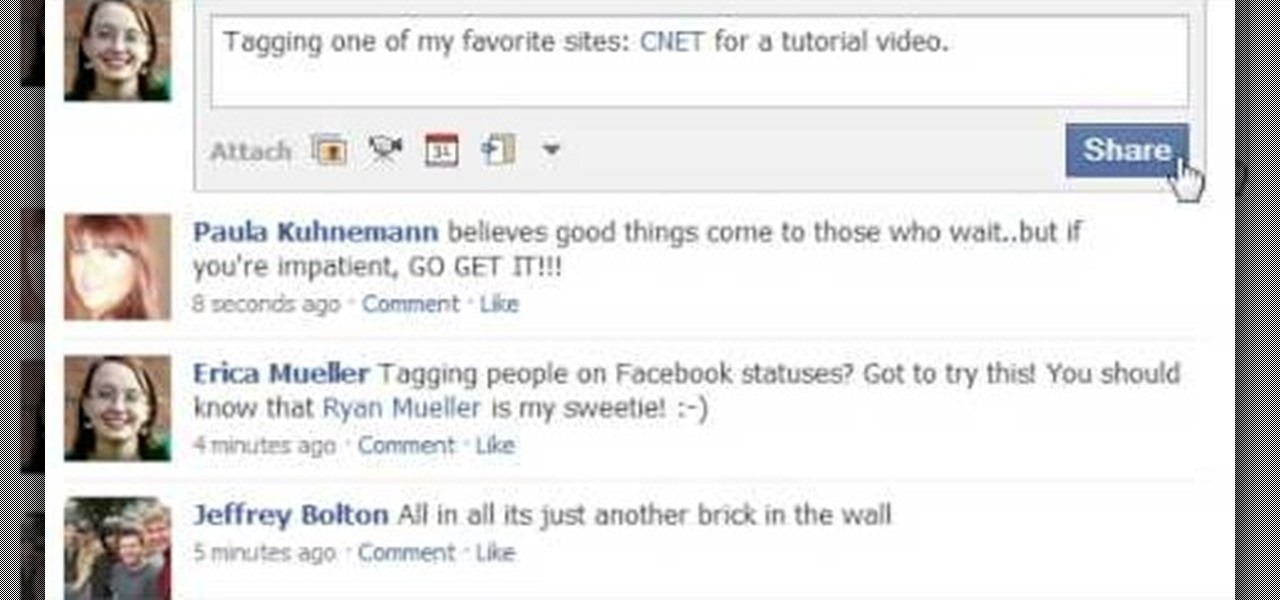
This short video demonstrates how to tag websites and groups in your Facebook status. In your status window start typing what you would like to tag. For example write "Tagging one of my favorite sites:" At this point type the @ symbol. Right after the @ type in the particular site you would like to tag. When you are finished typing press 'Share' and this will appear on your Facebook page with a clickable link to the site you tagged.

This is a really unique video that demonstrates how to make a basic friendship bracelet. It's unique in the sense that there is no one talking to you during the video. It's set to a catchy tune, with step by step instructions written on the screen, and then each step is demonstrated clearly in the video. There's a little humor woven in, no pun intended. Last, but not least, they show you what the end result should look like. Have fun with this one guys!

In these PHP basics video the tutor shows how to do form processing. Handling forms in PHP is basically the main functionality of PHP. The forms in HTML take the values of a from and send them to the PHP in real time to do the form processing. In this video the tutor shows how to make a HTML form from the scratch inserting a form into it with some fields and buttons. Now he makes the form post a method to a PHP page when you submit it. Now he shows how to make a PHP file from the scratch by w...

Can't wait until you get home to get onto MySpace? This video gives step by step instructions on how to try and unblock MySpace while you are at school or on a server that does not allow access to the site. This video does not have narration, but has written instructions on how to get around blocked sites with out using a proxy server. However, you have to have access to the system 32 files for this tutorial to work, and accessing these files does go against a lot of network policies.

