
How To: Pull the April Fool's Day Shower Head Prank
For the dedicated prankster, April Fool's Day is no joke. Nothing will stop them from coming up with the cleverest, most elaborate prank the world has ever seen. Or at least—their victim.


For the dedicated prankster, April Fool's Day is no joke. Nothing will stop them from coming up with the cleverest, most elaborate prank the world has ever seen. Or at least—their victim.
(Series designed to help explore whether your ideal employment ideas should be formalized into a business venture or as an employee or volunteer value added problem solver).

There are only few steps to find the area of the triangle in a simple method. First you consider a triangle, and to find the area in a simple manner just add the triangle of same properties and side lengths as same as the first one and attach to it. Then we know the formula to calculate the area of the square. Then find area of the square by side*side. Then you will get the area of the square, now divide the area by two, as we add another triangle. Then the area of the triangle will be obtain...
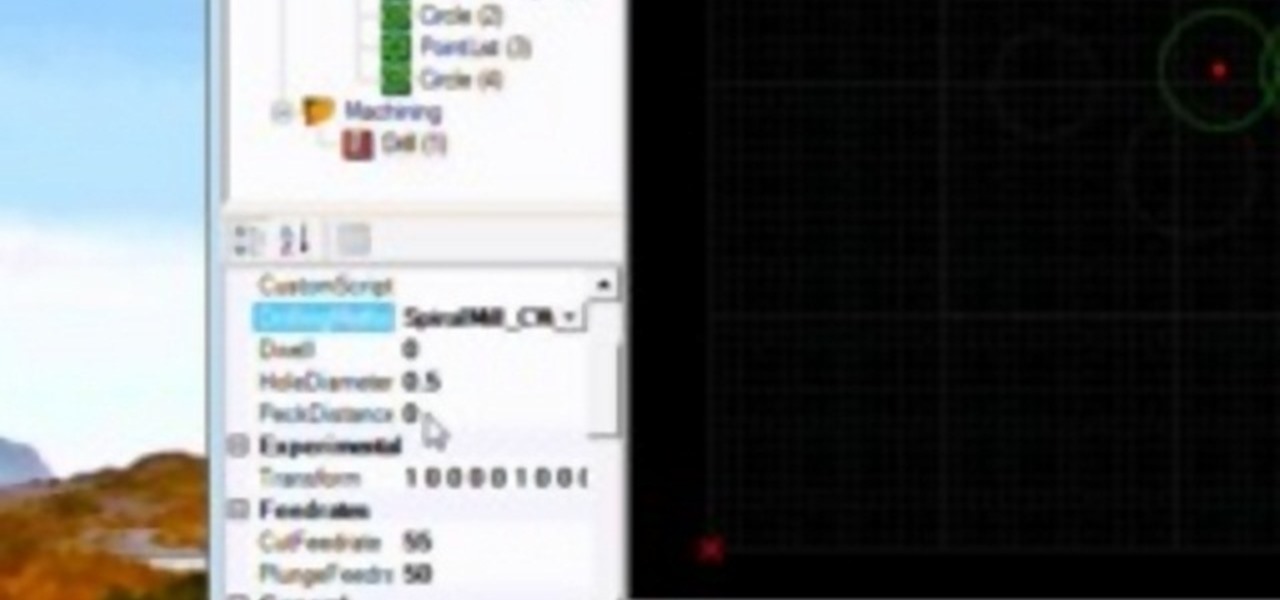
A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

Apple's successor to the iPhone X is a beautifully made smartphone with much of the same characteristics, including a 5.8-inch OLED screen, two storage choices, and Face ID. But many features set the iPhone XS apart from its predecessor, as well as the other 2018 lineup of iPhones, making it a worthy choice to upgrade to if you're in the market for a new mobile device.

Mosaics are a cool type of art. You can use mosaics to liven up your home or garden and they are cheap and fun to make. Check out this video for tips and instructions for making mosaics.

Motion can be studied in different dimensions. Study of motion of a body in a straight line is called motion in one dimension. A falling body can be called as motion in one dimension. Things can also move sideways when they fall at the same time. This is also called as projectile motion and it is a study of motion in two dimensions. When studying projectile motion we can neglect one dimension of the motion and study the other dimension obtaining the results of motion in that dimension. If a b...

