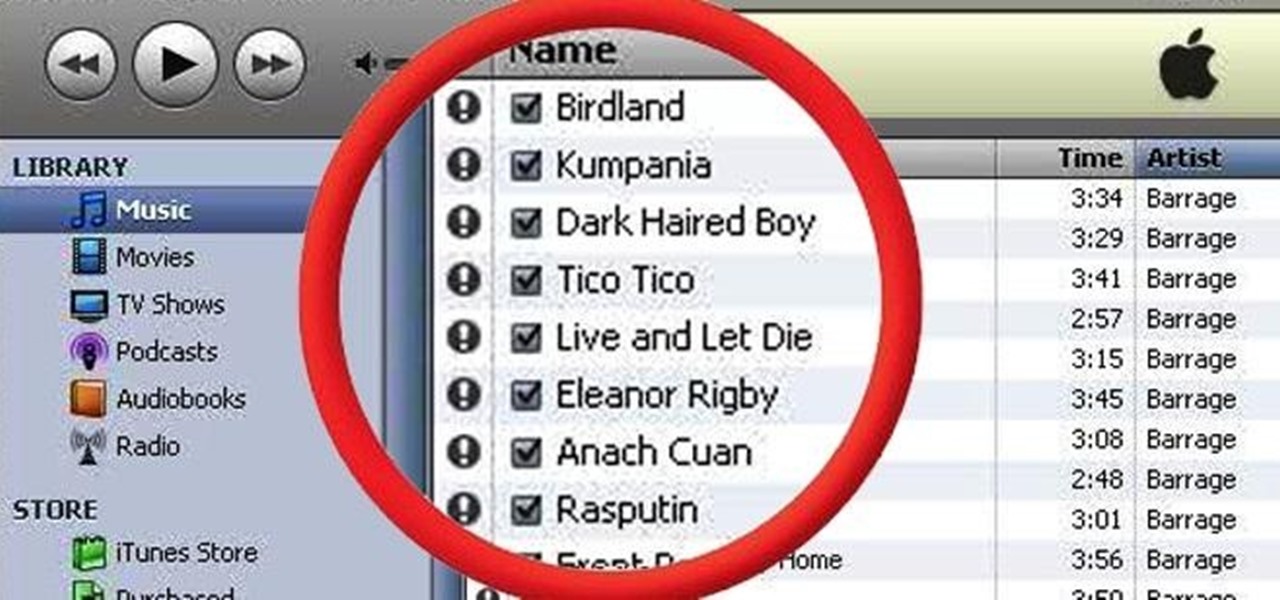
Thanks to Flutter, it's now possible to control the music on your computer simply by making a few hand gestures. The app is available for both Windows and Mac and uses your computer's webcam to monitor your hand movements. Through the use of a few simple hand movements, you can play, pause, forward or replay your music. Flutter works with iTunes, Spotify, Quicktime, MPlayerX and a few other programs.

Rooting your device gives you all-powerful administrative access to your phone and its system settings. Of course, with such power comes great responsibility, and sometimes that responsibility becomes to burdensome or just plain unnecessary.

Lucid dreaming, in which you're aware that you're dreaming, can be profoundly beneficial to us. It gives us freedom to do things we couldn't possibly do in the real world. It can show us the true potential of our brain power. You can even use lucid dreaming to question the nature of our own reality. For whatever reason, people everywhere are interested in this mysterious phenomenon...especially in achieving it. Whether it be visiting another planet or flying around, the possibilities in lucid...

You may have never heard of vacuum forming, but you use products made with the technique all the time. The lid on your coffee cup, the plastic bowls you used at last week's barbeque, and the blister packs your prescriptions come in are all made with a vacuum forming machine.

Combination locks in Minecraft can be really simple or frustratingly difficult, but no matter how complicated they are, some of them fall victim to the same simple exploits.

Admit it—at some point or another, you've wished that you had your own personal hovercraft. Don't worry, we've all been there. Well, a company called Aerofex wants to make a hovercraft that's way more than your standard leaf-blower-powered one, taking a queue from the swoop and speeder bikes from the Star Wars franchise, building their own sort of repulsorlift. This hover bike may not be quite as fast as the ones from Star Wars, but if the company has its way, it could be on sale by the end o...

If you've ever mistakenly moved your music files around without relinking them in iTunes, you might now be noticing that you have a long list of tracks asking you to relink them. You could go through them one by one, redirect them to the new file location, then delete any copies. Or you could try to track them all down and delete the old references. But come on, who wants to spend that much time when you can clean up your library using this clever method using only Notepad on your Windows com...

