As much as I love eating weird foods, when it comes to my favorite food, there is only one simple choice: cheese. Since cheese is my favorite to eat, it should come as no surprise that it's one of my favorites to make as well.

Welcome back, my tenderfoot hackers! Have you ever wondered where the physical location of an IP address is? Maybe you want to know if that proxy server you are using is actually out of your local legal jurisdiction. Or, maybe you have the IP address of someone you are corresponding with and want to make certain they are where they say they are. Or, maybe you are a forensic investigator tracking down a suspect who wrote a threatening email or hacked someone's company.

After you have registered to this site,sign in then to start missions. Basic Missions

In this simple tutorial you will be shown step-by-step how to write local shellcode for use on 64-Bit Linux systems. Shellcode is simple code, usually written in assembly that is used as payload in exploits such as buffer overflow attacks. Payloads are the arrow head of an exploit: though the rest of the arrow is important for the delivery of the attack, the arrow head deals the killing blow. In reality, payloads are slightly less exciting yet far more interesting and intelligent than medieva...

Welcome back, my novice hackers! In this continuing series on Metasploit basics, let's next look at a module that many aspiring hackers find useful—autopwn.

As a lover of food, I'm often asked, “If you could only have one food the rest of your life, what would it be?” My answer is always the same: sourdough bread. (Okay, it's not always the same... I usually cheat and say sourdough, fancy cheese, and a good beer.) Admittedly, I'm biased by my own sentimentality. My mother is an expert bread baker, with a major in making sourdough. Her sourdough starter is older than I am, and in all honesty, she's made thousands of loaves, each better than the ne...

If you've ever wiped your computer without having a proper backup of your operating system, or just wanted to cause some havoc online, chances are you've had to rely on Linux to help you out, specifically the Ubuntu distro.

Valentine's Day can seem like Singles Awareness Day if you're newly broken up, but that's all the more reason to treat yourself on this pink-and-red consumerist holiday. Whether you're happily single or bitter and bitchy, there's definitely something on this list of Anti-Valentine's Day treats to fit your mood. Remember: cake is still cake!

With over a billion monthly active users, it seems that Facebook is nowhere close to being dethroned as the most popular social media service in the world (sorry, Ello). While their stats may be impressive, it doesn't mean that Facebook is as good as it can be.

Unlike wine, you can't re-cork or stopper leftover bubbly after you've opened it, but all is not lost even if you haven't managed to finish every last drop. You can use your leftover champagne to make light-as-air crêpes or pancakes, to create a detox face mask, to cook seafood and rice, or to make dips and salad dressings.

There's nothing more jarring than the sound of your morning alarm. Even hearing it on others' phones, hours after your own abrupt wakeup, can cause you to flinch in fear. Though we depend on that shrill sound to get up each morning, it's actually better to wake up naturally—so don't even think about hitting that snooze button.

Injustice: Gods Among Us is one of the most popular games to come out over the last couple of years. It was a hit on video game consoles, and it's got a solid 4.5 rating on both Google Play and the iOS App Store, with almost 2 million people rating the game combined.

There are hundreds of delicious ways to enjoy caramel, from chocolate confections to sticky caramel apples and carnival bags of caramel corn. Caramel might be the special sauce that makes every dessert taste better, but it's also surprisingly simple to make.

I'll admit it: I've spent many eight-hour workdays stuck at my desk, staring at my computer as my breaks slip past unnoticed. I frequently tell myself I'll take one in a few more minutes—but somehow, the entire day will pass and I won't have taken a single break.

There are a lot of music apps on my iPhone's home screen, and the reason I have so many is because I can't get all of the songs I want from just one service. I use Spotify to listen to new releases, SoundCloud for remixes and unreleased tracks, and YouTube for just about anything else that isn't available through the rest. If you're thinking that it's a pain in the ass to jump from app to app, you're right—but not anymore.

Welcome back, my novice hackers! In my series on cracking passwords, I began by showing off some basic password-cracking principles; developed an efficient password-cracking strategy; demonstrated how to use Hashcat, one of the most powerful password-cracking programs; and showed how to create a custom wordlist using Crunch. In this tutorial, I will show you how to create a custom wordlist based upon the industry or business of the targets using CeWL.

