
How To: Repair your credit
It’s never too late to clean up your credit record – and save yourself thousands of dollars in exorbitant interest rates in the process. Learn how to repair your credit with this guide from Howcast.


It’s never too late to clean up your credit record – and save yourself thousands of dollars in exorbitant interest rates in the process. Learn how to repair your credit with this guide from Howcast.

Don’t panic if you’ve got a budding Picasso at home—cleaning crayon off of painted walls is simple. Check out this Howcast video tutorial on how to clean crayon marks off of painted walls.

Fix those little scratches before they become big rust marks. Learn how to fix a scratch on your car. Howcast prevents all the necessary steps for ridding your car of that ugly scratch.

Learn how to play "Underneath Your Clothes" by Shakira, an acoustic guitar tutorial. Follow along with this demonstration, tabs and lyrics here:

While it may be tempting to tell your boss where he can stick his letter opener when you’re ready to quit, it’s not a great career move. You will need a job to resign from, good stationery, acting skills (optional). Submit resignation. Submit resignation.

Take a lesson in architecture from renowned architect Doug Patt by watching this video tutorial. If you want to learn about drawing and designing, without going to school, Doug's just the teacher. Watch to see how to draw and letter with lead like an architect.

Grab your acoustic guitar, strap, and your pick and check out this free guitar lesson. This video tutorial will teach you country rock guitarists how to play a Blake Shelton song. Not just any Blake Shelton song, but one of his greatest: "Home." And just so you know, here are the lyrics to go along with this instructional guitar lesson:

Scam School presents four silly beer gags in this how-to video.

The art of inking script capital letters in calligraphy lives on in advertisements and wedding invitations. Learn capital letters in calligraphy and how to write using the art of calligraphy in this free online video series.

You need a break from gloomy coronavirus updates. We all do. The unrelenting stream of doom and negative news is both helpful in terms of keeping ourselves and our families safe, but it also has the unfortunate effect of increasing our anxiety. When will this end? How bad will it get? Is there reason to be hopeful?
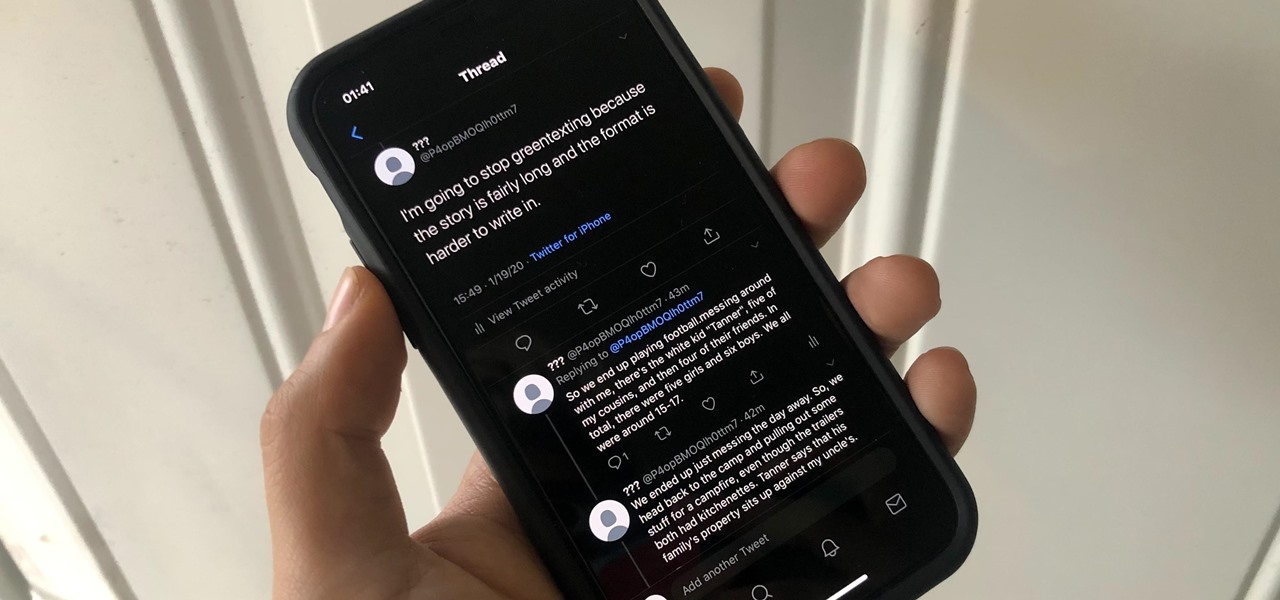
The 280-character limit for tweets on Twitter is double what it used to be back in the day, but it's still not enough to express in-depth thoughts, ideas, commentary, rants, blogs, stories, and the like. These tweetstorms, as they're called, are the reason why Twitter created its threads feature.

