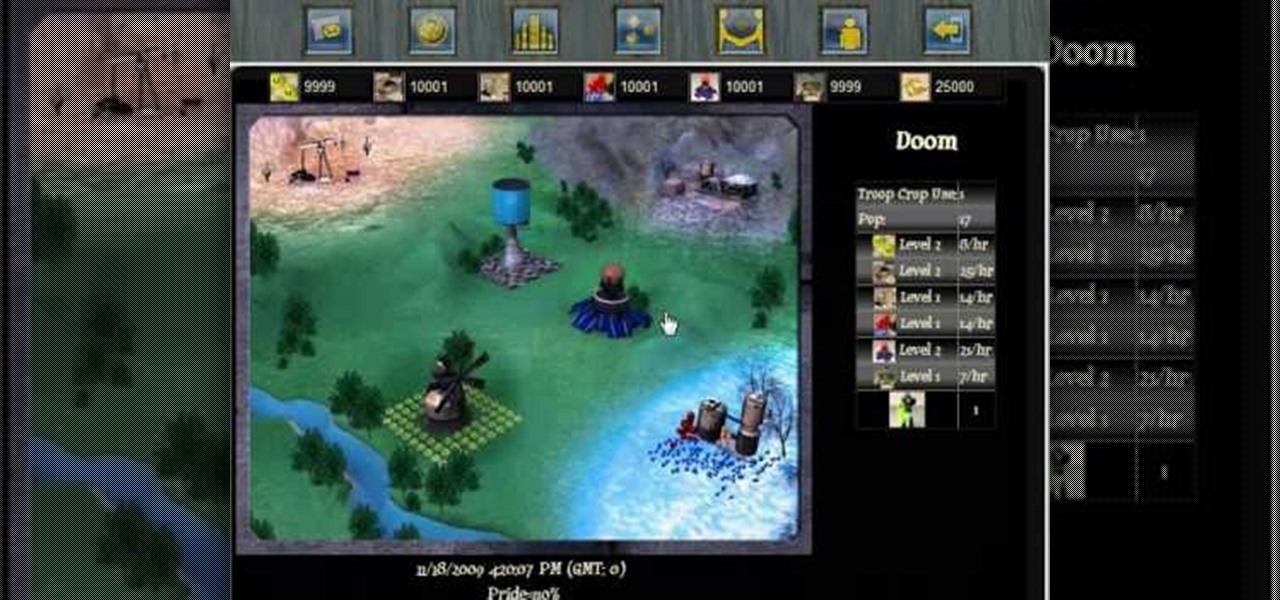
How To: Create spies and intelligence agencies on Conrohl
In order to spy and gain intelligence on your Conrohl enemies, you need to make an intelligence agency. Then you recruit your spies to perform simple espionage.


In order to spy and gain intelligence on your Conrohl enemies, you need to make an intelligence agency. Then you recruit your spies to perform simple espionage.

Art+Commerce Art Mix

Chicago cops, the FBI, Homeland Security, Secret Service and a large number of unnamed others have established a high-tech secret command center to surveil people exercising their First Amendment right in Chicago as the NATO war council unfolds this weekend.

In this video, we learn how to get credit when you don't have any. Most credit agencies are now gathering information about younger people to figure out if they are allowed to get credit cards, which will help them build a credit score. There is a website, PRBC, where you can start a file and enter your information, and it can verify all the information you report. This information will be given to credit reporting agencies, and give you more of a chance to get credit. Next, you can get depar...

Using a memorandum of understanding, or MoU or letter of intent, is an important business tool that can help deals or projects in the business world. Many companies and government agencies are known for using MoUs to help with relationships with departments, agencies, and other close partners. Although it's not really thought of as a binding contract, they can have that power with the right words being used.

A memorandum of understanding, or letter of intent, is used as a document that shows an understanding between parties. Although it can be used as a sort of contract, it needs to meet certain standards and wording. This MoU, as it's also referred to, is used amongst businesses and governments agencies. So if you need to figure out how to use a memorandum of understanding, this tutorial will tell you more about it. Good luck, pay attention, and enjoy!

Breaking a lease is almost always considered a legal breach of contract, even if a tenant has a good excuse. Here are some exceptions to the rule

| Update: ZTE's issues with the US government have finally been resolved. Check out the details below.

If you have seen the movie Fast and Furious 7, you know what "God's Eye" is. Well this might spark interest to you.

Since the San Bernardino shooting in 2014, Apple's been engaged in a game of cat and mouse with law enforcement. Authorities want access to evidence on criminals' iPhones, but Apple wants to protect all of its customers' personal data equally. The latest installment in this saga has Apple outright disabling the Lightning port.