This video demonstrates how to plant garlic cloves with toilet paper rolls. Take some toilet paper rolls and cut them in half. Fill the halves with damp soil. Put one clove of garlic into each little half, leaving the new shoot poking out of the top. You can make potting soil with peat moss, black dirt and vermiculite. When it is time to plant the garlic, you should just put the whole carton into the ground. When you buy garlic for planting, look for the giant variety. When you are saving gar...

This how-to video is about how to reduce belly fat with the help of a better diet.
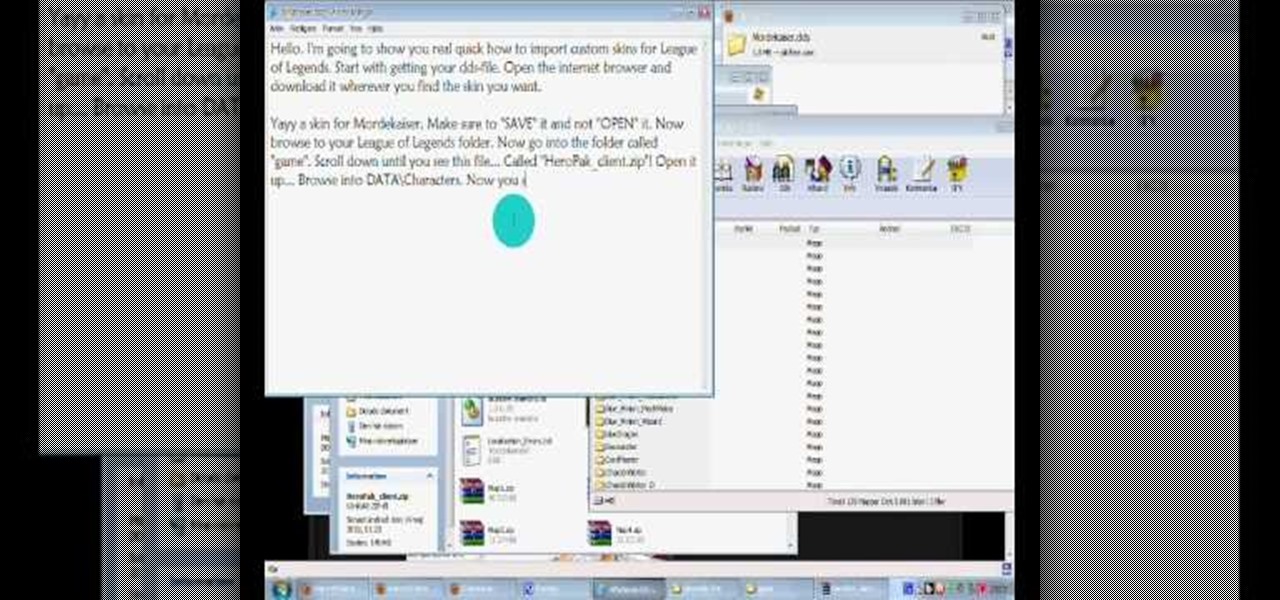
Give your League of Legends champion a new look! Alter the .dds files in the game directory so you can import custom skins. This video walks you through the process for obtaining and installing custom skins. Be aware that this will only change the way champions appear to you.

