With over a billion monthly active users, it seems that Facebook is nowhere close to being dethroned as the most popular social media service in the world (sorry, Ello). While their stats may be impressive, it doesn't mean that Facebook is as good as it can be.

Deciding what to remove from your iPhone in order to free up space isn't the easiest thing in the world. You've got to decide which apps, videos, and photos are worth keeping, even though in a perfect world, you couldn't have to part with any of them.

No more carrying around heavy laptops and thousands of Linux Live CDs and USBs to always be ready for pentesting on the fly!

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.

Sitting in a cubicle and never seeing sunlight during the workday is unpleasant to even think about—and sitting in a flourescent-light cube can have terrible effects on both our work performance and overall attitude. Yet there are ways to counteract the effects of cubicle sitting, even if you can't sit in a sunny office or work from home.

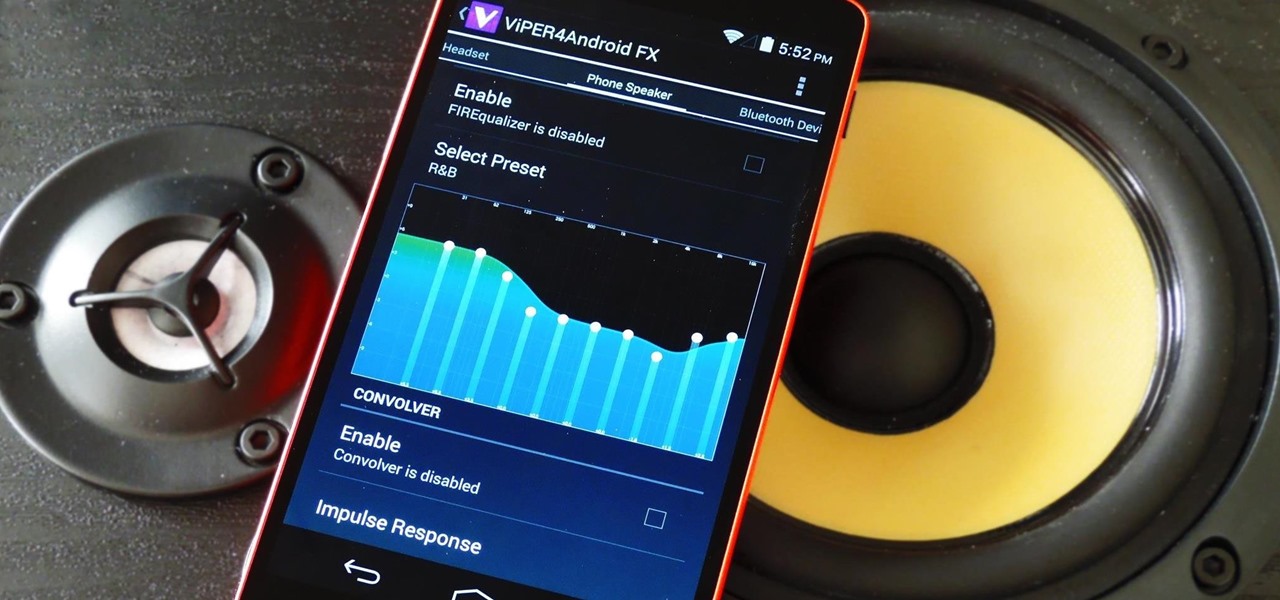
When it comes to getting your computer and smartphone to work well together, there's no service more robust and capable than AirDroid. For years, it's been the go-to tool for users looking to transfer files between their devices or access contact lists and call logs from their computer.

Welcome back, my novice hackers! In my series on cracking passwords, I began by showing off some basic password-cracking principles; developed an efficient password-cracking strategy; demonstrated how to use Hashcat, one of the most powerful password-cracking programs; and showed how to create a custom wordlist using Crunch. In this tutorial, I will show you how to create a custom wordlist based upon the industry or business of the targets using CeWL.

One of the more talked-about features of Google's new flagship device is the fact that all of the data on the Nexus 6 is encrypted by default. At face value, this certainly seems like an added bonus for the 6-inch phablet, especially in this day and age with growing security concerns abound. It's definitely something that the FBI is none too pleased about.