Is the augmented reality magic fading down in Plantation, Florida? That's the first question some may be asking following a casual revelation over the weekend that Magic Leap, the maker of the Magic Leap One, has assigned much of its patent portfolio over to JP Morgan Chase as collateral.

Just like Apple and Google, Facebook has been working to develop computer vision shortcuts designed to give mobile apps augmented reality superpowers.
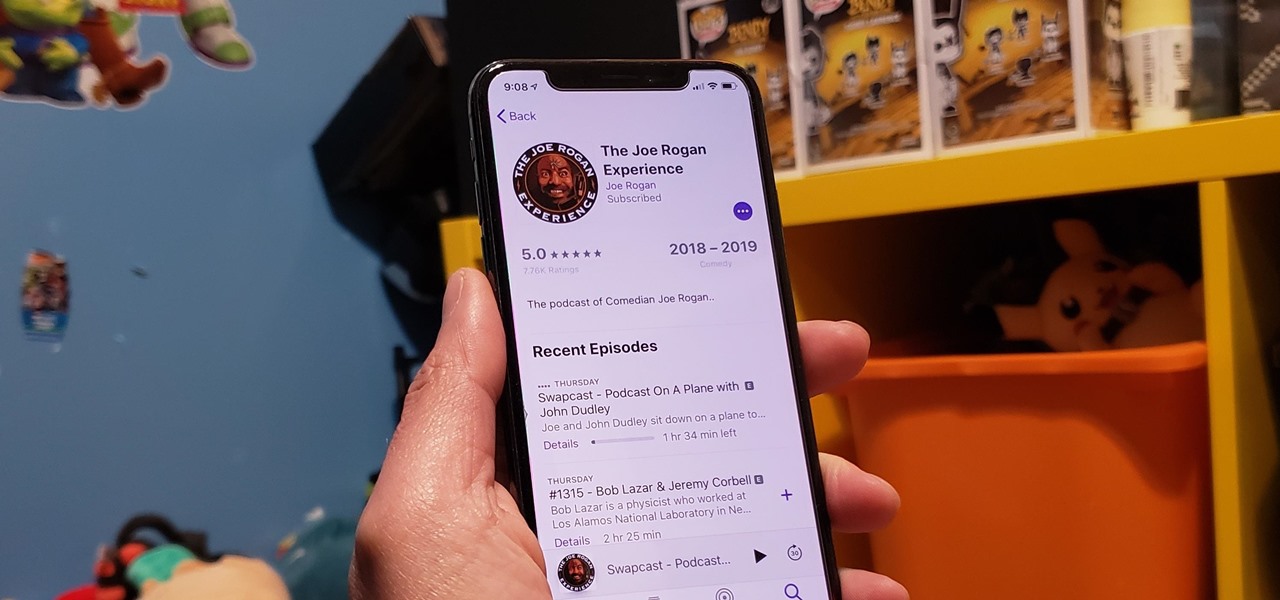
Ratings and reviews apply everywhere, from a restaurant you want to try to a new camera you're thinking of buying and games you might want to play. Podcasts are no different. Reading reviews of shows can help determine which are worth listening to, and your opinion is valuable to other people too. In Apple Podcasts, there are a few different ways to read, rate, and review shows.