Farkle hacks, cheats, glitches. How to hack Farkle. Watch this video tutorial to learn how to cheat on Farkle (09/15/09).
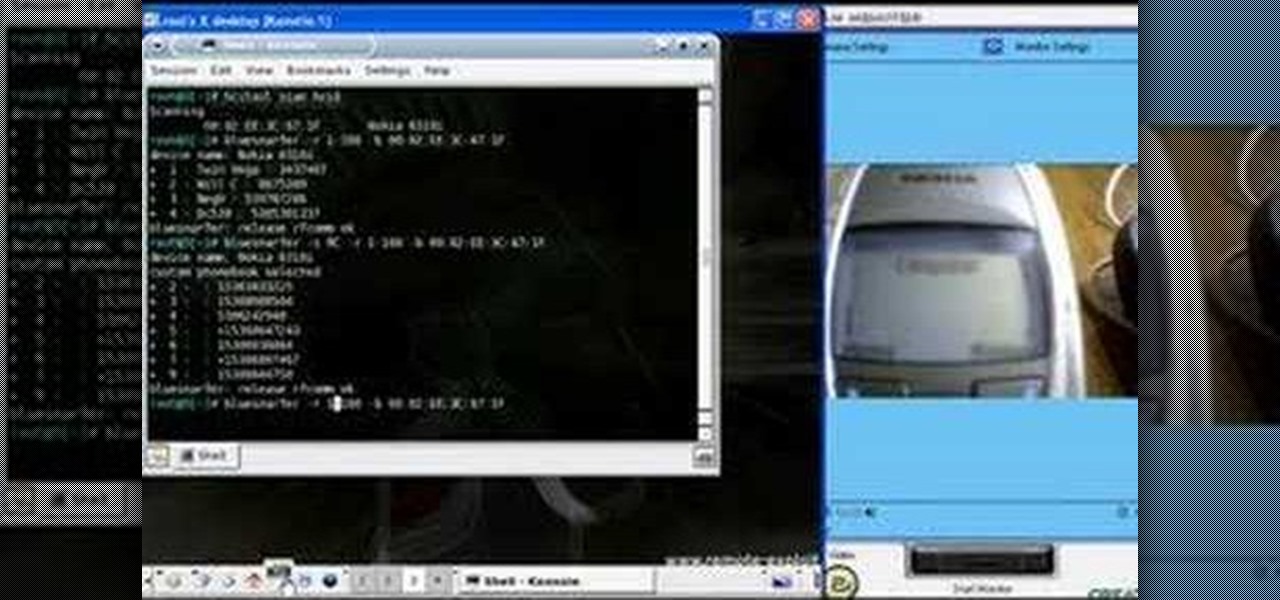
Check out this video tutorial to see how to bluesnarf a Nokia 6310i handset (cell phone). What is Bluesnarfing exactly?

Google, you have something that I want. You may think you have some idea of what you are in possession of, but you do not. In a few moments, it will be mine...and it can be yours, too, dear readers.
When compared to last year's model, the Pixel 4a has upgrades that go beyond the spec sheet. But since it's one generation old, 2019's Pixel 3a can be had for one hell of a discount right now, and it's still got two full years of software updates coming its way. So which one really is the better buy?

The native timer feature on your iPhone works well enough that you probably haven't even thought about installing a third-party timer. With just a few taps, you can get a countdown for any amount of time up to 24 hours (or one second shy of 24 hours, to be precise). But as fast as it can be to set a timer from the Clock app, there are even faster ways to start the countdown.

