
How To: Get your FBI file
Thanks to the Freedom of Information and Privacy acts, we’re all entitled to see what the FBI has on us. Learn how to get your hands on your FBI file.


Thanks to the Freedom of Information and Privacy acts, we’re all entitled to see what the FBI has on us. Learn how to get your hands on your FBI file.

Bowling is such a fun group activity and is perfect for birthdays and other types of gatherings. However, if you are not a pro bowler the scoring system can be pretty confusing. This tutorial will walk you through the steps of keeping score so you will know a strike from a spare and everything in between.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

With No Time to Die, the 25th installment in the James Bond saga, arriving in April and Black Widow, the first solo film for the Marvel Cinematic Universe's own secret agent, following a month later, what better way to get in the espionage mood than some augmented reality spy gaming?

The USB Rubber Ducky is a famous attack tool that looks like a USB flash drive but acts like a keyboard when plugged into any unlocked device. The Ducky Script language used to control it is simple and powerful, and it works with Arduino and can run on boards like the ultra-cheap Digispark board.

An incredible amount of devices use Bluetooth or Bluetooth Low Energy to communicate. These devices rarely have their radios switched off, and in some cases, are deliberately used as trackers for lost items. While Bluetooth devices support MAC address randomization, many manufacturers do not use it, allowing us to use tools like Bettercap to scan for and track Bluetooth devices.

The addition of a new research mode for Microsoft HoloLens will enable researchers and developers to tap into a wider range of data collected by the device's sensors.

In many ways, the Galaxy S9 is a holdout from the golden days of Android. It's one of the last major flagships to sport a headphone jack, it has an impressive array of internal sensors, and perhaps more importantly, it's got a micro SD card slot.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.
Thanks to live-streaming video and social media apps like Facebook, Instagram, and Snapchat, we're all on camera nowadays. Unfortunately, though, we don't have a script to work with when we're shooting selfie videos, so it's hard to come off as perfectly eloquent when you're just freestyling off the top of your head.

Many recipes call for self-rising flour as a staple ingredient. Oftentimes, we find ourselves passing these recipes by because we don't have it on hand, or because we don't use it enough to actually want to buy it.
Pretty much every note you save on your computer, phone, or tablet can be uploaded to your cloud and viewed on any of your devices. But what about those notes you write down on actual paper? Well, those notes can also be cloud-friendly, thanks to the Rocketbook Wave.

Sup? Today, we'll be learning about for loops in Java: What they are, how they work, and how to create them.
Hello there Nullbytes, In my previous tutorial found here,

Hello readers, in this tutorial, we will be discussing how to perform file operations such as reading and writing.

If you're lucky enough to have a dishwasher, you probably use that sucker to clean everything (minus your good cooking knives), and maybe even to cook your food, too. However, dishwashers are not without their faults. Dishes can still come out spotty and even with chunks of food on them, which usually leads to some hand-washing afterward.

In this article, we will explore the basics of radare2, a powerful package that comes with Kali. We are going to write a simple program, and then disassemble it, to see what is really doing in the processor.
Hello dear friends! I'm jgilhutton and I want to show you guys a Python wrapper I made a few months ago.

In this simple tutorial you will be shown step-by-step how to write local shellcode for use on 64-Bit Linux systems. Shellcode is simple code, usually written in assembly that is used as payload in exploits such as buffer overflow attacks. Payloads are the arrow head of an exploit: though the rest of the arrow is important for the delivery of the attack, the arrow head deals the killing blow. In reality, payloads are slightly less exciting yet far more interesting and intelligent than medieva...

Yellow buses are beginning to trickle into traffic. Retailers are pushing pens, pencils, and notebooks. Grumbling Facebook statuses run rampant through your feed. Surely you recognize the signs—school is starting. For some, it already has.

Yesterday, the Free Software Foundation published an article written by Paul Kocialkowski. A software developer for the the Android fork system Replicant, Paul stated that his organization discovered, and later patched, a "backdoor" vulnerability that existed in older Samsung Galaxy devices, including our beloved Galaxy S3s. Only problem is, it's kind of bullshit—but we'll get to that later.

