How To: Speed Up Your Wireless Internet Connection
In terms of internet, faster = better. We all want faster internet, but how exactly do you get a fast wireless connection? Believe it or not, the answer is quite simple.


In terms of internet, faster = better. We all want faster internet, but how exactly do you get a fast wireless connection? Believe it or not, the answer is quite simple.

Call Your State's Nurse Aide Registries for School Inquiries
FV Extender for Chrome This is an extension you can download for your the Chrome browser. At this time the extension only accepts and sends back gifts but may do more in the future. See developer's site for more information, and a quick video showing this feature in action.

I recommend you take a look into this issue and suggest that your friends delete their association with Gamers Unite and any other cheat providing site. This post is meant only as my advice for how to remove Gamers Unite or any other spammy app. This is all based on my personal feelings about the snag bar and websites that would hand out such cheats. I've provided this as INFORMATION ONLY. Please decide on your own what you think of the whole situation.

Can you guess which household liquids sink and which ones float? Play along with the A-TV science team in this video lesson!

Get ready to learn a cool trick where a ribbon is cut in half and then magically fused back together! You will need some ribbon, an envelope, and some scissors. Sometimes we use materials that require adult supervision... like scissors, so make sure you have friends and family around whenever you do magic tricks. 1. Preparation: Cut the ends off of both sides of the envelope.

(In case you can't read my writing, here is the description in a little more detail)

Ever written anything with an permanent marker on your magnetic blackboard? This is how to remove it. Remove permanent marker.

How to make a $2 bill man. No narration but very good written instructions. Cute trick to do for friends and family. Origami a $2 bill man.

Outside the realm of politics, where opposing sides are quite passionate and quite disagreeable, there are few areas in our society quite as divisive as Twitter. People who like Twitter love Twitter and are relentless in trying to co-opt the people they know into joining (this is both altruistic and an unsubtle attempt to boost followers).

What is a Data Structure?

Hello! Today, I will show you how to add captions to your YouTube videos. Captions help people understand when the video itself does not entirely explain your tutorial.

I have an absolutely wonderful time making projects and writing articles for all of you mad scientists! Today, I will bring you behind the scenes for a look at the workbench, tools, and software that make the Mad Science World possible.

Microcontrollers are great. You can do anything from water your garden to catch wildlife trash diggers in the act—and on the cheap. I prefer to use the Arduino microcontroller because of the large and helpful community built around the website. Though it is my favorite, there are some drawbacks to using an Arduino board in every project. It gets expensive, the board can take up too much space, and the rat's nest of breadboard wires are a pain to repair.
Ink & Paint was originally intended to provide a place for the sharing of graffiti and street art related news and the spreading of the street art culture. However in recent months I have noticed a distinct lack of "lowbrow" art in the WHT community. Don't get me wrong though, I'm a HUGE nerd. I love null byte, I love the Minecraft world, and all the tech posts that are becoming increasingly more common. It's awesome. However the nerd in me and the artist in me both want to see more comics, s...

Oh Data, You so Awesome! We are going to use Node.JS to gather us some data. Given nodes plethora of well abstracted network abilities and it's deep evened nature, it will make quick work of plugging into various data sources and gathering / making good use of said data.

In my opinion, Isaac Newton is definitely the number two astronomer, right below Galileo Galilei. His discoveries were very important to uncovering the secrets of space, and he deserves to be remembered.

US can legally kill Americans in terror groups You read it right. The US can now target Americans who are supposedly part of terrorist groups. Here's my analysis of Attorney General Eric Holder points (keep in mind though, these are point's brought up by MSNBC, original article here):

How to Read a Poem Poems can be read many ways. The following steps describe one approach. Of course not all poems require close study and all should be read first for pleasure.

This article is going to talk about video and only about video. Why? Because video is very important for any size of business. Even small businesses can use video to promote themselves on the internet. And in the next few years, you’re going to see more and more businesses using video. Even now, I’m going to show you some articles that have been written on different websites talking about video and how small businesses can use them and how businesses need to use them now, especially to rank o...

I write this post as an afterthought on the recent mass burnings of the Quran by U.S troops. Let me lay down the facts first to clear any misunderstandings:

It seems the Republicans aren't happy about Obama. But then again, they never will be. As the time for re-election draws near, the Republican Party is scrambling to chose their candidate who will beat Obama. So far, Mitt Romney (we'll discuss the candidates soon) has somewhat dominated the scene, with spurts of awesomeness from Rick Santorum and Newt Gingrich. Ron Paul stays steady, currently holding the second most number of delegates (yes, we'll go over terms also).

As many of you Null Byters may know, I was planning on writing this article a week or two ago. Better late than never! So, let's get right to it then—choosing the right Linux distro for your needs.

Do you need to email your wife your Social Security number? Send confidential business plans to your partner in Thailand? Send your hacker buddies the recovered hashes from last night's breach? Try using GPG, a valuable and easy to use open-source encryption program.

Law enforcement can make a lot of folks cringe. Too often do we hear on the news, and even experience in our own lives, the unjust way that an unacceptable portion of law enforcement treat the very citizens they are supposed to protect. People's rights are violate each and every day by law enforcement, simply because they are timid and uneducated with the laws of society. This dirty trickery shouldn't be played on harmless citizens under any circumstances.

Here's another delicious Byte. Ucha Gobejishvili, a Georgian Security Researcher under the handle of longrifle0x, discovered two cross site scripting (XSS) vulnerabilities on the official website of Forbes. He discovered the hole in two different locations on the site, and has already informed the website of the vulnerability.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server.