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.

Android 5.0 has a killer new feature that should make securing your device easier than ever. It's called Smart Lock, and it essentially lets you bypass your secure lock screen when you're in a "trusted environment." This means that if you're connected to a known Bluetooth device or near a pre-programmed NFC card, you don't have to bother entering your pattern, PIN, or password.

Many Android games use large, storage-heavy OBB files to store supplemental data. Generally, games with high-end graphics download these extra files when you install them from the Google Play Store.

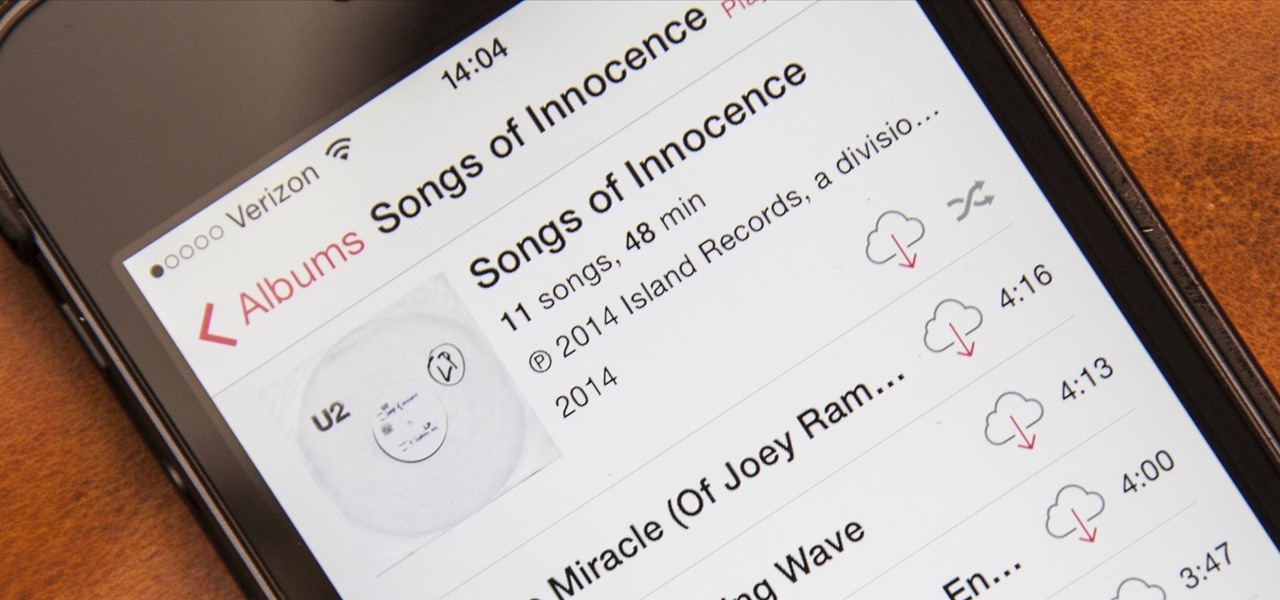
From my experiences, there are only two types of U2 people: those that love them and those that hate them. I'm the latter, so it's pretty damn annoying that Apple just added U2's new album, "Songs of Innocence," to my iCloud. If you find it creepy that U2 is appearing on your iPhone or in iTunes, don't worry—I've found a few ways to deal with it. UPDATE: How to Delete U2 Forever & Ever

Apple released the iOS 8 Gold Master build to developers shortly after their WWDC event ended on Sept. 9th, which is jam-packed with tons of new features for iPad, iPhone, and iPod touch. The public version comes out on Sept. 17th, but if you can't wait to test out iOS 8, you can get it right now.

Arcades have long faded away from popularity, but their legacy is being kept alive thanks to emulators and the avid fans who grew up loading quarters into all of those coin-op games. Although nothing beats an actual arcade environment, my favorite emulator from the early 2000s has found a new home on Android, and with it a second life.

One of the best features of Android is the fact that it's open-source, giving developers the ability to use it on pretty much any device they can think of, like on a Windows PC using Andy. That's what drove the creators behind the Android-x86 project to port over the mobile OS to any computer running an Intel processor.

