Getting an insider view of the goings-on at Magic Leap is hard to come by, but occasionally, the company lets one of its leaders offer a peek at what's happening at the famously secretive augmented reality startup. One of those opportunities came up a few days ago when Magic Leap's chief futurist and science fiction novelist, Neal Stephenson, sat for an extended interview at the MIT Media Lab.

Ever since Google CEO Sundar Pichai took the helms of the world's most valuable brand, he has made it his mission to bring smartphones to lower-income communities. Born in India, Mr. Pichai has created several programs to address the needs of the Indian market, particularly the lower income families.

In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greeting card being delivered to our intended target.

Dating websites allow you to see a person in a very intimate context, framing their successes and accomplishments in life to an important audience. The information contained in these profiles often can't be found elsewhere, offering a unique look into the personal life of the user.
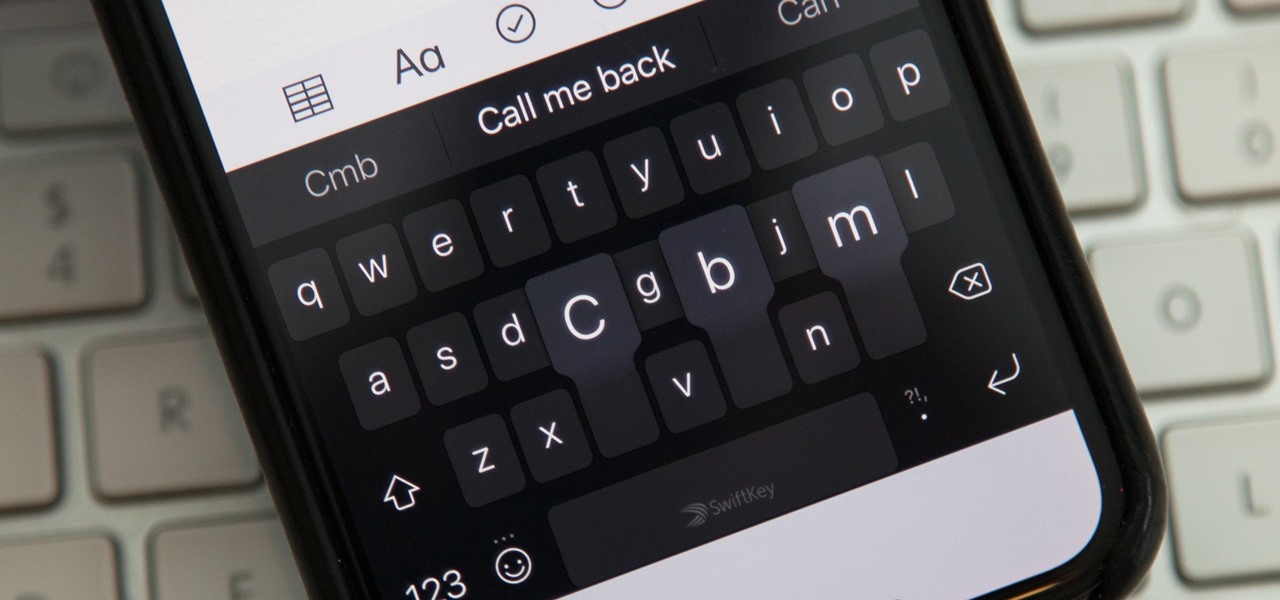
While you're probably already used to the keyboard on your iPhone, you'll likely never be able to type on it as fast as you can on a computer keyboard. But that doesn't mean you can't get any faster at typing on your iPhone. By using keyboard shortcuts to auto-populate commonly used phrases, email addresses, and other big-character items, you can drastically speed up your virtual keyboard skills.
Over the years, Nova Launcher has widened its audience. No longer is it simply a tool to return your home screen to a more stock look. With Nova, you gain customization tweaks and functionality unavailable with the stock launcher. One example of this is all of the cool stuff you can do to organize your app drawer.

Nova Launcher is one of the most popular apps on the Play Store thanks to its rich features and fluid navigation. But one downside that comes with this abundance of features is that much of Nova's functionality is lost on the masses. Fortunately, I've used Nova for several years and learned a few tricks along the way.

Most of us have never put much thought into this, but the question needs to be asked — what exactly happens to all of our online accounts when we die? No, the internet won't just know and delete accounts for you, so you need to plan for life's one guarantee. Because without a plan, things become a lot harder to sort out.

Google's launchers are some of the most polished home screen apps out there, but they lack the ability to customize. With the old Google Now Launcher, we had Xposed GEL Settings to add options for tweaking the layout, but that project was abandoned when the Pixel Launcher came out. Now, a new root mod will give us some key customization settings for Google's latest launcher.