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.
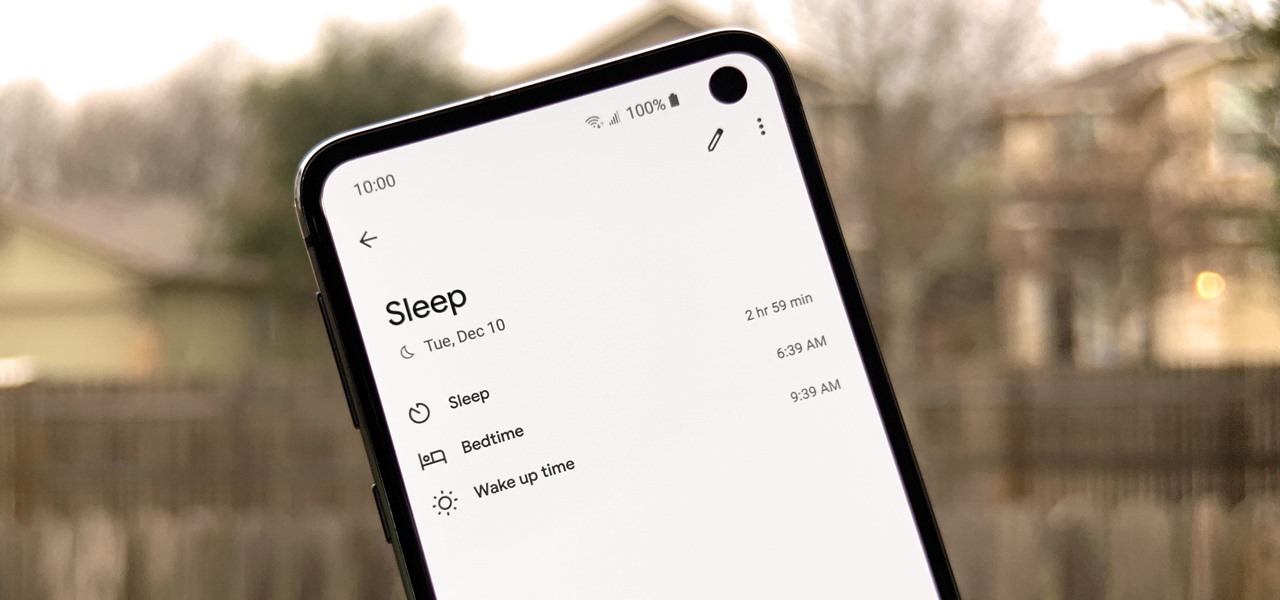
When trying to get fit, something that can easily be overlooked is your overall sleep quality. Your body needs sleep to recharge and it helps to maintain a healthy lifestyle, there's no denying it. Luckily, Google Fit can help you track your sleeping habits without having to jump through any hoops along the way.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

So you've managed to get a shell on the target, but you only have measly low-level privileges. Now what? Privilege escalation is a vast field and can be one of the most rewarding yet frustrating phases of an attack. We could go the manual route, but like always, Metasploit makes it easy to perform local privilege escalation and get root with its exploit suggester module.

Correctly identifying the underlying technologies that run on a website gives pentesters a considerable advantage when preparing an attack. Whether you're testing out the defenses of a large corporation or playing the latest CTF, figuring out what technologies a site uses is a crucial pen-tester skill.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