Summer is the season to enjoy stone fruit: peaches, plums, nectarines, and apricots are all kissed by the sun and bursting with juicy flavor—which is all well and good when you're eating them as is.

If you're using iOS 10 or lower, there is no built-in way to record an iPad, iPhone, or iPod touch screen, and Apple doesn't allow any third-party apps to screen record either. If malicious, an app could theoretically continue recording even after you think it's off, allowing it to capture account and password information that you enter on your device. This changes in iOS 11, which introduces native screen recording, but what do you do if you're still running iOS 10 or lower?

With Safestrap bringing custom recovery functionality to the AT&T and Verizon Wireless variants of the Samsung Galaxy S5, it's high time we covered this process for all other versions of the GS5.

Butter can be even more delicious than it already is. While that may be a shocking claim, it's most definitely true. Many new cooks and even seasoned chefs don't realize this, but the few minutes it takes to do these things will pay you back exponentially when it comes to that buttery taste.

Transition animations are an essential element of any mobile operating system. They give the user a sense of what's happening on the screen, where the apps are coming from, and where they're going.

Security is a priority for many when they first set up their mobile devices. Nobody wants to have a stranger or nosey friend go through their phone and discover risqué photos or embarrassing text messages. These days, the closet is gone—everyone keeps their skeletons in their phones.

Contrary to popular belief, taking someone's mind off their sadness and telling them to "cheer up" doesn't do much good. Misery loves company, and while it may be a tiresome cliché, there's actually some science behind it.

In the Apple's iOS beta 3, we were introduced to a new iCloud Drive feature, an option to disable QuickType, time indicators for Recently Deleted pics, and a way to keep "self-destructing" media.

Welcome back, my tenderfoot hackers! In continuing my series on digital forensics using Kali, I want to introduce you to two complementary tools, both built right into Kali Linux. These are Brian Carrier's tools Autopsy and Sleuth Kit.

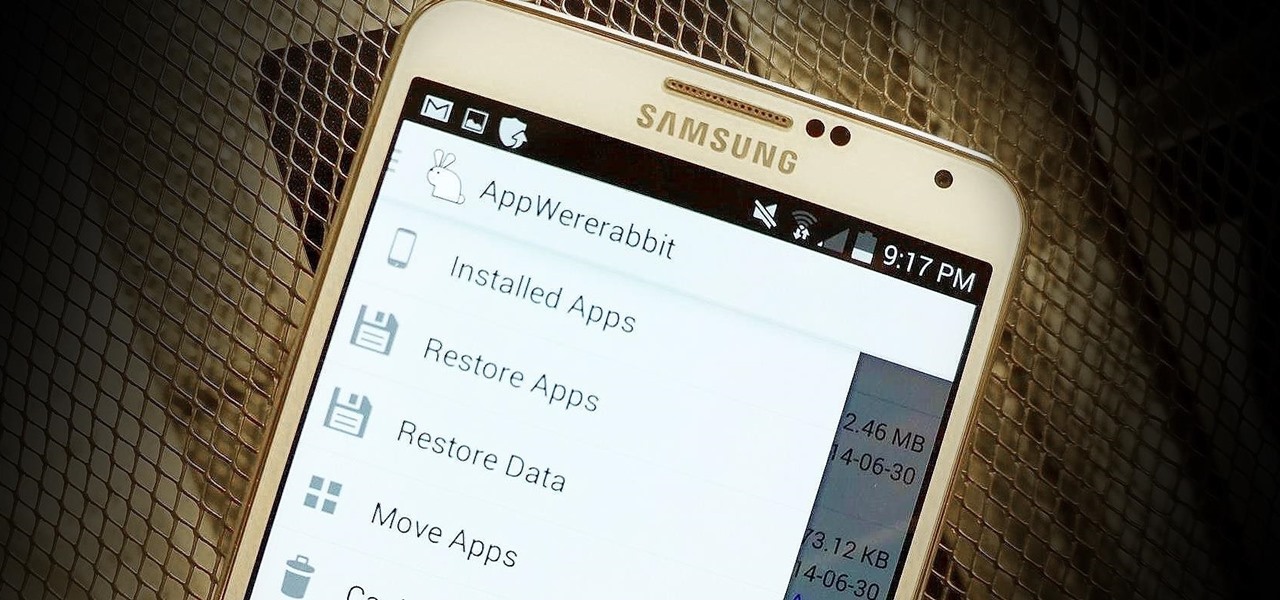
There are over 60-something Android apps cluttering my app drawer. While I'm constantly on the look out for new mods and apps to install, the default way of managing them is cumbersome and just feels unintuitive. I mean, who on Earth would wants to individually manage each app on their device?