This video is about how to use visualization to get a girlfriend. First, you have to wake up visualizing her. This will help you believe that you are capable of finding a girlfriend. Then you make a "My Girl" list. On this list, write down the qualities you would like to see in your future girlfriend. Next you imagine the qualities that your future girlfriend expects of a man. Slowly develop yourself into this guy. After your mind adapts itself to thinking these thoughts, you will find your i...

A fan who recently got "depruded" by his girlfriend (his first kiss) wrote in asking for advice on how to become a better kisser. Kiss like you're tasting a delicate fruit! Step one: Brush your teeth. Step two: GUM! Step three: Stay away from onions and garlic. Generally make your breath smell and taste good, you do NOT want your breath to smell like living death! Step four: Now practice on that delicious delicate fruit. Lips, tongue, and teeth, can all get into the action.

A low tunnel is a kind of mini-greenhouse for your garden. Growing vegetables in a low tunnel requires proper ventilation. In this tutorial, you'll learn how to provide the right ventilation for your low tunnel, keeping your plants happy and healthy.

Garlic is great for spicing up your meals (and keeping vampires away!) and fall is a great time to grow it. In this video tutorial, you'll learn how to grow garlic in your garden. Get some garlic bulbs from a seed catalog, nursery or organic grower, and you'll soon have a garlic crop to be proud of.

Come the fall, your garden is probably going to be looking pretty spare. But it doesn't have to be that way. There are vegetables that will thrive in the fall. In this Growing Wisdom gardening tutorial, you'll learn how to grow vegetables in the cooler months.

Autumn leaves may be beautiful, but they can also be incredibly annoying as they pile up around your garden. But there are things you can do with autumn leaves, like mulching them, composting them and turning them into a living fence. In this episode of Growing Wisdom, Dave Epstein walks you through how to make a leaf fence.

Hack mybrute with this mybrute cheat. MyBrute hacks, cheats, tricks. Watch this video tutorial to learn how to hack black skin in MyBrute (08/13/09).

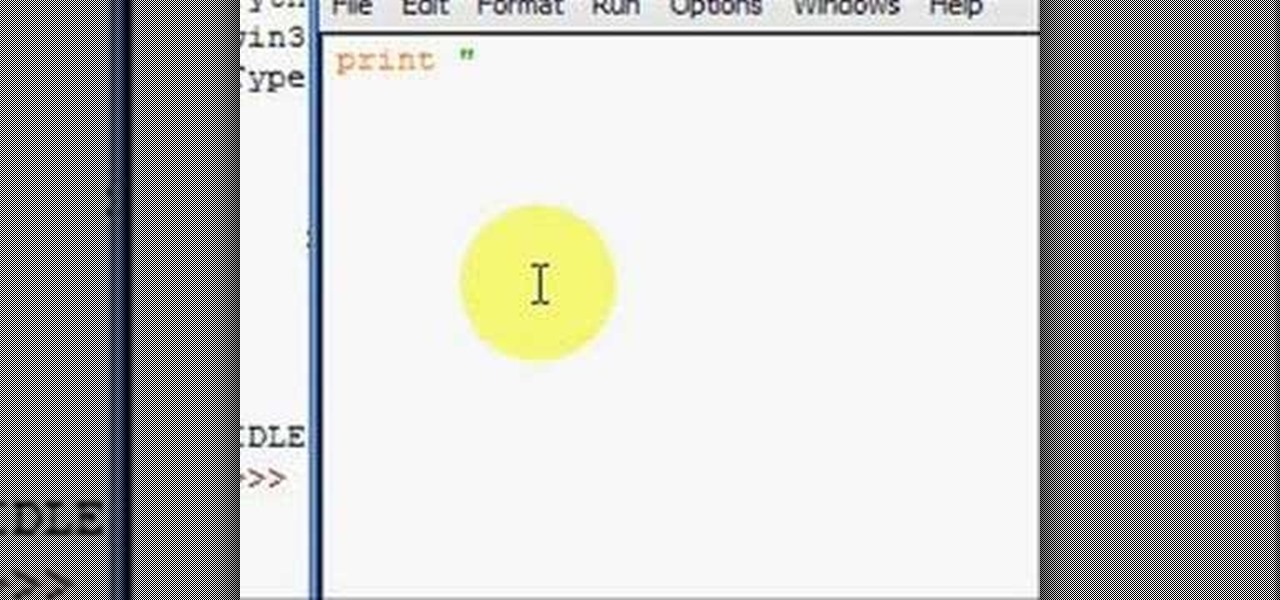
In this how-to, you'll find instructions for programming with the Python programming language. More specifically, this tutorial addresses everything from locating and installing Python to running it and writing your first programs. If you're interested in learning more about the Python programming language, watch this helpful video tutorial.