The recent Oculus conference in California revealed just a bit more about Facebook's secretive plans to compete in the augmented reality space with its own wearable devices.
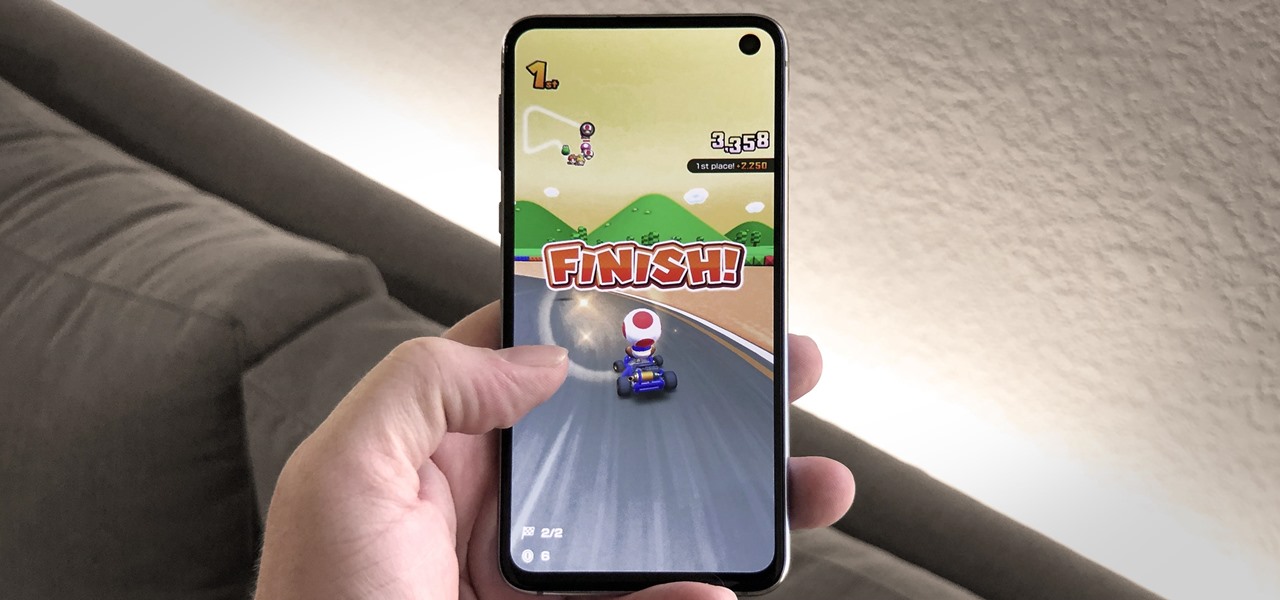
So you can't seem to win in Mario Kart Tour? Whether it's your first game in the Mario Kart series or not, Mario Kart Tour can be challenging, especially when you don't know the tracks. Instead of struggling your way through the cups, try out these five tips to get a leg up.
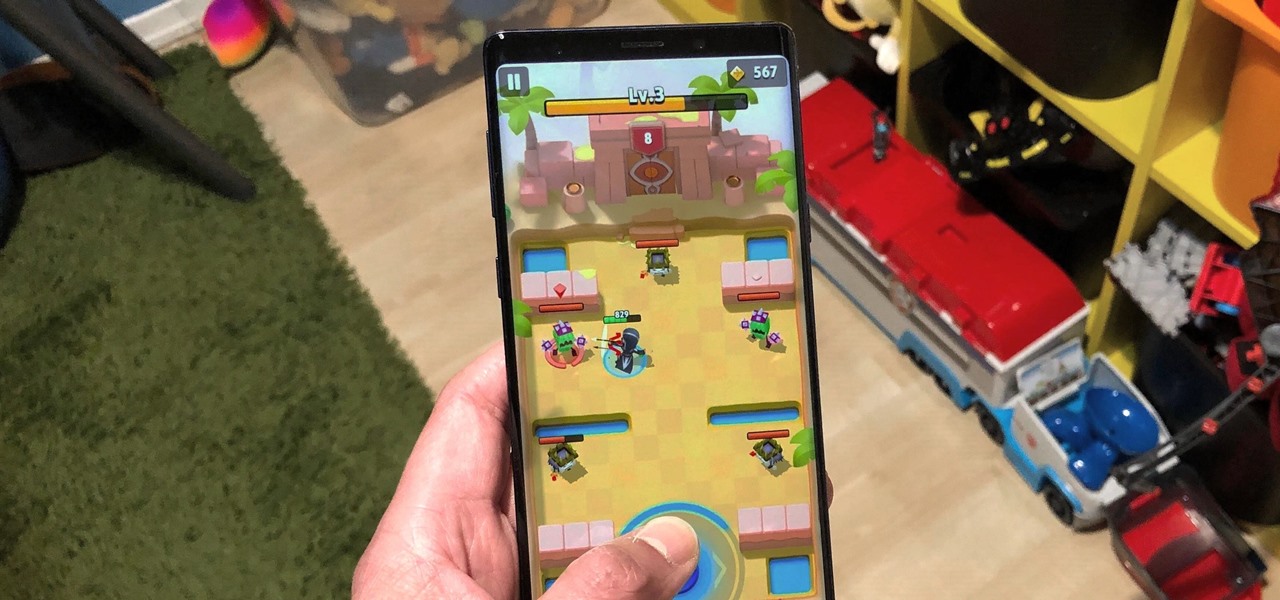
When it comes to shooting games, battle royale titles like PUBG and Fortnite have come to dominate the scene, leaving other sub-genres like top-down and third-person shooters living in the shadows. They're far from irrelevant, though, as evidenced by all the great games released just in 2019 alone.

They say home is where the heart is. So, the opportunity to view the inner sanctum of Magic Leap is like gaining access to what makes the company tick, just as the fruits of its labor make it into select AT&T stores.