Technology is awesome. You can use your iPad to record music or even turn your tunes into a solar system, but sometimes being plugged in all of the time can leave you nostalgic for simpler times. This new concept by Joelle Aeschlimann brings together the best of both worlds by turning your iPad into an old-fashioned, hand-cranked music box. The artist created three different music boxes, each one with its own unique song and visualization. The music boxes were made using wooden cylinders with...

Did you know you can help protect yourself when traveling with a gun? No, not like that; and not in any way that's going to land you in prison. Simply by packing a gun, you can ensure that not only will your luggage be safer, but that the airline will make certain that it reaches its destination. Photo by Alamy

Are you getting that nasty "Application access set to not allowed" error on your Nokia 5300 cell phone? Unfortunately, it's a problem for most Nokia 5300 owners, ones who wish to use 3rd party applications on certain carriers, like T-Mobile, who restricts the uses for branding.

Even those with hearing impairments need to know basic first aid procedures, because everyone, including deaf people, can save a life one day. People may collapse unexpectedly for a number of reasons, and people who faint periodically, or those who suffer frequent seizures or from epilepsy need help from others, so it's important that everyone know the proper first aid procedure for saving a collapsed victim casualty.

This how-to video describes how to properly write a cover letter. It explains that a cover letter is a separate selling point from the resume when applying for a job. The cover letter should only be about two-thirds of a page long and can easily be broken into three parts. Part one includes a brief introduction, what you are applying for, and a quick thank you for your time. The second part is the body where you explain why you are the right person and right fit for the job. The third and fin...

If you need to know how to make an arrangement on an acoustic solo fingerstyle guitar, you've come to the right video tutorials. This three-part instructional guitar lesson will show you want you need to know about arranging.

Although mainly demonstrational, this video shows you how to play a song "The Japanese Sandman" on guitar. This video is intended for advanced players who learn easily by watching or listening. Read the useful tips posted below to aid your guitar learning:

In this lesson, you will learn how to solve a probability word problem. Need help with your algebra and geometry? Well...

You don't have to be a sculptor along the likes of Michelangelo to create an aesthetically appealing, well-made wooden sign. In fact, all you need is a router and steady hands. Well, and maybe some practice.

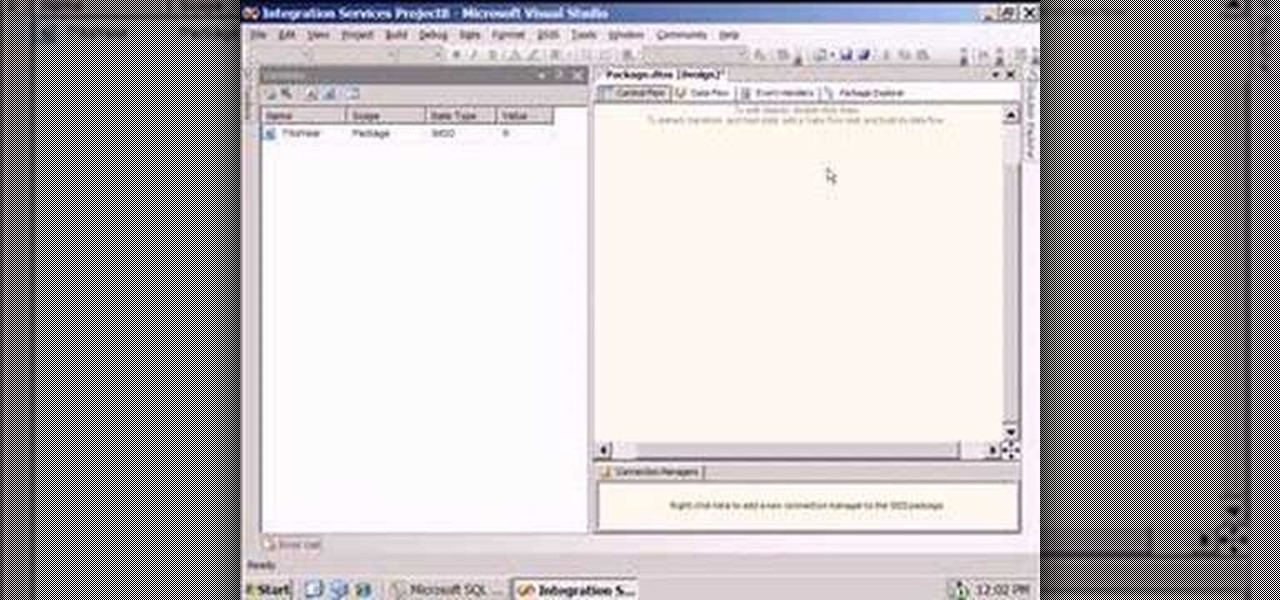
Expressions are new in SSIS (meaning that they were not in DTS) but they allow you to create extremely flexible packages. Expressions can be used to assign values to variables, help you determine whether to execute a task, and to assign properties. If you ever found yourself writing ActiveX code (VBScript) in DTS to determine which task to execute based on a variable's value, then you probably can forego the scripting all together in favor of expressions! They are very powerful in SSIS and yo...