Want to write ColdFusion within Eclipse? If so, you're in luck: In this three-part video tutorial series, you'll learn how to set up and use CFEclipse, a plug-in ColdFusion IDE for Eclipse. To learn more about the CFEclipse CFML plugin, press play.

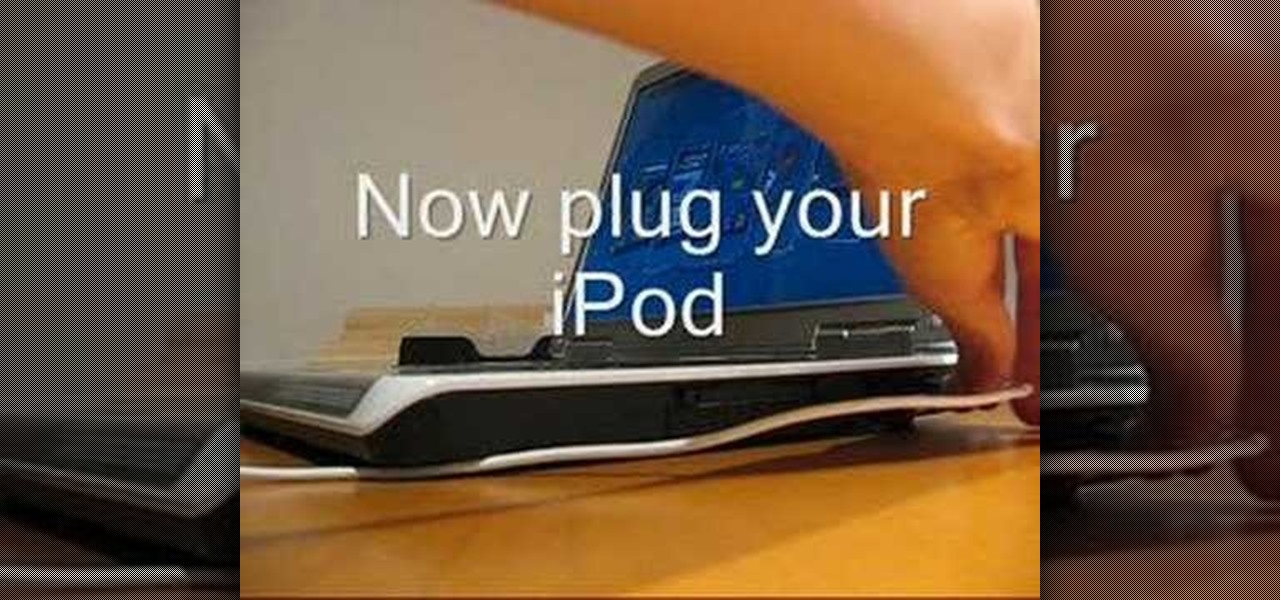
Make your old iPod Video look like the new iPod Classic. This is a tutorial on how to change your iPod Video (5G/5.5G) to a iPod Classic interface. Your iPod must have the 1.2.1 firmware or lower. But don't worry you can downgrade your 1.2.3 by writing The Ultimate Background Hack 1.2.2 You get the background hack and it downgrades your iPod to 1.2.2. You can use any other custom firmware. Watch this video iPod tutorial and learn how to modify an iPod Video to use the iPod Classic interface.