Before Apple jumped into the phablet game with their iPhone 6 Plus, there was the Samsung Galaxy Note series. Initially knocked for their size, the Notes slowly but surely gained popularity, thanks to powerful hardware, incredible displays, extensive features, great battery life, and a surprisingly-useful stylus.

Did you know Kali 1.0.8? You probably did, and you probably know about the EFI boot option that has been added.

If you've ever noticed that the stock launcher on an Android device seems to just feel faster than any third-party home screen replacement app, this is not a placebo effect. Most manufacturers, Samsung included, force their stock launchers to reside permanently in your phone's memory, thus reducing the risk of redraws.

Coffee! It's so amazing that J.S. Bach wrote a comic opera about caffeine addiction. Meanwhile, more than half of Americans 18 years or older start their day with a cup of the hot stuff. Most of us take coffee for granted, but it's a bean that can surprise you. Read on to understand more about coffee and how to take advantage of all that it offers.

Many Android games use large, storage-heavy OBB files to store supplemental data. Generally, games with high-end graphics download these extra files when you install them from the Google Play Store.

Third-party keyboards have been available for iPhone ever since iOS 8, but which ones are worth checking out? There have been many options over the years, and if you want keyboard features like swipe-typing and themes, you're going to have to put Apple's stock QuickType keyboard on the backburner and try out these top hits.

Keeping data private is vital in the days of smartphones and the free-floating information they carry. Justin wrote a guide on many of the deeply hidden and sometimes concerning privacy settings in iOS 7. Now we're back to cover some of the new (and old) privacy settings in iOS 8 that you need to address right now.

The Xposed Framework offers many great customization options for your Galaxy S5. S Health, with its ability to read your heart rate through a built-in monitor, is one of the main selling points of the GS5. Trouble is, the two don't seem to play nice together.

Voicemails are like chores for me. I have to listen to them, but never really feel like doing it. When I finally do, most of them get deleted right away, but every so often they'll be one I save and listen to over and over again, whether it's a cute birthday wish from grandma or a hilarious joke from my friend.

Okay, it's true: even the highest quality instant coffee is never going to replace really good fresh beans (and properly cleaning your coffee maker) when it comes to creating a great cup of joe. However, instant coffee does have all kinds of uses in the kitchen, as the smart folks over at Reddit observed.

Arcades have long faded away from popularity, but their legacy is being kept alive thanks to emulators and the avid fans who grew up loading quarters into all of those coin-op games. Although nothing beats an actual arcade environment, my favorite emulator from the early 2000s has found a new home on Android, and with it a second life.

If you've ever owned an HTC device or anything in the Nexus line, odds are, you have typed the word "fastboot" into your command line at one time or another. That said, odds are, you have only just barely scratched the surface of what this handy little Android tool can do. Let's take a deeper look.

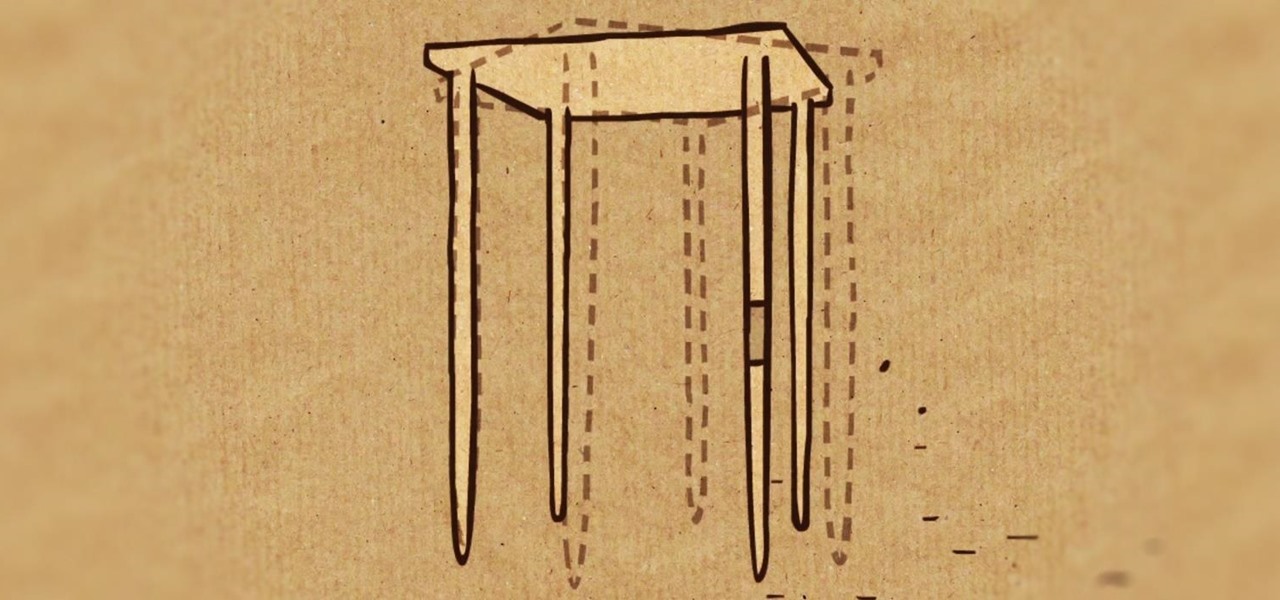
As sure as death and taxes, sitting at a wobbly table at one time or another is inescapable. With your weight on it, the table shifts from one end to the other, lifting one leg in the air and then the other; a parade of seesaws, especially if you have someone sitting on the other end.