With so much money on the line, it's no surprise that cryptocurrency exchanges are prime targets for cybercriminals. Because of this, the importance of keeping your personal account as secure as possible cannot be overstated. Binance is one step ahead in this regard, as it requires you to enable two-factor authentication to keep your bitcoins and alt-coins safe.

It's been nearly two months since Samsung kicked off the official Galaxy S8 beta program for Android Oreo. The Korean manufacturer recently announced that the beta is ending on January 15, so it's time to move on to the official build. Today, an official (non-beta) build of Oreo for the S8 has leaked.

Whether you're a veteran augmented reality developer looking for a quick access point to add a new platform to your arsenal or just getting started with your first AR head-mounted display, get ready to start developing for the Meta 2.

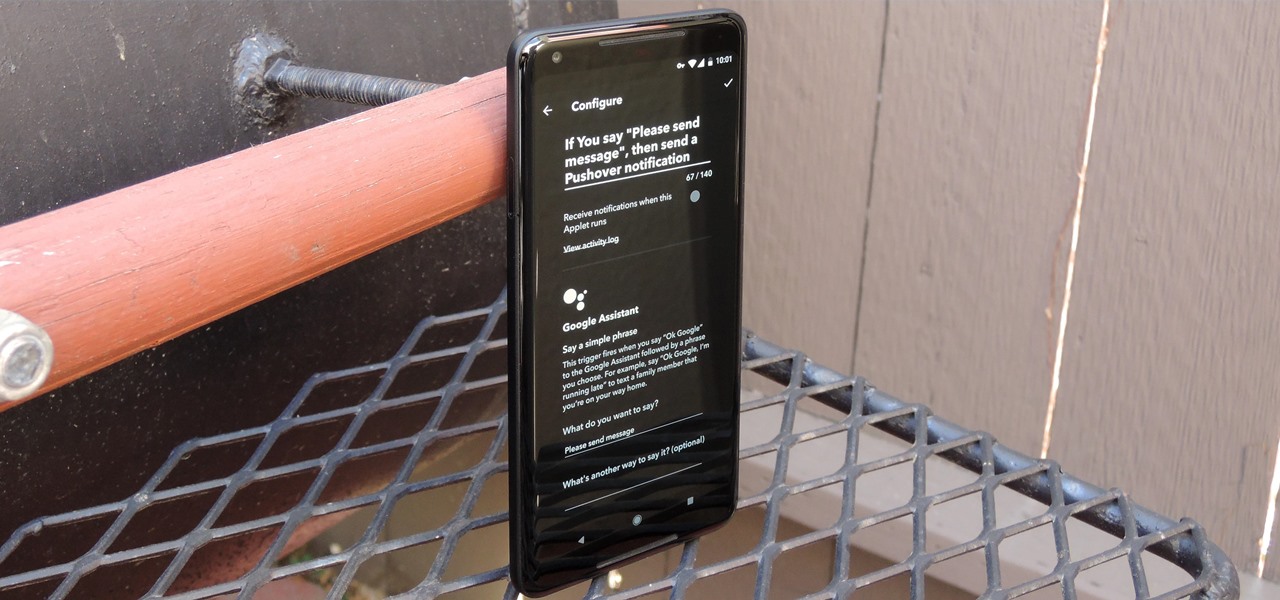
IFTTT is a fantastic tool that lets you trigger actions on your smartphone that normally require more advanced hacking. With the help of its friendly user interface, turning your phone into a more personal device has never been easier. However, the app has some more intricate options under the surface, making advanced implementations of applets difficult for beginners.

One of the biggest gripes we always hear about is the changes OEMs make to Android's notification shade. Icon styling and home screen layouts can be fixed with custom launchers like Nova and Action, but we're stuck with the tacky Quick Settings theme our phones came with. Today, we no longer have to envy Pixel 2 owners, as a new app will give you that clean stock Android look on any phone.

The year is 2018. You just received your own Magic Leap One: Creator Edition. What now? Rewinding back to today, we know of one specific app that will be available for Magic Leap's device, along with two others that could be tagged as highly likely. Paired with Magic Leap's own experiments and demonstrations, we can get a sense of what the playground for this new toy will offer.

Hackers can be notoriously difficult to buy gifts for, so we've curated a list of the top 20 most popular items Null Byte readers are buying during their ethical-hacking studies. Whether you're buying a gift for a friend or have been dying to share this list with someone shopping for you, we've got you covered with our 2017 selection of hacker holiday gifts — just in time for Christmas.

