
News: Stabilizing Bracelet Helps Artist with Parkinson's Draw Again
Having control of your basic motor functions is something most people take for granted, but for individuals with Parkinson's disease, that is not the case.


Having control of your basic motor functions is something most people take for granted, but for individuals with Parkinson's disease, that is not the case.

Backdoors are convenient to leave behind once you've already found a way into a server, and they can come in handy for a variety of reasons. They're good for developers who want a quick way into machines they're working on, or for systems administrators who want similar access. Of course, backdoors are also a hacker's best friend, and can be added in a variety of ways. One good tool for doing this is Weevely, which uses a snippet of PHP code.

Take one down, pass it around, 99 bottles on which to play classical music? As someone who has studied music extensively, I've seen many interpretations of famous pieces of music played on glass bottles, but hearing these four interpretations of famous pieces (not all classical) completely blew my mind.

Super Mario Bros. is one of the most renowned games in history. It helped resurrect a dying video game industry in the mid-'80s and still remains one of the best-selling video games of all time—one reason why the new NES Classic Edition is so popular and impossible to get these days. Its simple story of a plumber trying to rescue a princess resulted in a video game empire for Nintendo.

In 4.74 seconds, I can barely bend over to tie my shoes, and somehow this guy managed to crush the human world record for solving the Rubik's Cube in that time exactly.

We're almost there to completing the setup of your Mac for hacking! Now that we have Git and Homebrew under our belts, it's time to take on something fairly easy, but very important for our hacking needs.

Ah, ginger. From stir fry to smoothies, ginger is a reliably sharp and refreshing flavor that adds zing to everything it touches. It may be a pain in the ass to remove the skin from ginger (or not), but the zest it brings to food is well worth the trouble. Don't Miss: How to Brew Your Own Ginger Beer Like a Boss
Whatever you think of Google's new Pixel phones, the one thing we know for sure is that these are the most polarizing devices in recent memory. On the one hand, we've seen reviews in which longtime Android users say they'll be walking away from the OS all together thanks to Pixel. On the other hand, you've got the iPhone-obsessed David Pierce over at WIRED saying he'll be switching immediately.

A company known as Cyanogen, Inc. has been in the news numerous times over the past year, and almost every time their name is brought up, it's amid reports of an impending doom. The writing is on the wall for the makers of Cyanogen OS, as it appears that there is little that can be done to prevent the company from going belly-up in the near future.

When it comes to hacking guides, most are written from the perspective of a Linux user. There are a few outliers, but it's mainly Linux, which leads to the idea that Linux is the only OS that's viable for hacking. This couldn't be further from the truth. A properly set up Apple machine can do quite a bit of heavy lifting.

Security journalist Brian Krebs recently suffered a record-breaking DDoS attack to his his website, clocking in at or near a whopping 620 Gbps of traffic. Krebs' site was down for over 24 hours, and it resulted in him having to leave his CDN behind.