I can be pretty forgetful. If there's something important to remember, I need to jot it down right away or risk losing it forever.
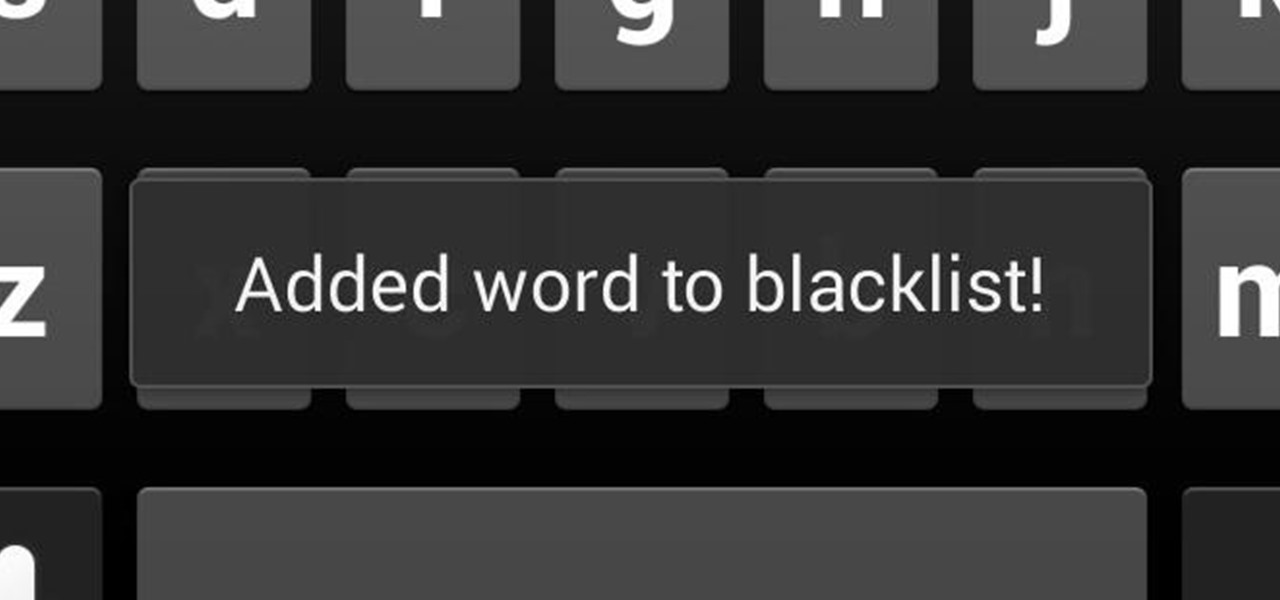
In the midst of furious finger typing on a small non-tactile screen, you're sure to make mistakes—so the majority of keyboards have autocorrect. Generally it works pretty well and is a welcomed feature.
Anyone who is familiar with Linux knows that to use your OS to the max, you will need to use the terminal every now and then. Whether it is to install a package or update the system or even delete a file.

Welcome back, my greenhorn hackers! Several of you have you have emailed me asking whether it's possible to install a keylogger on a victim’s computer using Metasploit. The answer is a resounding "YES"!

The vast majority of people involved in Steampunk are interested in history but, like with science, there's something about history that we don't talk about very often: The holes.

Facebook is an awesome free online resource that is connected to billions of people around the world. These days, you won't meet many people who do not have a Facebook account. As a real estate agent, you can take advantage of social networking to promote your business and share your listings. By posting on Facebook and creating a page for your business, you gain free advertising to thousands of local buyers. Check out this tutorial and learn how to start uploading videos to Facebook to promo...