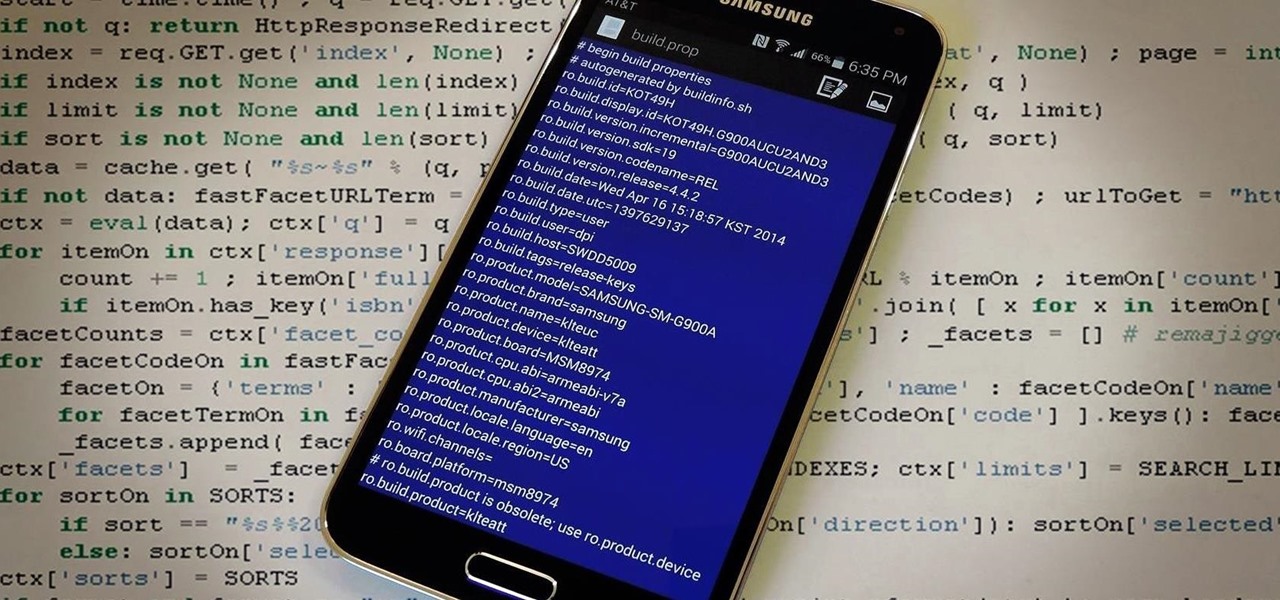
The build.prop file in an Android device is home to many system-level values and settings. Everything from screen density to video recording quality is covered in this file, and people have been editing these entries to get new functionality and better performance since Android has existed.

