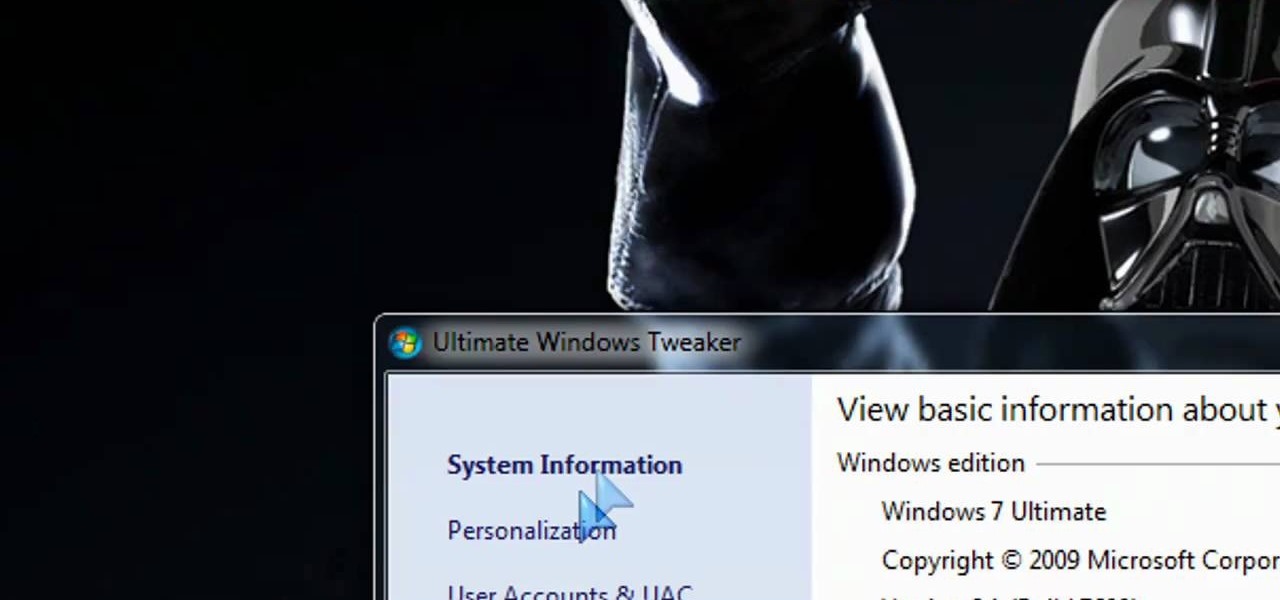
If you're not satisfied with your out-of-the-box version of Windows 7 or Vista then get ready to tweak it up good! With this video, you'll see how to use a little program called Ultimate Windows Tweaker to wrestle your software to perform the way YOU want it to. This software lets you get into the registry in a safe and easy way if you're not a computer wizard. Remember to always back up your system before toying with the registry.
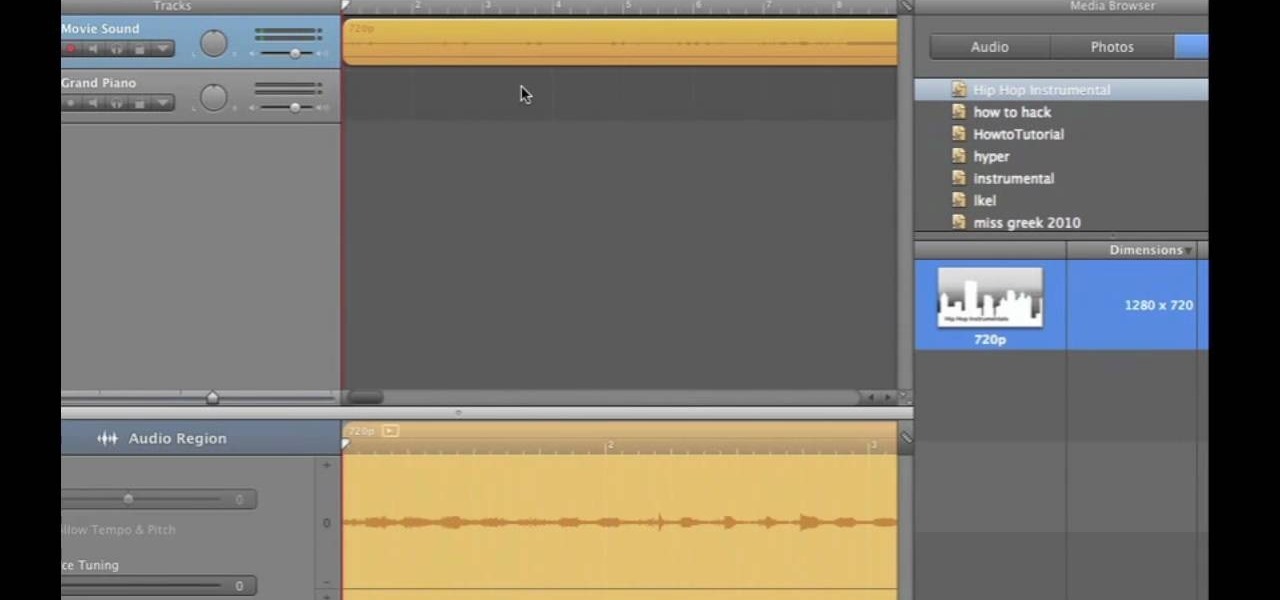
If you want to work on some audio attached to a video, then it's possible with two iLife programs on your Mac— iMovie and GarageBand. This video will show you how to strip that audio track from the video, converting it to MP3. You can strip the audio from files such as .MPG, .MOV, .AVI, .MP4, AVCHD, MPEG-2 and H.264.