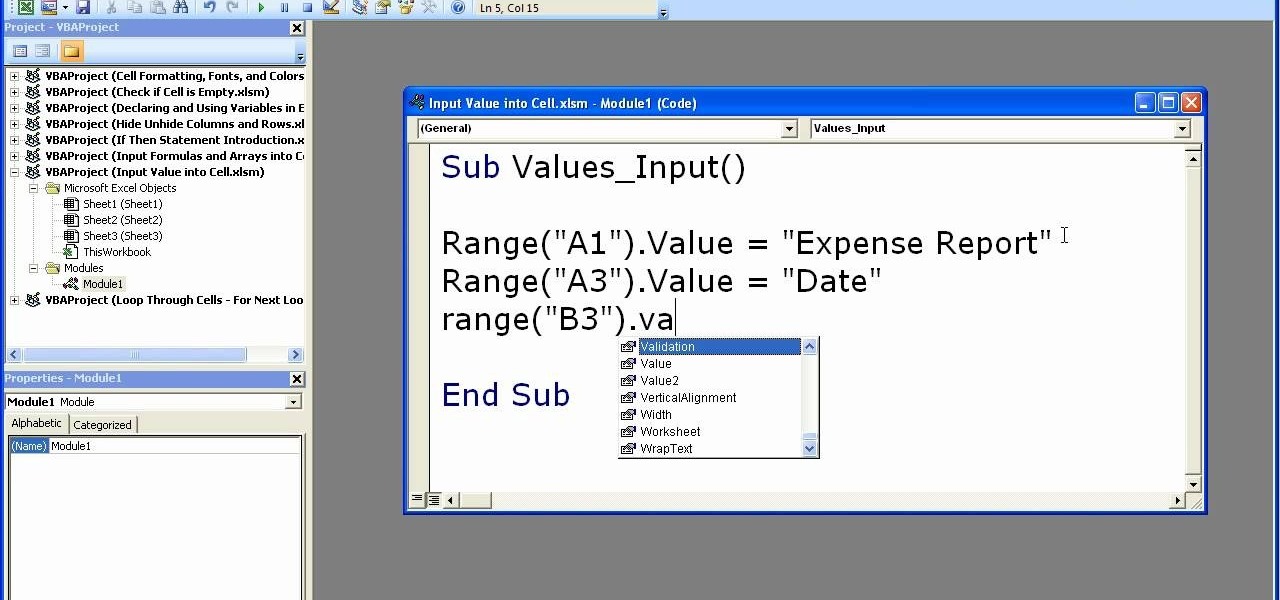
This video shows how to enter values into cells using Excel macros and Visual Basic. This includes a sample Expense Report that is used in this demonstration. In this demonstration, we will create the macro that inputs a title as "Expense Report", Three columns i.e. "Date", "Item" & "Amount", and the summery field as "Total Expenses", as well as the formulas located at the respective cells. Now, we're going to use two keyboard shortcuts i.e. "Alt + F11" to open-up the VBA window and "Alt + F8...