Zika is a threat to unborn babies — the virus can cause neurological damage if it infects a mother during pregnancy. But as with many things, our solutions to the problem aren't always all that much better than the problem itself.

Huawei has been in a losing battle with the US government for around ten years, with the last year being the spike of Huawei's problems. Because of US pushback against some Chinese-based smartphone manufacturers due to security concerns, Huawei is hoping to limit its dependency on US-based companies, and recent rumors of Huawei's very own mobile operating system may be the first step.

Mobile augmented reality developer Blippar has escalated the augmented reality advertising arms race, introducing a new rich media ad format that enables augmented reality experiences without a dedicated app.

The Null Byte community is all about learning white hat hacking skills. In part, this is because I believe that hacking skills will become the most valuable and important skill set of the 21st century.

Let's just say it's been a pretty bad year for spies and government agencies and an even worse one for the privacy of U.S. citizens. Edward Snowden blew the lid off the NSA's spy program, and the FBI was recently discovered to have the ability to access your webcam any time they want—without triggering the "camera on" light. Yeah, that means those Justin Bieber lip sync videos you recorded weren't just for your private collection.

In a world increasingly regulated by computers, bugs are like real-life cheat codes. They give you the power to break the rules and do good or bad without ever leaving your seat. And government agencies around the world are discovering and stockpiling unreported bugs as cyberweapons to use against anybody they see fit.

We're living in uncertain times. The sudden outbreak of the novel coronavirus and subsequent self-isolation of roughly half the world's population has led to a massive reorganization of the economy, countless layoffs, compromised security networks, and a variety of other significant disruptions that will forever alter the landscape of our daily lives.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

Amber, emergency, and public safety alerts on an iPhone are loud — startle-you-to-death loud even. They can happen at any time, day or night, and sometimes back to back when you're in a big city. Those blaring sirens can wake you from sleep, interrupt an important meeting, or disrupt an entire movie theater mid-movie, but you can turn most of them off if you're tired of hearing them.

With Huawei's recent emergence as the second largest OEM in the world, the company was poised to finally make a big push into the US market. Instead, their efforts were derailed by an unlikely foe, the US government. As a result, American customers will miss out on the newly-released Huawei P20.

Responding to the rapid emergence of dangerous pathogens around the world, a new initiative to prevent or contain pandemics was announced in Davos, Switzerland, yesterday. If you ever worried that a highly contagious pathogen could take down your community, or the country, this news is for you.

Last month, it was revealed that Juniper Networks' routers/firewalls were hacked. It was reported that a backdoor was implanted in the operating system of their routers/firewalls and that attackers could listen in on all encrypted communication. There are now fears that all confidential communications by U.S. government agencies and officials could have been compromised over the last three years.
How Do You Do A Business Plan? Part 1 of 5 (Series designed to discuss the parts of a business plan, what information is involved in each part, and why a business plan is needed.)

When Kaci Hickox, a Doctors Without Borders nurse, returned to New Jersey from working with Ebola patients in West Africa in 2014, she was surprised by her reception. Instead of a quiet return to her home in Maine after four weeks on the front line of Ebola treatment, she was quarantined by the State of New Jersey in Newark. She later filed a lawsuit in U.S. District Court for violation of her civil rights, false imprisonment, and invasion of privacy.

In the recent hit movie Furious 7, the storyline revolves around the acquisition of a hacking system known as "God's Eye" that is capable of finding and tracking anyone in real time. Both the U.S. spy agencies and an adversarial spy agency (it's not clear who the adversary is, but the location is "beyond the Caucasus mountains," which could imply Russia?) desperately want their hands on this system.