Do you dream of standing on stage in front of millions of fans with a guitar in your hand? You could make this dream come true, if only you could play the guitar! This guitar tutorial series from Robert Renman teaches you the basics of guitar playing along with a few beginner and intermediate techniques. You can learn how to play octaves on the guitar with this lesson. This octave technique is used in many songs. You can be jamming on the electric guitar to your favorite tunes, or even write ...

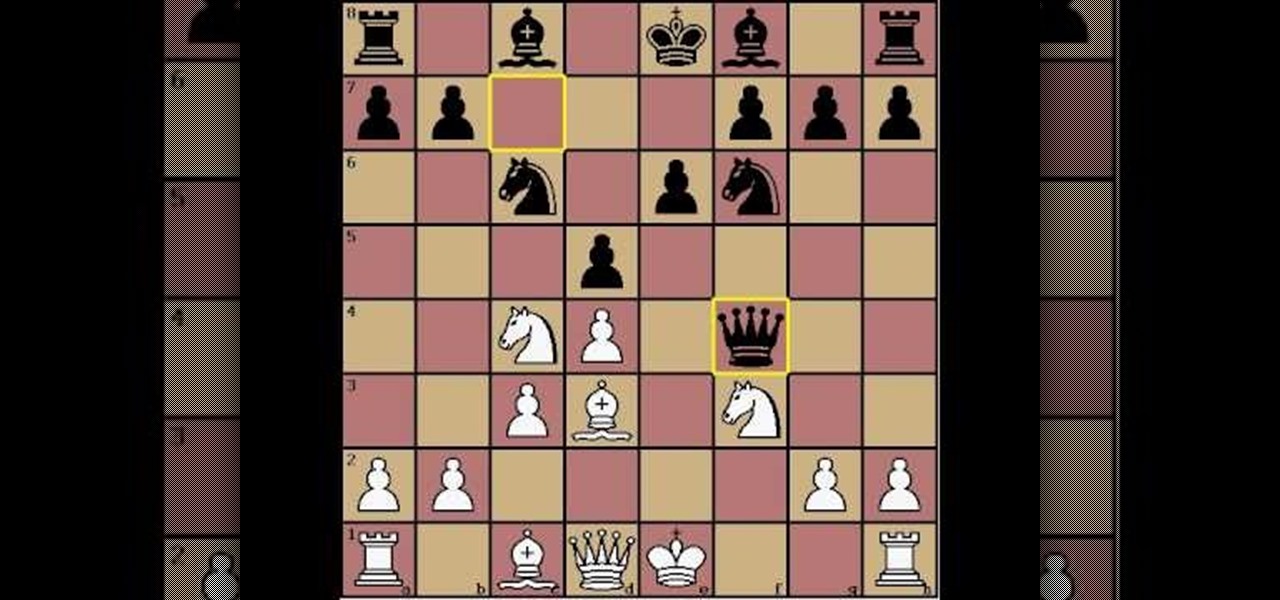
This video features 6...Qc7 in the mainline of the Stonewall, a good move since after the obvious 7.Ngf3, White turns out worse in all lines. Matt suggests an alternate development of pieces including Nh3 and Qf3.