Watch this science video tutorial from Nurd Rage on how to get lithium metal from an Energizer battery. They show you how to get Lithium Metal from an Energizer Ultimate Lithium battery.
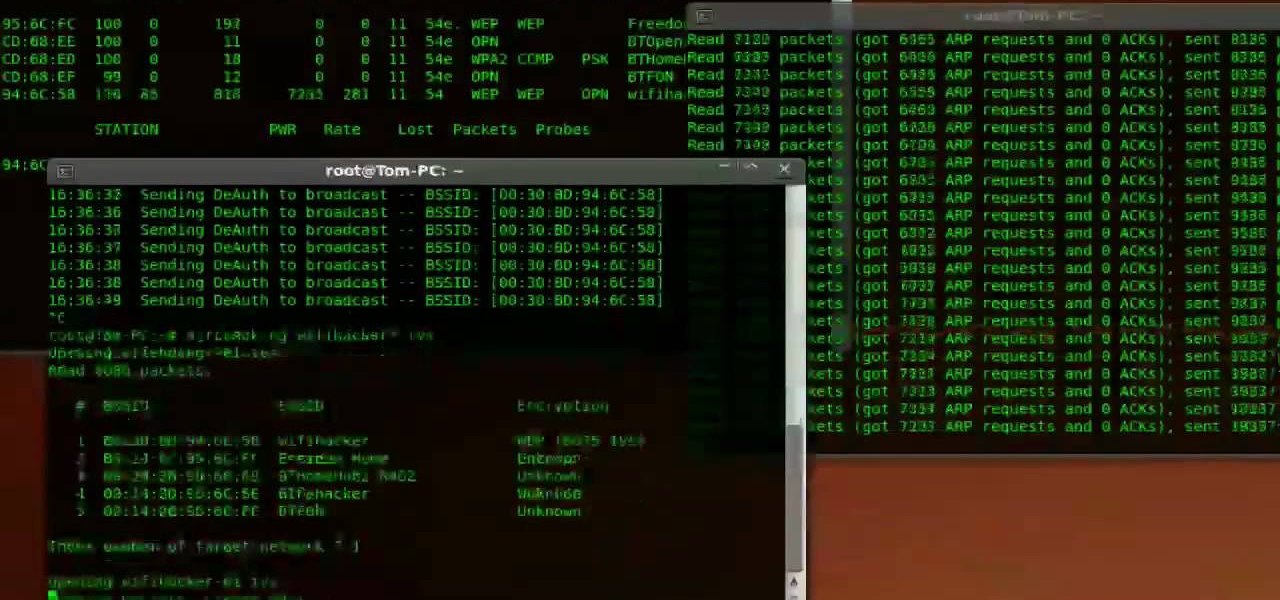
Oh how we love open source software. If it wasn't for Open Office, we never would have been able to write that seven-page English paper while on our friend's Microsoft Office-lacking laptop during an impromptu road trip to Mexico. And Ubuntu, an open source secure operating system, offers you similar convenience. A much more intuitive computer operating software than your standard Windows or Mac OS, Ubuntu is great if you know what you're doing.

WPA-secured wireless networks, or WiFI Protected Access, is a form of internet security that secures your wireless LAN from being accessed by unauthorized users. Safer than WEP, or wireless equivalent privacy, WPA still has weaknesses that are prone to cracking - IF, that is, you know what you're doing.

Have "Copacabana" written all over your face by creating this dramatic and oh so tropical makeup look. While most tropical makeup looks focus on super bright pops of color in neon green, yellow, and orange, this look veers more on the "evening out" tropical zone.

Comedian and actor Adam Sandler may be famous for his irreverant Jewish holiday hymn "The Chanukah Song," but he's also written several other holiday tunes that are of festive interest.

Want to play U2's "Still Haven't Found What I'm Looking For" on your ukulele? Learn how with this free video ukulele lesson from Ukulele Mike. Whether you play the ukulele or bass kazoo, there is no better way to improve your chops than by learning to play your favorite songs. Not only is it more fun and much easier than running drills or memorizing a chord book by wrote, it's obviously also a wonderful way to build your repertory of songs. For more information, and to get started playing thi...

Want to play "You Raise Me Up" on the ukulele? Learn how with this free video ukulele lesson from Ukulele Mike. Whether you play the ukulele or bass kazoo, there is no better way to improve your chops than by learning to play your favorite songs. Not only is it more fun and much easier than running drills or memorizing a chord book by wrote, it's obviously also a wonderful way to build your repertory of songs. For more information, and to get started playing this popular song on your own uke,...

Want to play "My Heart Will Go On" from James Cameron's Titanic on the ukulele? Learn how with this free video ukulele lesson from Ukulele Mike. Whether you play the ukulele or bass kazoo, there is no better way to improve your chops than by learning to play your favorite songs. Not only is it more fun and much easier than running drills or memorizing a chord book by wrote, it's obviously also a wonderful way to build your repertory of songs. For more information, and to get started playing t...