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.
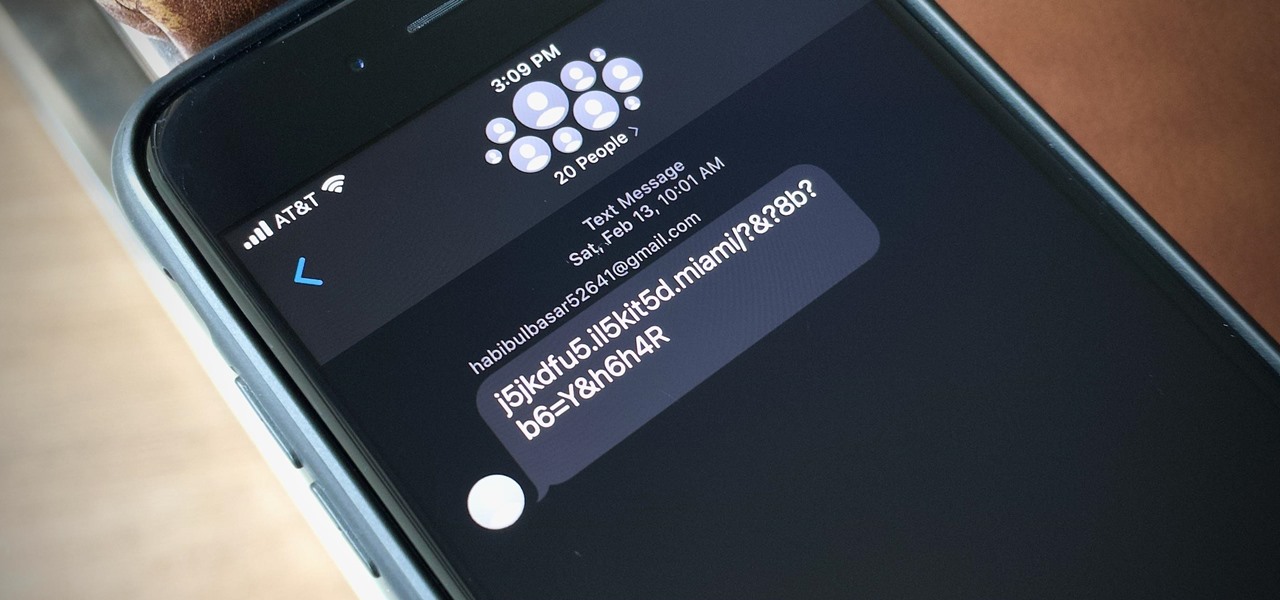
Next to spam calls, few things are more annoying than being inundated with spam, scam, and smishing texts. Your iPhone's Messages app should be a place for your friends and family to stay in touch, not a minefield of phishing attacks, malicious links, and viruses. Luckily, there are quite a few methods to block and report your way to a more spam-free iPhone.
One of the most prestigious annual events for the advertising industry, the Cannes Lions is the ideal backdrop for Snapchat to show the brands and agencies in attendance what it's got.

With all the talk about returning to the moon via SpaceX, NASA, and international agencies, some have forgotten some of the magic surrounding the original Apollo 11 mission.
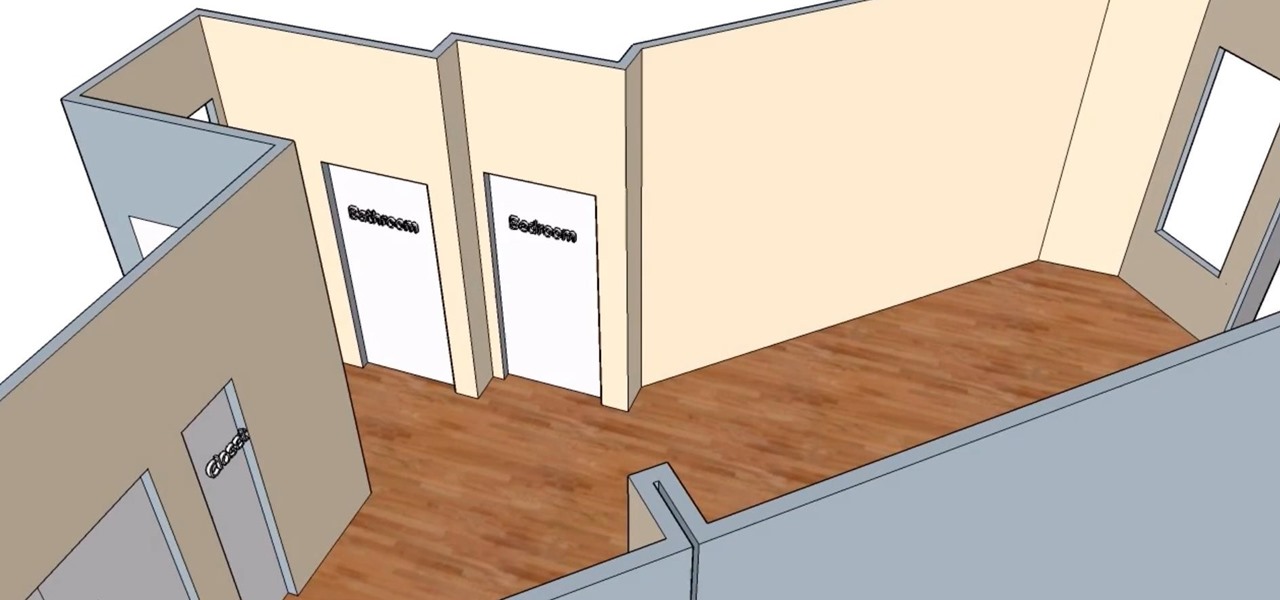
Measuring a room has never been so easy thanks to Apple's ARKit. SmartPicture 3D is known for its quick measurements based on pictures from your smartphone. Recently, they released a video of the company measuring a room using the ARKit.