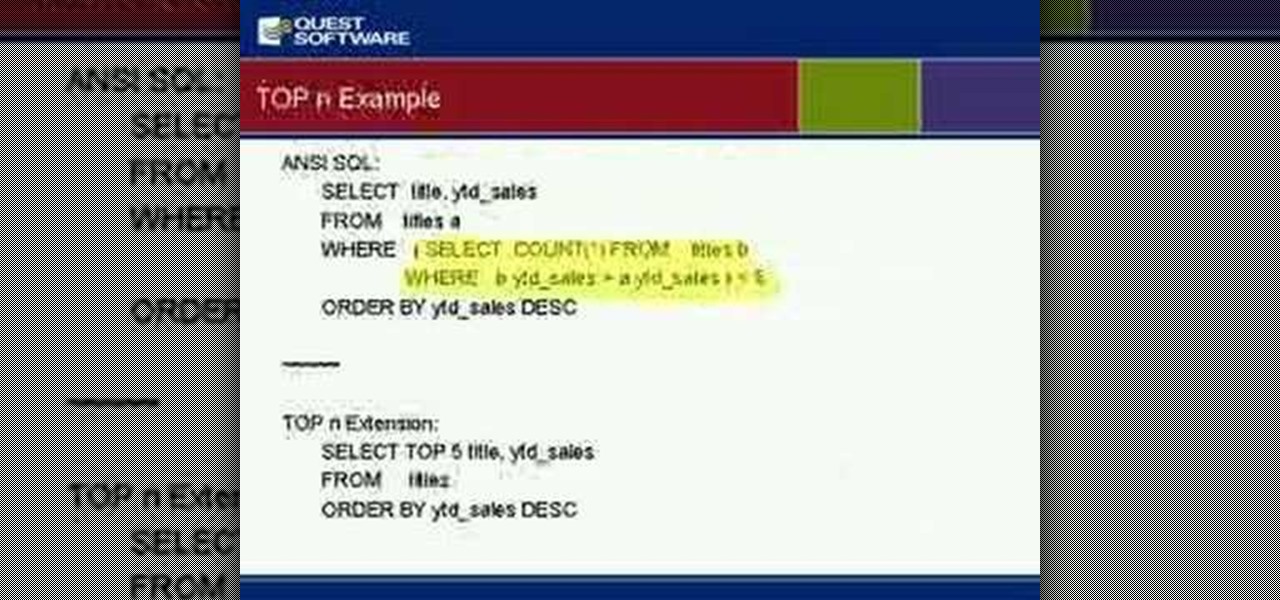
Gain insight into best practices for SQL Server optimization and ways to alleviate many root causes that can impact performance of your SQL Server database. Kevin also will discuss how to manage for planned and unplanned changes, speed time to implementation of your applications and ensure that your databases are running as they should.

New year, new me. You finally committed to working on the best physical you by going to the gym multiple days a week. Except about an hour in, you start getting really tired of it all. Before you run to the exit, pick up your phone.

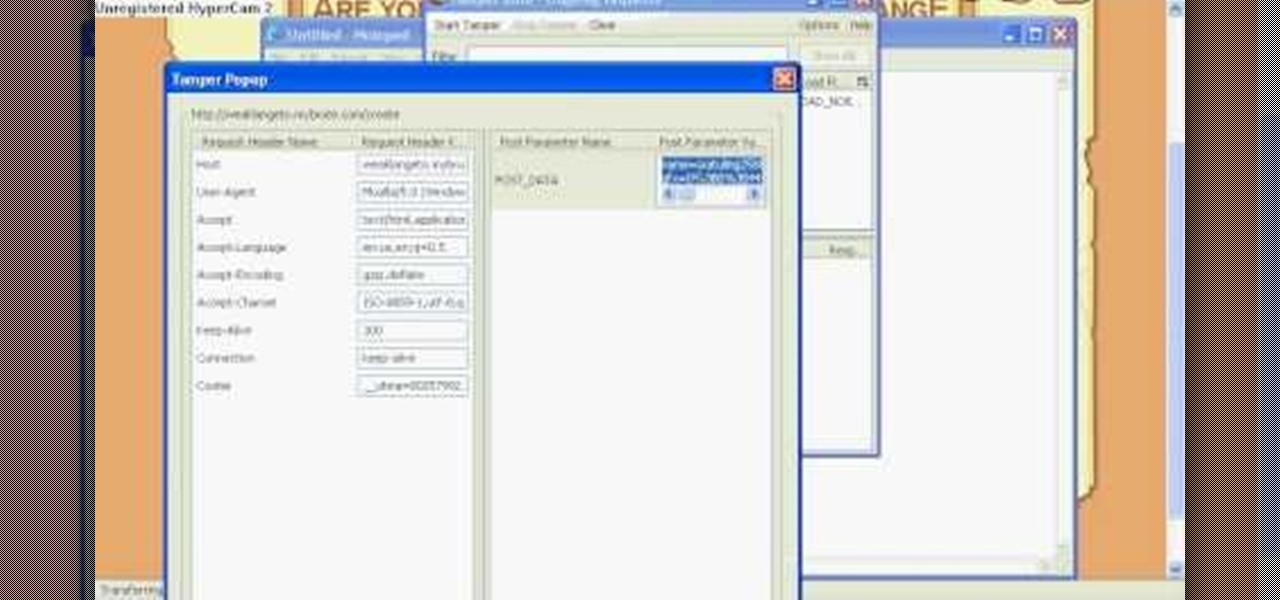
One of the first steps when pentesting a website should be scanning for hidden directories. It is essential for finding valuable information or potential attack vectors that might otherwise be unseen on the public-facing site. There are many tools out there that will perform the brute-forcing process, but not all are created equally.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