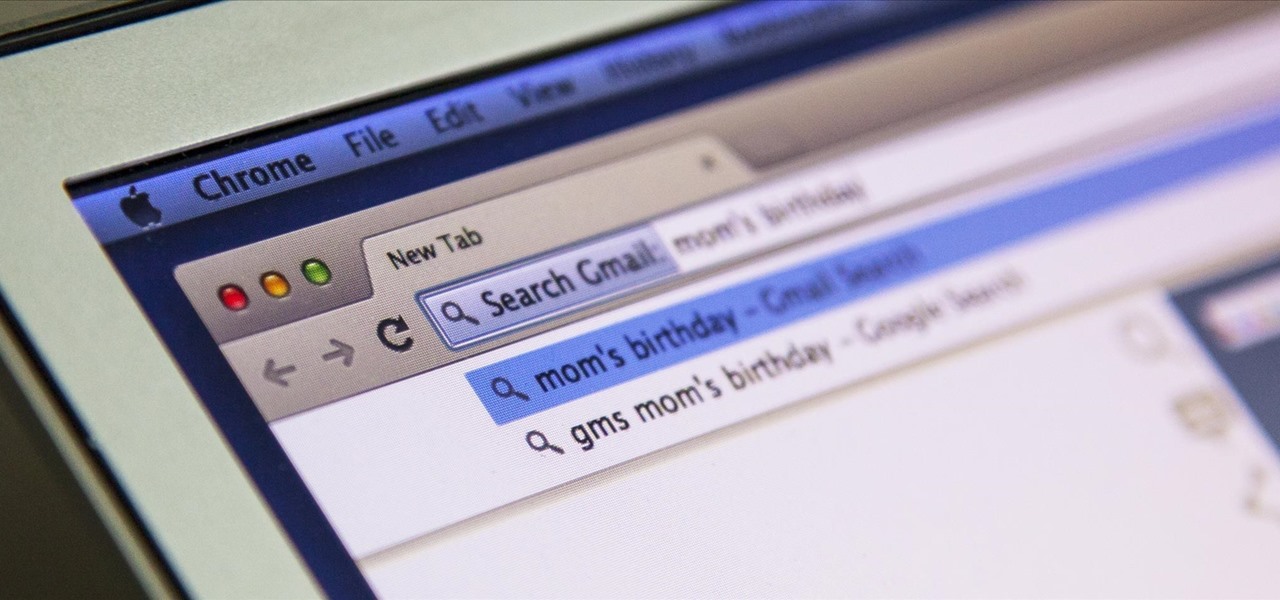
I'm all about saving time. If there's a quicker way to do something, I'm going to find it. For this reason, whenever I need to search through old emails or compose new ones in Gmail, I do it directly from Chrome's address bar, or as Google likes to call it, the omnibox—and you can, too.

If you're like me, you spend a lot of time on your computer, which can be damaging to your eyes in the long run. Studies have shown that staring at a computer screen or television up close for extended periods of time can have harmful effects on your vision.

Journals are a great source of hilarity and embarrassment, detailing everything from your elementary school crushes to those super awkward middle school dances. While rereading your old hand-scrawled entries might make you cringe, that old journaling habit could benefit you as an adult.

Google has finally announced the newest flavor of its mobile OS, Android L (Lollipop?), and I couldn't be more excited. While we won't see its official release until the fall, there are still some features we can get our hands on right now.

One of the best things about the Nexus line of devices is the ease with which one can achieve root. Plug your phone into your PC, download a couple files, type a few commands, and you can be rooted within 30 minutes. No muss, no fuss, no carrier-locked bootloaders.

Anyone who has rooted their Android device has likely used a tool called Android Debug Bridge, better known as ADB, at some point during the process. For most, that is their only interaction with the ADB, but to be a true Android power user, you need to really know the tools at your disposal.