Last week at Mobile World Congress 2019, Google put an augmented reality twist on its annual Android Partner Walk via its ARCore toolkit.

Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than others, and a little Python could be used to brute-force any weak hashes to get the passwords they were created from.

Using the ARKit 2.0 announcement as its springboard, software maker Adobe is looking leap up to the level of Unity Technologies and Epic Games, the companies making the go-to tools for creating augmented reality experiences.
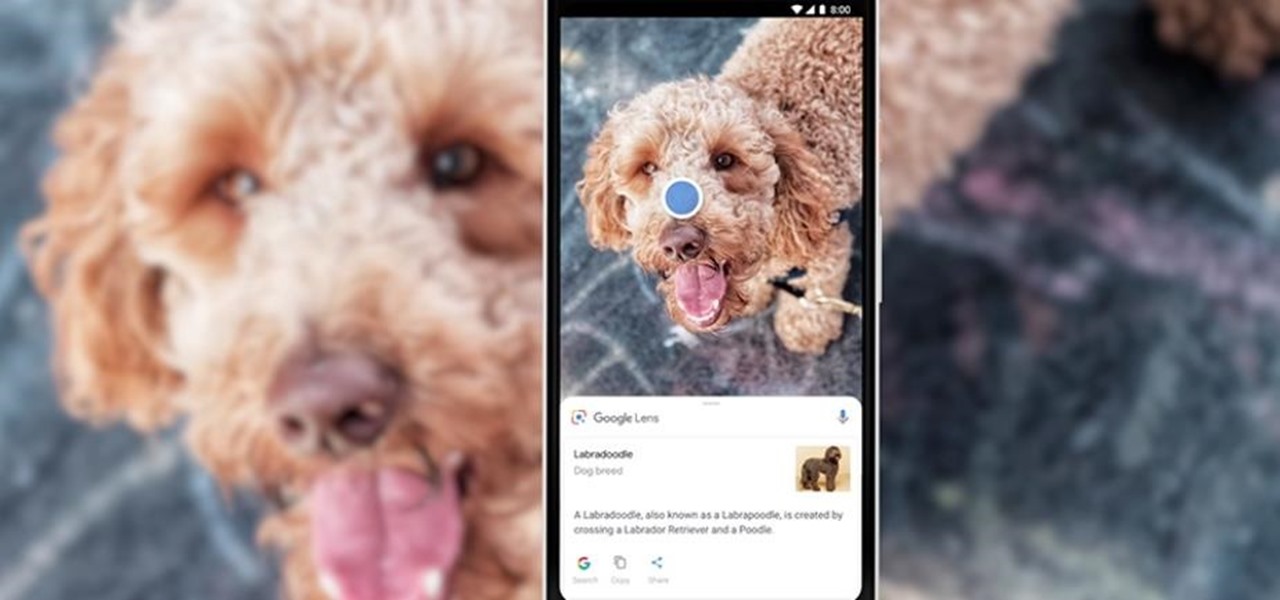
During Tuesday's keynote at the I/O developer conference, Google unveiled new capabilities for its Lens visual search engine and expanded the availability of the platform in smartphone camera apps.

Most of us have probably used a GIF at least once or twice to respond to a message, and that's why a lot of messaging services and keyboards have GIF search tools readily available to use. Now, Google wants to take GIF responses to a more personal level, by allowing you to create your own selfies GIFs to instantly sent to family and friends.

An attacker with shell access to a Linux server can manipulate, or perhaps even ruin, anything they have access to. While many more subtle attacks could provide significant value to a hacker, most attacks also leave traces. These traces, of course, can also be manipulated and avoided through methods such as shell scripting.

The launch of the latest line of iPhones came and went without major revelations for advanced AR hardware other than the next iteration of processors and cameras.

This is a tale about microbes, a man who became a hermit, and the parchment that carries both of their stories.