Google Trends says that "unicorn" costumes are among the Top 5 searches for 2017, holding steady onto the no. 4 spot, trailing only Wonder Woman, Harley Quinn, and clowns. Seeing as how this year, unicorns made the full leap back into our lives, its popularity when it comes to Halloween costumes is not surprising.

In our previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when an MS Word document is opened. Because Microsoft built DDE into all of its Office products as a way to transfer data one time or continuously between applications, we can do the same thing in Excel to create a spreadsheet that runs malicious code when opened. The best part is, it will do so without requiring macros to be enabled.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

While it's easy enough to ask websites not to track your browsing activity in Safari, they do not have to honor your request. Plus, some of the third-party content providers that websites use can actually invasively track you across other websites. Thankfully, iOS 11 includes a way to minimize companies from tracking you across the web on your iPhone.

Bluetooth Low Energy (BLE) is the de facto wireless protocol choice by many wearables developers, and much of the emerging internet of things (IoT) market. Thanks to it's near ubiquity in modern smartphones, tablets, and computers, BLE represents a large and frequently insecure attack surface. This surface can now be mapped with the use of Blue Hydra.

Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

Virtual private networks, or VPNs, are popular for helping you stay anonymous online by changing your IP address, encrypting traffic, and hiding your location. However, common IoT devices, media players, and smart TVs are hard to connect to a VPN, but we have a solution: Turn a Raspberry Pi into a router running through PIA VPN, which will ensure every connected device gets the VPN treatment.

Every time you make a call or send a text, you're giving the recipient your phone number. This can be quite the security vulnerability, opening yourself up to scammers, spammers, and the feds. In this how-to, we'll look at what a burner phone is, why you might want one, and how to get started using a free second phone number on your regular smartphone.

When Apple announced their ARKit platform in June, they immediately staked the claim to the largest augmented reality hardware platform, with millions of iPhones and iPads compatible with iOS 11 becoming AR devices this fall.

One of the least important but most noticeable changes in any iOS update is the look of home screen icons. In the new iOS 11, there aren't any drastic icon differences compared to iOS 10, but there's definitely a few design modifications for some of the main stock apps, such as Maps and the App Store.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

The incidence of tuberculosis (TB) is dropping in the US, but the World Health Organization (WHO) considers it to be epidemic in the rest of the world — there were over 10 million new cases in 2016.

A recent study offers information that might help combat a deadly virus that affects an estimated 300,000 people each year in West Africa.

Rising on the world stage, dengue fever is transmitted by mosquitoes — and apparently air travel too.

Staphylococcus aureus is a widespread bacteria — about a third of us have it on our body right now — usually in our nose or on our skin. And it probably isn't causing an infection. But, about 1% of people who have Staphylococcus aureus present have a type that is resistant to the antibiotic methicillin.

Casey Hudson, the one-time project director for games like Star Wars: The Knights of the Old Republic and the original Mass Effect trilogy, has announced his return to his former home, Bioware as the General Manager. Of course, that also means he is leaving his role at Microsoft Studios as Creative Director, where he was reportedly working on both Xbox One and HoloLens projects.

Nvidia's decades-long development of graphics processor units (GPU) for PCs has given it a major leg up in the driverless space.

Nvidia has emerged as the indisputable leader in chips for Level 3 and even more advanced driverless applications, catching some of the world's largest semiconductor makers and automotive suppliers by surprise.

Brace yourselves, because Siri has a trick up its sleeve that iPhone users have wanted for some time. Yep, that's right, I'm talking about the ability to use Siri without having to talk out loud for the whole world to hear. It's great for privacy, Siri-ing on the down-low when you're not supposed to, or ... you know ... if you have a speech disorder.

A vulnerability in the design of LiDAR components in driverless cars is far worse than anything we've seen yet outside of the CAN bus sphere — with a potentially deadly consequence if exploited.

It's not always easy to get to the root of an infection outbreak. Epidemiologists study infected people, contacts, and carefully examine where the infections happened and when. In the case of a 2012 outbreak of pertussis — whooping cough — in Oregon, scientists just published an analysis of how vaccination status affected when a child became infected during the outbreak.

Facebook is testing a new feature in India. One that could help you protect your profile photos from being used on sites without your permission.

Tesla hopes high-level personnel changes will help it gain an edge in neural network knowhow for its models' self-drive features, following the replacement of its Autopilot chief and the appointment of a recent Stanford grad to head its AI and Autopilot vision research.

Who would have thought that musical.ly would be the first social media app with a highly successful original show?