Hello, Null Byters. I'm Barrow, and I'm excited to introduce myself as the new admin here on Null Byte. Just like previous admins have done before me, I will be writing new guides, updating older guides if they need it, and responding to some of your issues in the forum. Before I get started with any of that, though, I wanted to talk a little bit about myself and the future of Null Byte.
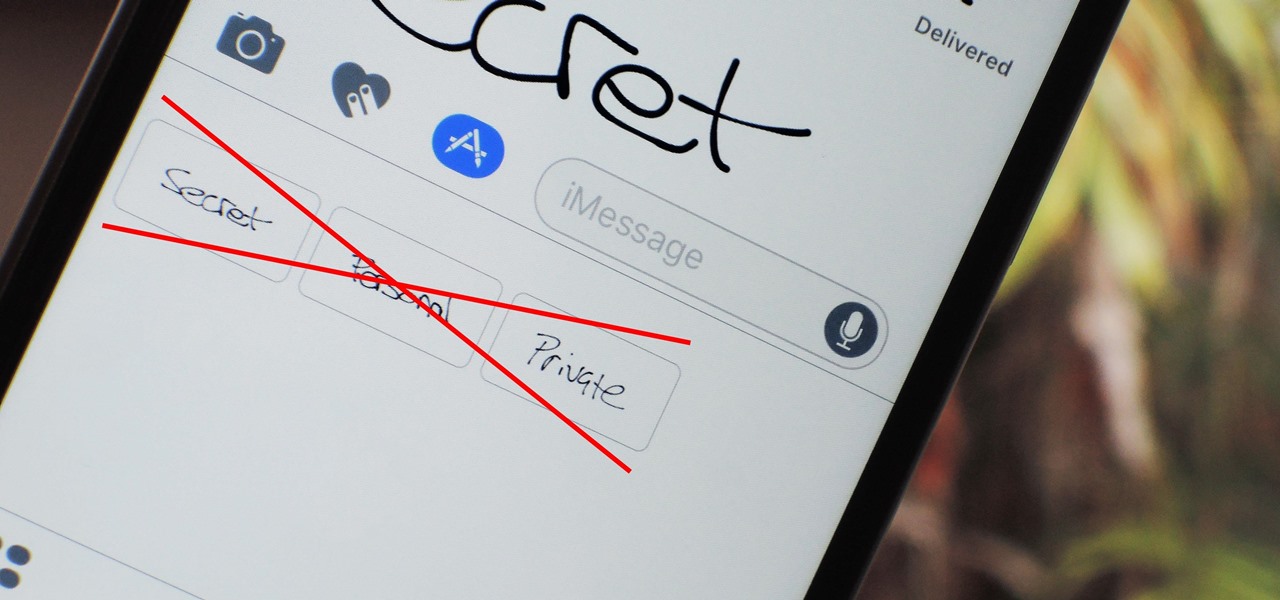
There are lots of cool new additions to Messages in iOS 10, including the ability to send GIFs, as well as custom stickers, weather info, and lots more with the new App Store for Messages.
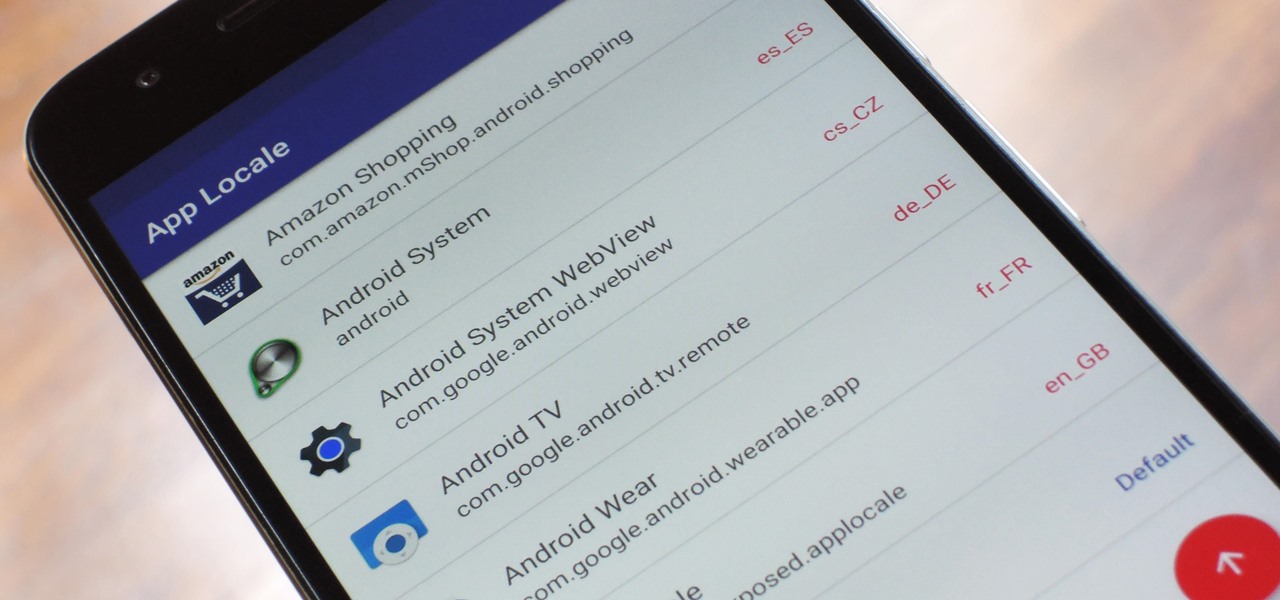
Android clearly wasn't made with bilingual users in mind. When you set a default system locale, every app on your phone uses that region's language—and there's no granular control here. This really becomes an issue if you use social media or news apps that are primarily in a different language, because apps are generally written in the developer's native tongue, then poorly translated to all other languages.

Imagine you have mastered the perfect cherry pie for your annual work picnic but, upon taking it out of its airtight pie carrier, your heart sinks as you realize the crust has turned to mush thanks to the moisture from the filling. Sound familiar?

Android Nougat came with a lot of new features, including a futuristic and sleek circle animation. When this article was originally published, it was rumored that the circular design would be used as the new boot animation in Android 7.0—but as it turns out, you'll only see this screen while you're installing a firmware upgrade or working with ADB.

Ever since iOS 8, you could add widgets on your iPhone using the "Edit" menu on the Today view page, but there's an easier and faster way to get widgets set up for viewing via a right swipe on the lock screen, a swipe right from the first home screen page, and a swipe down from center top everywhere else.