Open-source data scraping is an essential reconnaissance tool for government agencies and hackers alike, with big data turning our digital fingerprints into giant neon signs. The problem is no longer whether the right data exists, it's filtering it down to the exact answer you want. TheHarvester is a Python email scraper which does just that by searching open-source data for target email addresses.

Considering that nearly half a million brand new apps were published to the Google Play Store in 2015, you can definitely call it a banner year for Android development. In fact, it's getting to the point where we're a bit spoiled as end users, since we've grown to expect something new and exciting practically every week.
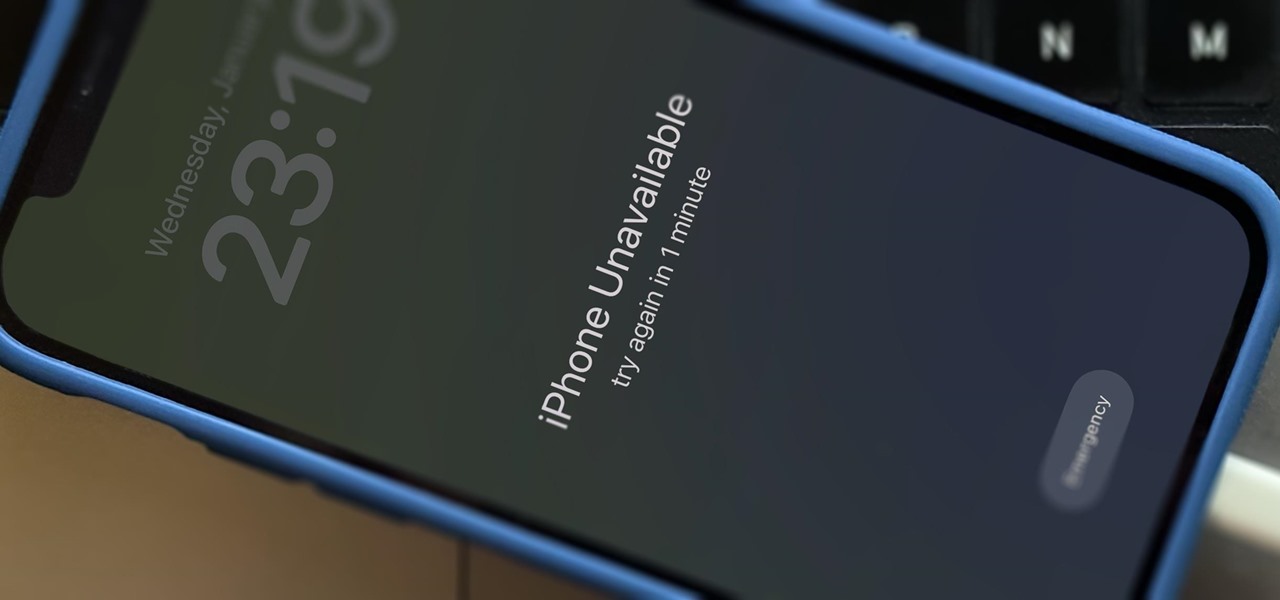
There's only one thing keeping hackers, thieves, law enforcement agencies, and maybe even the people you thought you could trust from breaking into your iPhone should they ever get possession of the device. Their odds of bypassing that thing are pretty good, but there's an easy way to make it an almost impossible feat.

UPDATE: Entries are now closed. Thank you for participating! Next Reality is where we help you literally 'see' into the future of augmented reality, and to help with that mission we're offering three free pairs of Snap Spectacles 3 to three lucky readers who sign up for the Next Reality daily AR email newsletter.

Following on the heels of the announcement that ThirdEye's Gen X2 MR glasses began shipping in September, ThirdEye has revealed it has developed an app that helps soldiers aim their weapons during battle situations.

After getting its start with models of augmented reality planets that serve as targets for augmented reality experiences, AstroReality is diversifying its portfolio by paying tribute to one of the space agencies that made its products possible.

Over the past year, two trends have emerged among augmented reality development software: make it easier to create AR content, and give AR apps better environmental understanding with just a smartphone camera.

Mobile app publishers are using augmented reality to solve everyday measurement problems from measuring the length or height of items to previewing furniture in the home.

Microsoft's latest move to further secure its hold on the emerging mixed reality space comes in the form of two new Mixed Reality Capture Studios in San Francisco (the flagship studio) and London.

As augmented reality gains popularity, the demand for delivering related services and generating content increases. This is demonstrated by a pair of investments from the past week, one in the expansion of a technology lab and another in the form of seed funding for a content studio.