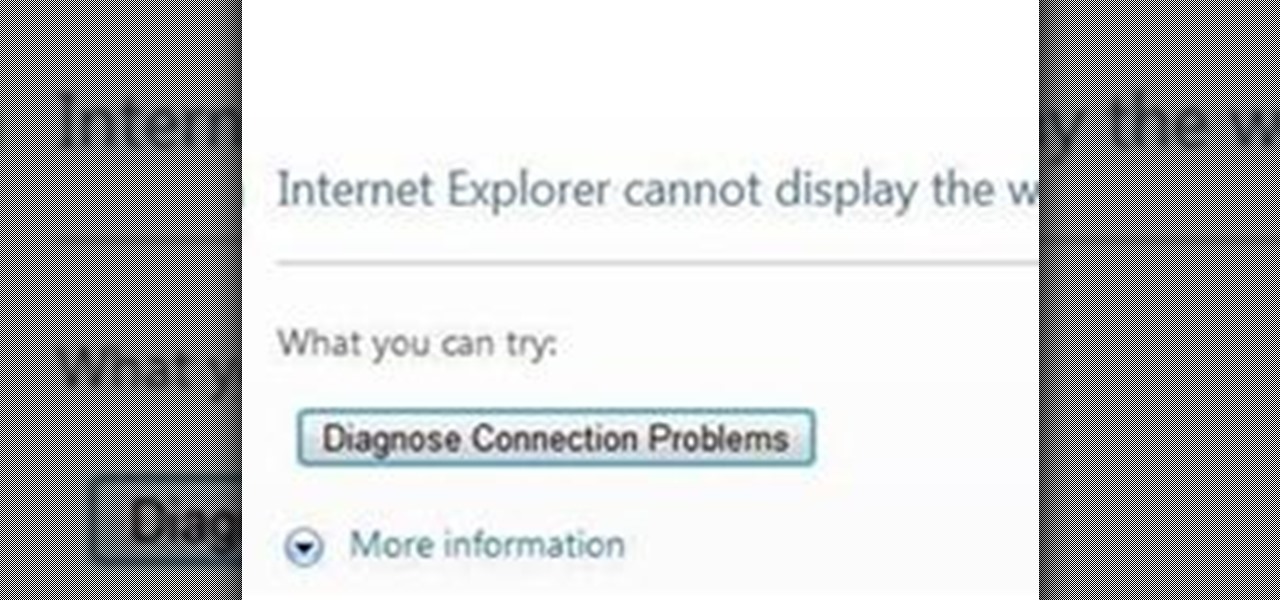
About Today's topic Today we will talk about diagnosing and fixing connection problems. Let's face it - the truth is everyone who uses a computer and has an internet connection will have to deal with this at some point. Connection problems often occur at the wrong time and it is a real pain.

Keyloggers are a must-have tool in your arsenal. Hardware keyloggers have the advantage of being undetectable through anti-virus or other protection programs. They also capture keystrokes before the OS even boots up, so they are pretty handy tools.

Reverse shells are useful for issuing commands to a remote client when the client is behind something such as a NAT. You might say, "But can't a normal shell or simple SSH tunnel do the same thing?". No, it can't. All over the internet I see a lot of confusion regarding the difference between a normal shell and a reverse shell. Let's clear this up before we get started.

This week's AON may be a little short, but the ones to come will be packed full with information. I am really hoping for the skies to clear so I can observe soon!

Last Friday's mission was to accomplish solving HackThisSite, basic mission 8. This meant that we had to learn some more basic Unix commands.

It's sad to say, but I will no longer be writing up anymore Scrabble Challenges. Frankly, I just don't have the time to make them now. And though they are incredibly fun and "challenging" to conjure up, I'm not sure that people are finding them as useful as I had hoped. But really, it all comes down to time. So, unless I have a future craving for puzzle-making, last week's Scrabble Challenge #20 was the last one.

Null Byte is looking for moderators. More threats to computers exist every day. Not only do we have computer viruses and malware, but we have rootkits and other nasty pieces of code that can log your keyboard strokes or even add your computer to a botnet to attack other websites. Your computer can be infected even if you have anti-virus software installed. I can't stress enough how easy it is for a hacker to write a piece of code that gets around every piece of anti-virus software.

I can't believe it, but I've actually read about dozens of people getting their iTouch, iPhone, or iPad stuck in a bricked recovery loop and then going out to buy a new one. This is overly unnecessary. When it gets stuck in the recovery loop, some people mistake themselves by thinking that it is impossible to get the device back into DFU (Device Firmware Upgrade) mode. Getting the device back into DFU mode would at least allow us to jailbreak the device, essentially bringing it back from its ...

What's your highest scoring game of Scrabble? Since starting this Scrabble World, I've been able to break 500 points on a regular basis. This year I've even managed to break the 600-point barrier a couple times. If you ask me, that's a pretty hefty sum to score in one game, but I'm not on par with the professionals yet.

Cheers to another completed Community Byte project! Things went well regarding timeliness and being friendly to the other coders and students. If you've got ideas for our next mission, or an idea for a tutorial, submit them to me. Friday, our mission was to take out HackThisSite, basic mission 5. This mission focused on JavaScript, again. This time there is a little bit more security in place.

What happens when a struggling writer cannot finish the screenplay to her second film? She writes a book.

Welcome to the Goodnight Byte for HackThisSite, Basic Mission 4. In Friday's session, we tackled some coding in Gobby. Nothing special, just a few modifications to the NullBot script we made a few session ago, and some education on regular expressions. Apart from coding, we did our scheduled HackThisSite mission. We had to take on some JavaScript, which was a new thing for Null Byte. This mission taught us about client-side HTML manipulation through JavaScript injections. This just means that...

Google+ is the greatest social network to emerge since Facebook annoyed everyone into joining, but that doesn't necessarily mean that our relationship with it is all rosy. Although Google+ has amazing innovations, like hangouts and circles, users are spending a lot of time begging for core features that take what seems to be an eternity to emerge.