This is a video tutorial in the Computers & Programming category where you are going to learn how to kill boredom with weird and random websites. This video lists 11 such websites and explains what each one does. The 1st one is Zigzagphilosophy. This site allows you to make a lot of zig zag lines on the screen by moving your mouse. #2 omglasergunspewpewpew. On this site you use the mouse to control a squirrel on the screen and use the left click to shoot a laser. The #3 site is allemande and ...

Modern bombshell Scarlett Johannson literally worked her butt off to get into shape for the role of Black Widow in "Iron Man 2." While always lean, Johannson whittled down her famous curves, losing about ten pounds (a major difference for a woman that small) and gaining a lot of lean muscle.

It can be really hard and intimidating to start a fitness program, especially if you've never worked out on a consistent basis before. But if your goal is to lose anywhere from 30 to 50 pounds then you really can't get away with not exercising.
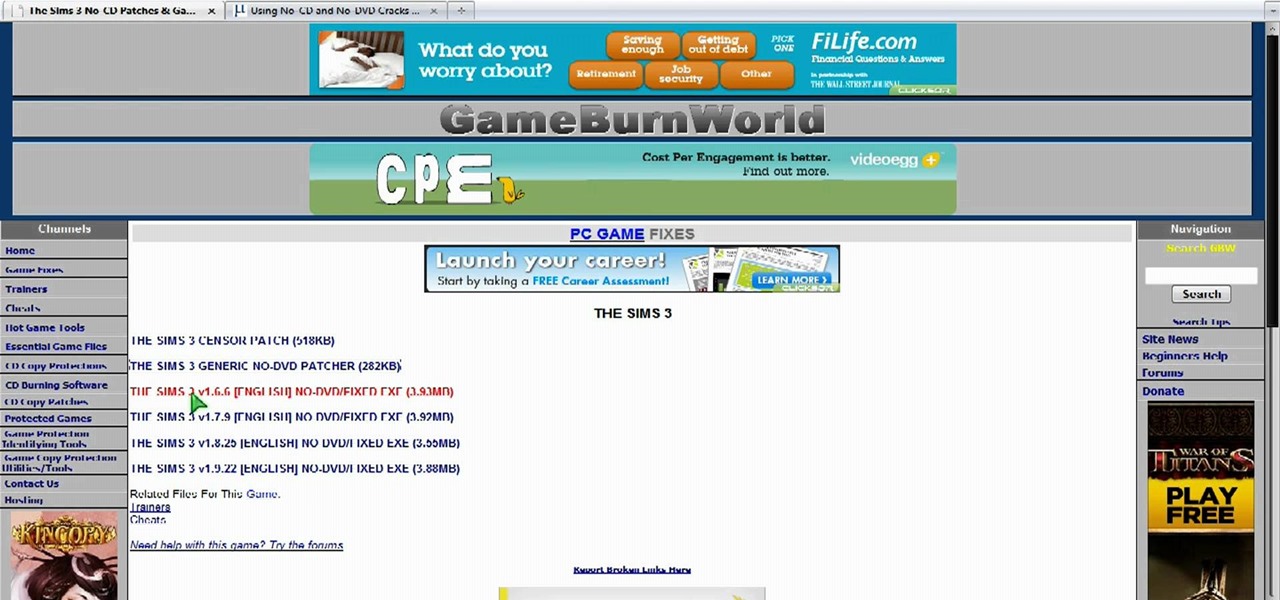
In this video, we learn how to use cracks to play a DVD or CD without the disk. First, go to Gameburnworld and download/install the patch to play your game. Then, open it up and go to the program files folder to find the files for the game. Drag this and drop it in, then you will not have to use the DVD for your movie or CD. Remember to only use this if you own the game or movie, not if you have downloaded it illegally. You can do this for all your discs, it's easy and just takes a few minutes!