Greetings fellow students! I'm currently reading a book called "Violent Python: A Cookbook for Hackers, Forensic Analysts, Penetration Testers and Security Engineers"

Many "quick and easy" donut recipes involve a donut pan and an oven, but those are basically just mini cakes shaped like donuts. Chances are, if you're in the mood for a donut, you aren't looking for a cake "donut" recipe—you want the real thing—a donut shop donut, fresh out of the fryer and topped with sugar or glazed to perfection.

It's a given that if you're driving, you or someone you know has Waze as a go-to on their smartphone. The Google-owned crowdsourced navigation app is one of the best for avoiding traffic, roadblocks, and even cops.
Hello everyone! This is my first attempt at a tutorial here. There are a couple great assembly tutorials here, and I wanted to toss my coin in the fountain.

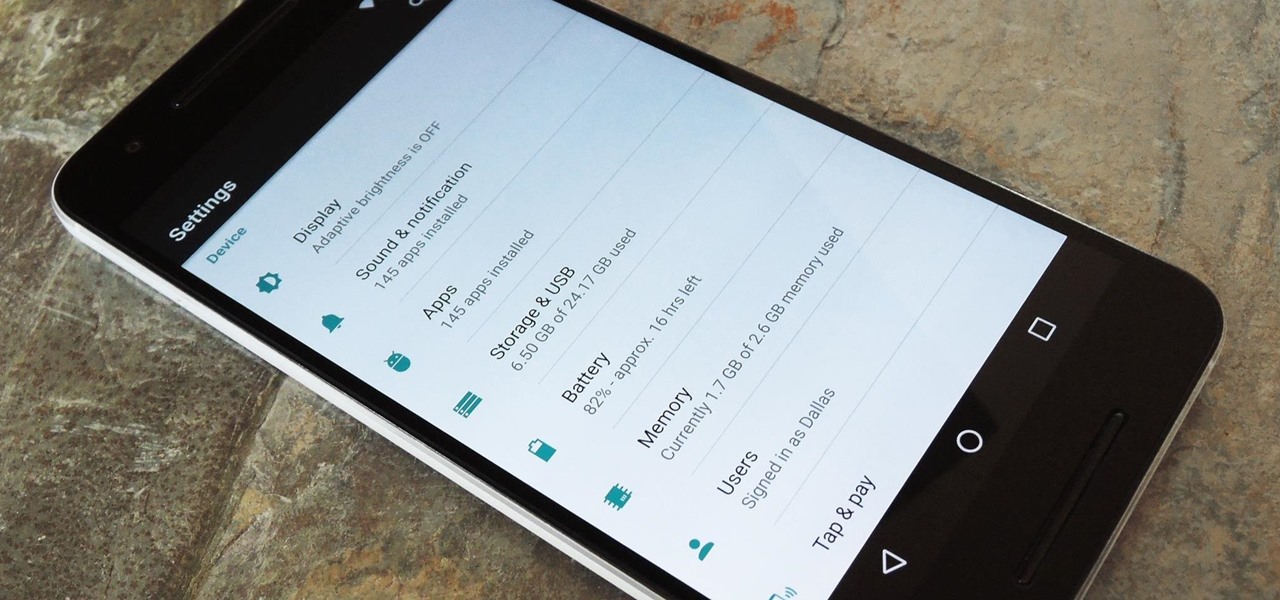
When Android N is officially released sometime later this year, it will bring a lot of cool new features along with it. We've already had the chance to play around with some of these, thanks to a preview build available to Android beta testers, and one change that we like in particular is a revamped Settings menu. Among other things, each settings entry now has subtext beneath it that shows relevant info at a glance.
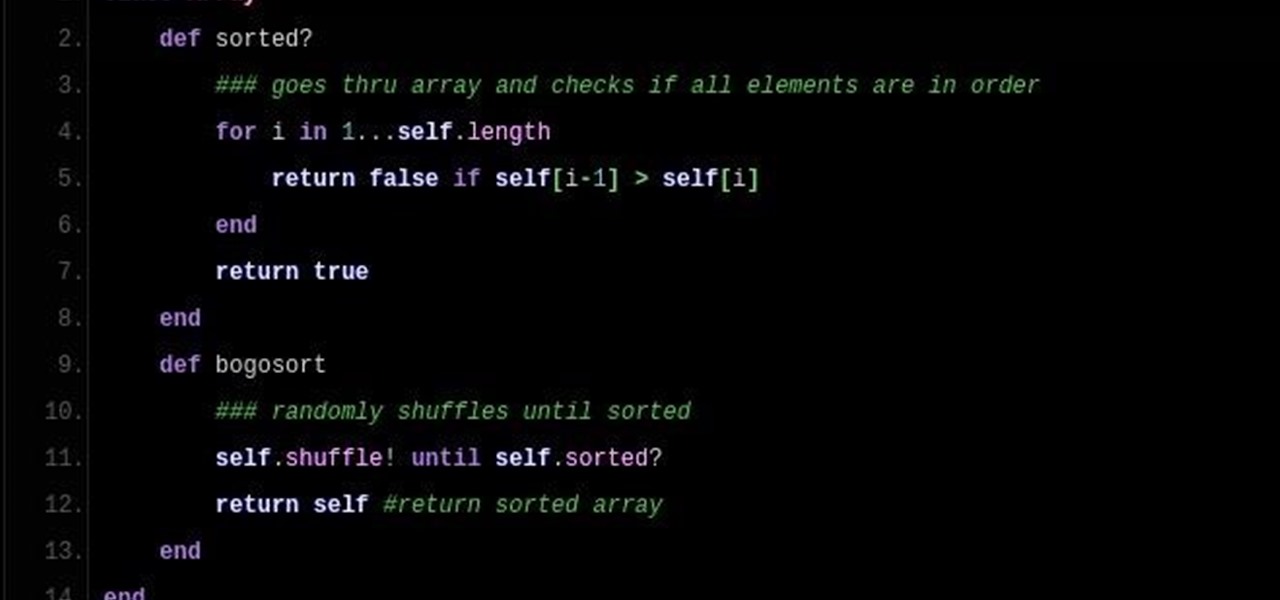
So DTM insisted I write up a little article on Bogo Sort. What Is Bogo Sort?