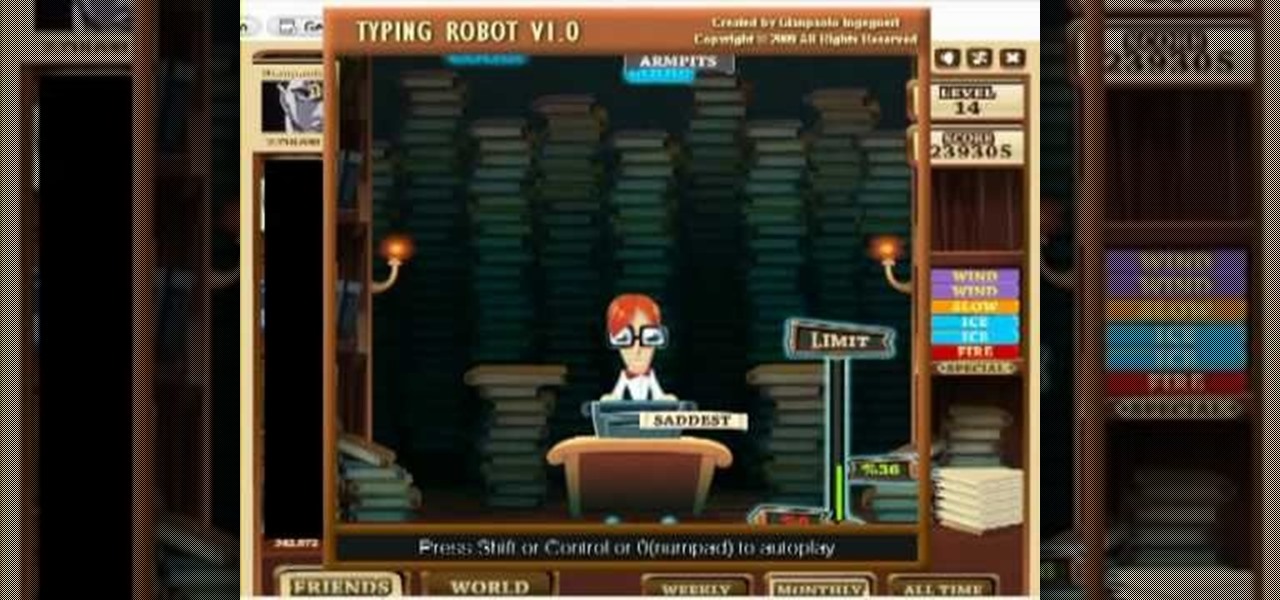
http://www.texturemind.com/post463/ TypingRobot is an artificial intelligence studied to increase your points record with the Typing Maniac game on Facebook. It can recognize several labels because it uses a powerfull OCR system (tesseract) and some principle of word correction. With this program you can make millions of points without problems (my personal record is about 2.700.000 points).

Learn how to follow proper netiquette rules. You may be a model of decorum in person, but a bonehead online. Check out how much you know about Internet manners.

You'll need to be playing this game on a PC, since that's what Cheat Engine has been written for. If you are, then just download the program and use the following steps to hack your money in Grand Theft Auto: San Andreas!

This video palmistry lesson brought to you by two amateur enthusiasts goes over the basics of reading your own palm. Unlock the secrets of written in the lines on your hand! Follow along with the diagram to find your own heart, head, and life line, and find out what these things mean about you. Check out this vide and learn how to read palms.

A curriculum vitae, or CV, are for professionals that are in the academic field and there are specific details on how to complete one. Follow the correct format of writing a CV with advice in this free video from a career adviser here to help people get the job they want.

A cover letter is a quick description as to why this resume is better for a particular job position than all the other resumes, so having specific job position details in it is very important. Write a cover letter specific to each job application by using these tips from a career adviser in this free video on job guidance.

If you're new to DreamCoder for Oracle, one of the things you may want to know how to do is to is write complex SQL queries. Happily, this tutorial will walk you, step by step, through the process. To learn how to use the DreamCoder for Oracle Query Builder, press play!

Follow these step-by-step instructions to fold an easy origami bookcase. You need one large piece of origami paper to complete this project. The visual guidelines are accompanied by written instructions. You can use this origami bookcase to store to store origami books.

This language tutorial teaches you how to read and pronounce Arabic letters. Follow this three part how to video and you will be reading and writing modern standard Arabic in no time at all.