While hackers know and love the Raspberry Pi, many don't know of its cheaper cousin, the microcontroller. Unlike a Pi, which can be used more or less like a regular computer, microcontrollers like the Wi-Fi connected ESP8266 require some necessary programming skill to master. In this guide, we'll build an Arduino program from scratch and explain the code structure in a way anyone can understand.

On Instagram, you can write text over any picture or video in your Story, but it may be hard to get your message across with a distracting background. Although there is a "Type" option for Stories, which allows you to write text over colorful gradient backgrounds, the selection is limited to just over twenty options, and there are no options for solid colored backgrounds or translucent overlays.

Two-factor authentication (also known as 2FA) adds a necessary additional layer of security to your username and password in many important apps. On Instagram, 2FA requires you to confirm it's you attempting to log in, with a special code sent to you via text message. Enter the code and you're in ... but what happens when you need to log in and don't have access to your phone?

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.

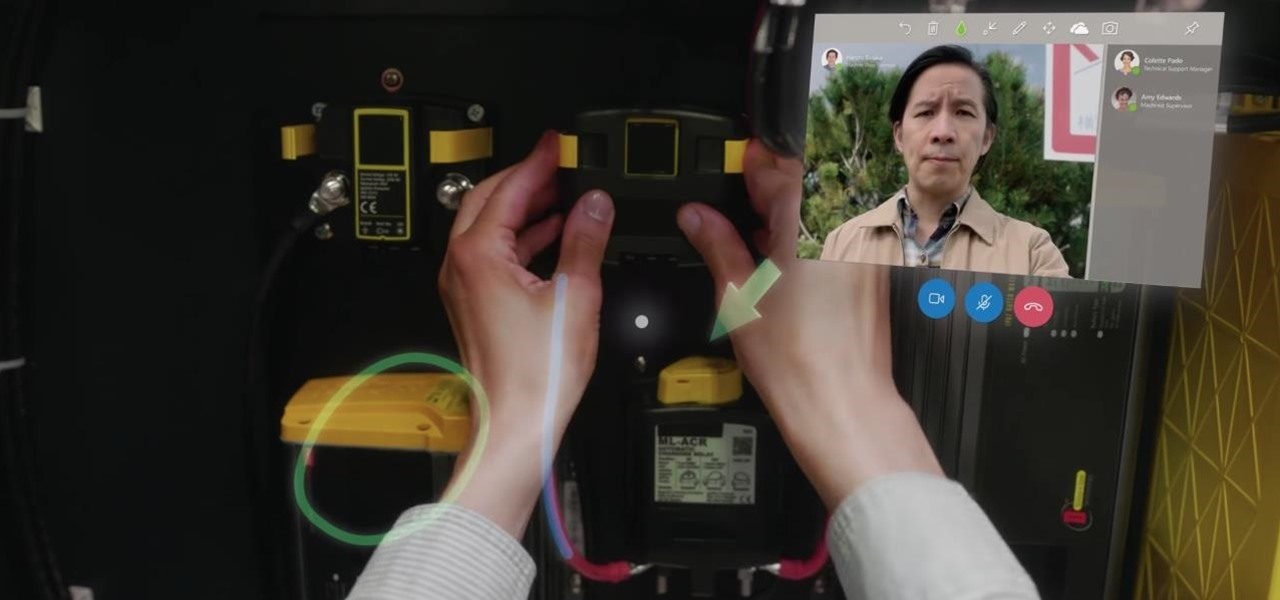
On Monday, at its annual Build developer conference, Microsoft revealed two new apps for the HoloLens apps.