In a way, Twitter is the town square of our era, where people can share and discuss ideas on a wide variety of topics. While the tech giant has its own app for Android, it's pretty bare-bones when it comes to features. This has paved the way for third-party clients that are rich with customization options.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.
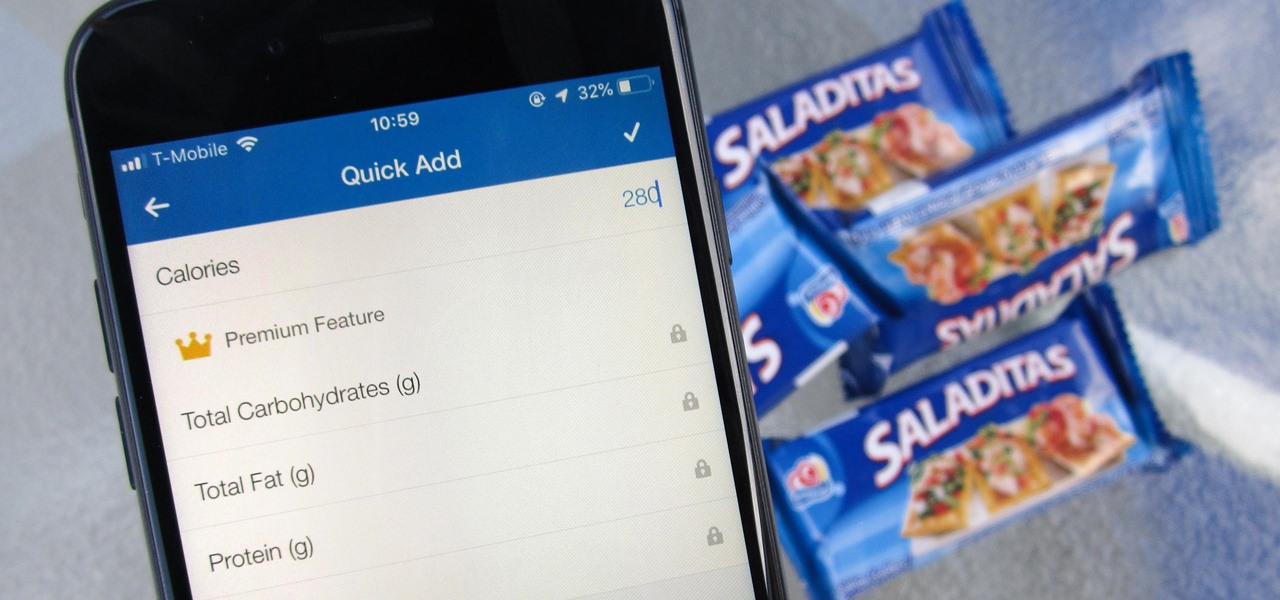
It's only normal to snack on a few french fries every once in a while when you're on a diet, but it's still important to hold yourself accountable, even when you cheat just a little bit. MyFitnessPal, for both Android and iOS devices, has a database of nutritional information to help keep track of the meals you eat, but it also has a way to add calories on the fly without digging for data.
Haptic feedback and vibration of our smartphones have come a long way in recent years. These features are much more premium now than they once were, but most users are still unable to adjust the intensity for notifications or phone calls. Most higher-end devices make less noise on surfaces than in the past, but adjusting these values can still come in handy even today.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.
When Google introduced the Pixel 3 on October 9th, one of new additions they briefly mentioned was the Titan M security chip. While they did talk about how it will improve overall security, they didn't expand on the number of changes it brings to the Pixel 3's security. Well, they finally shared more, and it's a pretty big deal.

There's more to recording calls than just protecting yourself against liability or an angry ex — oftentimes, this feature is the perfect tool to save momentous calls like breaking news of your recent engagement to loved ones. And with the prevalence of video calls, you can even capture memorable video chats such as your mom's first glimpse of your newborn on your mobile, courtesy of Skype.

The transcribing app can be an invaluable tool, especially if you're a student or are in a profession that relies on audio journals or interviews. These apps can convert important recordings like lectures and meetings into text for you to carefully read through to better comprehend.

Each year, Apple seems to design its devices to be more difficult for owners to repair themselves. So when an iPhone breaks, a trip to the Genius Bar or an Apple Authorized Service Provider is most likely necessary. But if you have an iPhone X that needs a new battery, a leaked video just spilled the beans on how to replace the battery precisely as Apple would.