When we were kids, Saint Patrick's Day was a green-hued holiday that promised green eggs in the morning and green mashed potatoes in the evening... along with some traditional corned beef and cabbage, of course.

A crick is a sudden, spasmodic pain and stiffness in the neck caused by tight muscles that can absolutely ruin your entire day. It can last for more than one day and can be triggered by the smallest movement of the neck, such as a simple pandiculation, aka a yawn-stretch. Although you can't always prevent them, there are many natural ways to lessen a painful stiff feeling in the neck.

Welcome back! In our last training session we covered classes and how OOP can make programming/scripting easier. Today we'll be taking a breather and covering something fairly simple, bitwise operators.

Right, So i've been asking alot of questions here on Null-Byte and everyone has been really helpful to me.

This is not essentially the next part in the series, but an expansion of previous part about why should you not use cryptocurrencies.

This tutorial was written with Windows 7 in mind, but the principle applies to all versions starting from 7.

Hello aspiring hackers, It's been a while since I wrote a tutorial, so I figured I might just share one of the tools that I have created to help the community grow.

Hello again, readers! In our previous crypter tutorial, we looked at how we could obfuscate our malware (or any program) by using a simple one-byte XOR key. In this quick tutorial, we will be looking at how a simple little tweak can create a better means of obfuscation. Let's get right into it!

Welcome to a tutorial on crypting technology. In this article, we will be discussing types of crypters, how they work and why they work. After defining these, we will then make our own basic crypter using the function I gave to you as a task to complete by yourself in the previous tutorial.

Hello there Nullbyte users! This will be my first article here.

Welcome back, my greenhorn hackers! Over the years, I have written many articles here on Null Byte chronicling the many the hacks of the NSA, including the recent hack of the Juniper Networks VPN. (By the way, my speculation in that article has proven to be correct. The NSA did embed a backdoor on those devices.)

Starting in Android 4.3, Google added some code to AOSP that tagged your internet traffic when you were running a mobile hotspot, which made it incredibly easy for carriers to block tethering if you didn't have it included in your plan. But as of Android 6.0, this "tether_dun_required" tag has been removed, which means you no longer have to edit a database file to get tethering up and running.

Even those of us most comfortable in the kitchen can be daunted by the idea of cooking for a whole houseful of people. Whether you have a large, well-equipped kitchen or a small one with just the essentials, it can prove to be quite a task to prepare food for a dozen or so people. It takes a certain type of recipe that allows for mass production, in respects to both technique and ingredients. And what I've provided below includes several recipes that you might normally make for just a family ...

Welcome back to a tutorial on malware. We'll be discovering a method to beef up our little trooper. Without further ado, let's jump right in!

Hello partners, first of all I would like to thank all those who have sent me positive feedback about my posts, to say that I'm always willing to learn and teach. I'm also open to answer the appropriate questions.

OK, In my last Tutorial we made a Server for sending Instructions to a Client. This time we will build the Client. Fire up your favourite Python environment and get the Code here.