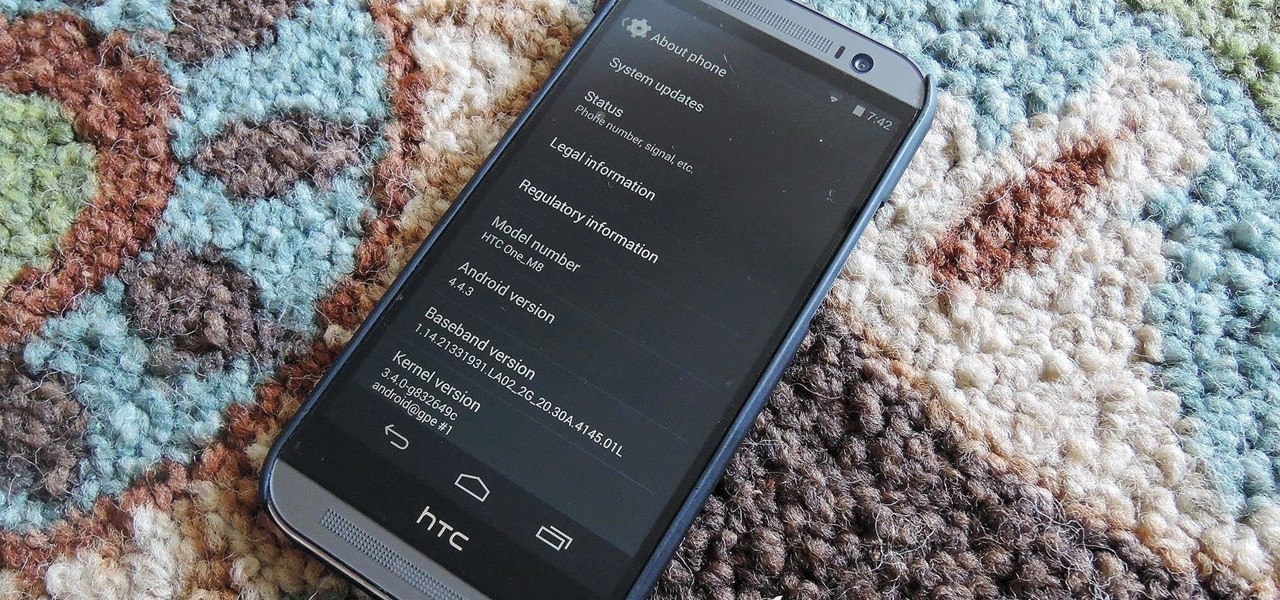
HTC has made it their mission to get updates out to its devices as quickly as possible, with new builds slated for release 90-days after Google finalizes a build—this is dubbed HTC Advantage.

Many home cooks were taught never to press down on a burger as it cooks since that would ruin your all-beef patty by getting it to release the juices it needs to stay tender and moist.

Contrary to popular belief, taking someone's mind off their sadness and telling them to "cheer up" doesn't do much good. Misery loves company, and while it may be a tiresome cliché, there's actually some science behind it.

Welcome back, my tenderfoot hackers! In continuing my series on digital forensics using Kali, I want to introduce you to two complementary tools, both built right into Kali Linux. These are Brian Carrier's tools Autopsy and Sleuth Kit.

Do you take your notes on a word processor while browsing the web? Well, stop. There's an easier, less RAM hungry way to take notes by turning the tab of your web browser into a notepad. Whether it's an email address, a line of code, a new how-to, or an idea you don't want to lose, you can easily jot it down without slowing down.

When the Samsung Galaxy S5 launched a few months ago, I was pretty envious of the new UI elements Samsung included on it, as I'm sure you were. The flatter interface provided for a more polished and less cartoony feel, bringing the device more in line with Google's design elements.

Airports are terrible germ-infested purgatories where people sit around for hours without Wi-Fi while they anxiously await to get wherever they really want to go. Unfortunately, there isn't much we can do about waiting, but this little Wi-Fi hack could help make the waiting a little less boring.

Welcome back, my novice hackers! In a recent tutorial, I showed you how to use shikata_ga_nai to change the signature of a payload to evade detection by security devices (firewalls, IDS, etc.) and AV software.

Ask a thousand Nexus owners why they chose their device over an iPhone, and after getting an earful of Apple hate, you will likely hear a clear pattern in their responses, namely, the freedom to customize their phones.