In a LinkedIn post published on Tuesday, Microsoft's leading advocate for the HoloLens made a prediction that the mixing of immersive technologies will define augmented reality in 2018.

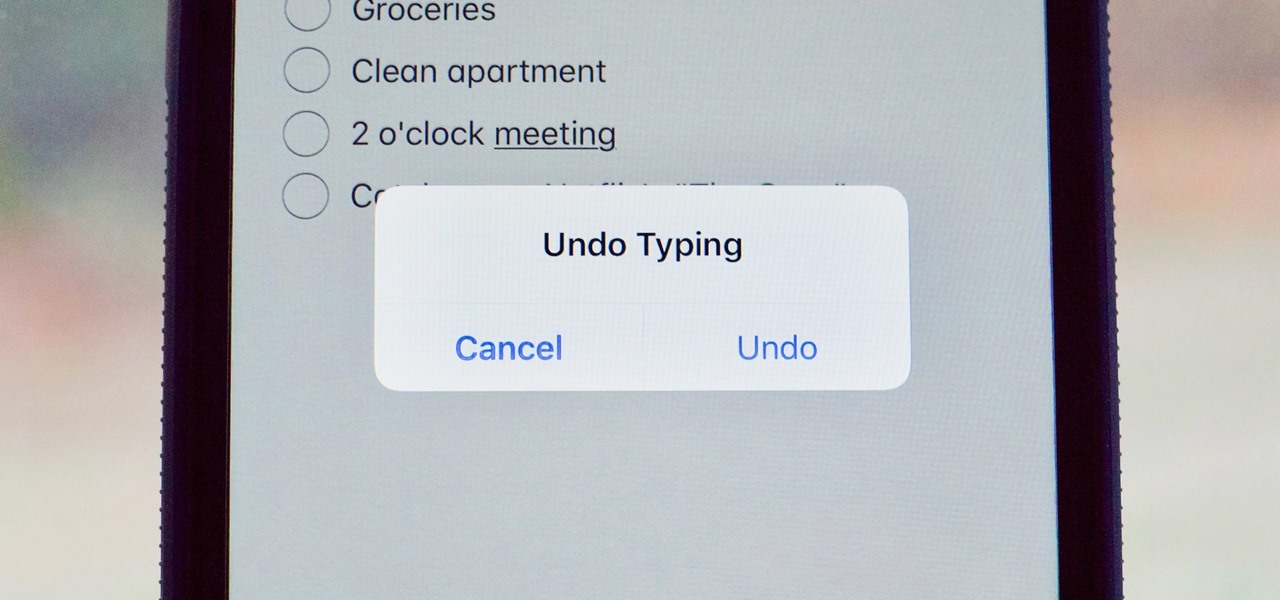
Many of us use the Notes app to jot things down in a hurry. Most of the time, that's no big deal. However, the faster the typing, the higher the chance of error. If you happen to make a typo, or if you accidentally delete that chart you worked so hard on, there's an easy way to undo the changes.

When you have an idea you want to jot down or a quick list to make, the Notes app on your iPhone is a great place to do it. However, by default, Notes use a blank canvas, which doesn't match the physical lined notebooks we're used to. If you've always use unlined or gridless sheets of paper, a blank canvas is probably fine, but you can actually customize your digital stationary with lines or grids.

Paying for street parking in New York City just got so much easier. Instead of searching for loose change or hoping you didn't forget your wallet, you can use a device you always have with you: your phone.

Social media is kind of depressing. On one hand, we love knowing what's happening in the lives of others. On the other hand, everyone seems happier, better looking, and more successful than you. We're putting on a facade by posting statuses and writing comments that present the person we want others to think we are, rather than truly expressing ourselves. Yes, social media has facilitated movements and miraculous events, but let's be real. For the most part, none of it matters.

Over the past week, we are seeing more companies capitalizing on services leveraging augmented reality. One company secured funding to expand their service, while two other companies grow its own services through acquisition.