A vaccine against HIV might prevent the disease that we can't seem to cure. Some HIV patients make antibodies that can take down the virus, much the way a vaccine might. But, scientists haven't been able to provoke that type of response in other people. However, in a process that might work in humans, a group of researchers has successfully generated antibodies in cows that neutralize multiple strains of HIV.

When the climate changes, so do all the things that rely on the climate, including people, plants, and pathogens. A European study recently took a broad look at what kind of microorganisms are most likely to be affected as climate change heats, cools, dries, and wets the world around us.

As if the swollen, painful joints of rheumatoid arthritis weren't enough, the disease is the result of our immune system turning against cells of our own body. Ever since this realization, scientists have worked to find the trigger that sets the immune system off. Scientists believe that gut bacteria may have a role in initiating the abnormal immune response. Now, a team of researchers from Boston has figured out how that might occur.

After years of telling patients to finish any prescribed course of antibiotics completely, a group of researchers in the UK say it is no longer necessary, and could even be harmful if we want to preserve the antibiotics we can still use.

It is not just a bad summer for ticks — it has been a bad decade for the spread of tick-borne infections. New surveillance from the CDC reports rapid expansion and increase in cases of babesiosis, a sometimes life-threatening disease, in Wisconsin.

The USB Rubber Ducky comes with two software components, the payload script to be deployed and the firmware which controls how the Ducky behaves and what kind of device it pretends to be. This firmware can be reflashed to allow for custom Ducky behaviors, such as mounting USB mass storage to copy files from any system the Duck is plugged into.

Bone loss and belly fat may no longer be certain fates of menopause, thanks to new research from an international team of scientists.

The problem with HIV is that it attacks and kills the very cells of the immune system that are supposed to protect us from infections — white blood cells. But a new technique, developed by scientists at The Scripps Research Institute (TSRI) in La Jolla, California, offers a distinct HIV-killing advantage.

An innovative new wound dressing has been developed by a research team at Lodz University of Technology in Poland that uses crustacean shells to create a bandage that packs an antimicrobial punch — and even more potential to help solve a global problem.
This month, Iowa issued their first hepatitis C virus epidemiological profile and the news was not good. The number of cases of hepatitis C reported in Iowa between 2000 and 2015 rose nearly threefold, from 754 cases in 2000 to 2,235 cases in 2015.

Maternal infection with genital herpes, or other pathogens, during early pregnancy could increase risk of autism, or other neurodevelopmental disorders, says a new study.

We all know you are what you eat—or so the expression goes—but it's good to remember that what you are (at least intestinally) is mainly bacteria. A new study has shown that what you eat, and how your gut microbiome reacts to that food, might be a key player in your risk of developing a certain type of colon cancer—and changing your diet can help decrease your risk.

The story of Helicobacter pylori is a real testament to the tenacity of medical researchers to prove their hypothesis. It took decades before the scientific world would accept that the bacteria H. pylori caused ulcers.

We're on the verge of an amazing evolution of technology where we can work and play in virtual worlds that merge with our own—or let us escape into our imaginations entirely. But creating virtual, mixed, and augmented reality experiences requires resources and hardware that not everyone has access to. If you want to build something awesome with the Microsoft HoloLens (or one of the other awesome platforms), we want to help you do just that.

Microsoft enjoyed a few months in the spotlight after releasing the developer version of the very first mixed reality (MR) headset, but now we're starting to see the competition jump in.
Hello, I'm a new guy around here and since I'm not seeing much tutorials in C i thought of contributing with something relatively simple. This will be a short series.

This is my first article on here, it's based off of a project that I'm working on at school which is on three ways to bypass windows user password's. If all goes as planned and you all would like I'll work on part two and part three and post them as soon as I can. I do have to give credit to Puppy Monkey Baby and The Defalt, both of whom are my classmates at college and have helped me with writing this article.

Welcome back, my budding hackers! In this series, I have been trying to familiarize you with the many features of the world's best framework for exploitation, hacking, and pentesting, Metasploit. There are so many features, and techniques for using those features, that few pentesters/hackers are aware of all of them.