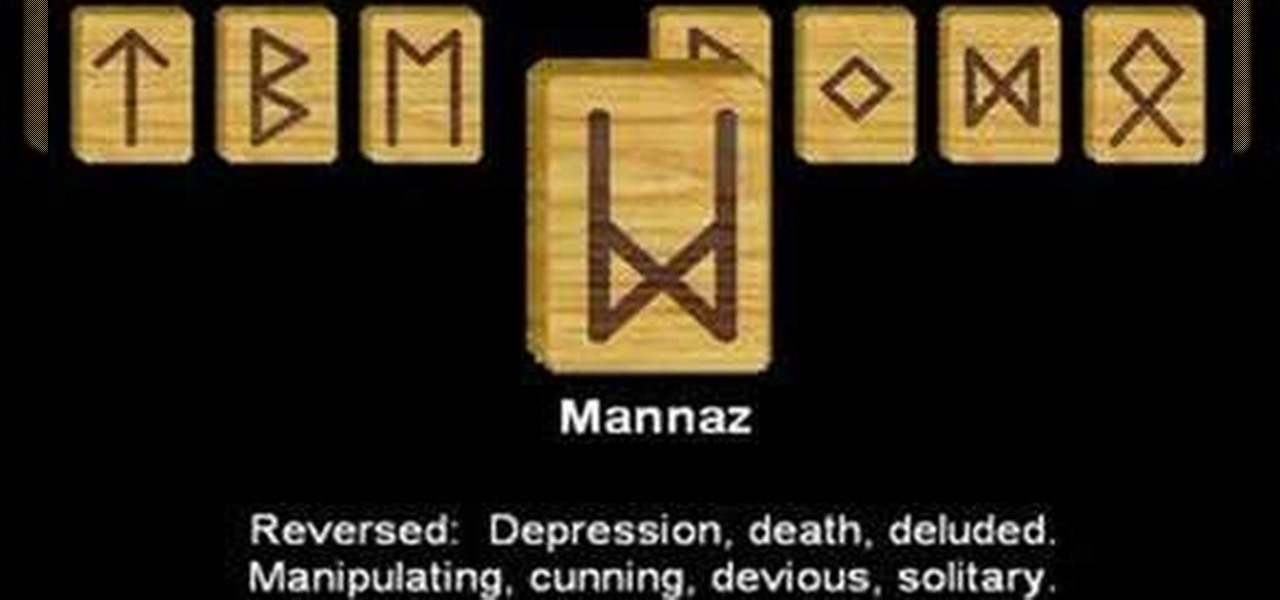
Check out this instructional video to learn the third aett runes of the Elder Futhark. This is Tyr's aett.

This tutorial explains how to list files in a recursive manner within C#. It expands upon the code for writing a program that lists files, so if you can't do that yet, watch that tutorial first.

Benny from askbenny.cn teaches you how to use "ba" correctly in Mandarin Chinese sentences including how to say "You wrote my name wrong, please correct it."

Ian Ozsvald walks you through installing and testing Python 2.5 downloaded from Python.org. This includes how to start Python from the Start Menu and writing your first (Hello World) line of Python code.

Choosing which programming language to learn next can be a truly daunting task. That's the case regardless of whether you're a Null Byter just beginning a career in development and cybersecurity or you're a seasoned ethical hacking and penetration tester with years of extensive coding experience under your belt. On that note, we recommend Python for anyone who hasn't mastered it yet.

Next to Apple, Snap is currently one of the most important companies on the planet in terms of delivering products that are moving augmented reality into the mainstream. That's why it's no surprise that Facebook, which is also focused on AR and tried to acquire the company for $3 billion several years ago, duplicates many of the smaller company's features.

If you record yourself for a vlog or story post using your selfie camera, it can be challenging to stay on message. You might worry too much about the way you look or sound to focus on what you want to say. Using a script can help, but looking away from the camera to read is unprofessional, even on social platforms like Instagram. What you need is a teleprompter, and there are apps for that.

Featured on MTV's Catfish TV series, in season 7, episode 8, Grabify is a tracking link generator that makes it easy to catch an online catfish in a lie. With the ability to identify the IP address, location, make, and model of any device that opens on a cleverly disguised tracking link, Grabify can even identify information leaked from behind a VPN.

If you want to get started sniffing Wi-Fi networks, you usually need to start with a wireless network adapter. But thanks to a Wi-Fi sniffing library written in Arduino and the ultra-cheap ESP8266 chip, you might not need one. For less than $10 in electronics, you can build a tiny Arduino Wi-Fi sniffer that saves Wireshark-compatible PCAP files and fits anywhere.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebody to write a few Python scripts to make it do whatever they want.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

For anyone using open source information to conduct an investigation, a balance between powerful tools and privacy controls are a must. Buscador is a virtual machine packed full of useful OSINT tools and streamlined for online research. This program can easily be set up in VirtualBox, and once that's done, we'll walk you through some of the most useful tools included in it.