Hello people, I'm back for Part-3. In this part, as promised, we are going to create a client program and then we are going to test it with our server program made in Part-2.

How is it goin', fellow 1337 haXX0rZ! dtm here with another article, this time, we'll be looking at infecting PE files, executables in particular for this write-up. Obviously some prerequisite knowledge will be needed since this isn't really newbie-friendly. If you are still a beginner, fear not, it might still be interesting to read! Hopefully!
Hey everyone. Only found the site a few days ago but really loving it. Been

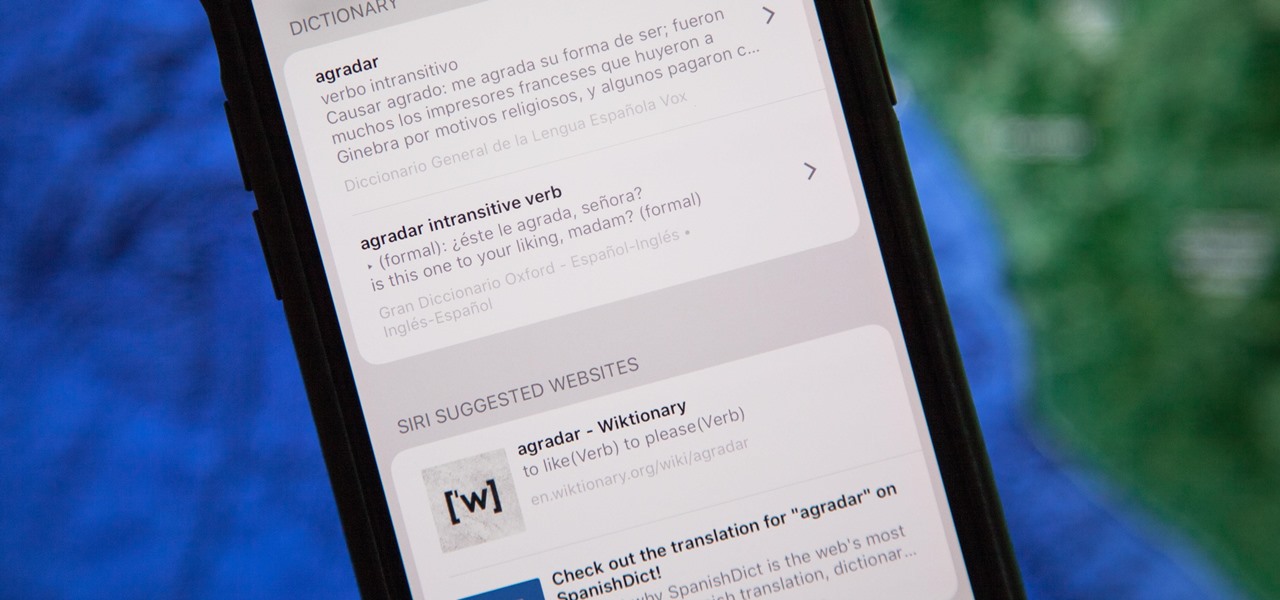
The native dictionaries in iOS, which have been around since 2011, let you define words on your iPhone on the fly in Safari, News, Notes, and other apps. But if you read or write in more than just English, you won't be able to see accurate definitions unless you add those other languages to your list of dictionaries manually.

Welcome back to another C tutorial, this post covering the first part of control structures, if statements. Let's get right into it.

Hi I am a new member of null byte(although I am reading this website from the beginning) and this is going to be my first post.

As many of you know, processor's clock frequency improvement got stuck in about 2003, causing the origin of multicore CPU (and other technologies). In this article I'll introduce you on how to run code simultaneously in various processors (I suppose that all of you have a multicore CPU). When you write code without any parallel directive, it only executes in one CPU at the same time (see it below). OpenMP make simple to work with various cores (if not with all of them) , without so much heada...

Hello my anxious hackers, the week has started and here we begin a new series that I think will help many here and not only, for those that have the opportunity to follow our tutorials but they are not yet part of the community.