When BlackBerry made the move to Android OS, they were aware of the limitations it presented. Unlike with BB10, they didn't create the operating system and would have to deal with the vulnerabilities already included. As a result, they added numerous security enhancements, and at the heart of this is DTEK.
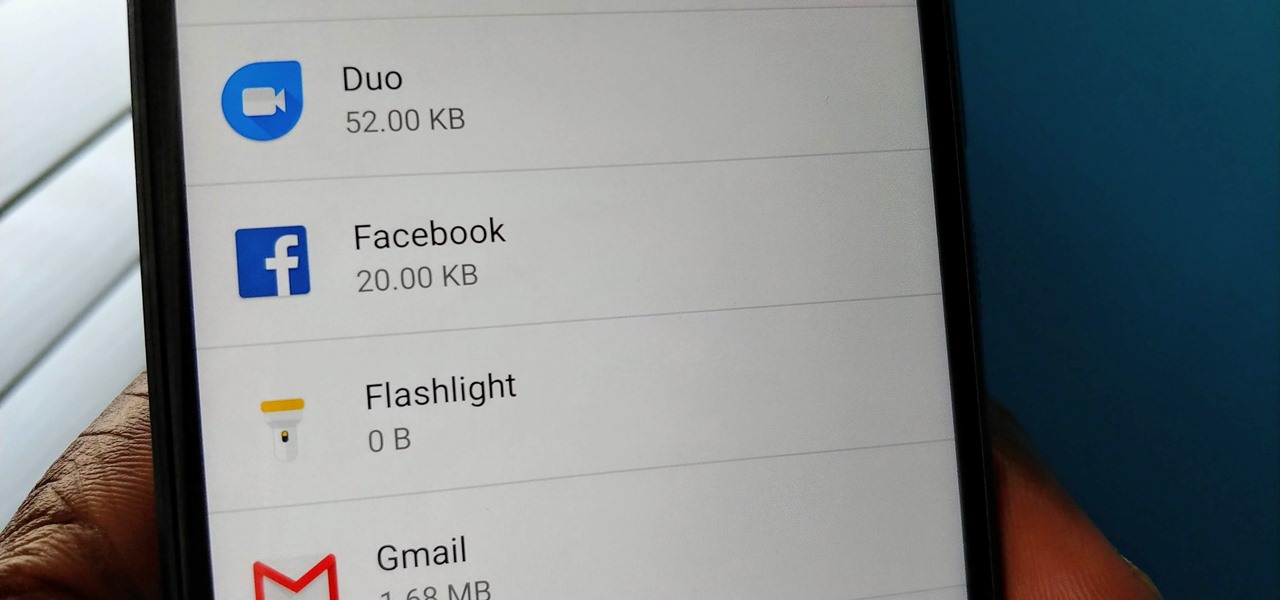
Despite years of user complaints, OEMs are still preinstalling third-party apps on brand new devices. Even in 2019, you'll still find plenty of phones with Facebook preinstalled. What's worse, it's installed as a system app, so it can't normally be uninstalled without root access. However, there are a few workarounds.

After backdooring a MacBook not protected by FileVault or using a fake PDF to gain remote access, an attacker may wish to upgrade their Netcat shell to something more fully featured. While a root shell allows attackers to remotely modify most files on the MacBook, Empire features some useful post-exploitation modules which make hacking Macs very easy.

A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials.

Apple has introduced a special edition iPhone 8 and 8 Plus to bring attention to the ongoing worldwide battle against AIDS. As the second iPhones to carry the (PRODUCT)RED name, these rare iPhones may quickly sell out when preorders open up on Tuesday, April 10, at 5:30 a.m. (PDT), so we'll go over some tips to help you secure a red iPhone before it's gone.

Deleted bank statements and private photos are still within an attacker's grasp, so don't think that emptying your recycling bin is enough to keep your files from coming back to life. It's possible for a hacker to recover compromising files and images from a backdoored computer completely without the victim's knowledge.