The Nexus line of devices consistently offer the most bang for your buck. It's why many of us purchased a Nexus 5—at a $350 entry price, it's half the cost of any other phone with similar specs.

The beauty of having a Google Play Edition HTC One is the ability to get as close to stock Android as possible while still getting some extra non-Google, proprietary HTC features. The newest version of Android, 4.4.3, has just hit the Nexus and Google Play Edition line of phones, but if you are rooted with a custom recovery, you will not be able to apply the OTA.

Look away from this screen and try to remember the sound of your childhood hero's voice. Did you do it? Do it again, and this time pay attention to your eyes.

The late, great writer Laurie Colwin once wrote that if she were allowed to have only one fruit in her kitchen, she would always choose lemons (or limes, since they can often be used interchangeably).

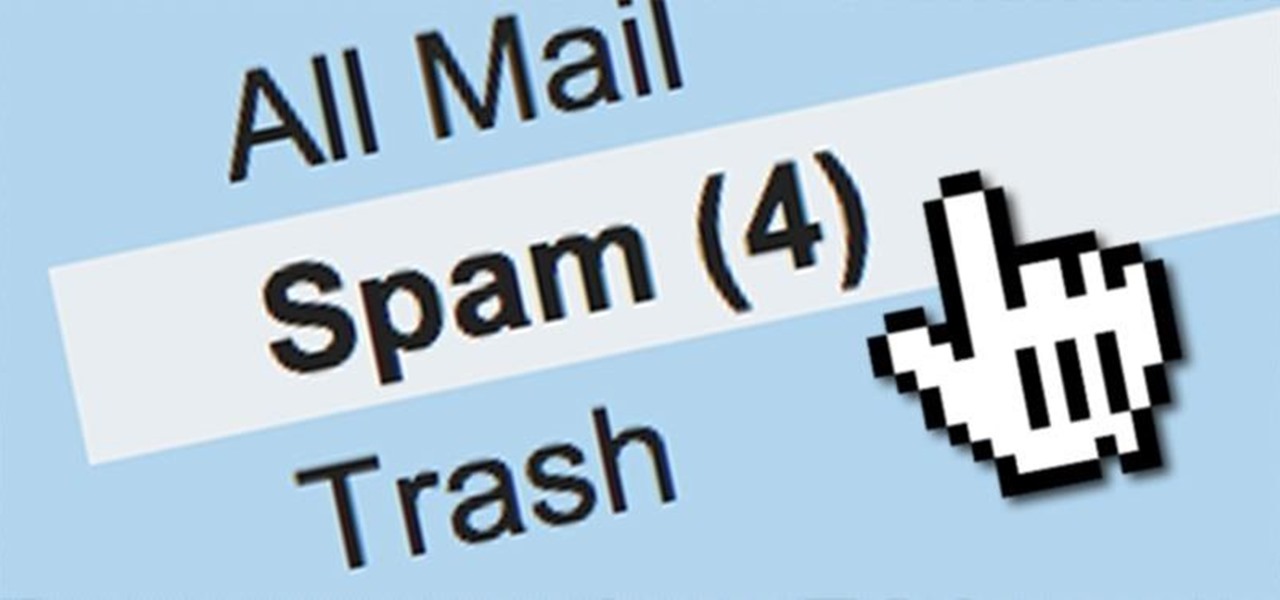
I rarely receive spam mail, but every now and then I’ll get an email from Cat Fancy Magazine. I’ve never read an issue of Cat Fancy Magazine or been to their website. Actually, I’m allergic to cats. So how did they manage to get my information?

Welcome back, my hacker novitiates! Recently, I demonstrated a hack where you could redirect traffic intended for one site, such as bankofamerica.com, to your fake website. Of course, to really make this work, you would need to make a replica of the site you were spoofing, or better yet, you could simply simply make a copy of the original site and host it on your own server!

Welcome back, my greenhorn hackers! After the disaster that was Windows Vista and the limited and reluctant adoption of Windows 8 and 8.1, Windows 7 has become the de facto standard operating system on the desktop/client.

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

A well-executed jack-o'-lantern can be pretty damn impressive, but some of us lack the carving skills necessary to pull it off and end up disappointed. Sometimes you just don't want to put in all the time required to cut open a pumpkin, gut it, and chisel an elaborate face or cool design into it.