Want to play "The Climb" by Miley Cyrus on the ukulele? Learn how with this free video ukulele lesson from Ukulele Mike. Whether you play the ukulele or bass kazoo, there is no better way to improve your chops than by learning to play your favorite songs. Not only is it more fun and much easier than running drills or memorizing a chord book by wrote, it's obviously also a wonderful way to build your repertory of songs. For more information, and to get started playing this popular Hannah Monta...

Want to play "Calendar Girl" by Neil Sedaka on the ukulele? Learn how with this free video ukulele lesson from Ukulele Mike. Whether you play the ukulele or bass kazoo, there is no better way to improve your chops than by learning to play your favorite songs. Not only is it more fun and much easier than running drills or memorizing a chord book by wrote, it's obviously also a wonderful way to build your repertory of songs. For more information, and to get started playing this popular standard...

Whether you're looking to publish your own game or just make your homebrew better, this tutorial is for you. Veteran game designer John Wick shares his insight earned from several decades of being a game designer to teach you how to write an awesome tabletop roleplaying game!

In this video, we learn how to balance a chemical equation. First, take a look at both sides of the equation and figure out how many atoms there are for both. Once you write this out, you will have an idea of how unbalanced it is. Now that you've done this, you need to think about how you can make the equation equal. Look at the first line and then see how many you have to add to one side to make both equal to each other. Then, go to the second line and do the same. When finished, you will ha...
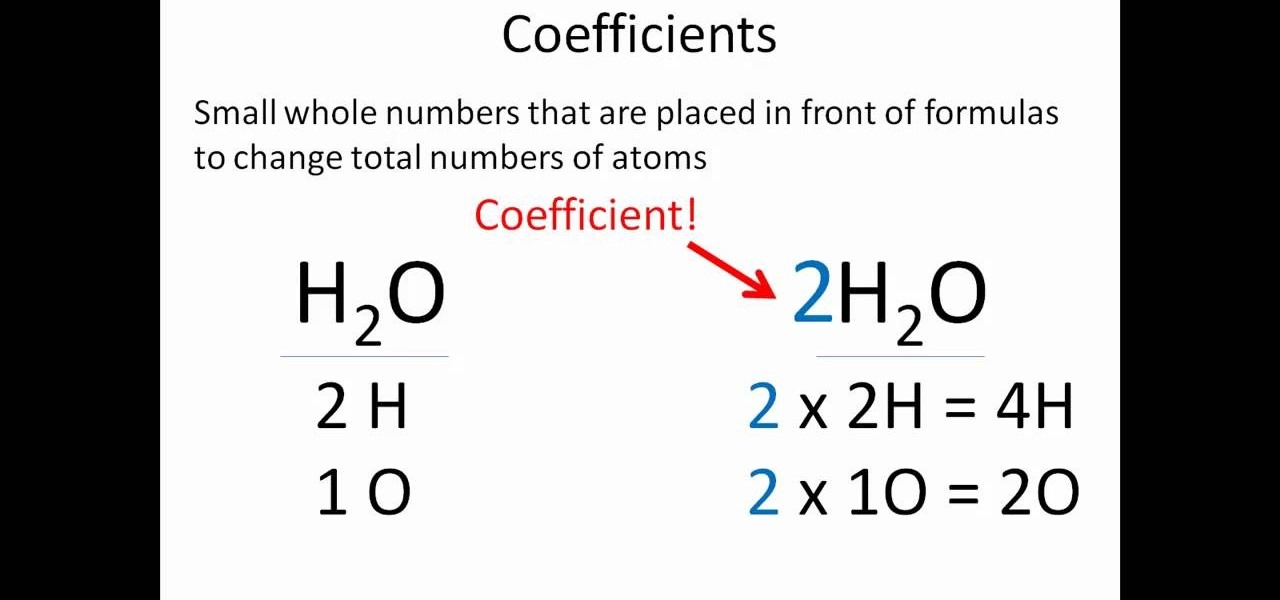
In this video, we learn how to properly balance chemical equations. You will see what substances are in each side of the equation. You will then need to count the atoms that are on each side of the chemical equation. Once you write down the number of atoms on each side, you will need to even them out. To do this, you need to change the coefficients within the equation. These change the total number of atoms inside of a chemical. Once you do this, you will add more to each atom present and the...